Phishing Email Alerts
Catch of the Day: Domain Suspension Phish
Chef’s Special: E-Fax Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
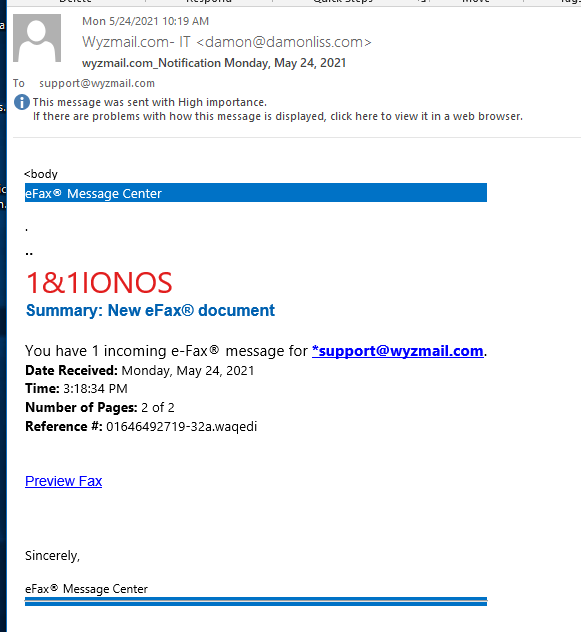
IONOS E-Fax Phish
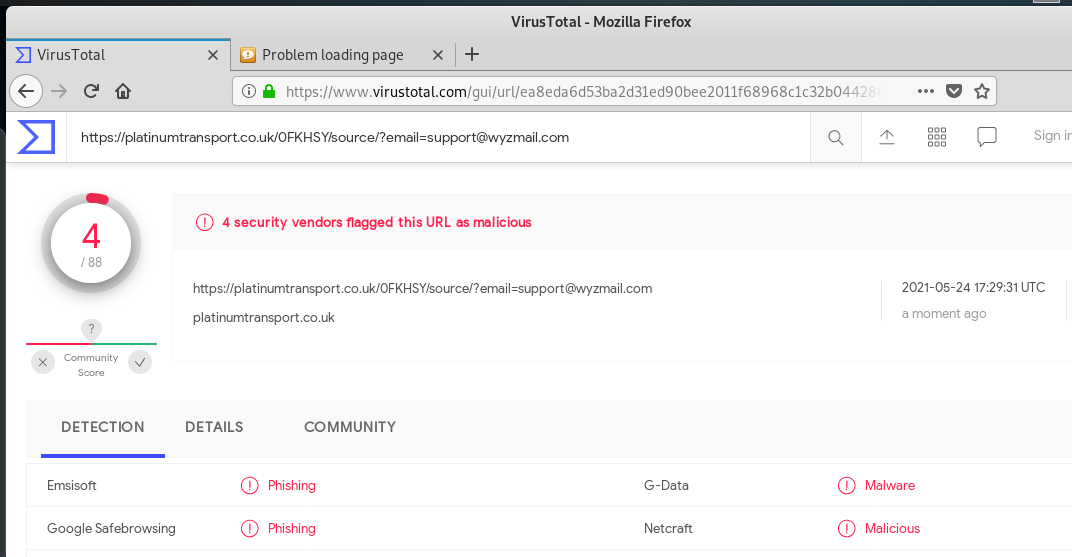
This exploit had already been taken down along with the hijacked website at https://platinumtransport.co.uk. This is where the Preview Fax link resolved: https://platinumtransport.co.uk/0FKHSY/source/?email=support@wyzmail.com. VirusTotal is flag this link as malicious.
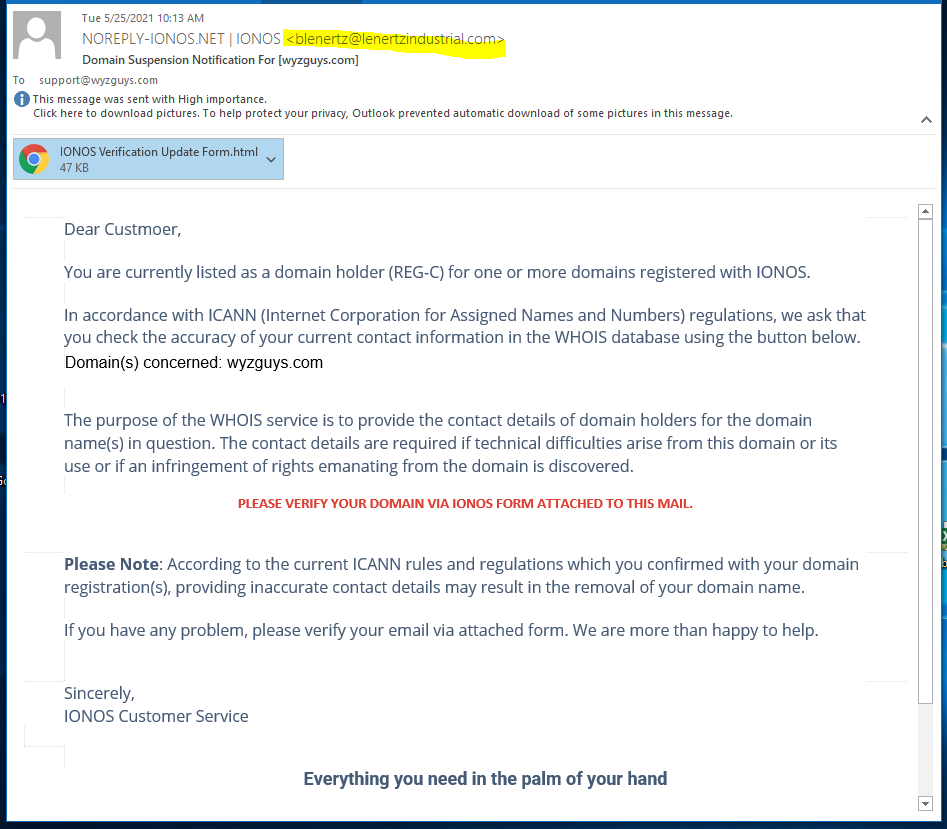
Domain Suspension Phish
Over the years, as a person who “owns” a number of domains, I have received many messages like this one. Starting with the postal mail registrar switching letter from “Domain Registry” and moving on to various phishing emails that lead with some sort of problem with your domain. Your domain is going to expire. You domain has been “blocked.” And this one, where your domain is suspended.
If you are running a website, these sort of messages can cause anxiety, because losing control of your domain name can cause serious problems. This particular message is very well written, using the actual content and syntax that I have seen in legitimate emails from the Registrar.
The sender email address is a strong clue that this is a phish. The exploit is carried inside another HTML attachment. Here are some images. First the phishing email.
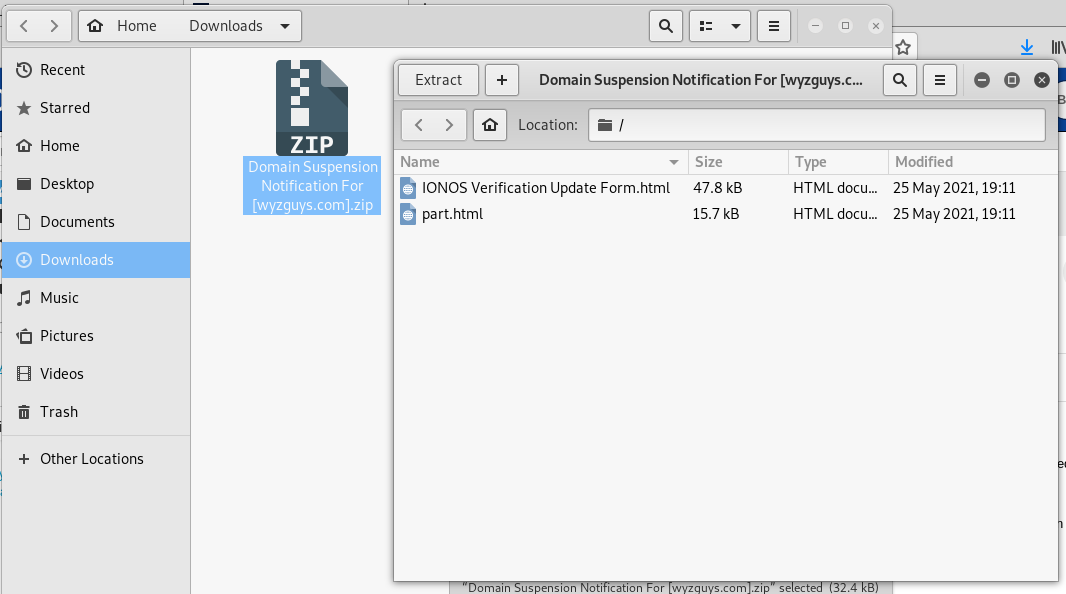
I opened the attachment using a Kali Linux virtual machine.
When I opened the Update Form and this following HTML page opened. Notice that this opened in the directory structure of the virtual machine, which makes this a “self-hosted” landing page. Looks to be a simple credential stealing exploit.
Virus total identifies this as a phishing exploit attachment.
When responding to anything to do with your domain or web site hosting, the best thing to do is to log in to your Registrar and/or Web Hosting account and confirm the details of the email directly with them. Forwarding these emails to their “abuse@” support email addresses can also help to confirm if the email is legitimate or fake. Usually, if your web site is working properly, this is another indication that the email is fraudulent. If your domain was really “suspended” your should not be able to open your home page, it would have been replaced with a warning page set up by your Host.
Share
JUN







About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com