 Virtualization and containerization technologies allow developers, pentesters, network admins and server admins to create multiple virtual instances of a computer system, running inside the actual, physical host system. This is an easy way to quickly deploy and manage dozens or even hundreds of systems used in a learning lab, test network, or even to run full fledged user systems on a single server.
Virtualization and containerization technologies allow developers, pentesters, network admins and server admins to create multiple virtual instances of a computer system, running inside the actual, physical host system. This is an easy way to quickly deploy and manage dozens or even hundreds of systems used in a learning lab, test network, or even to run full fledged user systems on a single server.
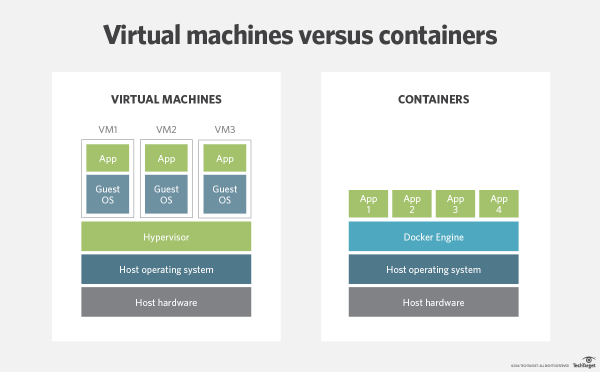
Virtual machines (VM) are created using hypervisor products such as VMWare, Virtual Box, and Hyper-V. VMs require a full, licensed operating system for each instance, and consume fractional shares of host system resources such as the processor, RAM, and hard disk space.
Containerization takes this to the next level, and uses a single virtual guest system to act as an emulator for multiple instances of an application, such as a web site, or web application. The advantage is that the containers use vastly fewer resources of the host system than the same number of VMs would consume. See the illustration below, and keep reading.
For security purposes, one VM or container should not be able to take over another one. Unfortunately, a serious security flaw dubbed CVE-2019-5736 was found in the function runc (run container) that allows that security breach to happen.
If you are using Docker, LXC, or Kubernetes or any containerization product that uses runc, this new vulnerability can allow an attacker with root permissions in one container to elevate to root permissions outside the container. This can allow them to attack and take over other containers or even the host system. If you have a version numbered runc 1.0-rc6 or earlier, you need to take action.
Docker users should be running version 18.09.2, which patches this bug. Check the Docker release notes for 18.09.2
Kubernetes users should read the Kubernetes article entitled Runc and CVE-2019-5736, to learn how to patch the bug and set up hardened security settings.
The solution is to update any vulnerable containers systems. Prevent guest containers from running with root privileges. If your containers are part of a cloud service you are using, you will need to check with your vendor to see if they have updated your containers.
ShareFEB




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com