Data breaches are becoming so commonplace at this point that whether or not your company has one is less a matter of “if” and more a matter of “when.” It is a almost an inevitable certainty that your company will have one – if you haven’t already. And if you are not looking for them, you may never know that it has happened to you.
Ignorance may be bliss – right up until the day you succumb to a Zeus or Neverquest Trojan attack and wake up to find your bank accounts have been drained. How are you going to bounce back from that?
 In an article on Tech Republic, Michael Kassner discusses the plan put forth by the World Economic Forum, and their Partnering for Cyber Resiliency whitepaper. This 16 page plan can be downloaded from the previous link. Cyber resiliency is different from cybersecurity in that it looks at how to survive and recover from a breach, more so than actually preventing one. It examines the interdependency of Internet connectivity, and approaches security from a “act local, think global” viewpoint. It also focuses heavily on developing cooperation between vendors, customers, and other who connect into our networks. As we have seen, really good security can be breached if just a single vendor or client credential is revealed to a determined group of cyber-criminals.
In an article on Tech Republic, Michael Kassner discusses the plan put forth by the World Economic Forum, and their Partnering for Cyber Resiliency whitepaper. This 16 page plan can be downloaded from the previous link. Cyber resiliency is different from cybersecurity in that it looks at how to survive and recover from a breach, more so than actually preventing one. It examines the interdependency of Internet connectivity, and approaches security from a “act local, think global” viewpoint. It also focuses heavily on developing cooperation between vendors, customers, and other who connect into our networks. As we have seen, really good security can be breached if just a single vendor or client credential is revealed to a determined group of cyber-criminals.
The real issue is cultivating corporate leadership that is trained about security threats to their business and are willing to put cybersecurity at the forefront of every business decision, much in the same way that legal liability and related concerns are now. The corporate counsel needs to be joined by a C-level information technology or cybersecurity officer. The CEO needs to learn, understand, and care about cybersecurity threats and preventatives.
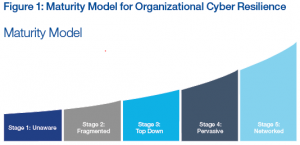
So here is a short checklist from the WEF to help you decide where your company is on the cybersecurity awareness and readiness scale. My comments are in italics.
Step 1: Unaware organizations consider cybersecurity irrelevant, there is no cyber-risk management program in place, and no regard for the security posture of companies they are networked with. Unfortunately, I find many of my clients are right here in the basement, thinking that they are too small to be a target.
Step 2: Due to a breach or education a company starts to understand that being connected to other organizations is a source of risk, there is still little regards for a cyber-risk management program, except for isolating what the company IT department considers important data. These are the companies who have lost data to an ex-employee, or maybe had a case of CryptoLocker wipe out their stored data files. They have tightened security, added or updated their firewall, or taken other piecemeal steps to harden the perimeter, but do not have an organized plan.
Step 3: At this point, C-level executives are on board with a cyber-risk management program, but do not understand it or consider it a competitive advantage. The CEO or owners are aware there is a persistent level of ongoing threats to deal with, but feel overwhelmed by the task.
Step 4: The company has a working cyber-risk management program and complete ownership by the company’s leaders. Management is also cognizant of exploitable weaknesses within the company and those created by interconnections with third parties. These companies have added a cybersecurity professional to staff or hired a qualified consultant to assist with planning and implementation. They have implemented a program that includes employee cybersecurity training as a recognition of the weakest link in any security plan – the people.
Step 5: At this point, cyber-risk assessment is forefront in every business decision. Company management can convey cyber-risk information within the company and inter-company using business terms that enhance understanding across all departments and between companies. This is the goal, where every corporate initiative is given a through cybersecurity review, and threat mitigation and data security is part of every plan.
Go ahead, be hard on yourself, and give your organization a rating. If you are at step one or two, you have a long way to go to get to step three, much less steps four or five. Find a qualifies cybersecurity professional and begin the process. Yes, it will probably be expensive, but less expensive than losing the entire business to cyber-thieves. If you are at step three, then you have made a nice start, but still have your work cut out for you. Either way, find a professional to help you navigate the process.
ShareSEP




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com