Happy Friday the 13th
Phishing Email Alerts
Catch of the Day:
Chef’s Special:
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
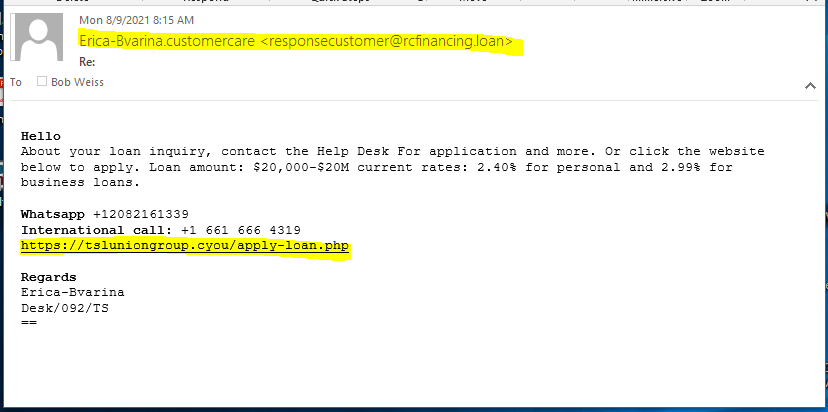
TS Financial Services Phish
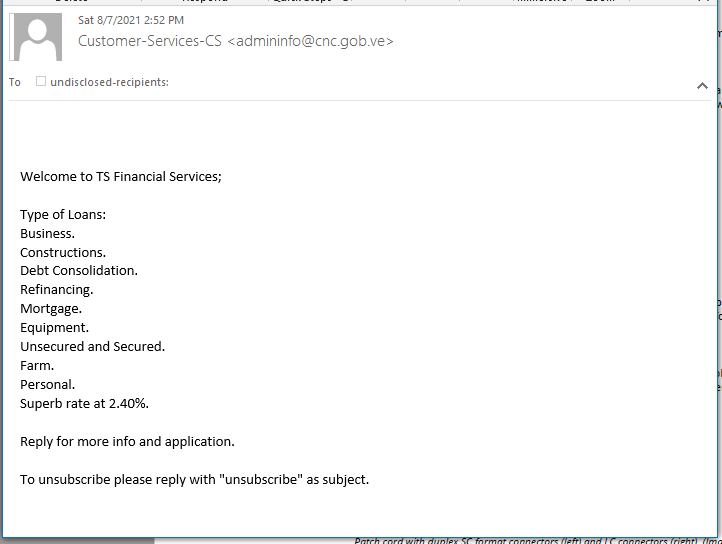
This email was very brief, not much of a story. But the email of the sender is not spoofed, it is evidently hijacked, and it is on a legitimate government domain for Venezuela. I found this curious .
Here’s the phishing email:
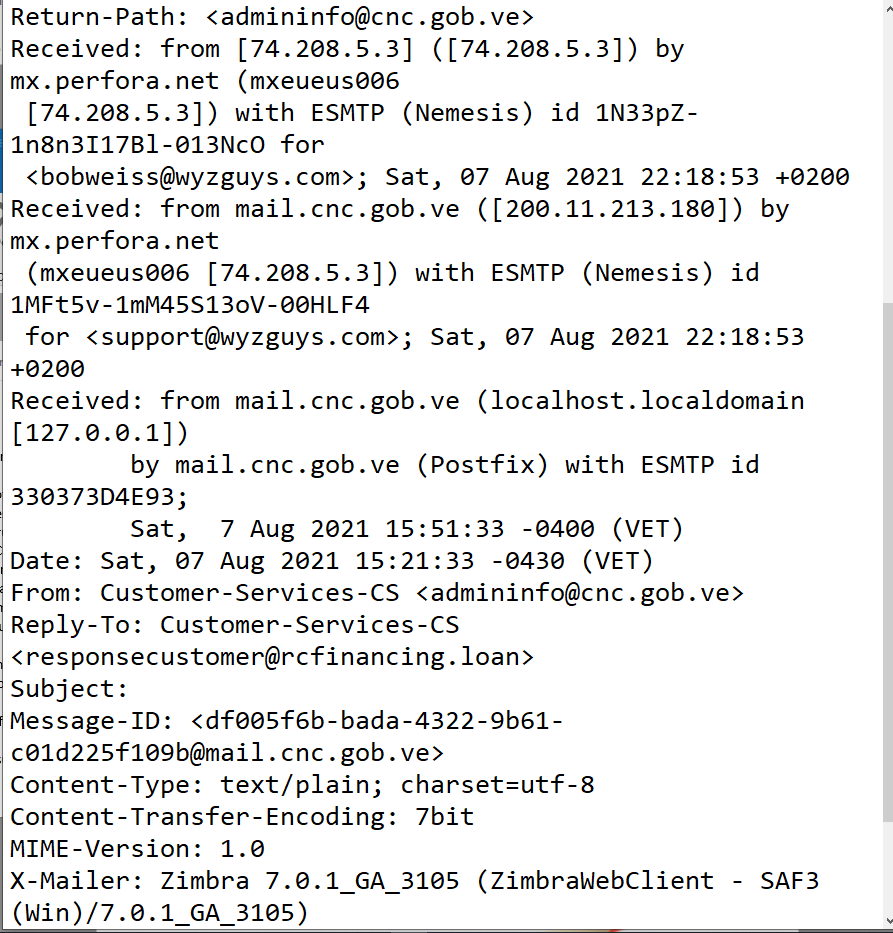
The email headers validate the senders email address as valid.
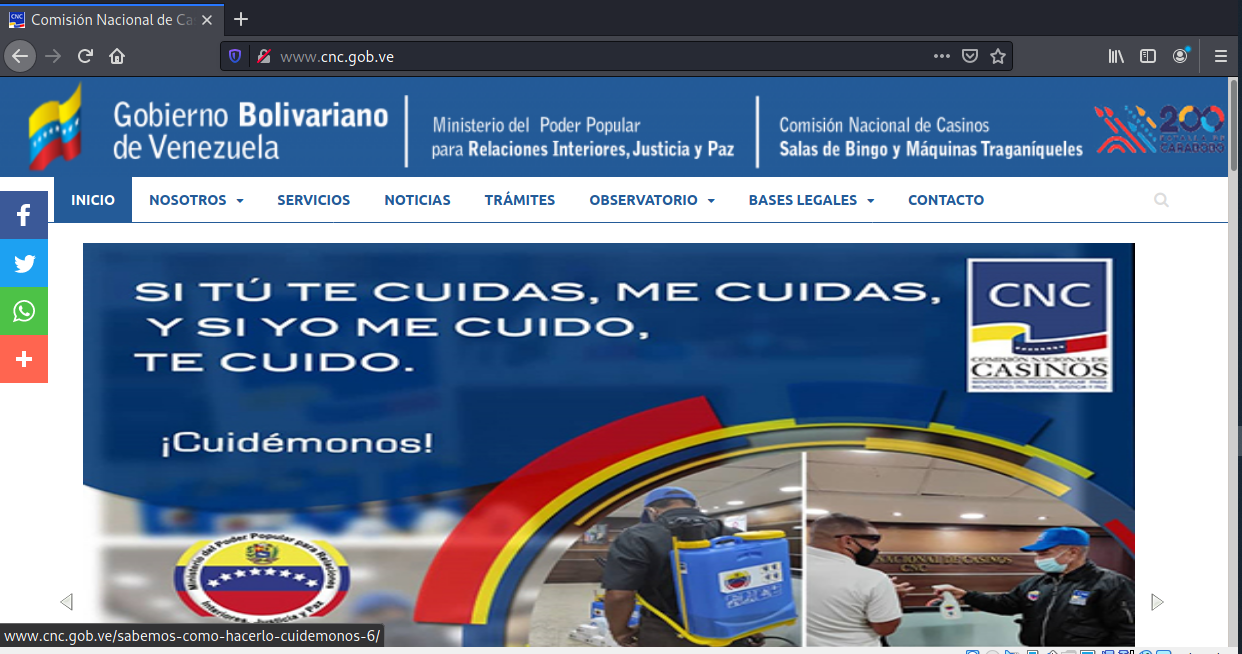
I tried to use the email domain cnc.gob.ve as a URL and this is what I found – a governmental website for Venezuela.
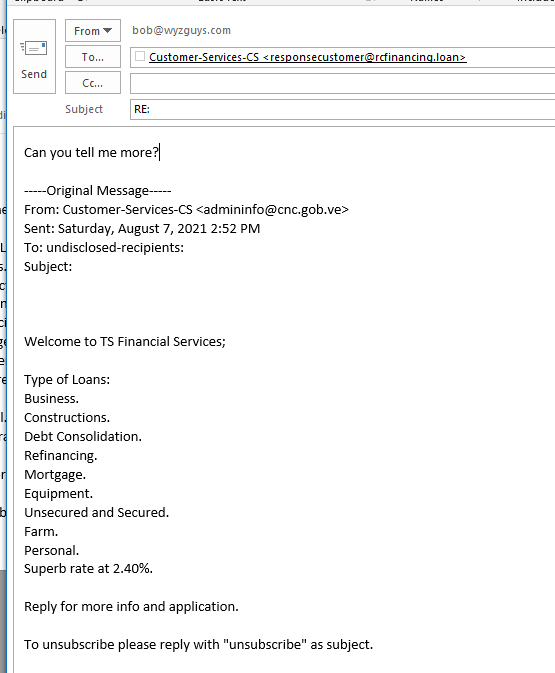
Since there were no links to click, I did what I could – I replied to the email. I suspect the response and resulting dialog could be interesting.
So here is the response. This time with a link.
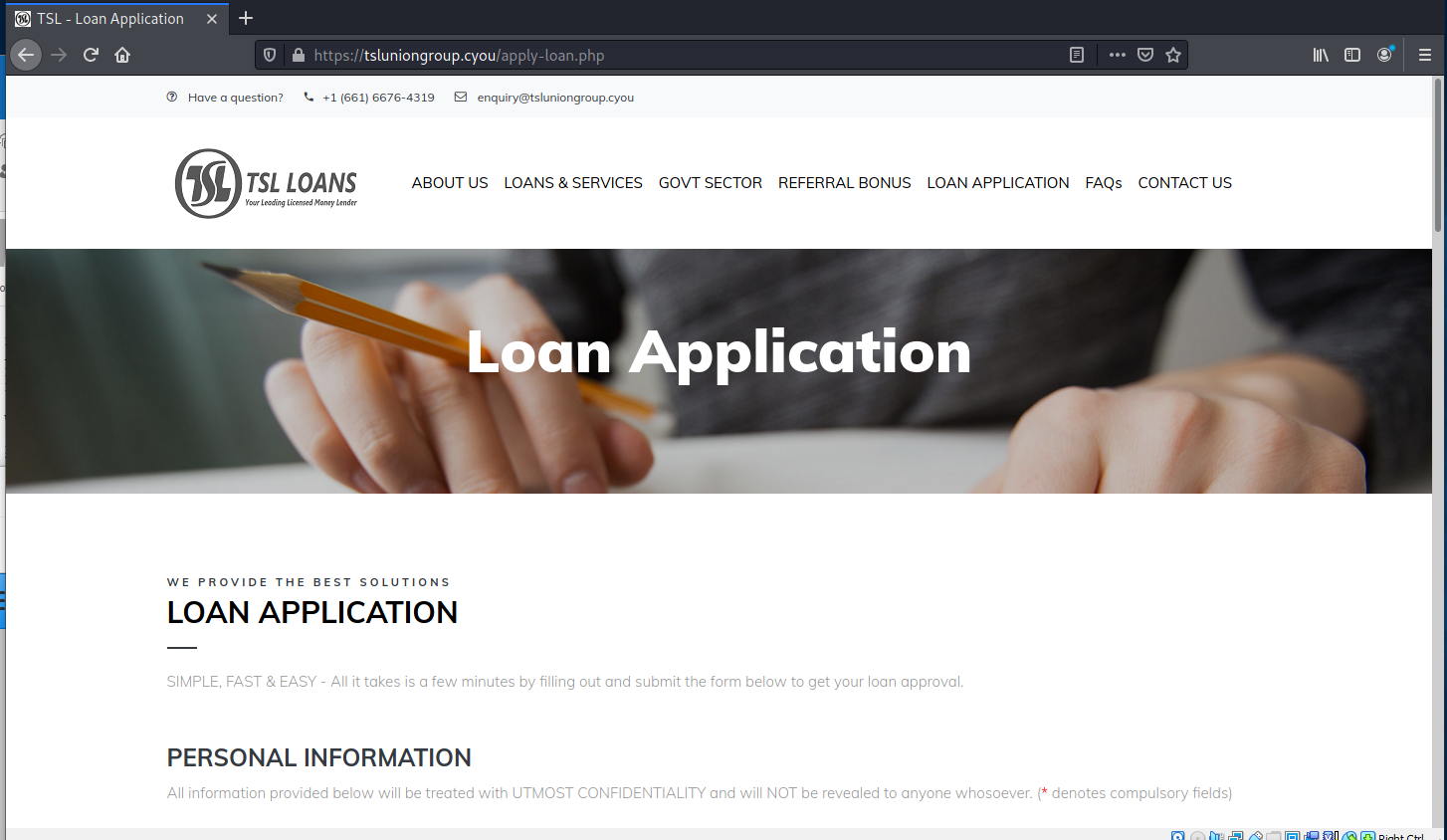
The link goes to a website with an application form. Why would you give this much personal information to a total stranger. This looks like a PII stealing, identity-theft type of operation to me.
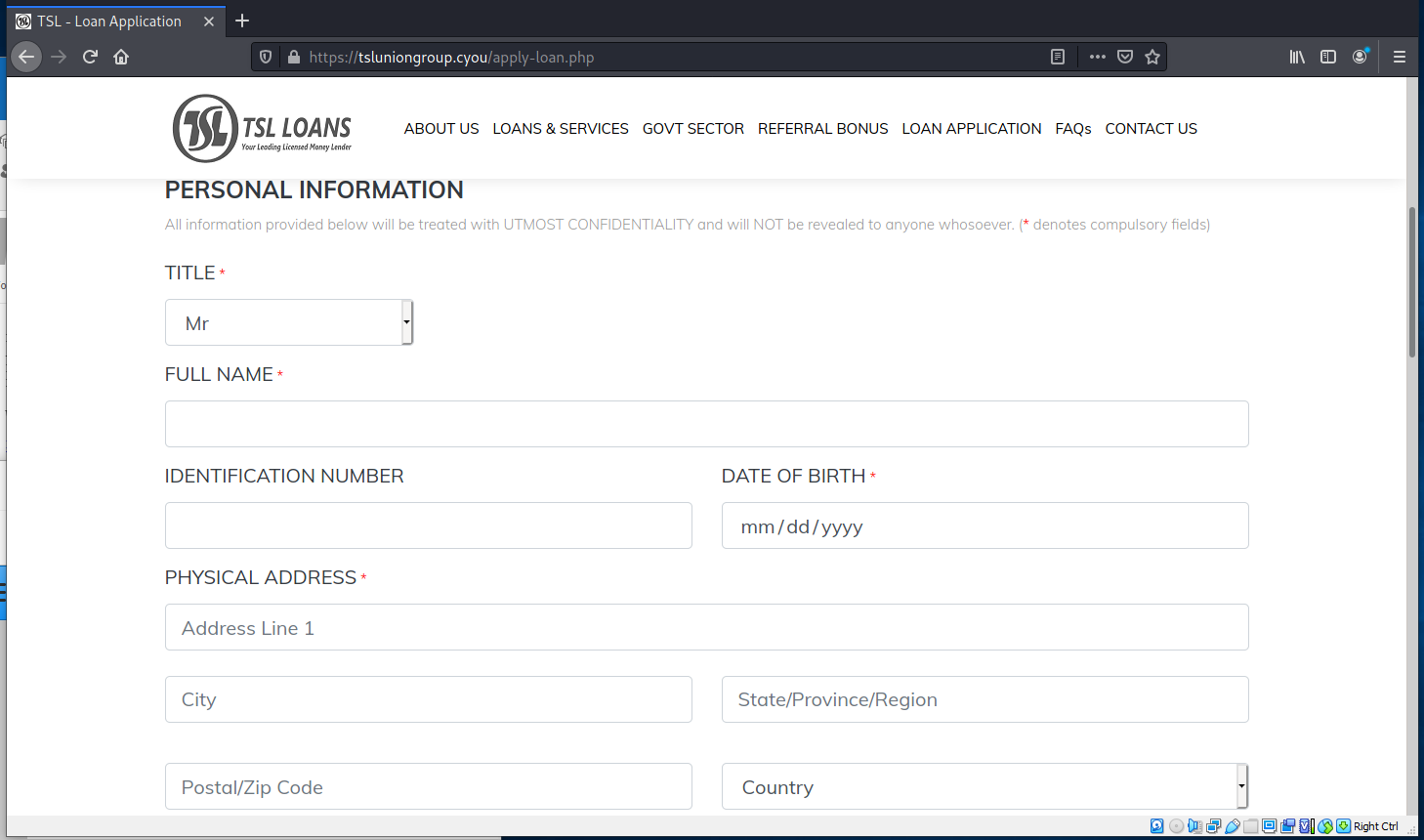
I included the landing pages and two pages worth of form. There was a lot more information they were asking for.
Don’t Have A Heart-Attack Over This Phish
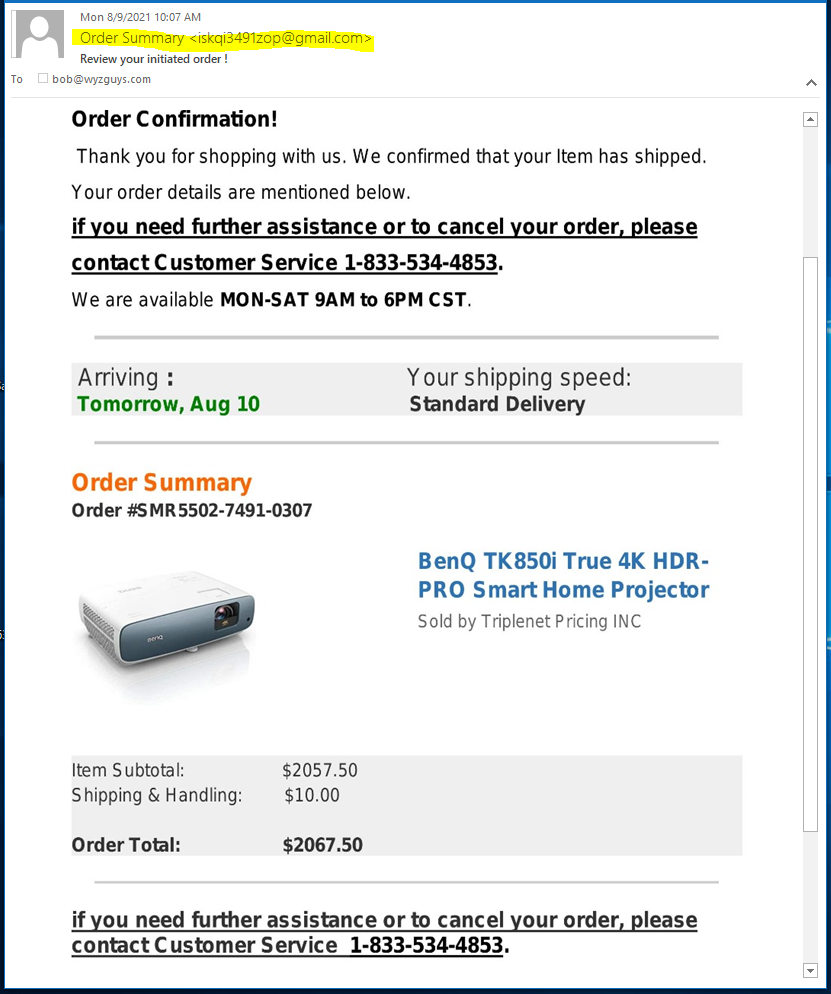
This is at least the third one of these Amazon Order Confirmations that I have received. Graphically very realistic, but completely fake. Check the senders email address (highlighted). Calling the toll-free number to dispute this purchase can only be bad for you. Evidently the cyber-crooks have determined that two grand will get people motivated enough to call the toll free number.
When you get these sorts of “invoices,” just log into your Amazon (or whoever) account to check if there was even a purchase like that made. And remember your credit card company will protect you from dollar one in the event of fraudulent use. These are bogus. Just delete them.
Microsoft Warns of Sneaky Phishing Campaign
Microsoft’s Security Intelligence team recently sent an alert to Office 365 users and admins to watch out for a suspicious phishing email that uses spoofed sender addresses.
The alert was sent after observing an active campaign that was zoning in on Office 365 organizations with convincing emails.
In a statement by Microsoft, “An active phishing campaign is using a crafty combination of legitimate-looking original sender email addresses, spoofed display sender addresses that contain the target usernames and domains, and display names that mimic legitimate services to try and slip through email filters.”
Microsoft notes that this campaign is sneakier than usual due to the convincing Microsoft logos with the link posing as a ‘file share’ request to access bogus reports. However, the main phishing URL relies on a Google storage resource that takes the victim to the Google App Engine domain Appspot. This results in hiding a second URL that directs the victim to a compromised SharePoint site, and thus allowing the attack to bypass sandboxes.
Our blog has the rest of the alert with the specific example of the phishing page:
https://blog.knowbe4.com/heads-up-microsoft-warns-of-sneaky-phishing-campaign
New Phishing Campaign Uses Blackmail to Lure Victims
Bitdefender has observed a phishing campaign that tries to blackmail users into sending money by claiming their computer has been hacked. The emails contain real passwords that have been leaked, in order to convince the recipient that the claims are legitimate.
“In this case, spammers attempt to fool recipients by referring to old passwords and existing email addresses, most of which have already been exposed online,” Bitdefender says. “The perps specify that login credentials to your online accounts were purchased from the web and used to install malicious software and spyware on your device.
“They use scare tactics to induce a sense of panic in recipients, threatening to expose a video montage containing lewd scenes of victims watching adult videos online to friends and family.”
The researchers note that this technique isn’t new, but the scale of the campaign is significant. “The attacks spread across the globe, with unusually high numbers of spam emails reaching users in Romania (over 400,000 emails), Italy and the Netherlands,” the researchers write. “The messages originate from multiple IP addresses in Europe, Asia, Africa and the Americas. It seems they’ve been distributed in masses via a large spam botnet controlled by the same threat group.”
Blog post with Bitdefender recommendations and links:
https://blog.knowbe4.com/new-phishing-campaign-uses-blackmail-to-lure-victims
Share
AUG





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com