Phishing Email Alerts
Catch of the Day: Password Expiring Phish
Chef’s Special: Voice Message Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
Password Expiring Phish
This email was pretty obviously a fraud, and it turned out to be an email credential stealing exploit.
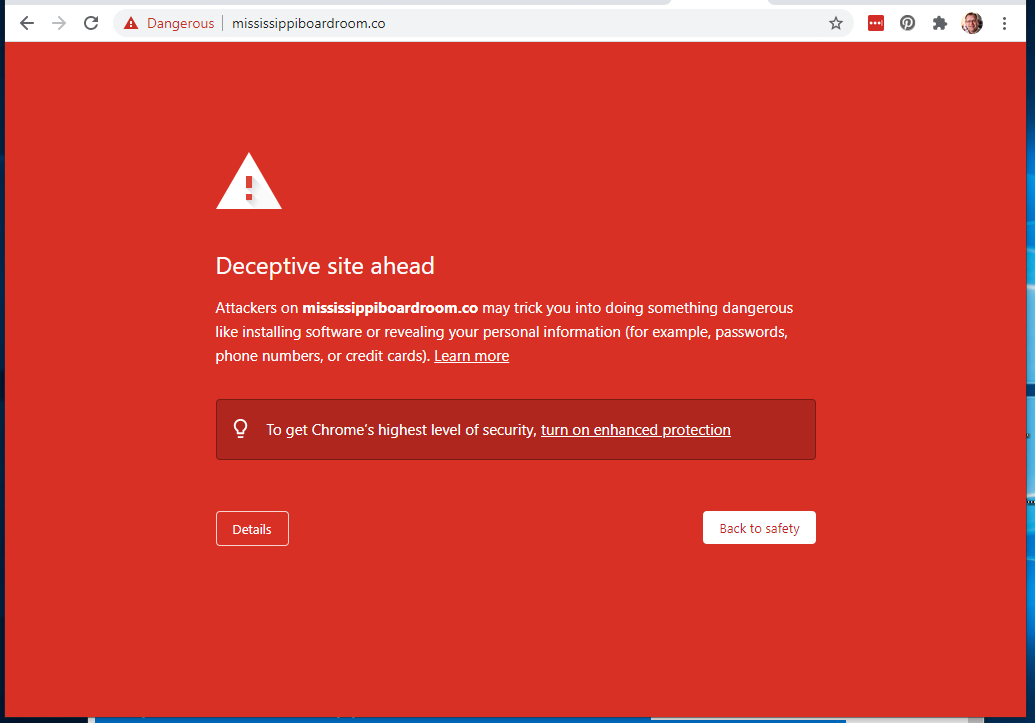
The Confirm Password link resolved to https://mississippiboardroom.co/kol/?referrer=m4st3r&email=Ym9id2Vpc3NAd3l6Z3V5cy5jb20= The landing page is below.
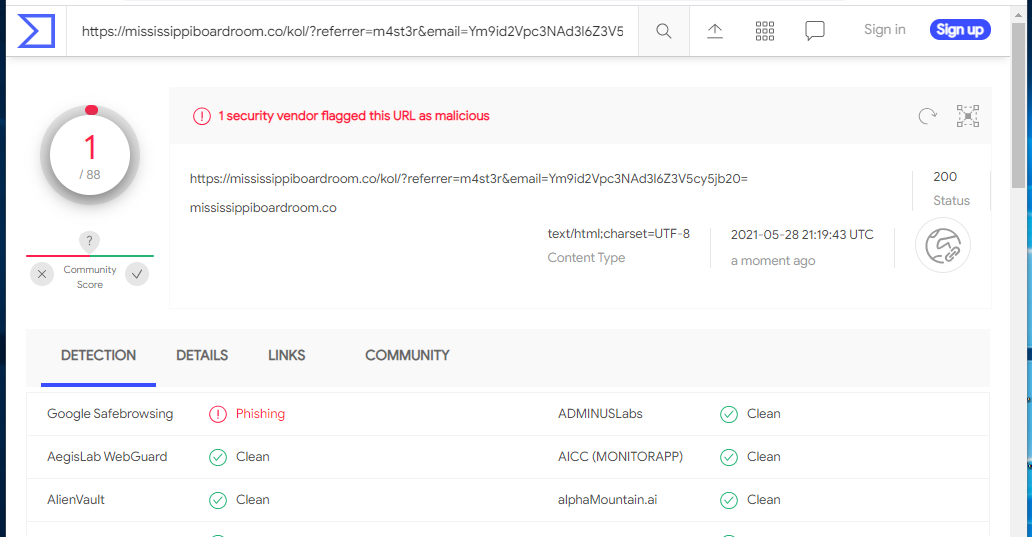
I was curious about the apparent hijacked domain mississippiboardroom.co, but my attempt to check this site out was thwarted by Google Safe Browsing
VirusTotal confirm Google’s warning about this site.
It is exploits like this one that lead to the loss of your email account password. This can lead to Business Email Compromise and a variety of financial frauds including fake wire transfer orders, fraudulent invoices, and electronic funds transfers.
Voice Message Phish
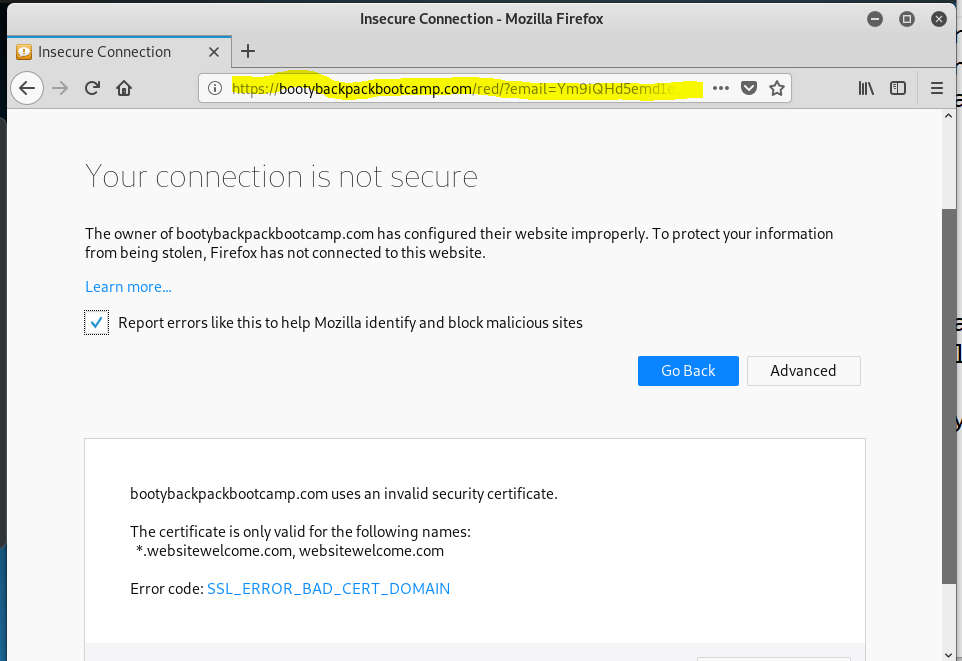
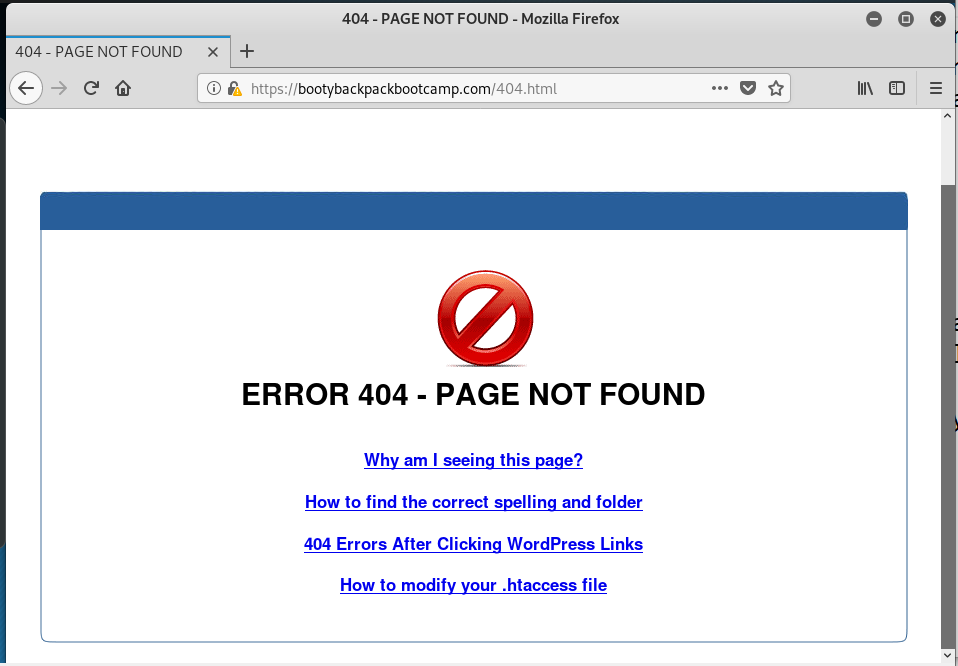
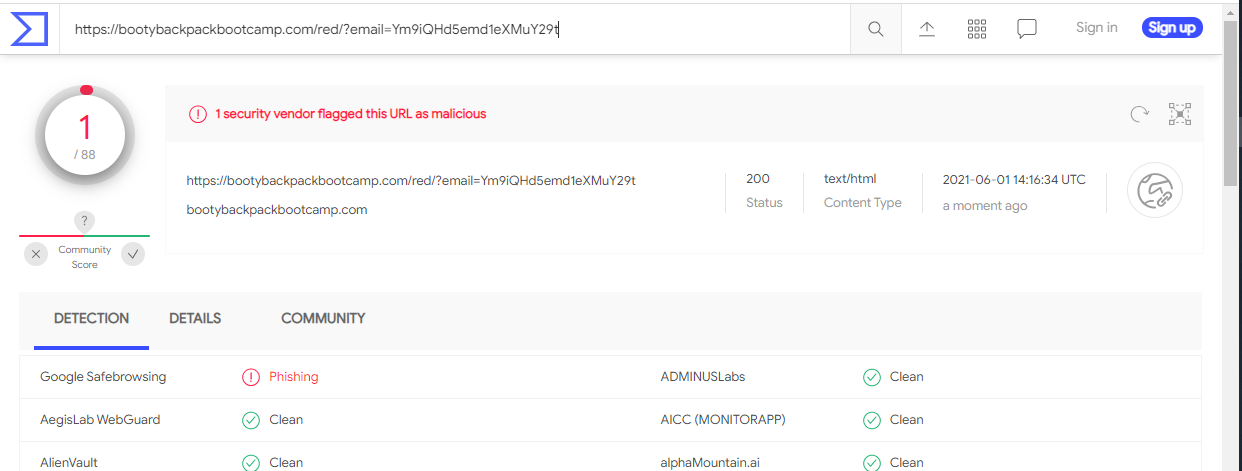
I am not sure where this exploit was supposed to go, as it appears that much of the infrastructure, including the landing page, have been taken down. The Listen to Voice Message button resolves to https://bootybackpackbootcamp.com/red/?email=Ym9iQHd5emd1eXMuY29t. But after plowing through several warning messages about the insecurity of the landing page, I ended up on a 404 Not Found page. Here is the document flow, starting with the phishing email.
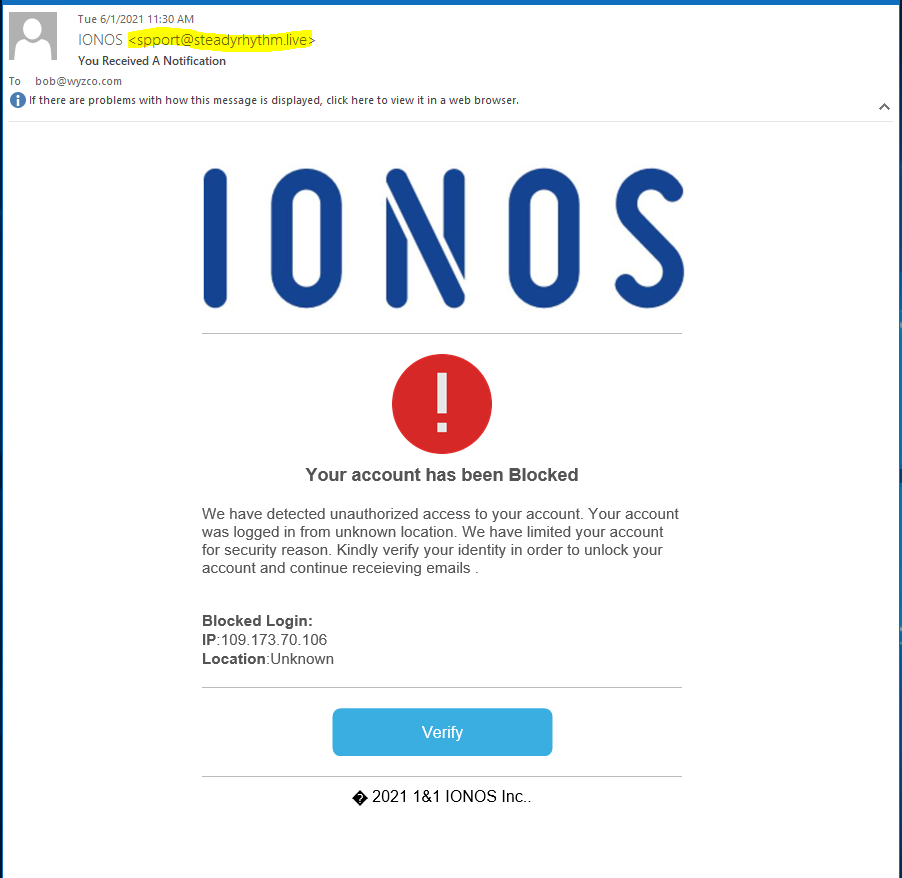
The sender was nicely spoofed to look like an authentic IONOS message, but the email headers told a different story. The email was sent from a mail server named mail.walcarius.com.
Return-Path: <noreply@ionos.com>
Received: from mail.walcarius.com ([81.244.246.138]) by mx.perfora.net
(mxeueus004 [74.208.5.3]) with ESMTPS (Nemesis) id 1MqaYm-1l1Paf1VLc-00mYYw
for <bob@wyzguys.com>; Tue, 01 Jun 2021 10:41:35 +0200
Received: from localhost (localhost [127.0.0.1])
by mail.walcarius.com (Postfix) with ESMTP id E587E40936
for <bob@wyzguys.com>; Tue, 1 Jun 2021 10:30:14 +0200 (CEST)
Received: from mail.walcarius.com ([127.0.0.1])
by localhost (zimbra.int.walcarius.com [127.0.0.1]) (amavisd-new, port 10032)
with ESMTP id V7QLtZMHtN1X for <bob@wyzguys.com>;
Tue, 1 Jun 2021 10:30:13 +0200 (CEST)
Received: from localhost (localhost [127.0.0.1])
by mail.walcarius.com (Postfix) with ESMTP id 96500408C4
for <bob@wyzguys.com>; Tue, 1 Jun 2021 10:28:34 +0200 (CEST)
My attempts to connect to the landing page were met with a series of Firefox warnings:
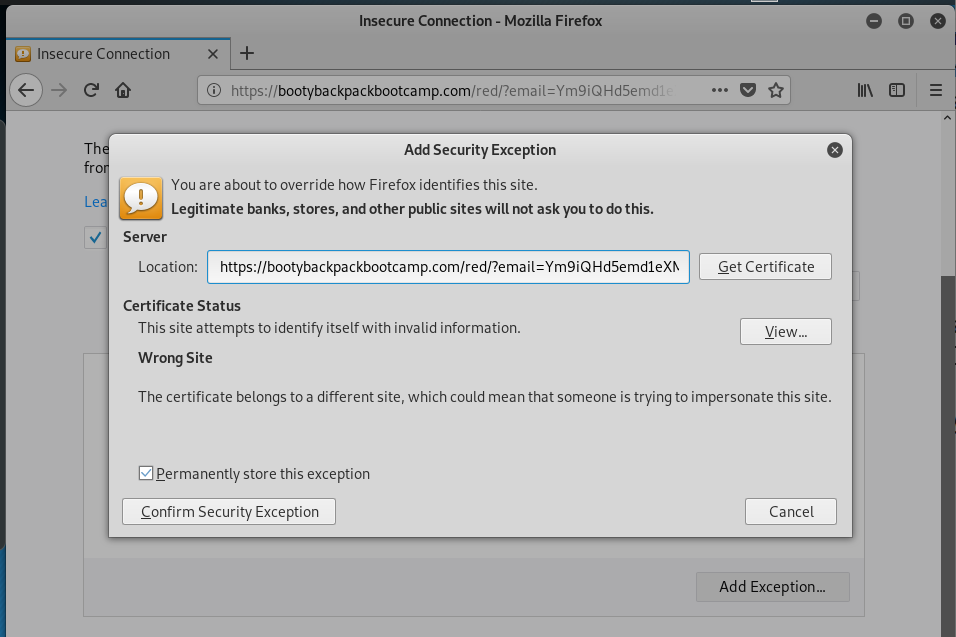
My first attempt at bypassing security got me here.
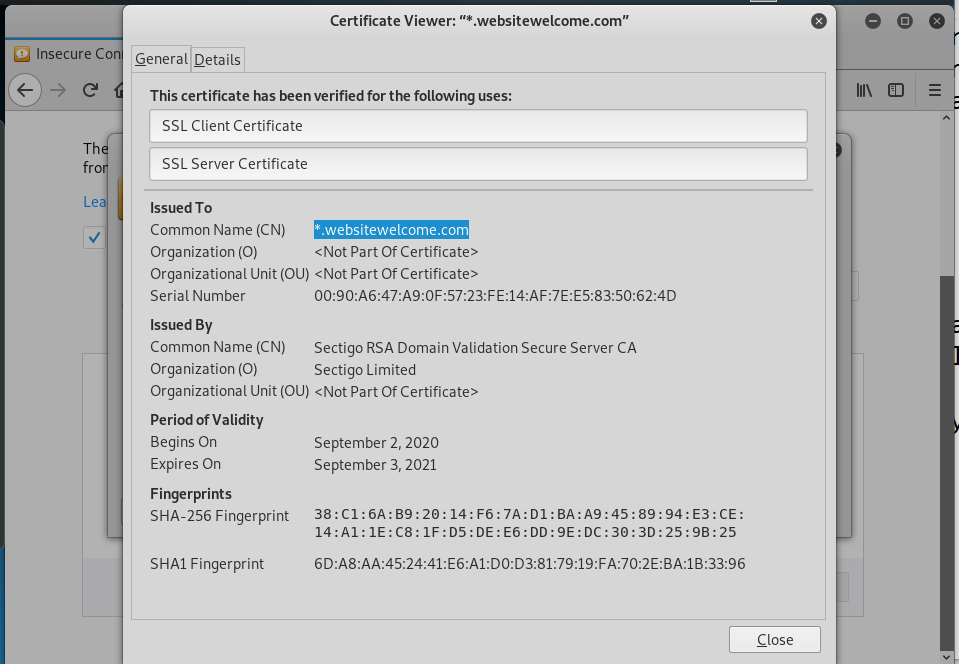
I checked out the security certificate information.
Bypassing security got me to a 404 Not Found page on the bootybackpackbootcamp.com web site, but the site itself appears to have been hijacked, and may be down for repairs and cleaning.
I ran the URL through VirusTotal. Google Safe Browsing reported this URL as a phishing link.
What made this dangerous was the well-done spoofing of the sender email address. Those of you who are following the Friday Phish Fry need to be careful about this, and not just use the sender email address as your only source of sender verification.
Account Blocked Phish
Before we get into this exploit, I want to address the reason why SO MANY of the exploits that target me are using the IONOS brand name and logo. The reason is a little bit scary. These attackers know that I use IONOS for hosting my web sites and email accounts. This information IS PUBLICLY AVAILABLE through online resources such as WHOIS, MXToolbox.com, and any number of IP address locator websites. By simply “pinging” the domain name using the Windows Command Line tool and typing ping wyzguys.com they will get back an IP address that they can use to determine what hosting company is at that IP address.
This information is also publicly available about you, too.
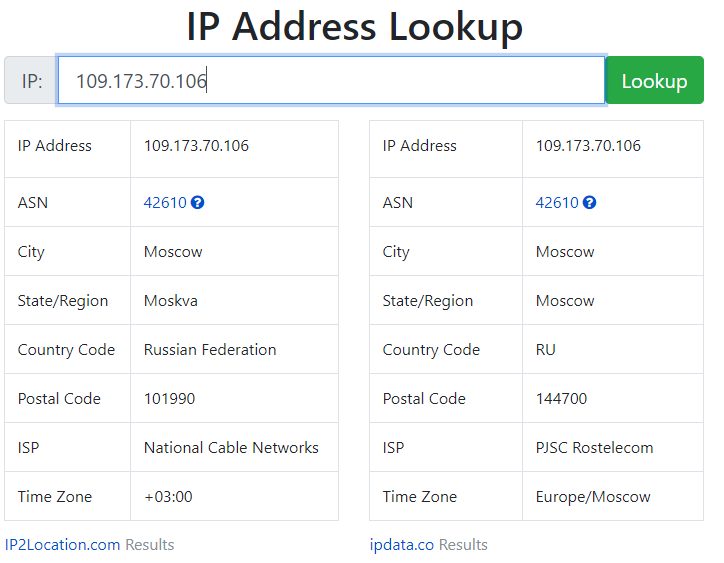
The email that follows claims that my account has been BLOCKED due to unauthorized access from the IP address 109.173.70.106. Of course, the sender email address is suspicious
Using whatismyip.com, I traced this address back to a location in Moscow, Russian Federation. This is most likely just clever story telling. Or the attacker is simply using their own IP address!
The Verify button resolved to https://aadi765.s3.eu-de.cloud-object-storage.appdomain.cloud/albification/index.html#bob@wyzco.com and opened this landing page. Pretty typical credential stealer page.
The appdomain address is an ASP.net web page code writing tool that is used to load applications into web pages. You can read a little about application domains here. Not positive, but this COULD indicate that in addition to stealing my login credentials, this exploit may also be downloading and running malware code, too.
USPS SMS
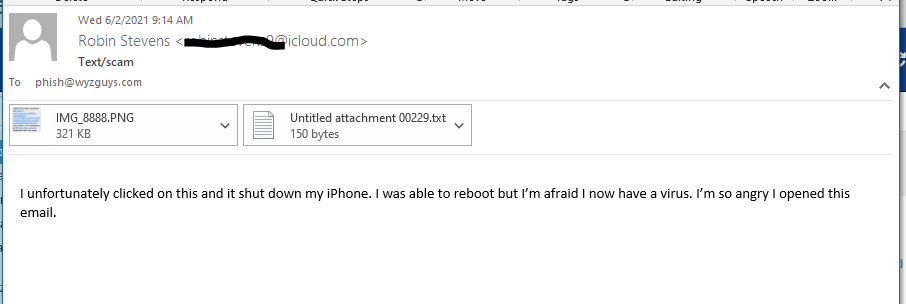
I received this example from a site visitor named Robin that found me through Google. I have three emails she sent to me, and screen shots from her iPhone of an email and a text message that supposedly was sent by the US Postal Service.
And then this email came a few minutes later
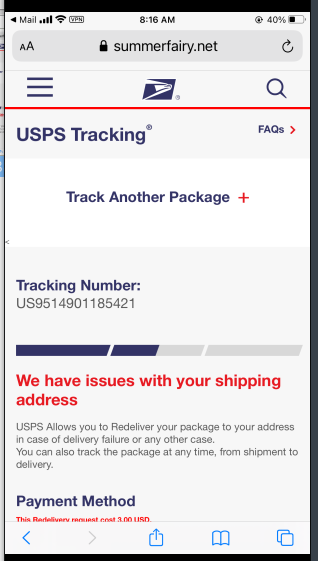
There was also a third email with an attachment. I opened the two attachments and found these two exploits. These were sent a screenshots, so the links were not active, which made it tough to investigate The first one is an email with an originating domain of summerfairy.net, which is suspicious.
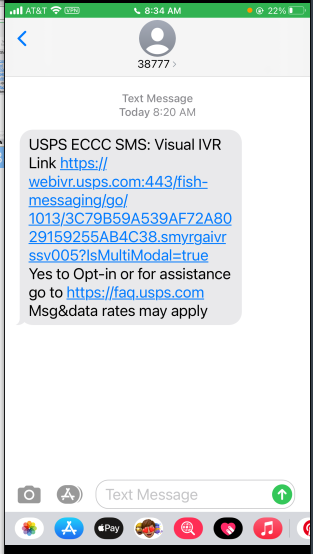
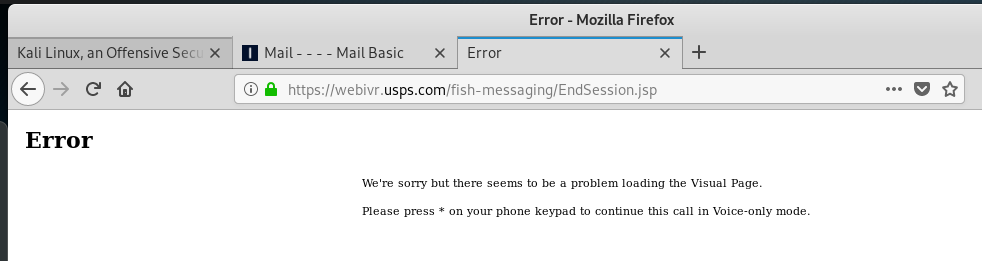
This next one displays what appears to be a legitimate USPS domain in the link.
My attempt to enter it manually took me to an error page on what looks like an actual USPS site. My suspicion is that this URL actually masked a different destination page somewhere else.
Not sure exactly what the scam was, but clicking on the link restarted Robin’s phone. This does illustrate the importance of exercising suspicion when looking at these sore of messages on your phone.
Joint CISA-FBI Cybersecurity Advisory on Sophisticated Spearphishing Campaign
Original release date: May 28, 2021
CISA and the Federal Bureau of Investigation (FBI) are responding to an ongoing spearphishing campaign targeting government organizations, intergovernmental organizations, and non-governmental organizations. A sophisticated cyber threat actor leveraged a compromised end-user account from Constant Contact—a legitimate email marketing software company—to spoof a U.S. government organization and distribute links to malicious URLs.
In response, CISA and FBI have released Joint Cybersecurity Advisory AA21-148A: Sophisticated Spearphishing Campaign Targets Government Organizations, IGOs, and NGOs and Malware Analysis Report MAR-10339794-1.v1, providing tactics, techniques, and procedures (TTPs); downloadable indicators of compromise (IOCs); and recommended mitigations.
CISA strongly encourages organizations to review AA21-148A and MAR-10339794-1.v1 and apply the necessary mitigations.
Share
JUN










About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com