Phishing Email Alerts
Catch of the Day: Email Account Misuse Phish
Chef’s Special: Virus Detected Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
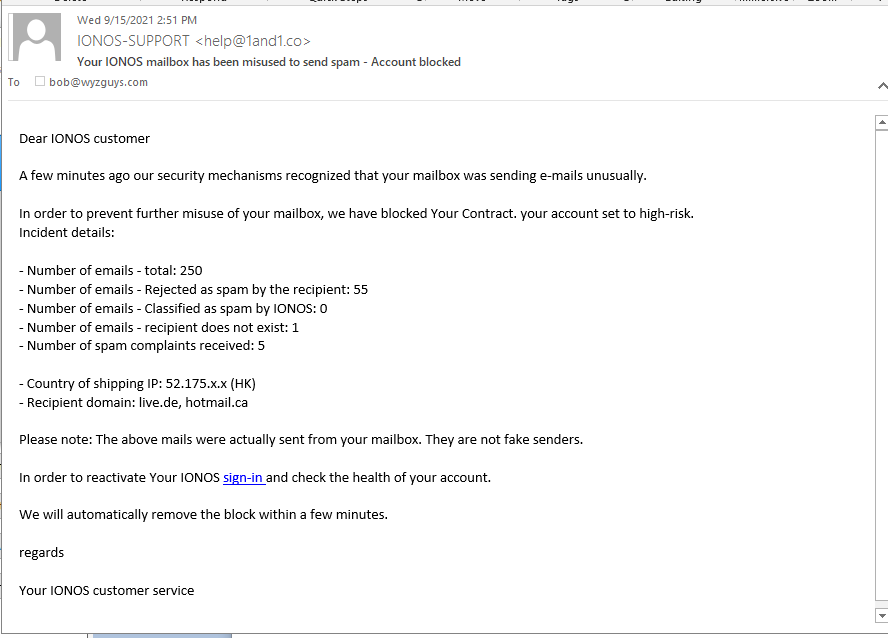
Email Account Misuse Phish
This email makes it look like my email account has been hijacked.
The sending email is a close, typo-squatted spoof (1and1.co not .com) The email headers show the source as: Return-Path: <bounce@deadstock.ca> Received: from nvn.deadstock.ca ([116.203.95.223]). The sign-in link resolves to https://www.oldps1.com/status
.Here is the landing page:
Another day, another credential stealing exploit.
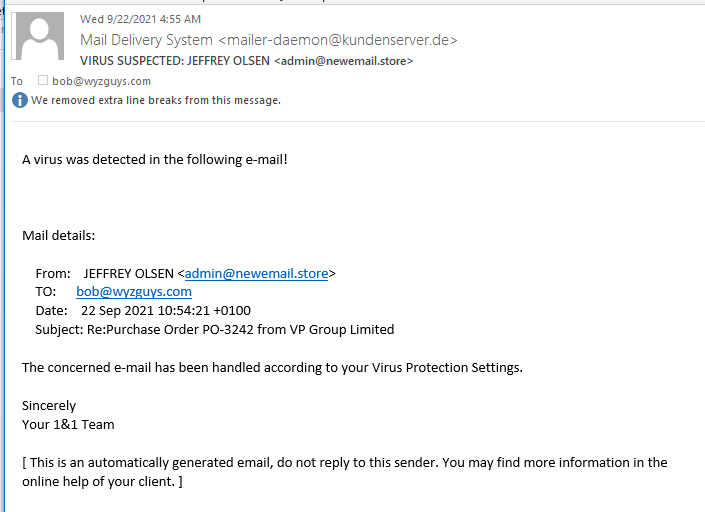
Virus Detected
It’s good to know that your security stuff is really working. This alert came from my email host, the first of several layers of email defenses. I included this in the Phish Fry as an example of phishing types. This one would contain a fake purchase order as a document attachment.
Business Email Compromise Scam Takes New Hampshire Town for $2.3 Million
Social engineering is at the heart of this attack, where scammers successfully tricked a town into redirecting not just one but several bank transfers.
Last month, the town of Peterborough, New Hampshire, put out a press release stating they were the victims of a Business Email Compromise (BEC) scam in July focused on tricking their finance department into changing banking details on payments intent on being made to the Contoocook Valley School District as well as a general contractor Beck and Bellucci.
Taking advantage of the “transparent nature of public sector work to identify the most valuable transactions and focus their actions on diverting those transfers,” the cybercriminals were able to redirect funds to scammer controlled bank accounts without raising any red flags with the town of Peterborough. It wasn’t until the ConVal School District called inquiring about their missing $1.2 million payment that the town was even aware of a problem.
As of the time of writing this article, the $2.3 million overall that was stolen had not been recovered.
This simple story of how social engineering is sometimes all it takes to become a victim is a stark warning for organizations that anyone involved with financial transactions should be taught to be vigilant when interacting with emails. Through security awareness training, stories like this could literally become a thing of the past – all it takes is a single user to recognize that something’s amiss and check the from email address, make a phone call to verify, something other than just unknowingly go along with the fraudulent request.
Blog post with links:
https://blog.knowbe4.com/business-email-compromise-scam-takes-new-hampshire-town-for-2.3-million
“Back to basics” as courier scammers skip fake fees and missed deliveries
“Stop. Think. Connect.” Say those words aloud – and please pronounce the pauses prescribed by the periods!
A New Phishing Attack on Microsoft 365 Users Leverages Open Redirects To Avoid Detection
The use of open redirects from legitimate domains makes phishing emails that much more believable and credible, obfuscating the dangerous nature of these attacks.
In the ongoing saga of attacks on Microsoft 365 users, security analysts at Microsoft recently announced a widespread attack that utilizes open redirects – a technique used in web development to point to the URL visitors of a website should be taken to once the initially-visited page is done processing the visit.
A simple example of an open redirect is the following:
[https://]example[DOT]com/redirect[DOT]php?url=[http://]attacker[DOT]com
According to Microsoft, attackers will use a bit more trickery to fool those that choose to hover over links in emails before clicking on them, embedding a malicious URL within what appears to be a trusted URL (note the red portion of the screenshot at the blog)
In many cases, redirects to malicious URLs first take visitors to Google reCAPTCHA pages to further obfuscate the nature of the final destination from security solutions designed to evaluate email links.
While evaluating destination URLs via hovering over links in an email is definitely a good security practice, threat actors are becoming wise to this and are taking steps such as those mentioned above to make it even more difficult to spot a malicious link.
Users should be taught via Security Awareness Training to be more mindful of the actual message being sent – if unsolicited, it should be treated with at least a bit of distrust and scrutiny, being certain it is legitimate before engaging with links – benign or malicious.
Blog post with links and screenshot:
https://blog.knowbe4.com/new-phishing-attack-on-microsoft-365-users-leverages-open-redirects-to-avoid-detection
New WSJ Article About Social Engineering: ‘Blame it on the Lizard Brain’
This is a good article to send to your C-level execs with your request for new-school security awareness training budget.
People need to work to overcome their inherent biases in order to avoid falling for social engineering attacks, according to Heidi Mitchell at the Wall Street Journal.
“Criminals lure smart people into their traps by taking advantage of the unconscious, automatic processes that act as shortcuts to make our decision-making more efficient,” Mitchell explains. “These cognitive biases—arising from what’s often referred to as our ‘lizard brains’—can cause us to misinterpret information and make snap judgments that may be irrational or inaccurate.”
Professor Cleotilde “Coty” Gonzalez from Carnegie Mellon University told the Journal that criminals take advantage of human psychology to make their attacks more effective, explaining that “if something is presented as a loss, we are more willing to take a risk [to avoid it]; if it’s presented as a gain, we are OK with taking a safe option.”
As a result, people are more likely to fall for a scam that tells them they’re going to lose money, as opposed to one that offers to give them money.
Mitchell adds, “Or a scammer might send a message to your work email, claiming that there is a problem with an account at one of your corporate suppliers, and warning that your shipment—one that your boss is counting on—will be delayed unless you verify your account information in a link provided by them. The fake link leads to a fake website that looks like the real thing. By playing on your fear of losing access to your account, the scammer gets your credentials.”
Scammers also take advantage of authority bias and urgency bias to compel their victims to act. Authority bias can be seen in business email compromise (BEC) attacks, in which an attacker impersonates a person of authority within an organization and sends a request to a lower-level employee. Urgency bias is often tied into these attacks, and involves making the victim believe they must act quickly to fulfill a request.
New-school security awareness training can give your employees a healthy sense of suspicion so they can spot red flags associated with social engineering attacks.
The Wall Street Journal has the story (paywall):
https://www.wsj.com/articles/how-hackers-use-our-brains-against-us-11631044800
SEP






About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com