Phishing Email Alerts
Catch of the Day: Password Renewal Phish
Chef’s Special: FBI BEC Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
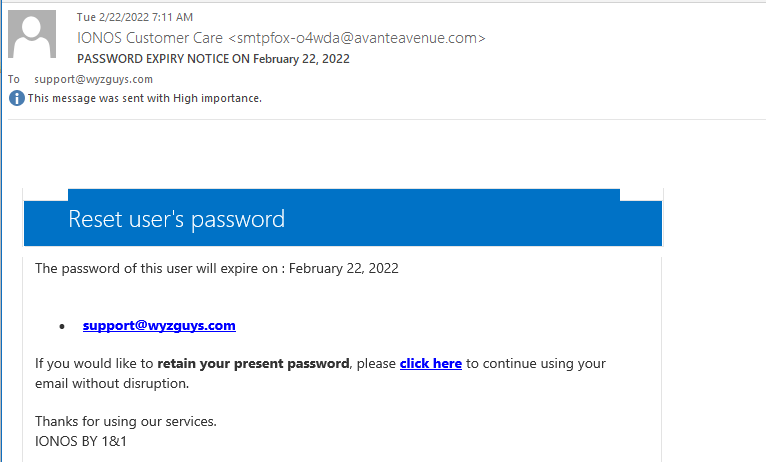
IONOS Password Renewal Phish
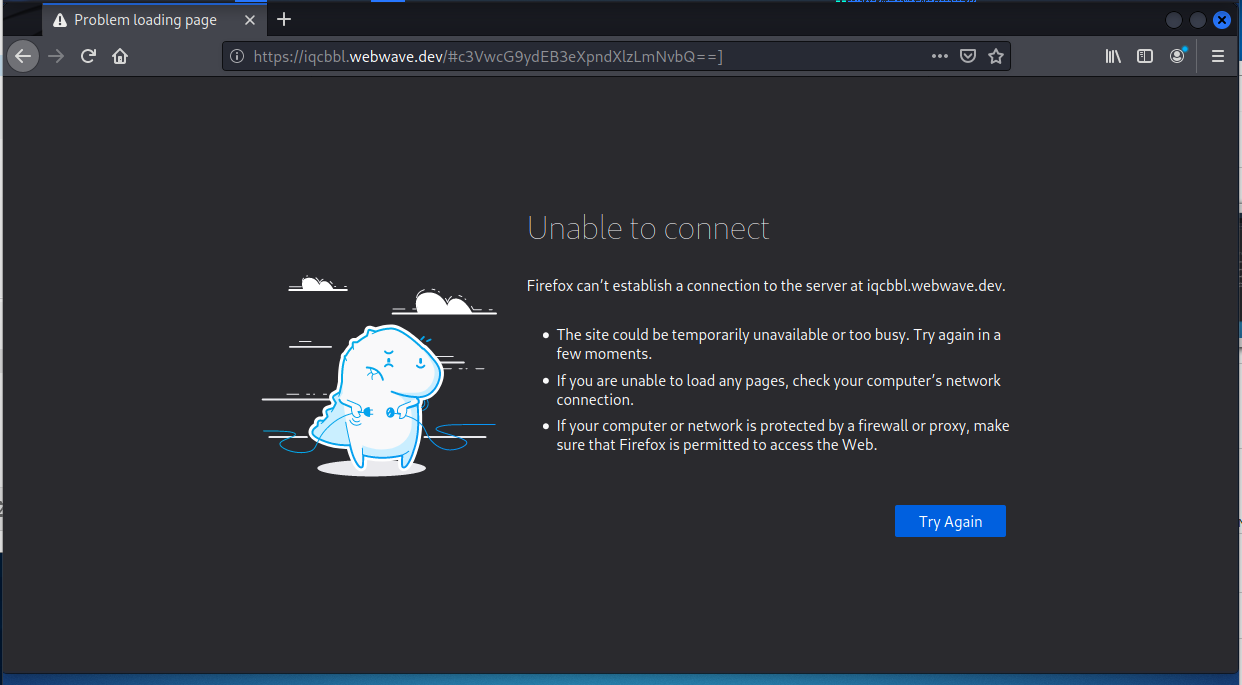
The nets have been empty, but I did manage to catch this credential stealing phishing email sneaking into my inbox. When I analyzed it, the malicious link had already been identified and the landing page taken down.
The link resolved to https://iqcbbl.webwave.dev/#c3VwcG9ydEB3eXpndXlzLmNvbQ==] The letters following the # sign is Base64 encoding, and when I decoded it it translated into support@wyzguys.com.
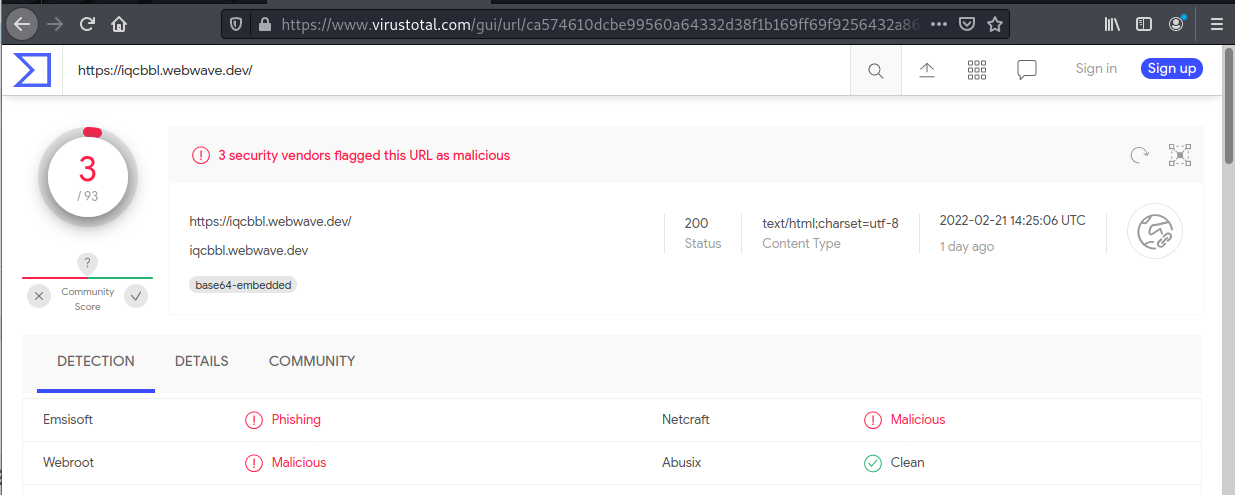
Here is the email, the landing page, and the VirusTotal report on this phish.
FBI Sees Increase in Use of Virtual Meeting Platforms for BEC scams
The US Federal Bureau of Investigation said today that it had seen an increase in the use of virtual meeting platforms as a way to trick organizations into sending payments to the wrong accounts as part of a type of attack known as BEC scams.
The post FBI sees increase in use of virtual meeting platforms for BEC scams appeared first on The Record by Recorded Future
The Four Traits of Most Email Scams
The best thing you can do, at the individual level, is to teach yourself (and everyone else) how to spot a scam. You want everyone to have a healthy level of skepticism and evaluate all incoming messages, no matter how they arrive (be it email, web, SMS, social media, voice calls, etc.), and look for potentially suspicious signs of a social engineering scam. A scam is a scam is a scam. Most scams have the following traits:
- They arrive unexpectedly
- The ask the receiver to do something the sender has never asked the receiver to do before
- They indicate a sense of urgency, claiming the receiver will be penalized if they do not take action immediately
- The requested action could be harmful to the receiver or their organization if the requested action is taken and is malicious
Read the full article at this blog post with links and flow chart: https://blog.knowbe4.com/traits-of-most-scams
Meta and Chime File Lawsuit Over Phishing Attacks
Meta (Facebook’s corporate parent) and the digital banking company Chime have filed a joint lawsuit against two Nigerian citizens for allegedly impersonating Chime in phishing attacks, BleepingComputer reports. The defendants are accused of using “more than five Facebook accounts and more than 800 Instagram accounts” to direct users to spoofed Chime login pages in order to harvest their credentials.
“Many of these accounts used the Chime logo as their profile photo and the word ‘Chime’ with varied spellings in the username, such as ‘_ch_im_e_’ and ‘chime942,” the lawsuit says. “Between no later than March 2020 and October 2021, Defendants used their network of Chime-branded Facebook and Instagram accounts to impersonate Chime in violation of the Terms.”
“For example, Defendants used Chime-branded usernames, domains, and/or profile photos in these accounts without Chime’s authorization.”
Blog post with links: https://blog.knowbe4.com/meta-files-lawsuit-over-phishing-attacks
Share
FEB





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com