Phishing Email Alerts
Catch of the Day: Domain Name Search Phish
Chef’s Special: Geek Squad Renewal Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
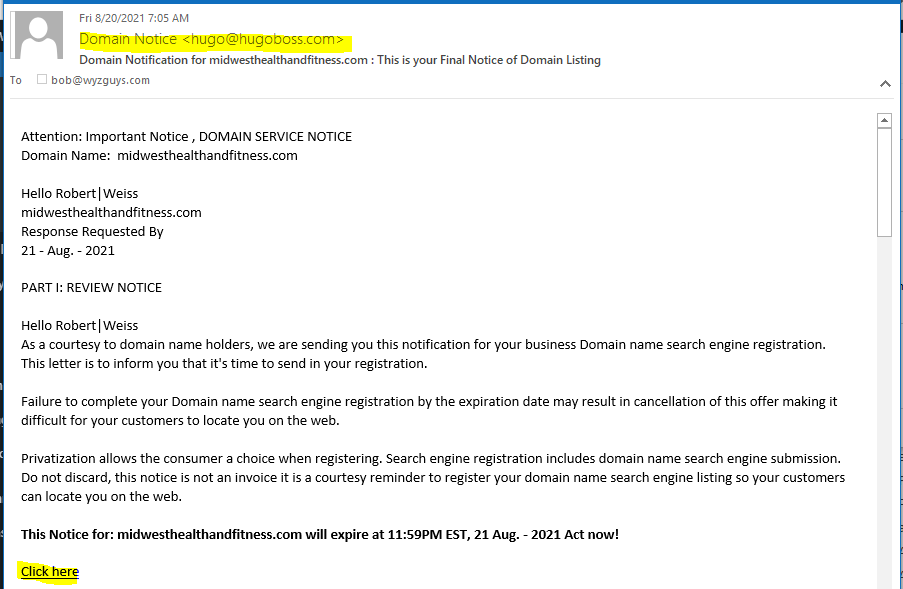
Domain Name Search Phish
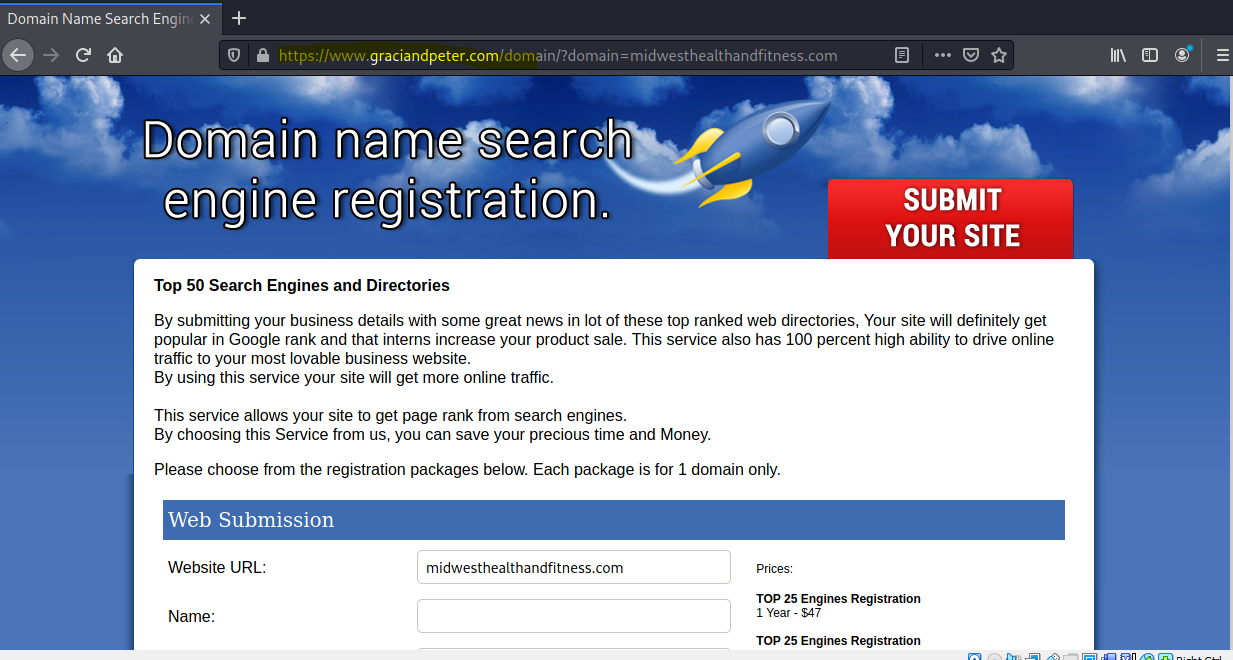
This is a pretty straight up scam to part you from your money. The company claims to list your domain with many “search engines” in order to improve your page rank.
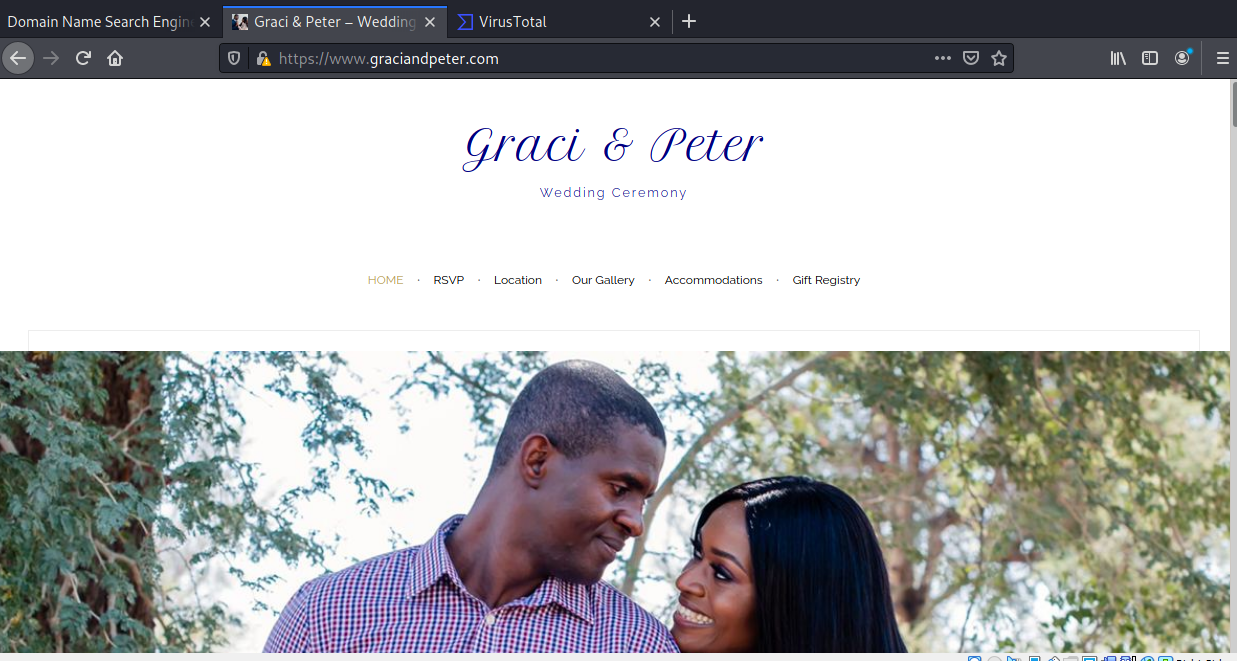
The sender is “Hugo Boss” from hugoboss.com. LOL. The Click here link resolves to https://www.graciandpeter.com/domain/?domain=midwesthealthandfitness.com.
The domain gracianadpeter.com is the unfortunately hijacked domain for a couple’s wedding website.
You are right to distrust sales pitches and offers like these. A “legitimate” search engine listing service would use their own domain name, as any business would.
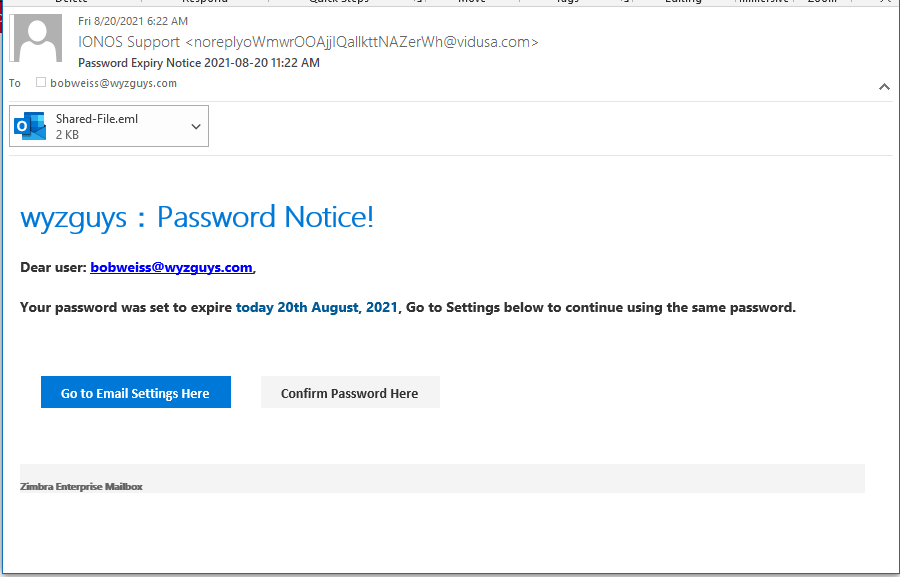
Password Expires Phish
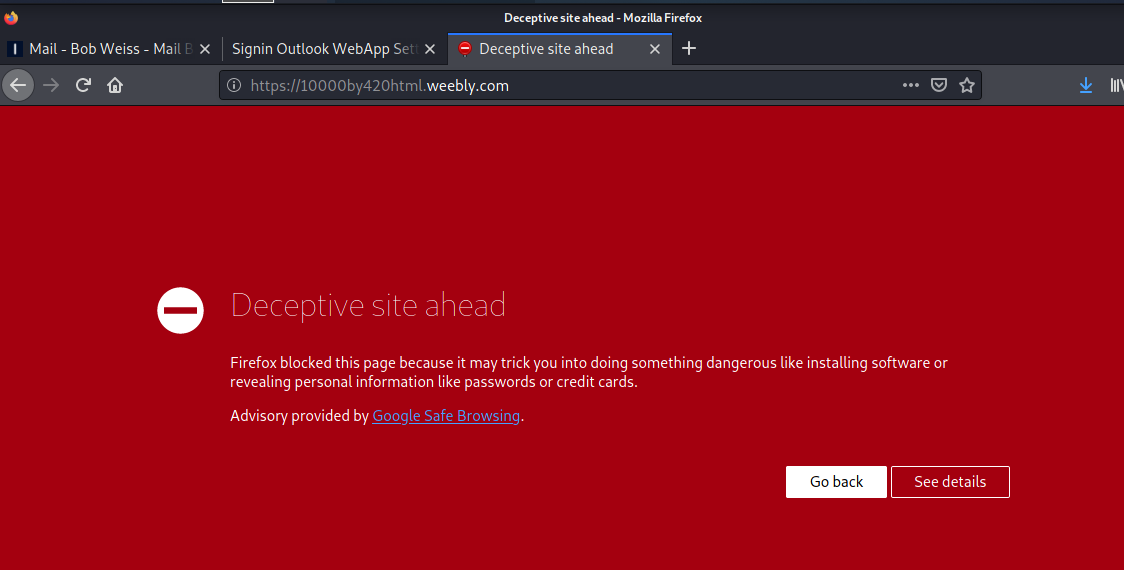
Here is a credential stealing phish from IONOS, but the landing page looks like it is for Weebly customers..
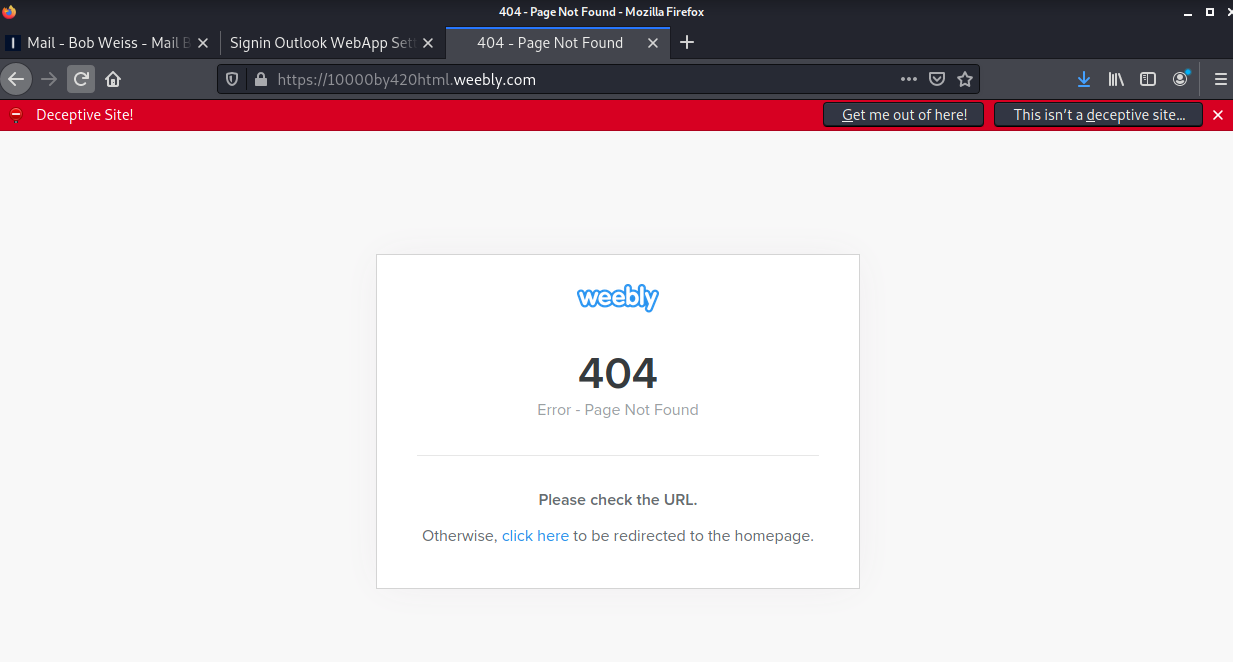
The links both resolve to https://10000by420html.weebly.com/. The attachment looks like this, and also resolves to the same Weebly address.
First there is a Firefox warning
And when pushing through to the landing page, a 404 not found :
This site was down before I had a chance to get to it, which highlights the ephemeral nature of these exploits.
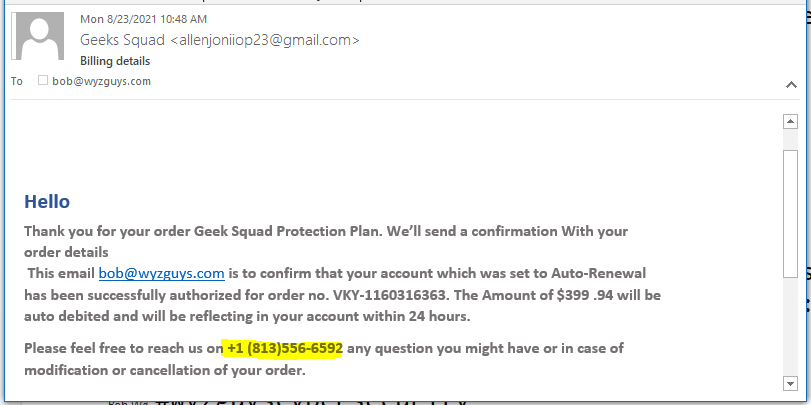
Geek Squad Renewal Phish
Supposedly I am being charged $300 to renew a plan I don’t have. The provided telephone number should connect me to the Social Engineering Squad.
The Anatomy Of New Smishing Attacks And How To Avoid Them
Cybercriminals and nation-state actors continue to launch new smishing attacks to steal credentials and distribute malware, according to Michael Marriott, Senior Strategy and Research Analyst at Digital Shadows. Marriott describes a new Android banking Trojan called “AbereBot” that’s being sold on cybercrime forums. Since the Trojan targets mobile devices, it’s distributed via text messages.
“This is just one recent example, and barely a month goes by without another Android malware making news headlines,” Marriott says. “Back in January, for example, FluBot was reported to have spread quickly and significantly across targets. This malware was installed by SMS, in this case purporting to be from a delivery company providing a package tracking link.
Users were prompted to download an application that would enable them to track the package, however, the malicious application enabled the attacker to capture banking credentials.”
Marriott cites advice from the UK’s National Cyber Security Centre (NCSC) on how to avoid falling for these scams:
- “Only download apps from App Stores, such as the Android Play Store.
- “If you suspect you have clicked on a malicious link, reset your device to factory settings and reset credentials of any accounts that you have entered since the infection.
- “Even non-Android users should be cautious of clicking on links that may be attempting to capture credentials.
- “Beware of unsolicited texts using high-pressure tactics that introduce urgency, such as closing accounts or transferring funds, for example. When in doubt, go to the full website of the company and check notifications for your accounts there.
- “Beware of anything that forces you to log in to unrelated services, such as entering banking credentials to receive a package.
- “Always treat a message offering ‘something for nothing,’ such as winning money or prizes, as suspect, especially when you need to provide financial or other sensitive information.”
New-school security awareness training enables your employees to recognize these types of social engineering attacks.
Blog post with links:
https://blog.knowbe4.com/the-anatomy-of-smishing-attacks-and-how-to-avoid-them
Microsoft: “Attackers Use Morse Code To Encode Phishing Attachments.”
A phishing campaign is using Morse code to encode malicious attachments in order to slip past security filters, according to researchers at Microsoft. The phishing emails contain HTML attachments designed to steal credentials.
“This phishing campaign exemplifies the modern email threat: sophisticated, evasive, and relentlessly evolving,” the researchers write. “The HTML attachment is divided into several segments, including the JavaScript files used to steal passwords, which are then encoded using various mechanisms.
These attackers moved from using plaintext HTML code to employing multiple encoding techniques, including old and unusual encryption methods like Morse code, to hide these attack segments. Some of these code segments are not even present in the attachment itself. Instead, they reside in various open directories and are called by encoded scripts.”
(Morse code is not, of course, really encryption. It’s just another alphabetical system, but nowadays only old-school ham radio fists are likely to be fluent in Morse. And so it can function like a cipher for those not in the know.) This technique gives the emails a better chance of bypassing security technologies, since the filters are less likely to recognize the attachments as malicious.
“In effect, the attachment is comparable to a jigsaw puzzle: on their own, the individual segments of the HTML file may appear harmless at the code level and may thus slip past conventional security solutions,” the researchers write. “Only when these segments are put together and properly decoded does the malicious intent show.”
CONTINUED:
https://blog.knowbe4.com/attackers-use-morse-code-to-encode-phishing-attachments
Share
AUG






About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com