Phishing Email Alerts
Catch of the Day: Microsoft Invoice Phish
Chef’s Special: Home Delivery Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
Microsoft Invoice Phish
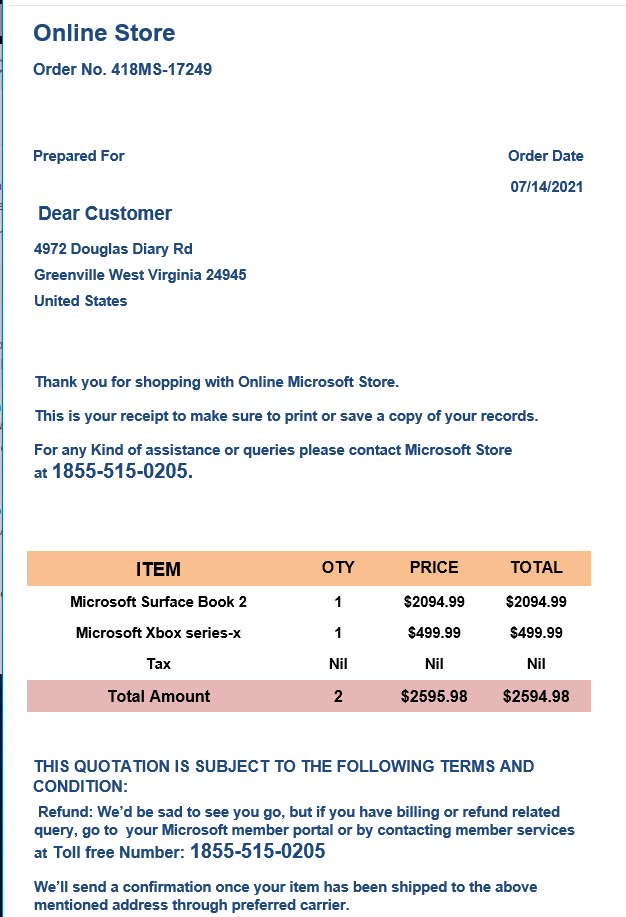
This email was forwarded to me by a client who called to check if I thought this email was a fake. First lesson: teach your clients to doubt the email, call tech support, and forward the email to tech support.
This is a bit of a phishing/vishing/social engineering hybrid exploit. The email with the fairly significant total of $2594,98 is designed to get most people up off their keister and dialing the phone to the repetitively offered toll free number. The goal I am sure is to get the target to supply their credit card and other personal information in order to process the “refund.”
There are a lot of things missing that should tip off the wary that this is fake. The lack of personalization where it clearly belongs. “Dear Customer.” No credit card information on the receipt, there should be at least a partially redacted card number showing the last 4 digits. The lack of sales tax (Nil).
You should always check your bank accounts, credit card accounts, and other payment systems like PayPal and Venmo for recent unexpected activity that corresponds to the alleged charges. My client did not see any charges, which was the real confirmation that this invoice is just a scam.
Here’s an image of the email:
Home delivery scams get smarter – don’t get caught out
We’ve said it before, and we’ll say it again: don’t be in too much of a hurry for those home deliveries you’re expecting! Click the link for the full article including images of the phishing and smishing messages. This scam shows European the delivery carrier DPD. Here in the US it would most likely be UPS, FedEx, and USPS being used.
Live Phishing Attack Uses New Infection Technique to Deliver Malware
Researchers at McAfee warn that a current phishing campaign is delivering malware via Word documents that don’t contain any malicious code. When a user opens the document and enables content, the document will download an Excel file that’s used to construct a malicious macro after the documents are on the system. This helps the macros bypass security filters.
“The malware arrives through a phishing email containing a Microsoft Word document as an attachment,” the researchers write. “When the document is opened and macros are enabled, the Word document, in turn, downloads and opens another password-protected Microsoft Excel document. More…
Spear Phishing Campaign Targets Energy Companies
Researchers at Intezer have spotted a phishing campaign that’s targeting energy companies in South Korea, the United States, the United Arab Emirates, and Germany. Most of the targets are located in South Korea.
“The attackers use typosquatted and spoofed emails to launch the attack,” the researchers write. “The campaign spreads via phishing emails tailored to employees at each company being targeted. The contents and sender of the emails are made to look like they are being sent from another company in the relevant industry offering a business partnership or opportunity More…
Share
JUL





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com