What follows is a sponsored post from cybersecurity firm Sequretek.
Businesses usually tend to trust their partners/ technology partners when related to the security of the data flowing across partners. This approach has changed drastically these days; now businesses themselves need to focus on their cyber security measures. There is a sudden rise in the number of supply chain attacks, by which we can conclude that attackers are easily spotting out vulnerabilities in the supply chain network of the organisations. Today, information security is not about your organisation alone; it is also about the security measures that your partner has in place.
Let’s look at an incident that recently took place against a leading Taiwan-based multinational computer and electronics OEM company. The attack created a menace in the market because it was carried out through trusted sources. The OEM’s update system was hijacked to send out malicious updates to almost half a million users. The attackers hijacked the OEM’s auto-update process to deliver malware. Although preventing such attacks is pretty difficult, vendors and the customers need to do more in order to mitigate cyber risks.
The hackers created a trojanized version of a legitimate application, called the ASUS Live Update Utility, signed it with valid certificates belonging to ASUS, and distributed it to users through the application’s own update mechanism. This signifies that the attackers may have had access to ASUS’s code signing and update infrastructure. (Source: CSOonline)
This is an example of how cyber criminals can take control of the very system that you rely on to protect your machines. This is exactly what a supply chain attack does!
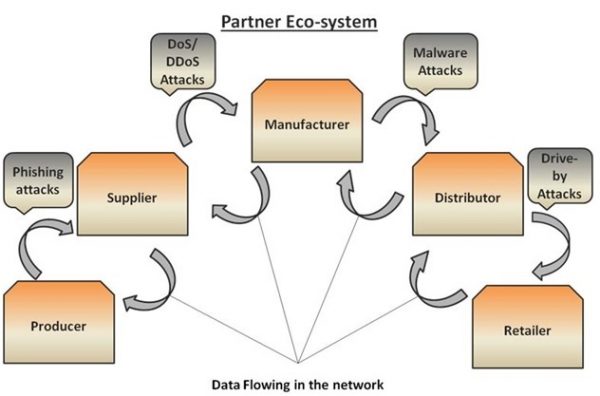
The diagram below depicts the various partners generally involved in a supply chain, and the type of attacks that may occur when data flows from one partner to other.
It becomes difficult to control the data as the number of parties involved in supply chain increases. There are chances of multiple attacks taking place in the supply chain. Therefore, it becomes crucial for each partner to understand the need of information security and apply a defense mechanism. Any vulnerability in even a single system can affect the complete supply chain.
MITIGATION
A mitigation strategy against cyber attacks ideally has three steps: Detection, Protection and Response.
You should be aware that your system has been attacked, without which you will never know if some sensitive information is flowing out of your system. Detecting a supply chain attack becomes difficult with just traditional AV scanners. Traditional AV scanners rely only on the database of malware signatures which makes detection of modern malwares cumbersome. Such supply chain attacks prove to be effective as the victims download the security updates from an official site itself; neither people treat security updates with suspicion nor do many anti-malware tools.
You need to constantly monitor every application – even if it is from a trusted source. New technologies like AI-ML help you to identify or trace the patterns of the activity that rhyme with malware behavior. Activities like dropping some files, deleting files, making changes to registry, communicating to malicious IP’s are some suspicious activities.
As the number of malware and types of malware attacks evolve, it becomes extremely important to protect each of your vulnerabilities in your system. Some best practices could include patching the system with tested and verified updates, having a regular checkup on the inventory in the system, investing in a Next Generation Antivirus, and having control over all the applications that users are allowed to use.
Modern malware needs a modern approach to create a defensive shield. Deploying strong code integrity policies to allow only authorized applications to run, and using endpoint detection, protection and response solutions that can automatically detect, protect and remediate malicious/suspicious activities are better ways to protect against supply chain attacks.
Sequretek’s EDPR (Endpoint Detection, Protection and Response) is one such modern product available that could help you not only respond to such attacks, but also simplify the process of identification and protection of your vulnerable systems. Sequretek’s EDPR is, by far, the only product in the market that unifies 5 different endpoint technologies (namely Anti-Virus, Anti-APT, Patch, White-listing and Data Leakage Prevention) across heterogeneous platforms supporting both on-premise and cloud solutions.
Click here to request for a demo of EDPR | Know more about Sequretek’s Offerings
ShareJUN




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com