Phishing Email Alerts
Catch of the Day: Adult XXX Phish
Chef’s Special: BEC Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
Adult XXX Phish
I received a response email from a web site I created for phishing simulations at http://outlook.of.fice356.com. Notice the clever use of sub domains to spoof the legitimate Office 465 address.
The offer in the email is simple – the chance of “intimate photos.” Clicking on the shortened Tiny URL link https://tinyurl.com/yhcq2kkr resolved to
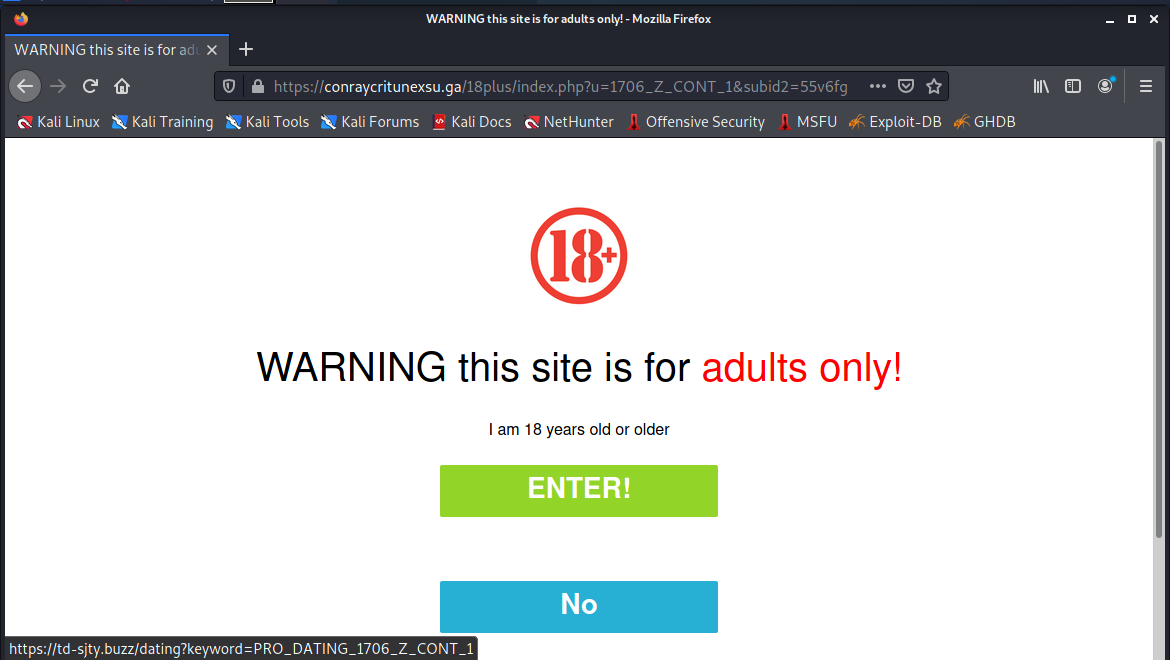
https://conraycritunexsu.ga/18plus/index.php?u=1706_Z_CONT_1&subid2=55v6fg. This is an adult site landing page.
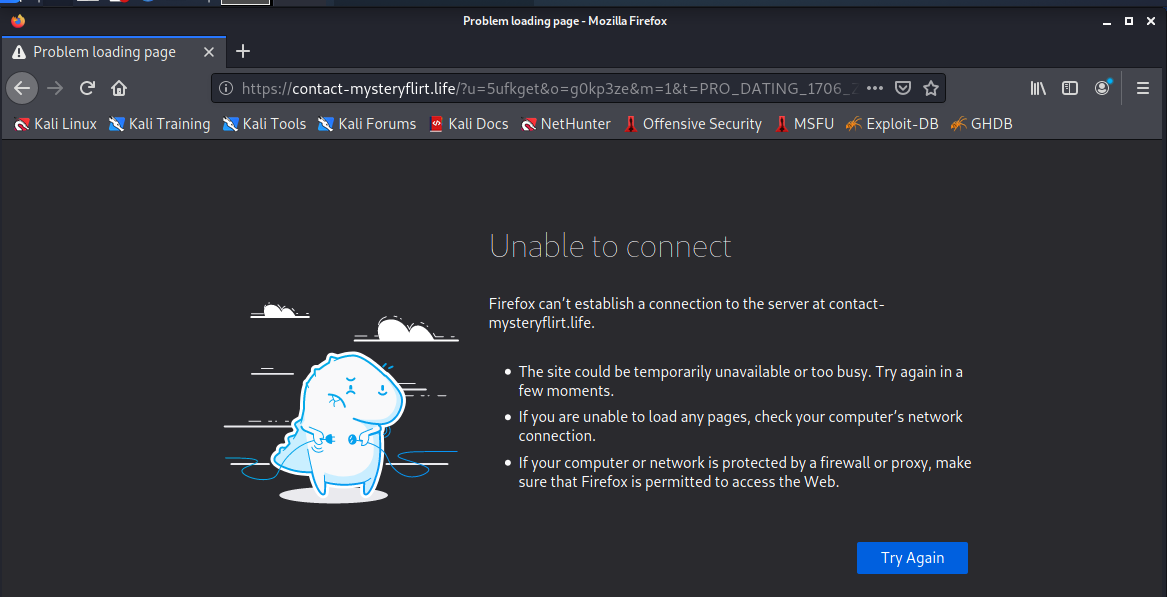
Clicking on the ENTER! button link resolved to https://contact-mysteryflirt.life/?u=5ufkget&o=g0kp3ze&m=1&t=PRO_DATING_1706_Z_CONT_1 and brought me to the following error page.
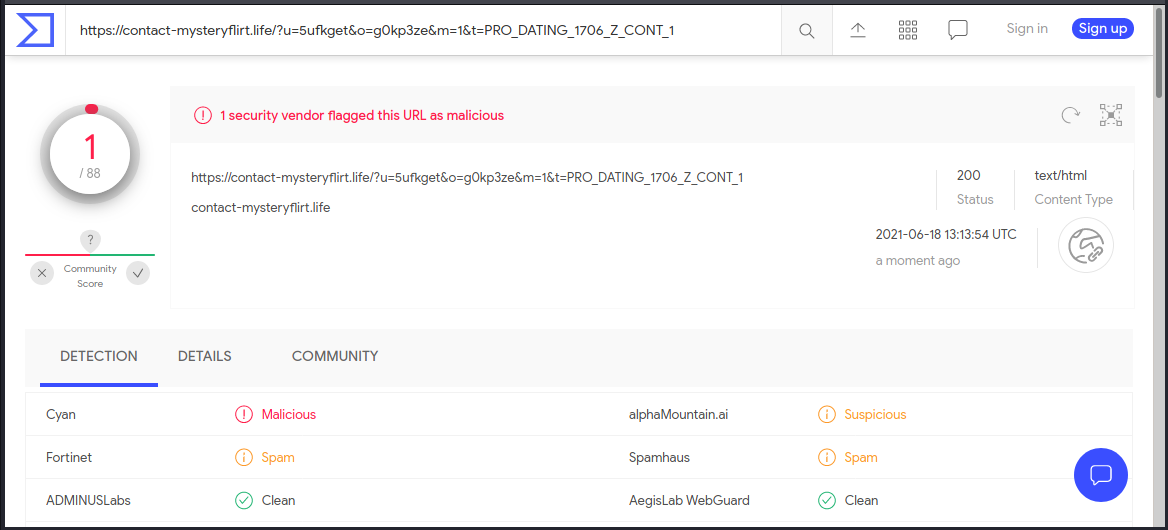
VirusTotal reported this link as malicious,
I am not sure what this exploit was after, other than perhaps some personal information and a credit card. This started with an email responder from one of my own web sites, generated by a web form filler bot. Again, just because you know the source doesn’t mean that the sender is ok.
New BEC Phishing Attack Steals Office 365 Credentials and Bypasses MFA
Leveraging Microsoft Exchange’s Basic Authentication support, scammers were able to use harvested online credentials and bypass any MFA in place, giving them access to mailboxes.
A new attack identified by Microsoft begins with a simple phishing campaign touting a file the recipient must read pointing to a malicious link that takes victims to a lookalike Office 365 logon page.
Once the victim offers up their credentials a “file not found” message is displayed. Now the fun starts. More…
Share
JUN






About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com