You know those surveys, games, and “like and copy” messages that your Facebook “friends” share with you? Would you be surprised to learn that many of these “fun with friends” activities are just cover for a new form of phishing exploit? In the last few years phishing attacks have evolved from a primarily email-based attack into attacks using other vectors including surveys, games, gifts and prizes, and social networks.
Akamai identifies two broad types of phishing campaigns.:
- Negative campaigns – The more familiar is a “negative” campaign causes feelings of fear, uncertainty, and doubt in the recipient target. These include scams such as “your email account is blocked.” “your credit card has expired,” “your invoice is past due,” or “your computer is infected.” There is some sort of problem and the solution is to click on a link or open an attachment to fix the problem.
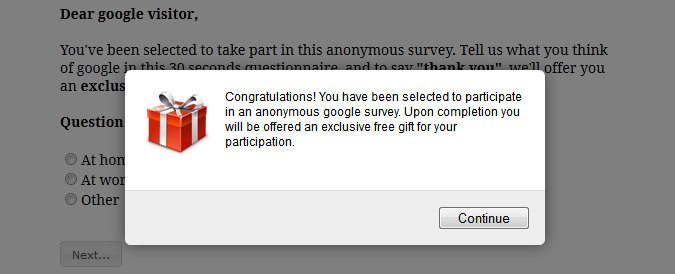
- Positive campaigns – These campaigns evoke feelings of excitement, profit or gain, hope, happiness, and other positive feelings. These campaigns often leverage popular brands in the travel, electronics, retail, or food categories. The approach is frequently via social networks such as Facebook. Often the exploit starts with an invitation to participate in a survey, play a game, or copy and paste a post on your Facebook feed.
- Would you like to play game? – In the scam, you are invited to play a game, and upon winning, you qualify for a prize. To collect the prize you are required to enter your personal information, and this information is used by the scammers to further their attack. No prize ever arrives. Prizes can include gift cards, free products, or even movie or airline tickets.
- Take a quiz or survey – In this scam, the target is invited to take a quick survey, often as short as three questions. Upon completion, the victim learns that they have qualified for a free gift, with the usual instructions to provide personal information.
- Win a prize – Sometimes the phisher dispenses with the game or quiz and just leads with the happy news that you have won a prize of some sort.
- Share with friends – Some scams require the target to “share” the game or survey, or a marketing message with a certain number of friends in order to amass “points” and qualify for a gift or prize. Sharing with your actual friends this way just increases the number of targets for the scammer. You know the saying “with friends like you who needs enemies?” This is a perfect example.
- Fake social network profiles – Another tactic is the use of fake social profiles of other “winners” to create the appearance of legitimacy.
These scams often use popular brands such as American Airlines, Dunkin Donuts, Target, Walmart, Disney, and others. The landing page where the information is collected usually employs some sort of domain name spoofing or typo-squatting. So the landing page may show a URL such as “www.target.survey.com” or “www.dunkkindomuts.com.” These web pages use the logos, colors and other trade dress elements to appear as a legitimate web page for the brand.
We have all learned to be suspicious of fake problems that a negative phishing campaign usually presents. But these positive campaigns often are recommended to us by actual Facebook friends or other social network connections. They are designed to look like legitimate offers from trusted brands. My advice – if it looks too good to be true, it probably is. I generally avoid playing games or filling out surveys just to avoid these sorts of scams.
The Akamai report has a lot of images and examples, and is worth a look if you are concerned about this new phishing method. For more information, click the links that follow.
More information:
ShareJAN




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com