So this is how the Internet is designed to work: Basically information from your computer, such as email, or web requests, are broken up into small data packets, sent across the Internet using the best path available, and reassembled by the receiving computer back into human useable form. This communication across the Internet is considered to be “connectionless” and “unreliable” because the communication pathway is not dedicated to the particular transaction, and delivery of packets is merely best effort, not guaranteed. If packets are lost along the way that is ok, the receiving computer merely asks to have those packets retransmitted. Packets may and do arrive out of order; packets in the same session may travel different routes as long as they basically try to end up in the same place. This fairly haphazard system actually works pretty well in practice, as we all know. This communication protocol, TCP/IP, is how the Internet works.
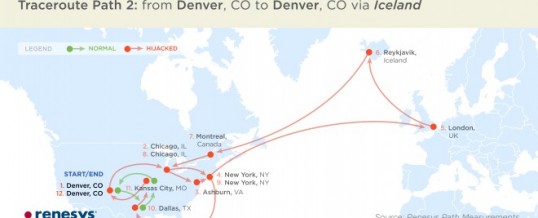
It would be possible for an organization to try to influence the route that packets take by manipulating the different traffic shaping protocols that the Internet Service Providers use to route traffic efficiently to less busy nodes during times of high utilization. In fact this happened in 2013 when a large block of traffic was mysteriously routed through Iceland for no apparent reason. (see graphic below)
Information security blogger Bruce Schneier recently posted an article illustrating how the NSA could legally spy on Americans by using traffic shaping protocols to route US Internet traffic overseas where collecting the information would be deemed “legal” since the data collection actually happened to traffic that was overseas. So it would be possible for the NSA and other governmental and criminal organizations to use the connectionless nature of Internet traffic to pass it through routers they control in order to do whatever they want with the information they gathered, before sending the packets back on their way, with no one being the wiser, in most cases.
This is why there has been in increase in the use of encryption technologies for information that you are sending over the Internet. If you have a choice, obviously encryption beats just letting whoever rifle through your email and other transactions.
JUL




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com