
I just read an article on Ars Technica that gave me the willies. This is a longer article that explains why passwords are failing to do the job anymore, even longer, more difficult passwords that contain upper and lower case letters, numbers and symbols.
This little beauty shown below uses the graphics processing units of 8 AMD Radeon graphics cards to crack passwords. At $12,000, it ain’t cheap, but it can process the entire key space of 8 digit passwords in 12 hours. That is 576.5 TRILLION password possibilities. A smaller unit mention in the article that only used 4 GPUs could process 6.2 billion possibilities per SECOND.
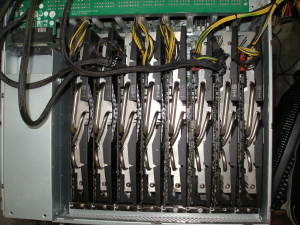
The colossal number of password breaches over the last three years have only made the process easier for the bad guys. Plain text password troves have made it easy for cyber-criminals to calculate the encrypted password hashes of these common passwords, and then compare the encrypted value to other lists of passwords hashes recovered from other databases.
In the last year alone over 100 million stolen passwords have been published online. This is making it easier for the people who write password cracking software tools to design better and faster products. The basic message is this – no matter how clever you think your password it, it probably follows some well used norm that is built into automated password cracking tools.
Some popular “strong” passwords are a first name with with a first letter capitalized and a date, such as Robert1954, which would be mine if I were using this password. (I am not, by the way.) Or two words, both capitalized, with some letter/number or letter/symbol substitution, like Sup3rM@n, which is seen often enough in password postings to be included as a type of password to be tried. Or the same word forwards and backwards like SeptemberrebmetpeS. Even though this looks hard, there is an observable pattern that can be easily dealt with by the software writers.
For me, it is beginning to look like using a password management tool such as KeePass, or two factor authentication like that offered by DropBox is the way to go from here on out.
Keep an eye out for my blog post on two-factor authentication. If you want to get real depressed, click through on the Ars link above and read the full article.
ShareSEP




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com