Phishing Email Alerts
Catch of the Day: Porn Extorsion Phish
Chef’s Special: DocuSign Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
Porn Extorsion Phish
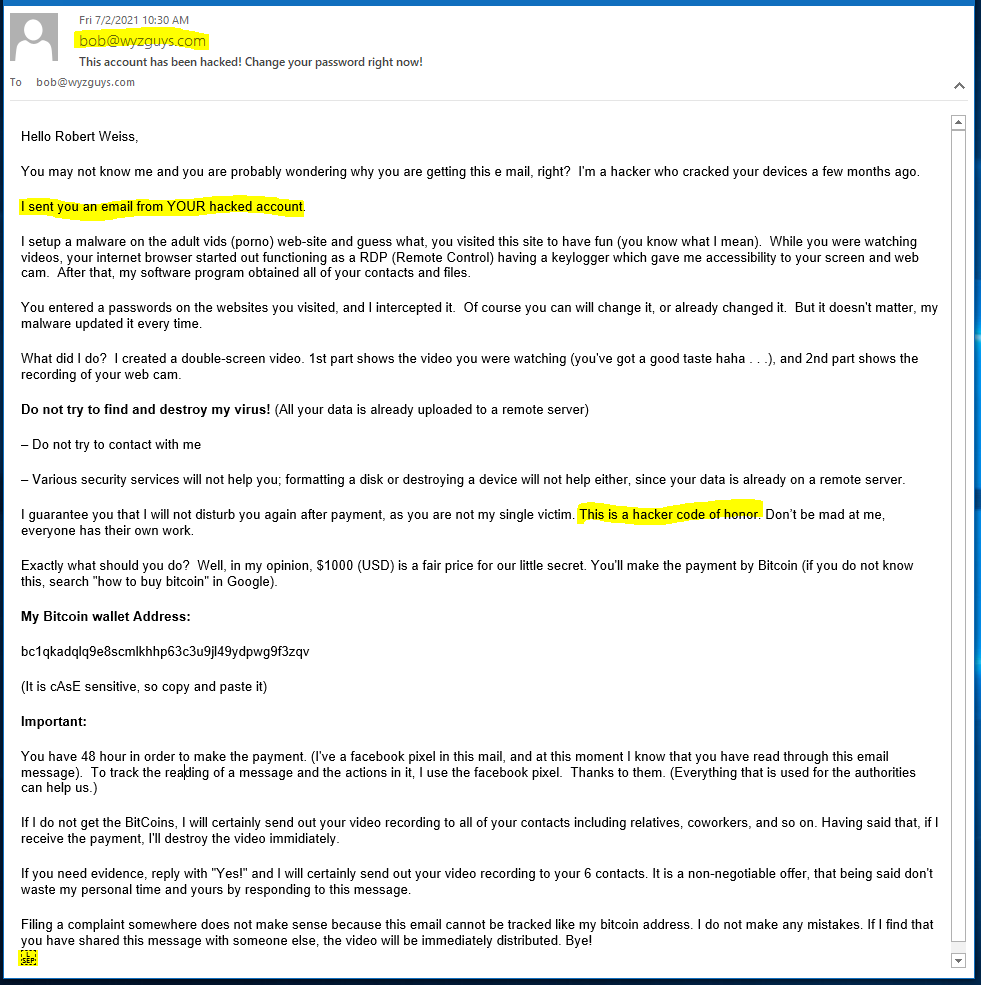
Here’s another example of a pornography extorsion scam. All I can say is these are FAKE FAKE FAKE. A good preventive security measure is to do your personal business on a computer without a camera, or cover the camera when not using it. This is just plain good advice, because there are lots of malware tools that can take over your web cam and record what is in the field of view. If your laptop is in your bedroom, or if working from home means clothing optional, then using your web cam with care is a good idea.
So let’s pick apart what we can learn about this exploit. Here’s an image of the original email. I edited it somewhat by removing line-breaks to fit all the content on the page.
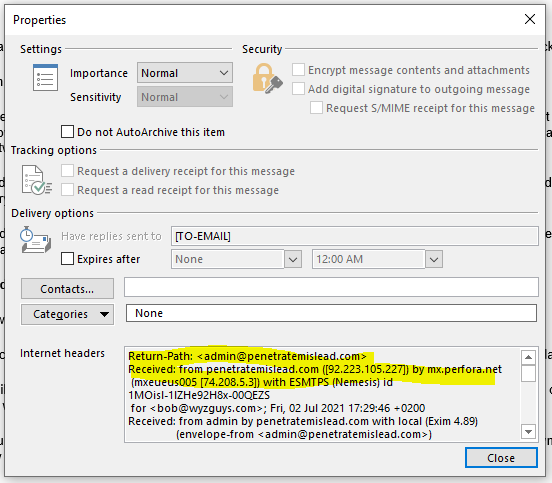
The sender email address is spoofed to look like it came from my own (hacked) account, but a quick check of the email hears identified the sender as admin@penetratemislead.com. More on that later.
The attacker assures you that this will be the only extorsion because of the hacker code of honor. ROFLMAO! Code of honor, I’m sure. If you were foolish enough to pay this crook once, I am sure they will return with further threats of exposure, or some new exploit.
Now let’s look at the email headers.
Email headers
Return-Path: <admin@penetratemislead.com>
Received: from penetratemislead.com ([92.223.105.227]) by mx.perfora.net
(mxeueus005 [74.208.5.3]) with ESMTPS (Nemesis) id 1MOisl-1lZHe92H8x-00QEZS
for <bob@wyzguys.com>; Fri, 02 Jul 2021 17:29:46 +0200
Received: from admin by penetratemislead.com with local (Exim 4.89)
(envelope-from <admin@penetratemislead.com>)
id 1lzL6v-00027t-3N
for bob@wyzguys.com; Fri, 02 Jul 2021 15:29:45 +0000
To: bob@wyzguys.com
Subject: This account has been hacked! Change your password right now!
My email address was spoofed to appear as if I were the sender. But the sender (Return-Path) is admin@penetratemislead.com. This means his claim to have hacked my email account is bogus. Another way to send an email like this so it looks like it came from your account is to submit it from a web form on your website. We have already seen examples of this. Don’t fall for either method.
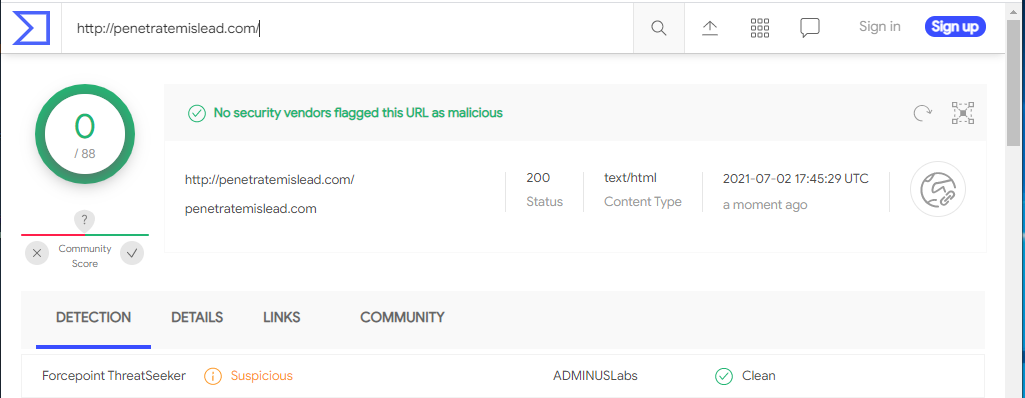
Checking the email domain on VirusTotal showed the domain as suspicious.
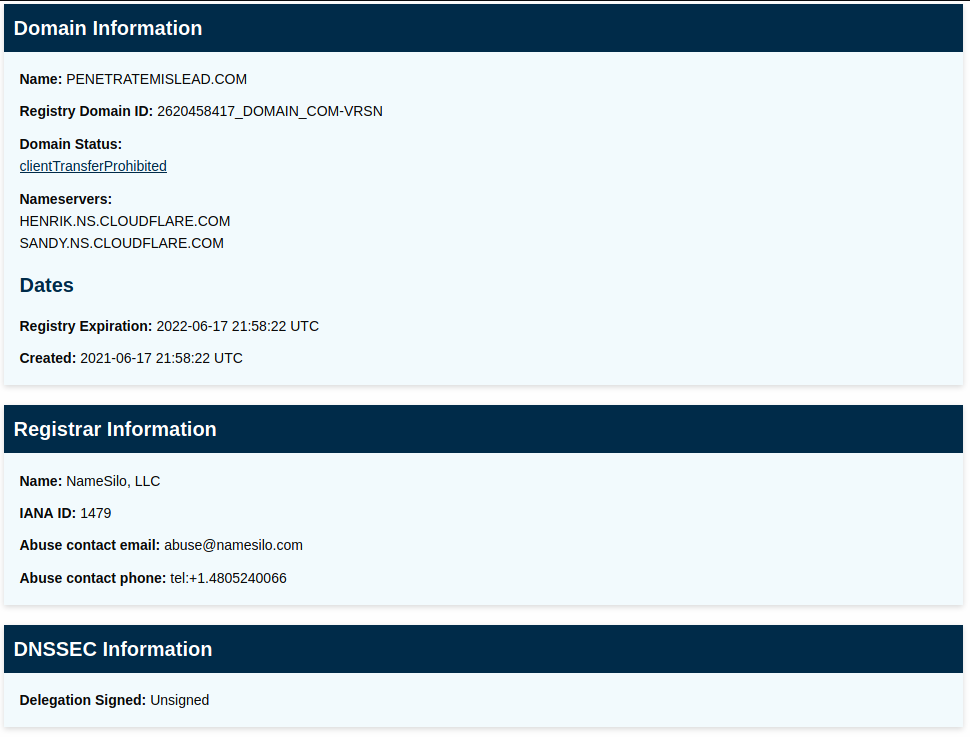
So I gave it a quick lookup on ICANN WhoIs. We can see that the domain name was recently registered 0n 2021-06-17 through NameSilo,LLC
NmaeSilo is a inexpensive domain name registrar headquartered in the US, but owned by a Canadian company.
I decided to see if there was a website for penetratemislead and there was, but not too much of a home page yet. Not really necessary for this type of exploit.
So this is pretty much what I could fine out about the source of this email. I am thinking about inviting admin@penetratemislead.com to read this article when it publishes on July 9.
DocuSign Phish
What’s this one all about? I’m not sure. Looks like a fairly straightforward credential stealing exploit, and ends up looking like an affiliate marketing ploy for a payroll app called Gusto. You be the judge.
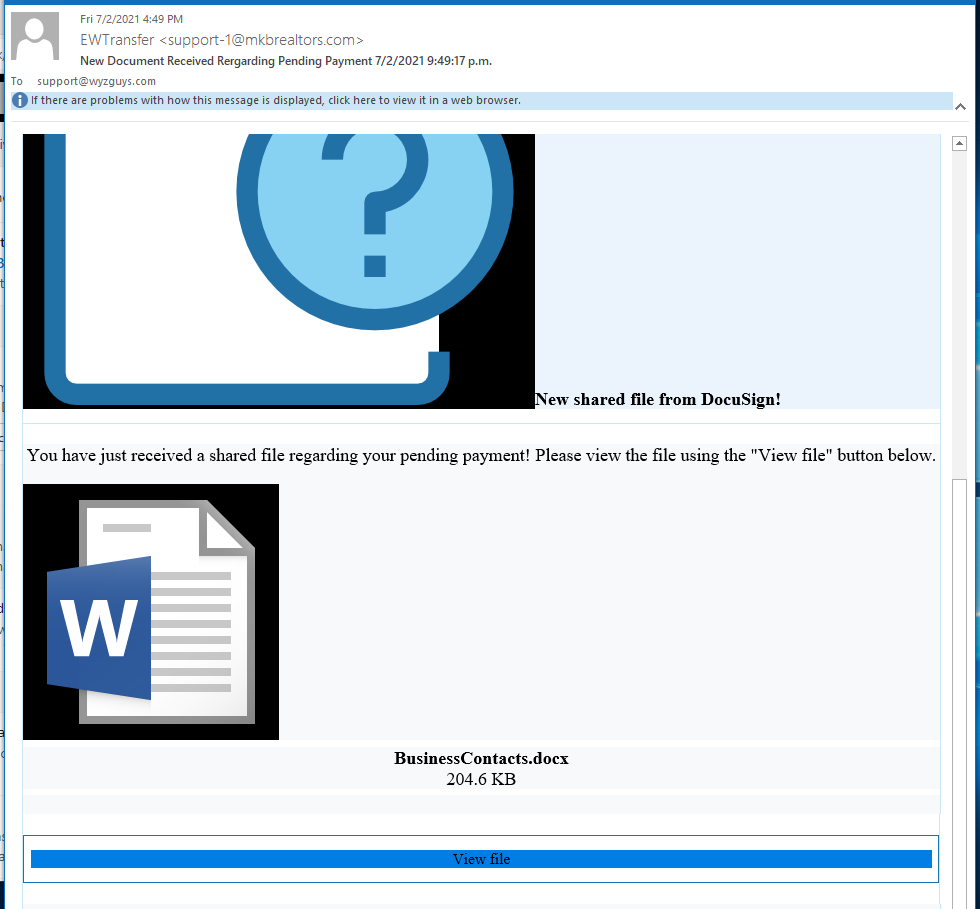
Here’s the initial email, image sizing was poorly done, which meant I had to crop the top off the email to get it all to fit on my screen. The sender is supposedly a realty company (mkbrealtors.com) in Roanoke VA. The realty appears to be legit and has a nice website. So, this email appears to have come from a legitimate but hijacked email account, or perhaps an email account added by the attacker to a compromised email server. A check on MX Toolbox showed the legitimate email server to be elsewhere than 74.208.5.3.
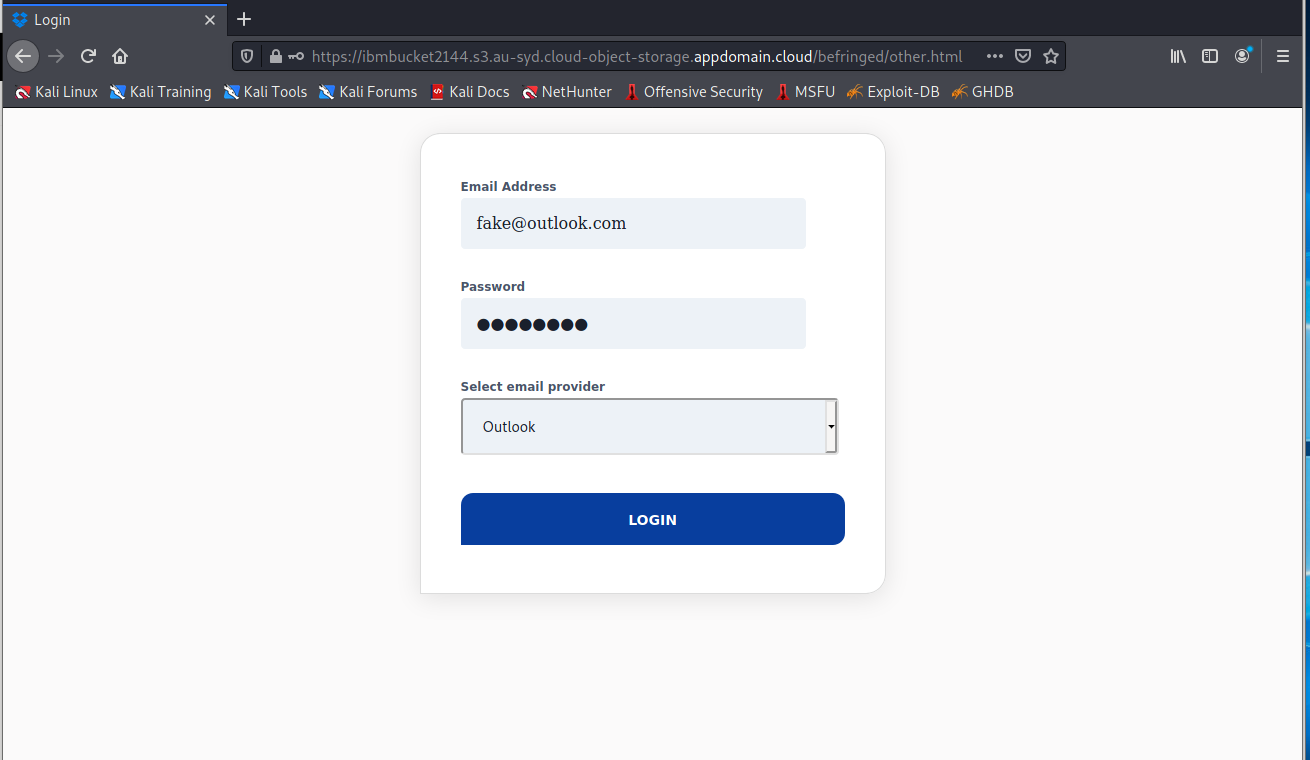
The View File button resolved to https://ibmbucket2144.s3.au-syd.cloud-object-storage.appdomain.cloud/befringed/index.html, which is the web page below.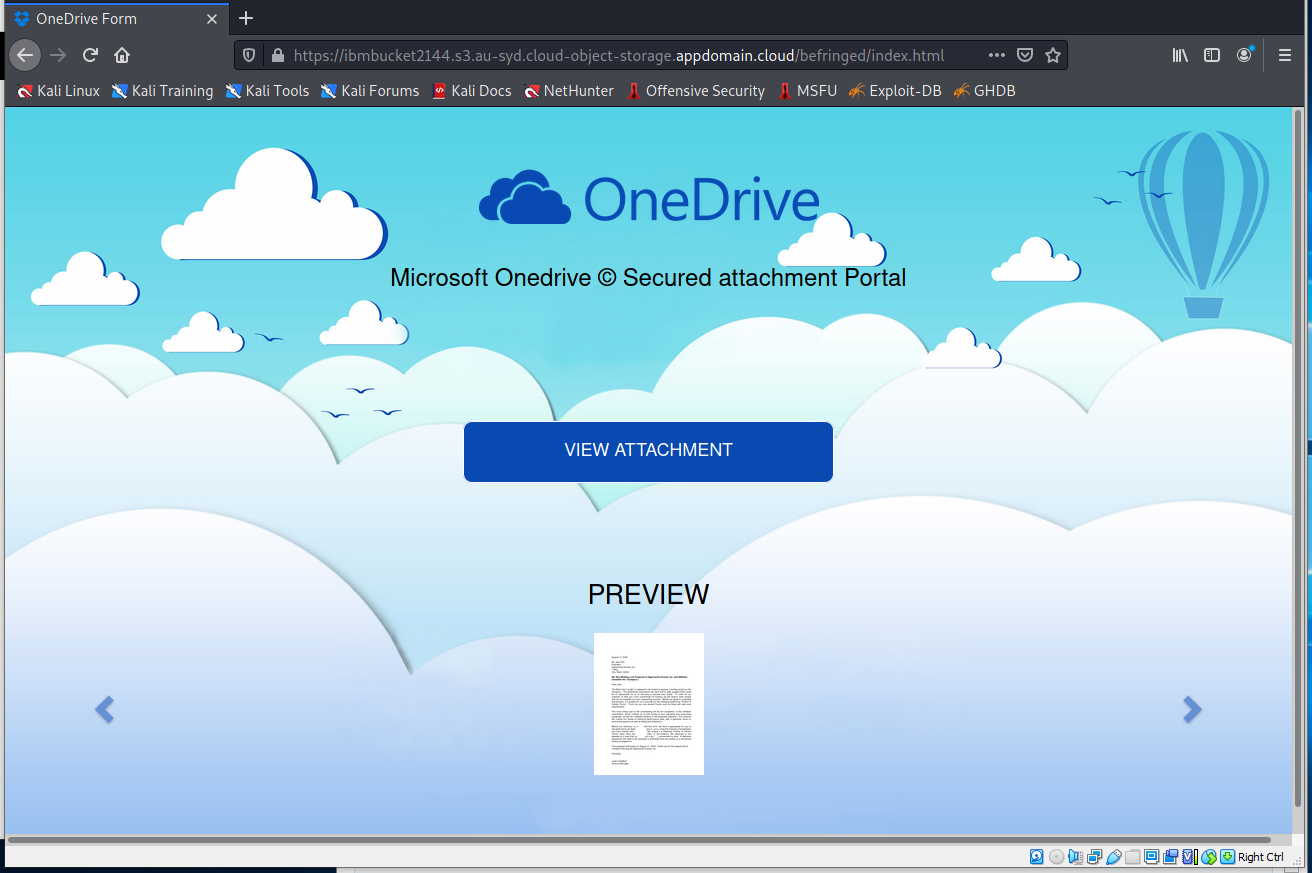
Clicking VIEW ATTACHMENT brought me to this screen.
Continuing brought up this login screen. Seems like credential stealing at this point.
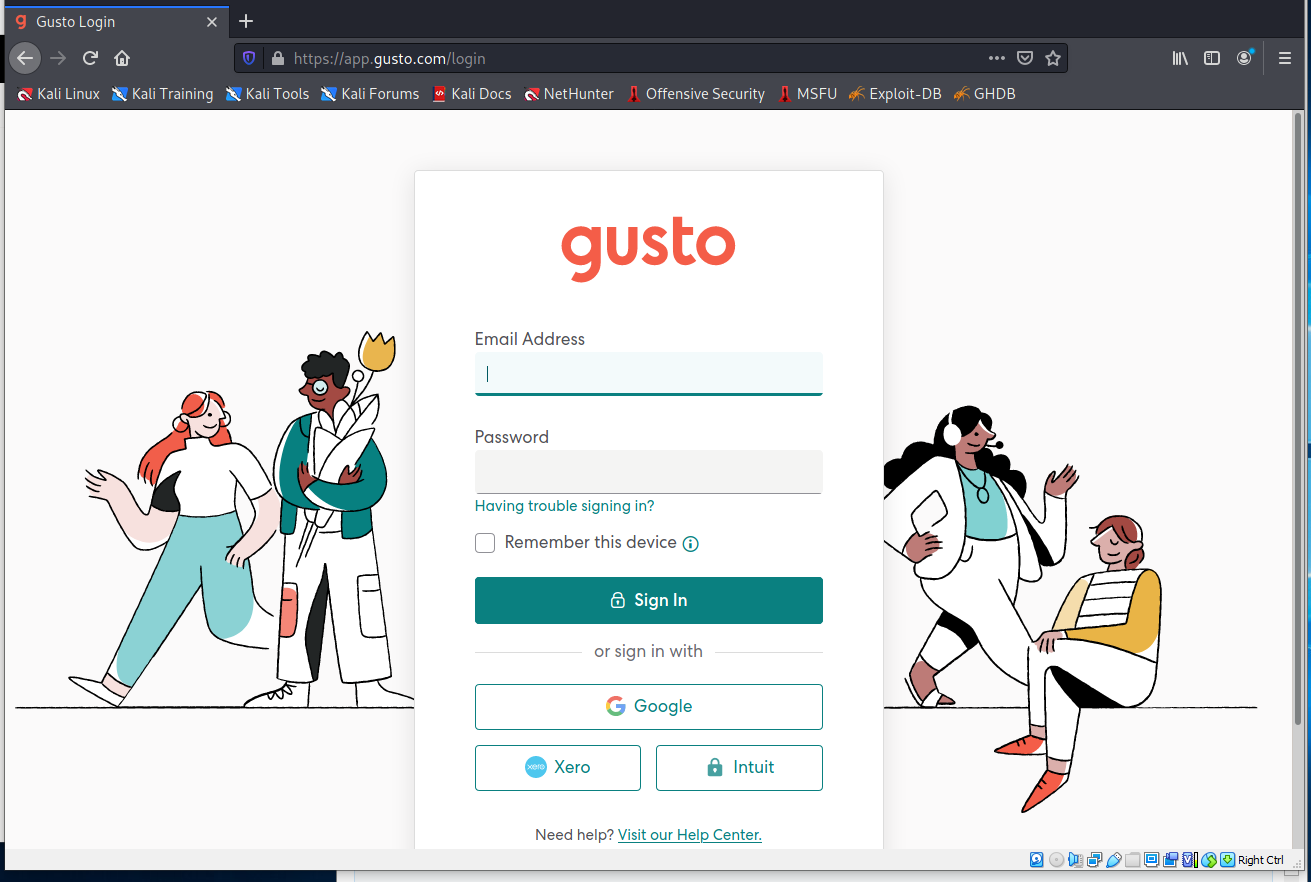
The next screen was a bit of a surprise. Another login screen, for a web service called Gusto.
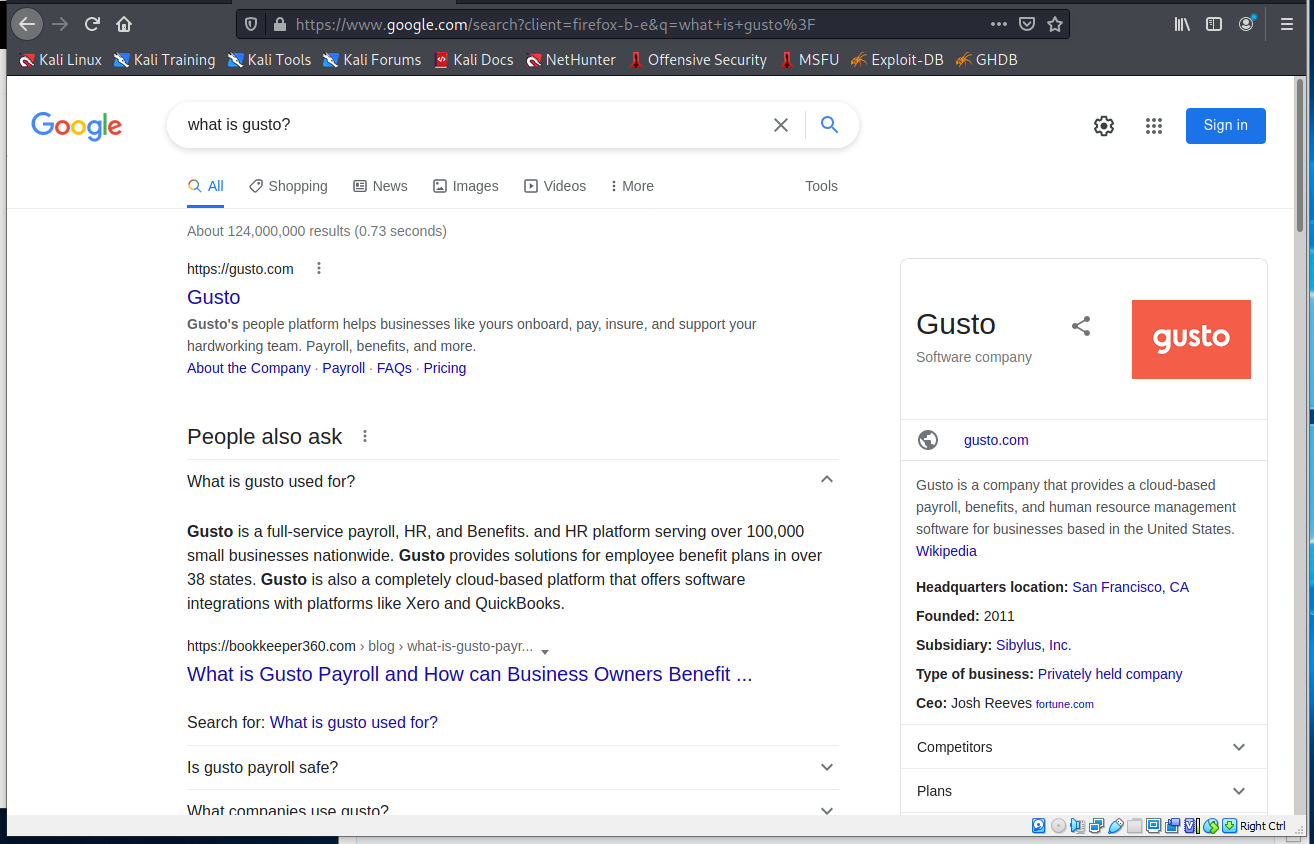
I have not heard of Gusto, but a quick Google search told me that Gusto is an online payroll application. So I am not entirely sure what the end-game is here. If any of you have chased this one, I would be interested in your conclusions. Please submit as a comment.
Gusto is a full-service payroll, HR, and Benefits. and HR platform serving over 100,000 small businesses nationwide. Gusto provides solutions for employee benefit plans in over 38 states. Gusto is also a completely cloud-based platform that offers software integrations with platforms like Xero and QuickBooks.
Is this some sort of convoluted affiliate marketing scheme, or credential stealing. What do you think?
Office365 File Share Phish
This exploit is similar to the one above, with the exception that it is very well done. Clearly a credential stealing exploit for Office365 accounts.
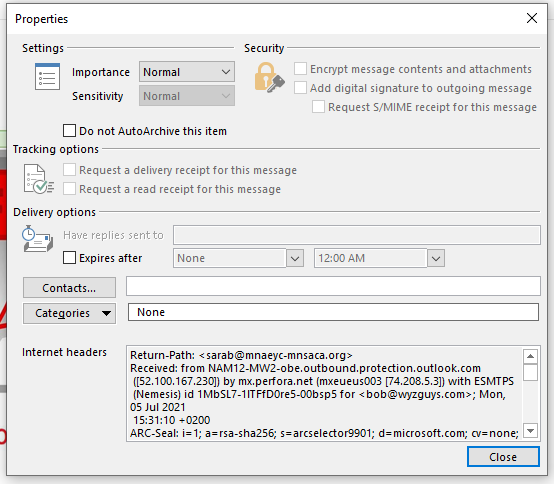
The sending account of this email is one for Sara Benzkofer. The email account and the email domain both appear to be legitimate, although according to Sara’s LinkedIn profile, she left MNSACA last year. So the first question is why is her email account still active? Poor account management practices by MNSACA’s IT department is the probable answer. So this looks like a hijacked email account for a user who is no longer employed by the non-profit. Here are the email headers:
Return-Path: <sarab@mnaeyc-mnsaca.org>
Received: from NAM12-MW2-obe.outbound.protection.outlook.com
([52.100.167.230]) by mx.perfora.net (mxeueus003 [74.208.5.3]) with ESMTPS
(Nemesis) id 1MbSL7-1lTFfD0re5-00bsp5 for <bob@wyzguys.com>; Mon, 05 Jul 2021
15:31:10 +0200
The non-profit organization MNEEYC-MNSACA appears to be a legitimate organization as well. Here’s their home page.
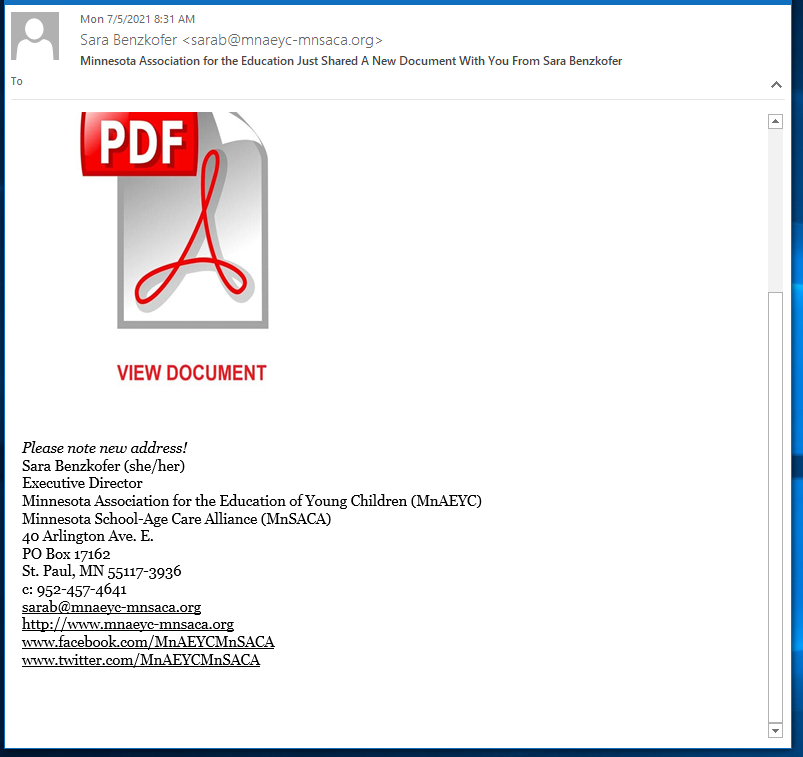
The phishing email is below.
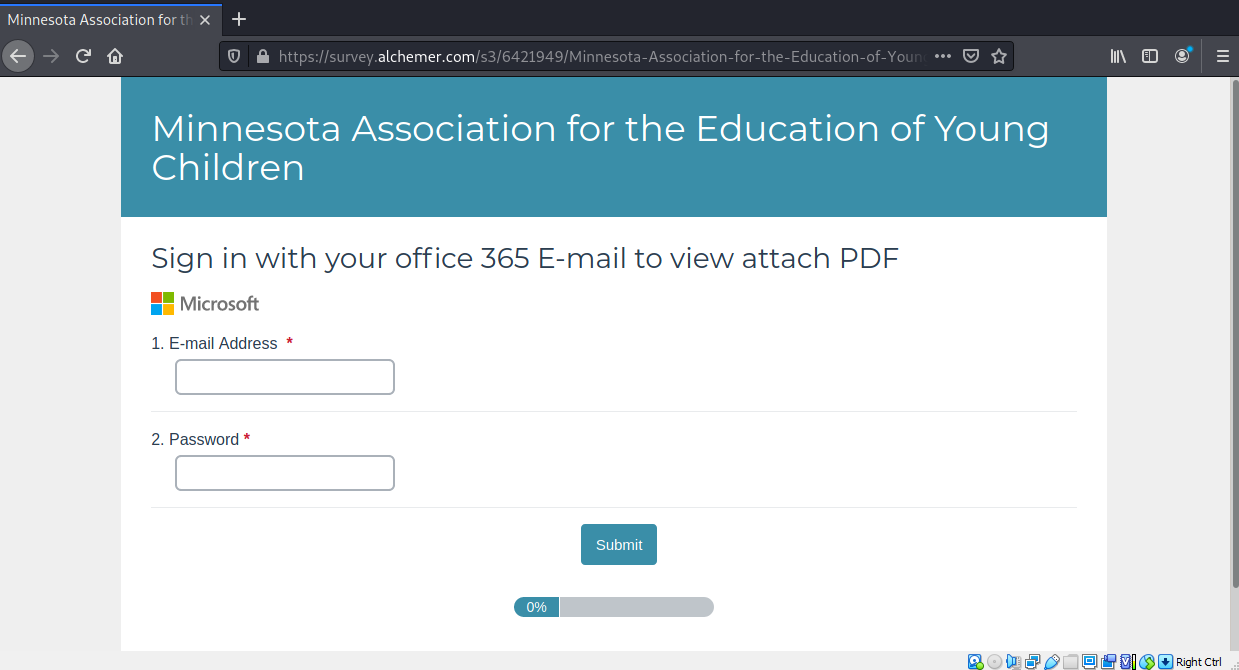
The View Document button resolves to https://survey.alchemer.com/s3/6421949/Minnesota-Association-for-the-Education-of-Young-Children. The first landing page is below. Notice some of the errors, such as the un-capitalized office.
I entered a fake user ID and password and was sent to a download page, which never progressed. See below.
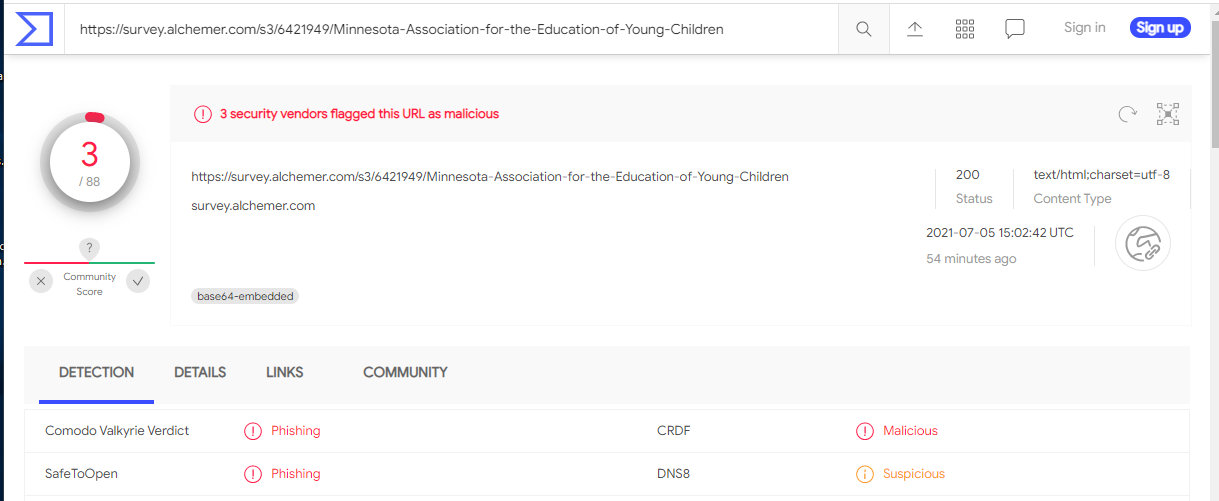
I checked out the link on VirusTotal and found it marked as malicious. I was curious about the domain name alchemer.com, and this does appear to be a legitimate online survey company.
So this exploit is built from several legitimate pieces to help it appear more realistic. The email is sent from a hijacked email account of an actual person, through the mail services of an actual non-profit organization. The survey company that was used to host the two landing pages was also legitimate, although the landing pages were definitely for Office365 account credential stealing. Exploits such as this one can be tough to detect and identify, but their were a few errors (the sender no longer works at the non-profit. and the typo on the landing page) that helped to identify this as an exploit. The button link redirect to a non-Microsoft URL landing page was the third identifiable inconsistency.
But it did take a bit of work and time for me to uncover these issues, so an average recipient might just find this realistic enough to bite on the offered bait.
Share
JUL








About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com