Phishing Email Alerts
Catch of the Day: Square Deposit Phish
Chef’s Special: Login Alert Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
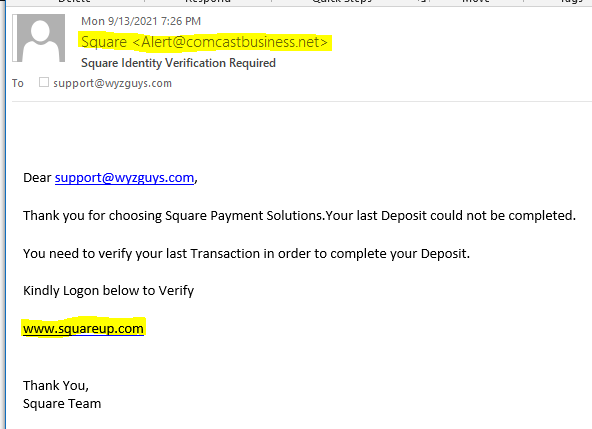
Square Deposit Phish
This email makes it seem that a deposit from Square, a popular credit card processor, failed. The email encourages you to sign in to your account to rectify the problem.
The sender address from Alert@comcastbusiness.net is concerning because it appears to be a legitimate email account on a legitimate Comcast domain.
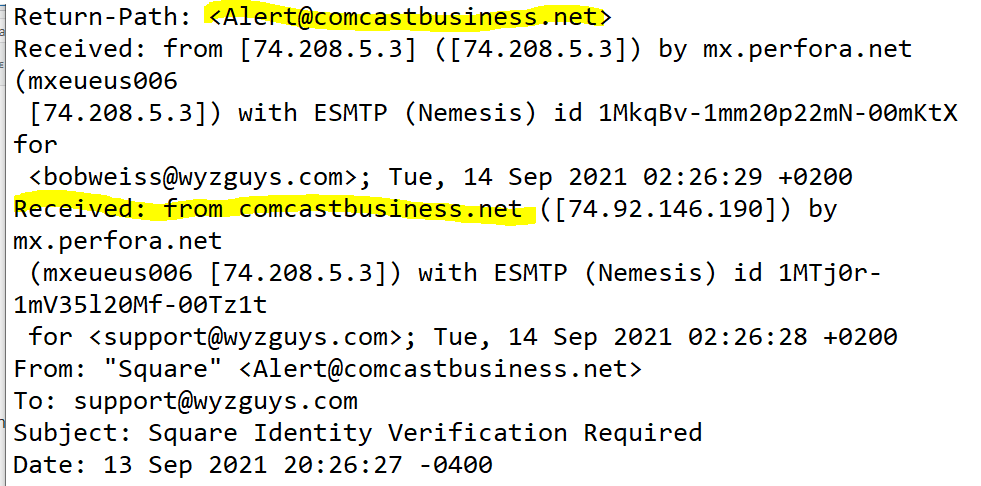
The email headers are below. As you can see this is being sent from a Comcast email account by Comcast mail servers.
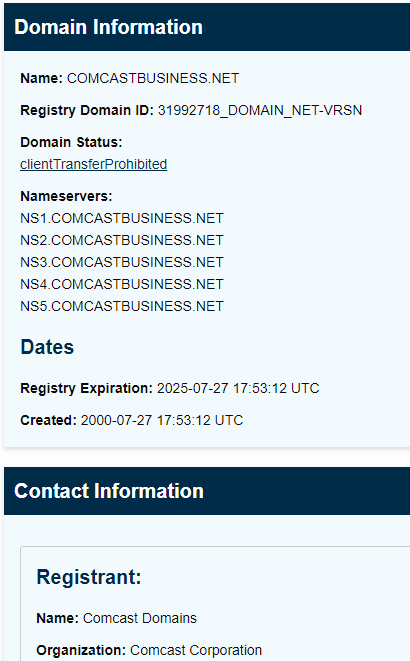
A quick check with ICAAN WHOIS confirms that this is a legitimate Comcast domain, not a clever bit of typosquatting.
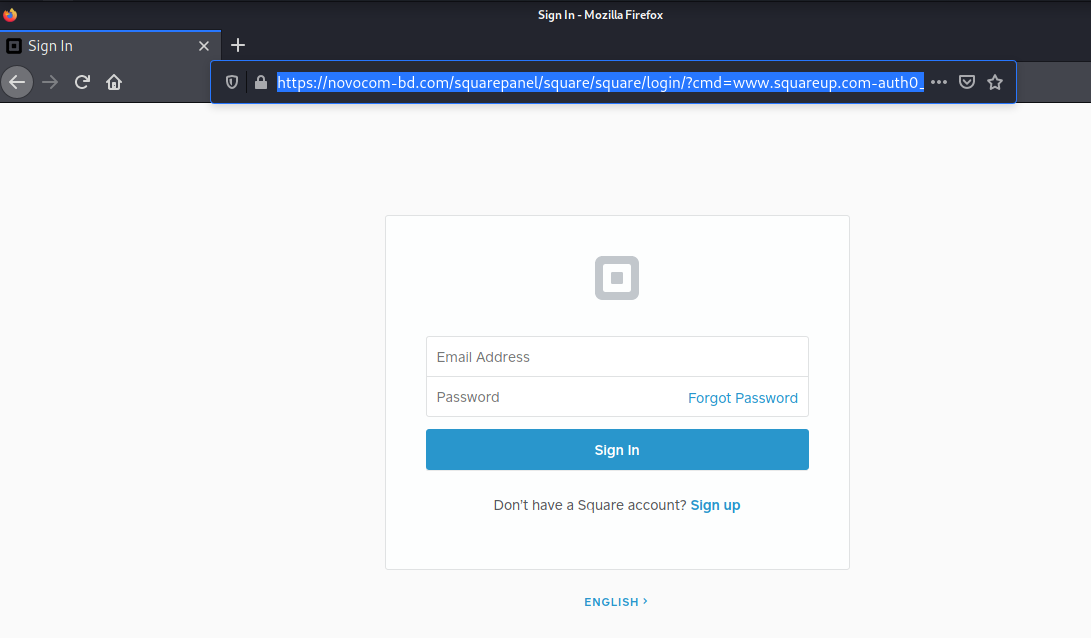
The www.squareup.com link resolves to https://s.id/FUHjh which redirects to https://novocom-bd.com/squarepanel/square/square/login/?cmd=www.squareup.com-auth0_submit&id=17c60f06bb226c5bfcd079f5cd371b1e17c60f06bb226c5bfcd079f5cd371b1e&session=17c60f06bb226c5bfcd079f5cd371b1e17c60f06bb226c5bfcd079f5cd371b1e
Here is the landing page. Looks like a legitimate Square login screen, but entering your credentials here will just give the attacker access to your Square account, and attached bank savings and checking accounts.
Be on the lookout for suspicious phish from your credit card processors.
Login Alert Phish
I got this one the other day, and by the time I got around to analyzing it, the destination web site had been taken down. The good news is these exploits get expunged by the powers that be within 24 hours in many cases.
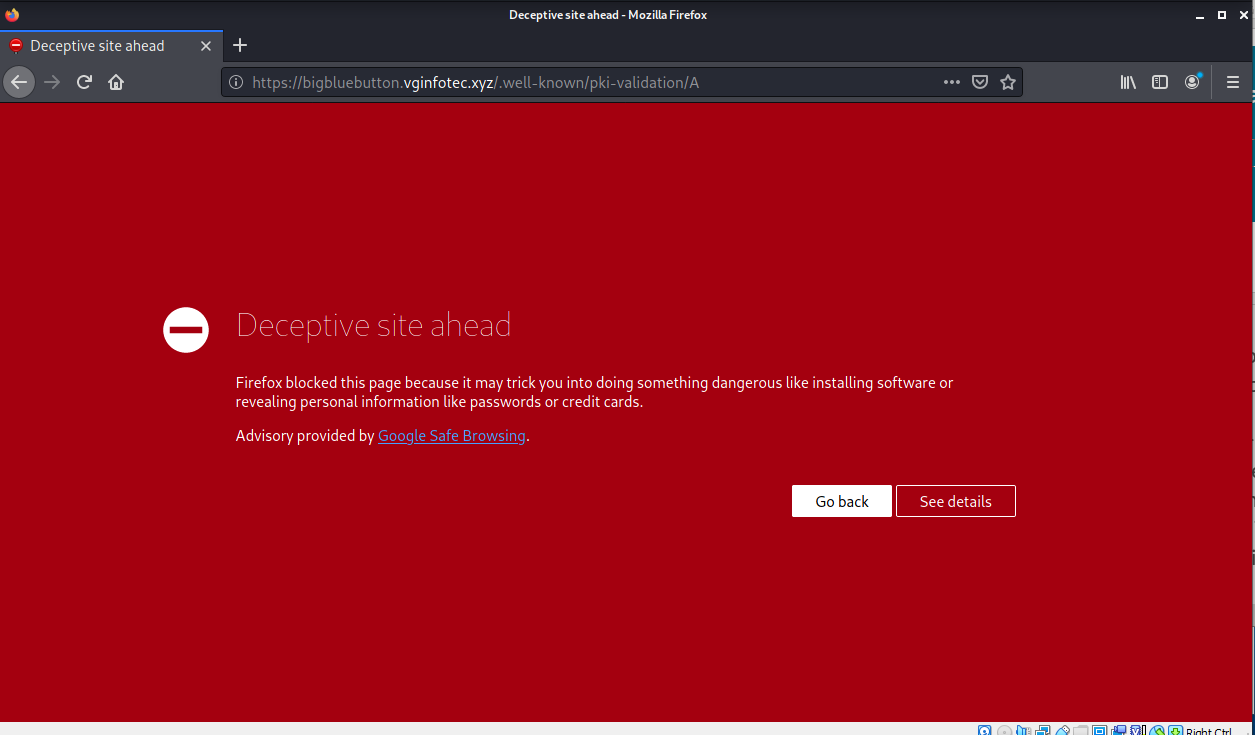
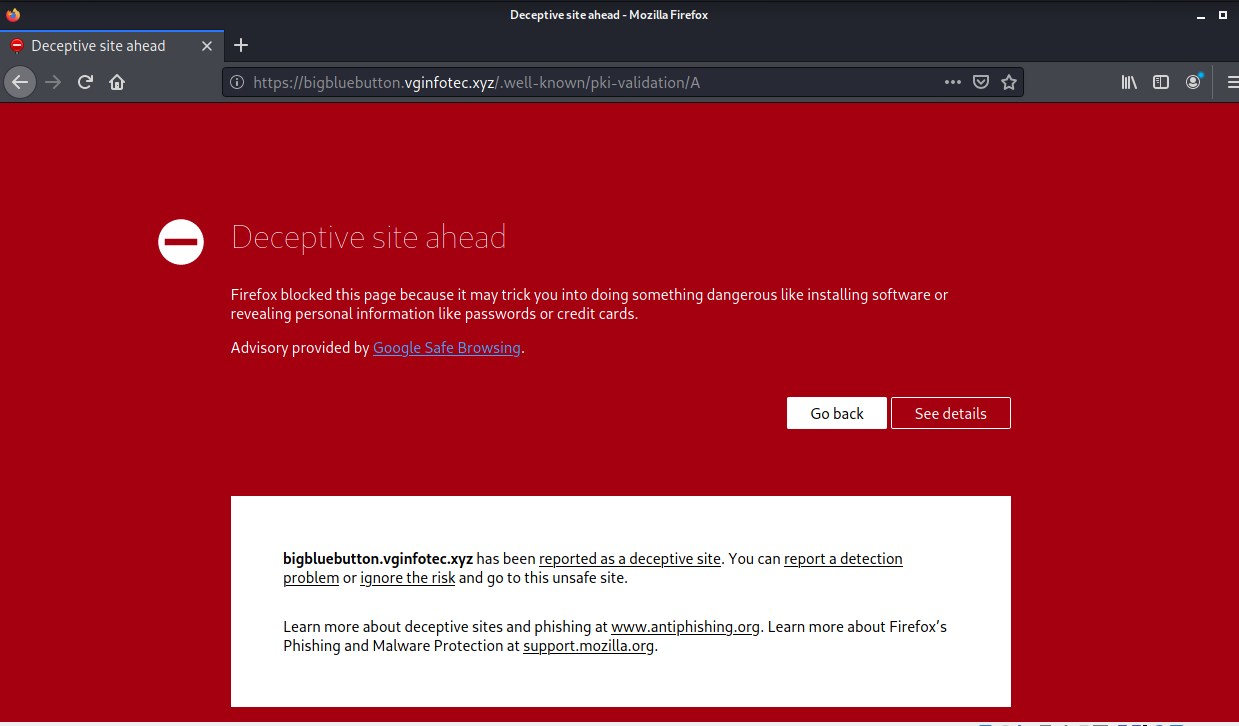
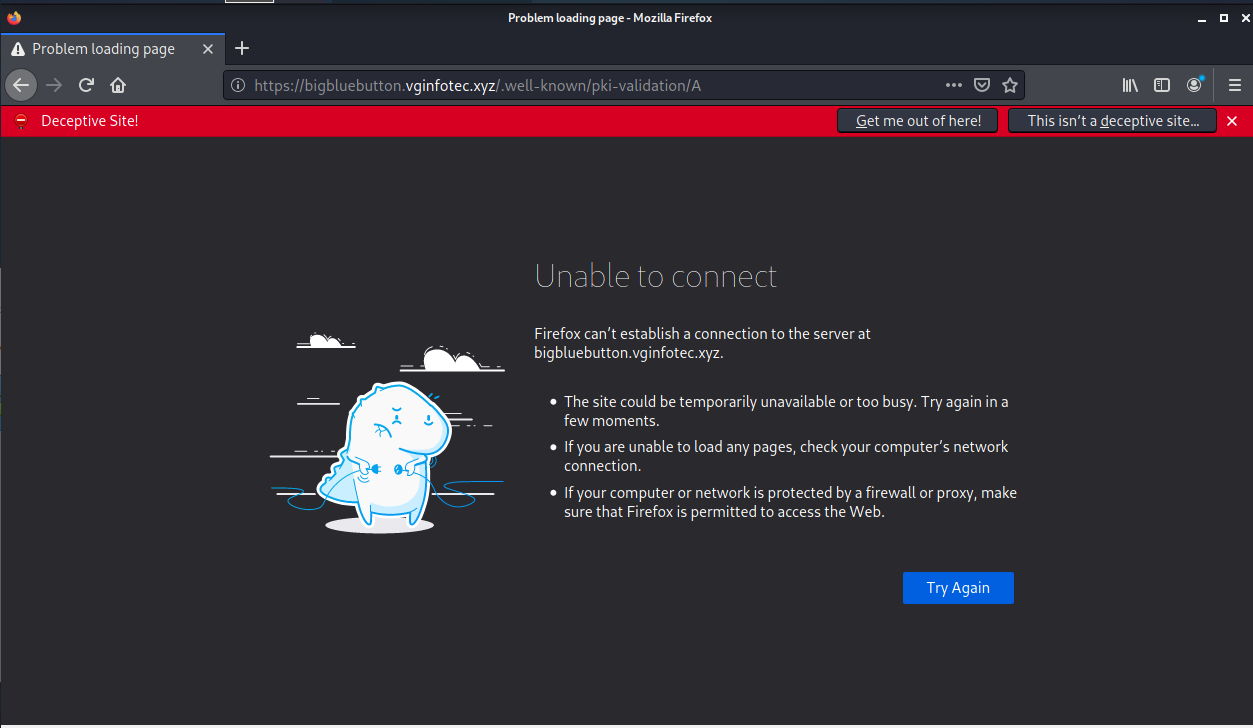
The Check Activity button resolved to https://bigbluebutton.vginfotec.xyz/.well-known/pki-validation/A and took me to this set of landing pages. Unfortunately, only warning pages remain. But these should be a good clue that you are headiing in the wrong direction.
Clicking on See details
Clicking on ignore the risk
So the landing site is down already. Probably another credential stealing exploit.
QuickBooks Phish
I reported this phishing attack on August 20, but the links had expired, and we couldn’t tell much. Today I got the same email again.
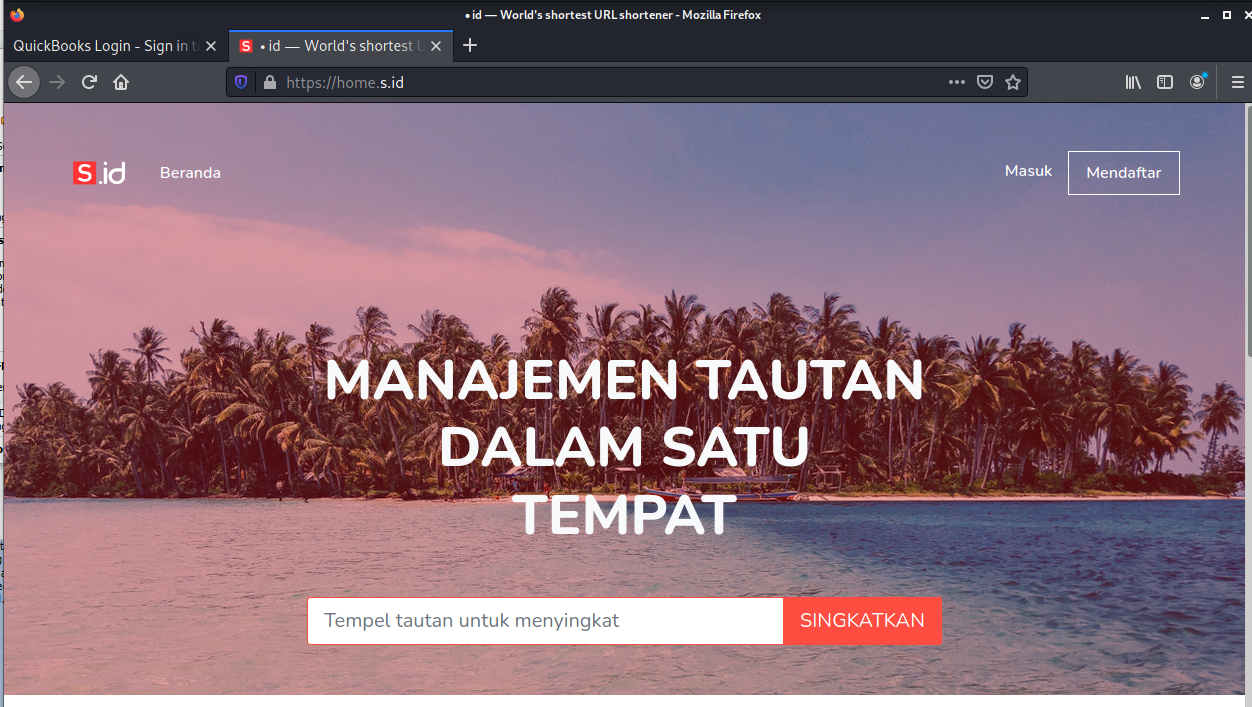
The www.intuit.com link again resolved to https://s.id/G714. Https://s.id appears to be a hijacked Indonesian “coming soon” website that is being used for redirection.
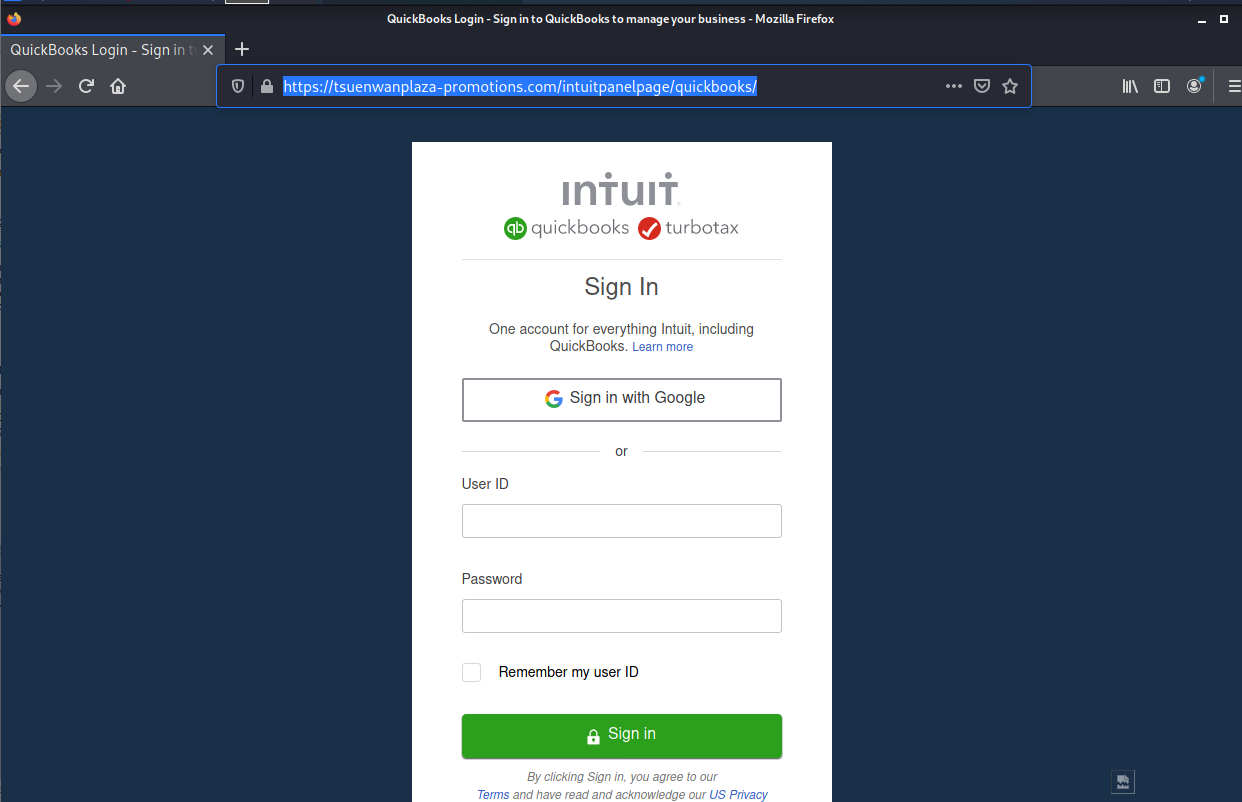
Clicking the link redirected us to https://tsuenwanplaza-promotions.com/intuitpanelpage/quickbooks/, which is hosted on another hijacked site. At the time of inspection (2021-09-16 06:50 CDT), VirusTotal evaluated this site as clean.
Here is the landing page. Yet another credential stealing exploits, and this time you can give away your Google account login if you would prefer, which is a key that can open many doors.
Undelivered Email Phish
I received the phishing email below, and it appears to come from my hosting provider. This appears to be an international effort. What it really shows is that the criminal entities that are engaged in this type of attack rely on underground resources from around the world.
First, the sender email is from an Japanese account Wyzmail IONOS Mail <u1580004@ov158.mcnx.jp>
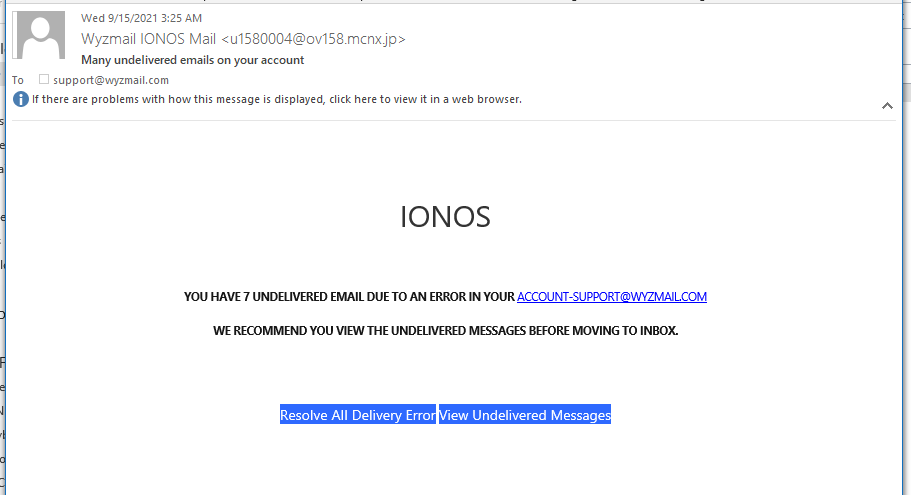
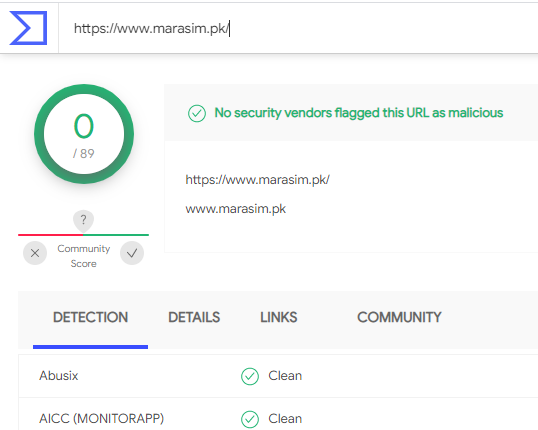
The Resolve All Delivery Errors and View Undelivered Messages buttons both resolve to https://www.marasim.pk/#support@wyzmail.com, a website in Pakistan that appears to have been hijacked to provide a “safe” URL for the embedded links that would slip past spam filters. When I checked it out on VirusTotal I got a clean result.
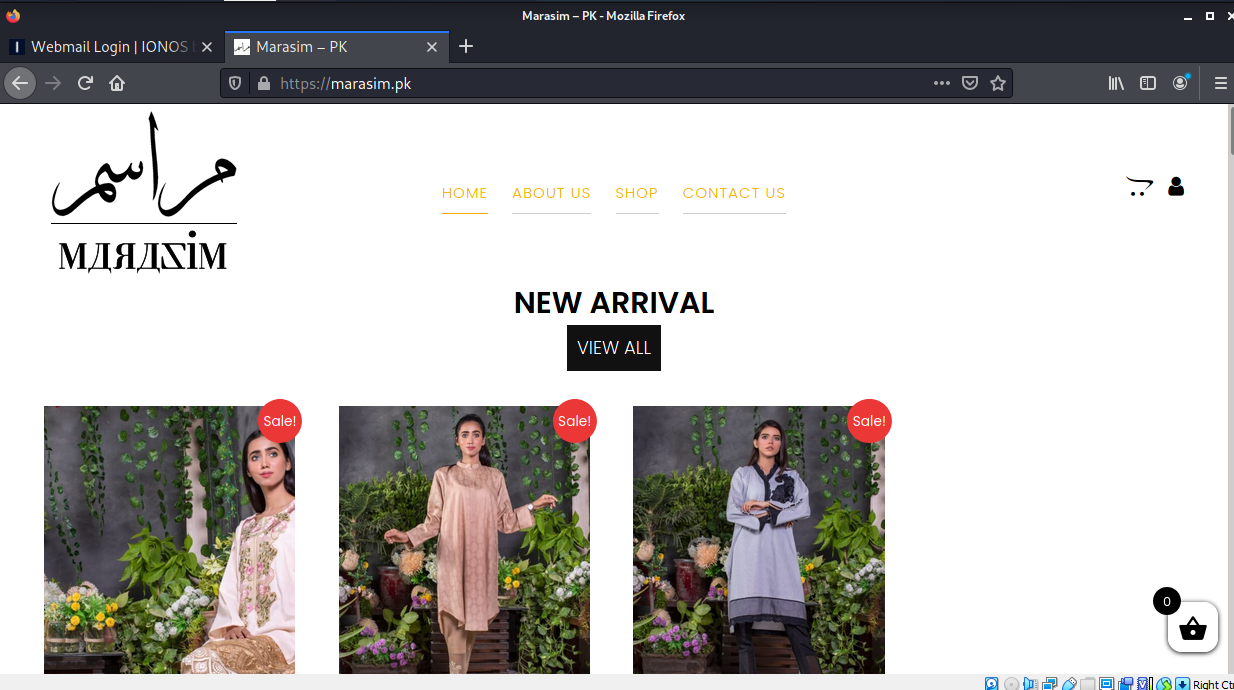
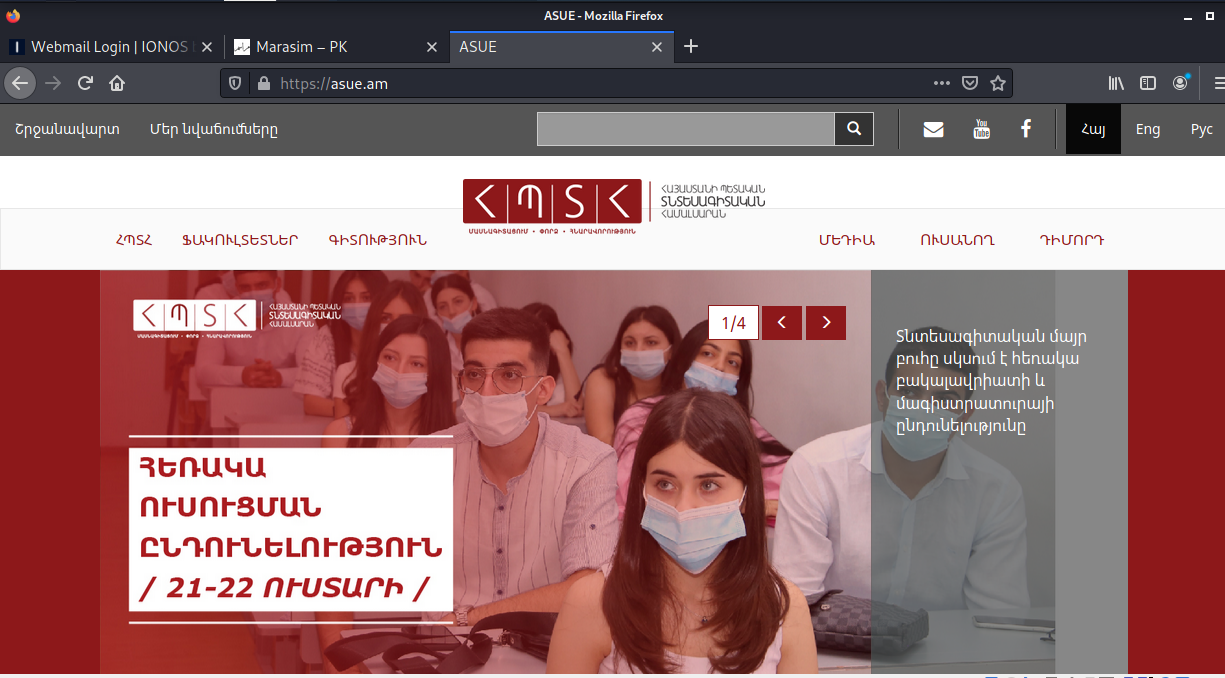
And here is the hijacked website’s home page.
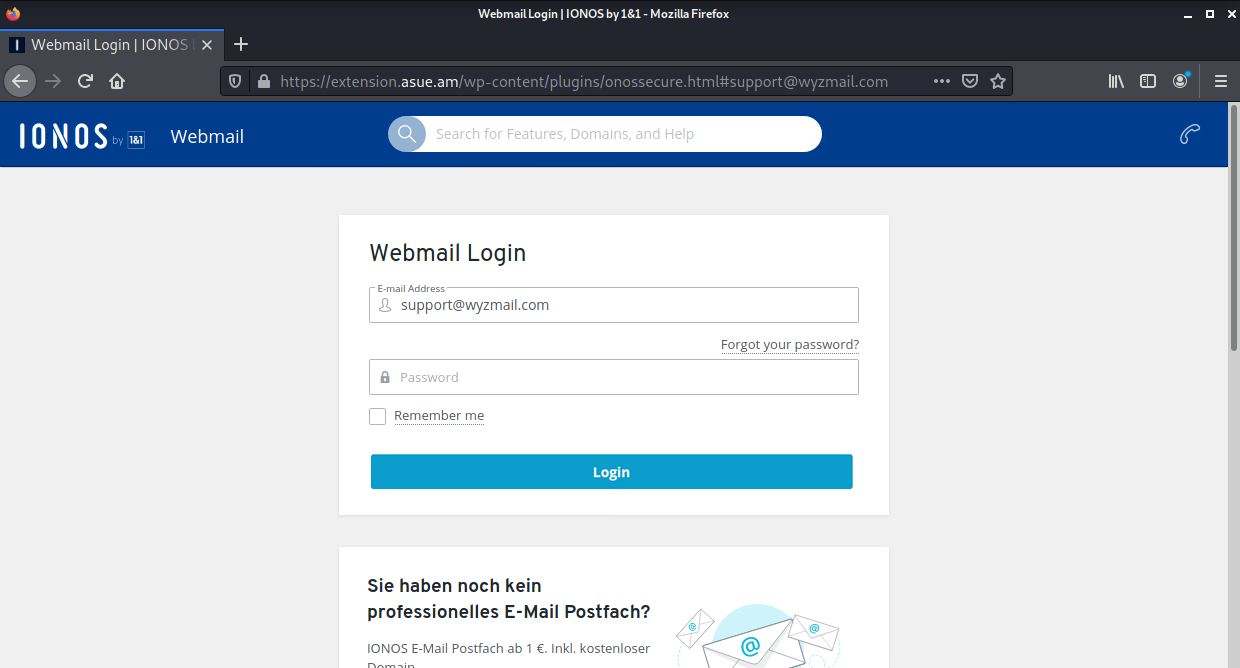
This link was redirected to https://extension.asue.am/wp-content/plugins/onossecure.html#support@wyzmail.com. This is an Armenian site that is hosting the credential stealing landing page shown below. The landing page is in the German language. This is like a mini Festival of Nations!
First the VirusTotal report
And now an image of the landing page hosted in Armenia.
And here is the homepage of this hijacked website.
Needless to say, I avoided the credential stealing login page, and so should you.
No, I Did Not Hack Your MS Exchange Server
The Shadowserver Foundation, a nonprofit that helps network owners identify and fix security threats, says it has found 21,248 different Exchange servers which appear to be compromised by a backdoor and communicating with brian[.]krebsonsecurity[.]top (NOT a safe domain, hence the hobbling).
Shadowserver has been tracking wave after wave of attacks targeting flaws in Exchange that Microsoft addressed earlier this month in an emergency patch release. The group looks for attacks on Exchange systems using a combination of active Internet scans and “honeypots” — systems left vulnerable to attack so that defenders can study what attackers are doing to the devices and how.
David Watson, a longtime member and director of the Shadowserver Foundation Europe, says his group has been keeping a close eye on hundreds of unique variants of backdoors (a.k.a. “web shells”) that various cybercrime groups worldwide have been using to commandeer any unpatched Exchange servers. These backdoors give an attacker complete, remote control over the Exchange server (including any of the server’s emails).
On Mar. 26, Shadowserver saw an attempt to install a new type of backdoor in compromised Exchange Servers, and with each hacked host it installed the backdoor in the same place: “/owa/auth/babydraco.aspx.”
“The web shell path that was dropped was new to us,” said Watson said. “We have been testing 367 known web shell paths via scanning of Exchange servers.” More…
The Number Of Daily Ransomware Attacks Skyrockets Nearly 1,000% In 2021
New analysis of cyberattack data by security vendor Fortinet sheds light on not only how much ransomware is really being experienced, but who’s being attacked the most.
Just when I think I’ve seen it all, yet another stat from a new report shocks me. This time it comes from Fortinet’s FortiGuard Labs 1H 2021 Global Threat Landscape Report and revolves around the currently-observed state of ransomware. According to the report, ransomware is increasingly being felt by more and more organizations:
- The weekly average number of ransomware attacks detected in June of 2021 was more than 149,000. A year prior, it was only 14,000 – making an increase of 966%
- Over one-third of businesses in the Automotive, MSSP, Government and Telecommunications industries and one-quarter nearly all other sectors experienced ransomware attacks
- The report noted that “the key takeaway is that ransomware is a clear and present danger regardless of industry or size.”
This data not only corroborates previously observed increases this year in the number of ransomware attacks, but helps to substantiate the kinds of organizations (the Fortinet report list more than 20 industry verticals) that are consistently being targeted and – therefore – should be proactively putting protective measures in place.
This should include security awareness training to enable your users to stop email-based attacks that successfully make it past a layered set of security filters designed to stop phishing, social engineering and malware in its tracks.
NIST recently updated Special Publication 800-53, Security and Privacy Controls for Information Systems and Organizations, adding some critical new language to the sections covering security awareness. The relevant language is within Section 3.2.
The updated NIST standard now includes providing frequent simulated social engineering testing. Specifically, their language states, “Practical exercises include no-notice social engineering attempts to collect information, gain unauthorized access, or simulate the adverse impact of opening malicious email attachments or invoking, via spear phishing attacks, malicious web links.”
This is a significant addition from NIST and is a formal recognition that phishing simulation vendors, like KnowBe4, are providing a much-needed security control. This behavior-based training is the key to building your effective last line of defense.
So, let’s examine the NIST recommendation in detail. CONTINUED:
https://blog.knowbe4.com/nist-updates-you-should-be-aware-about
Share
SEP








About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com