Phishing Email Alerts
Catch of the Day: Quickbooks Phish
Chef’s Special: IONOS Login Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
Quickbooks Phish
We’ll never know what the end game was for this phishing exploit, as the landing page was already taken down by the host just 3 hours and 30 minutes after the email was received. Presumably so sort of credential theft of an Intuit account.
The link on the email resolved to https://s.id/DXPyx which displayed this 403 error page
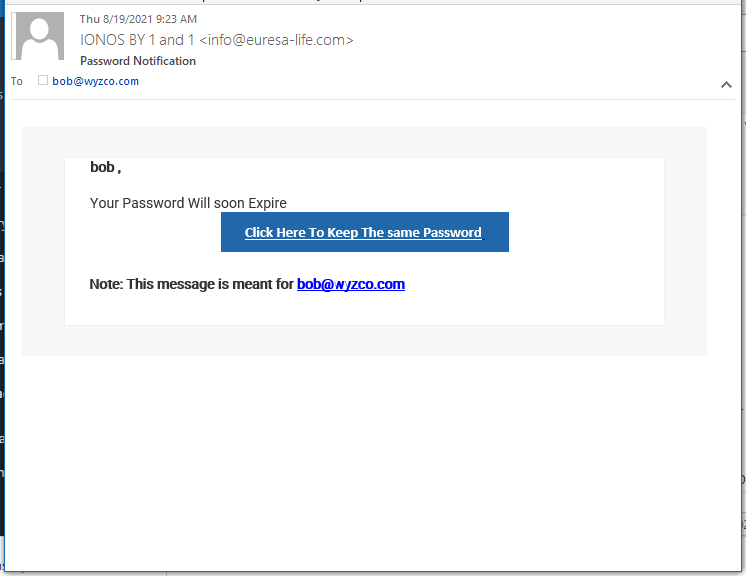
IONOS Login Phish
Here’s a credential stealer we’ve seen before. The sender’s email address is our first clue this is a phish.
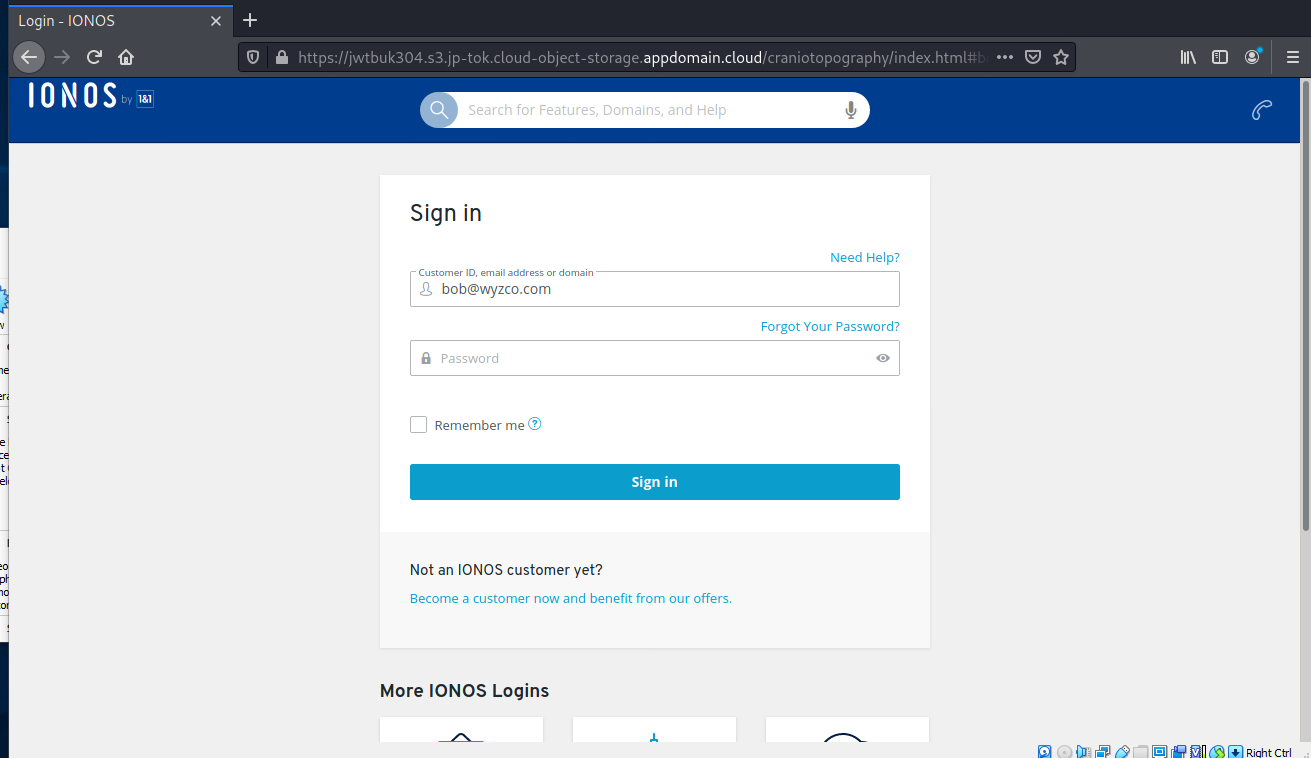
The Click Here To Keep The Same Password link resolves to https://jwtbuk304.s3.jp-tok.cloud-object-storage.appdomain.cloud/craniotopography/index.html#bob@wyzco.com
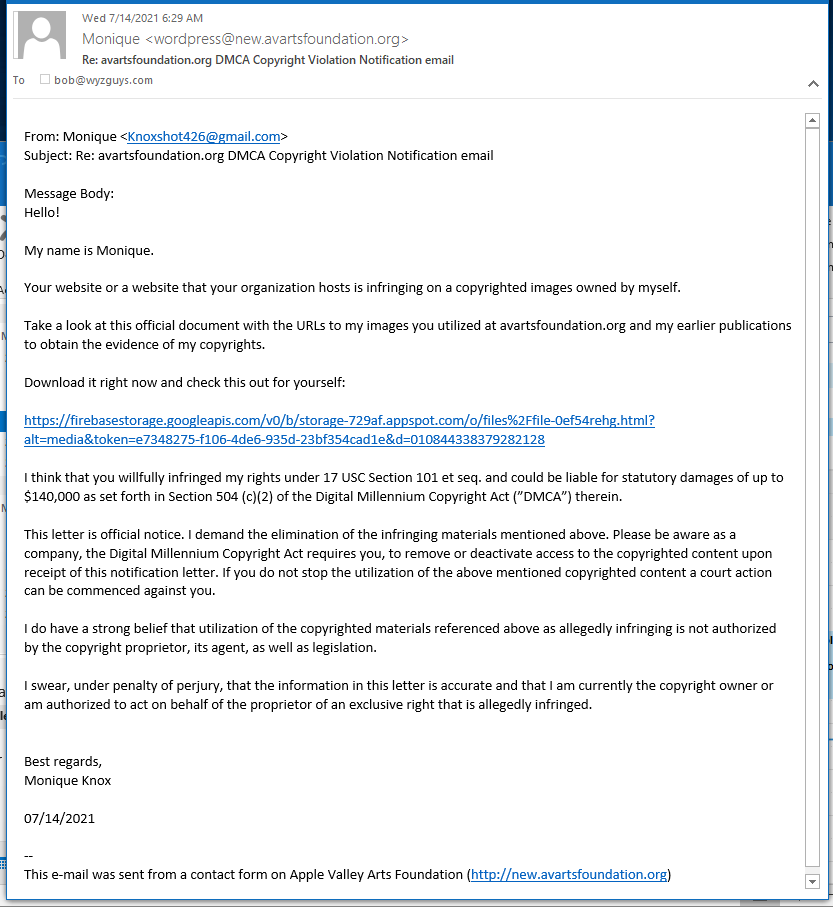
Copyright scammers turn to phone numbers instead of web links
Forewarned is forearmed. Here’s our advice on dealing with “copyright infringement” scammers. Read more…
Spear Phishing Becomes A Bigger Problem As The Average Org Is Targeted 700 Times A Year
With threat actors honing their trickery skills to craft the perfect email used to fool a would-be victim recipient, new data shows cybercriminals are stepping up their game on a number of fronts.
Spear phishing only works when the misleading email content is relevant to the recipient. It’s one of the reasons social engineering plays such a critical role in today’s email-based attacks. According to security vendor Barracuda’s latest report, Spear Phishing: Top Threats and Trends, organizations are experiencing far more convincing and impactful campaigns that are focused on a wider range of roles in the organization than ever before:
- 1 in 10 attacks are Business Email Compromise (BEC) attacks
- 77% of BEC attacks target employees outside of finance and executive roles
- Even so, the average CEO receives 57 targeted phishing attacks each year
- IT staff still receive an average of 40 per year
- Microsoft remains the top impersonated brand with WeTransfer in at number two
According to Barracuda, the roles targeted within an organization extend well-beyond that of the CEO or IT, making every employee a potential target. There is an interesting graph that shows the different employee groups and the attacks per mailbox at the KnowBe4 blog:
https://blog.knowbe4.com/spear-phishing-becomes-a-bigger-problem-as-the-average-organization-is-targeted-700-times-a-year
Share
AUG







About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com