 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: Target Invoice Phish
Chef’s Special: Domain Renewal Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
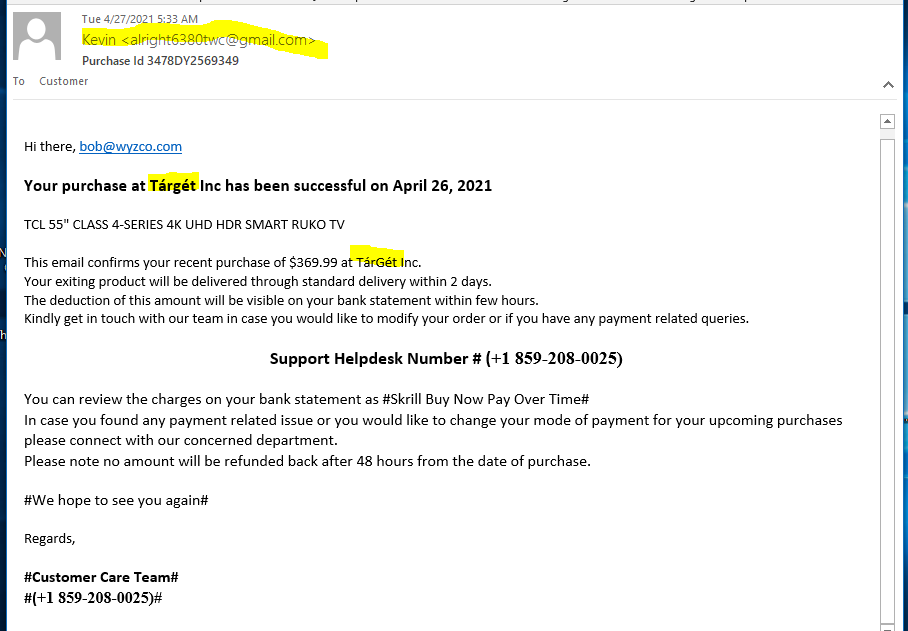
Target Invoice Phish
Not much to this exploit, it appears to rely on a phone call from the “target” victim to complete the scam. I have noticed a trend lately to less complex phishing attacks using attachments of the HTML landing page, or call-back scams like this one.
Note the sender’s Gmail address, and the spelling of Target using European style inflected vowels. And the purchase of a “Ruko” (not Roku) TV. The details reveal that this is a scam.
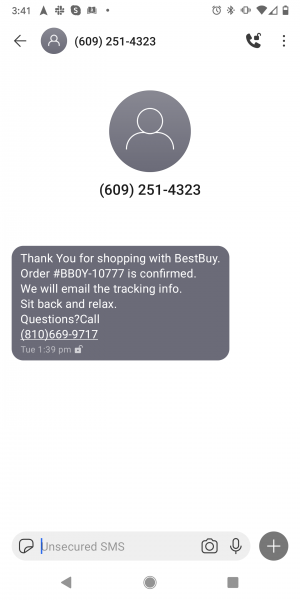
Best Buy Smish
Don’t trust goofy text message alerts on your smartphone either. Again, call a phone number if you have “questions.” Like why am I spending so much time shopping?
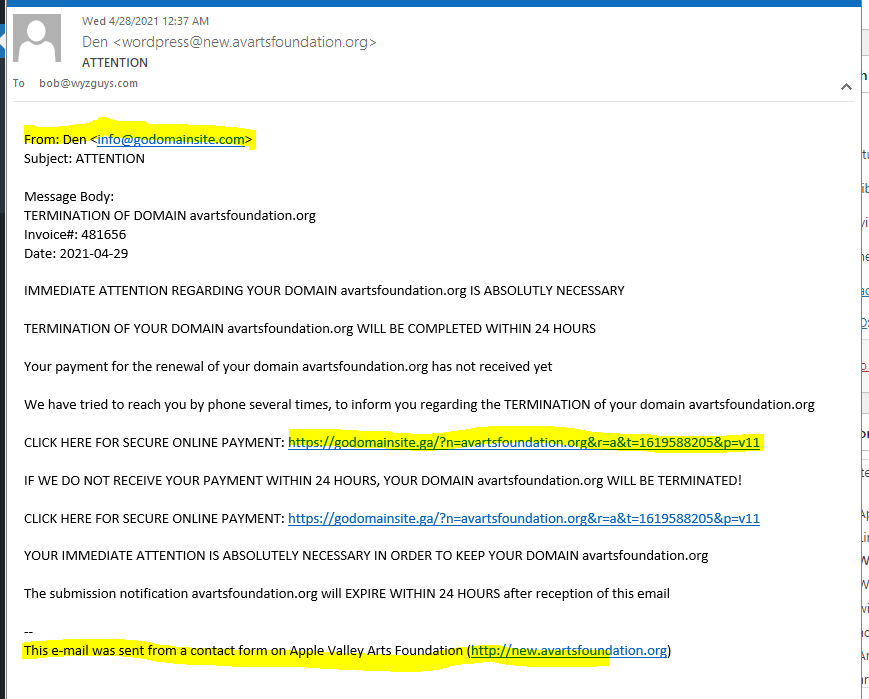
Fake Domain Renewal Phish
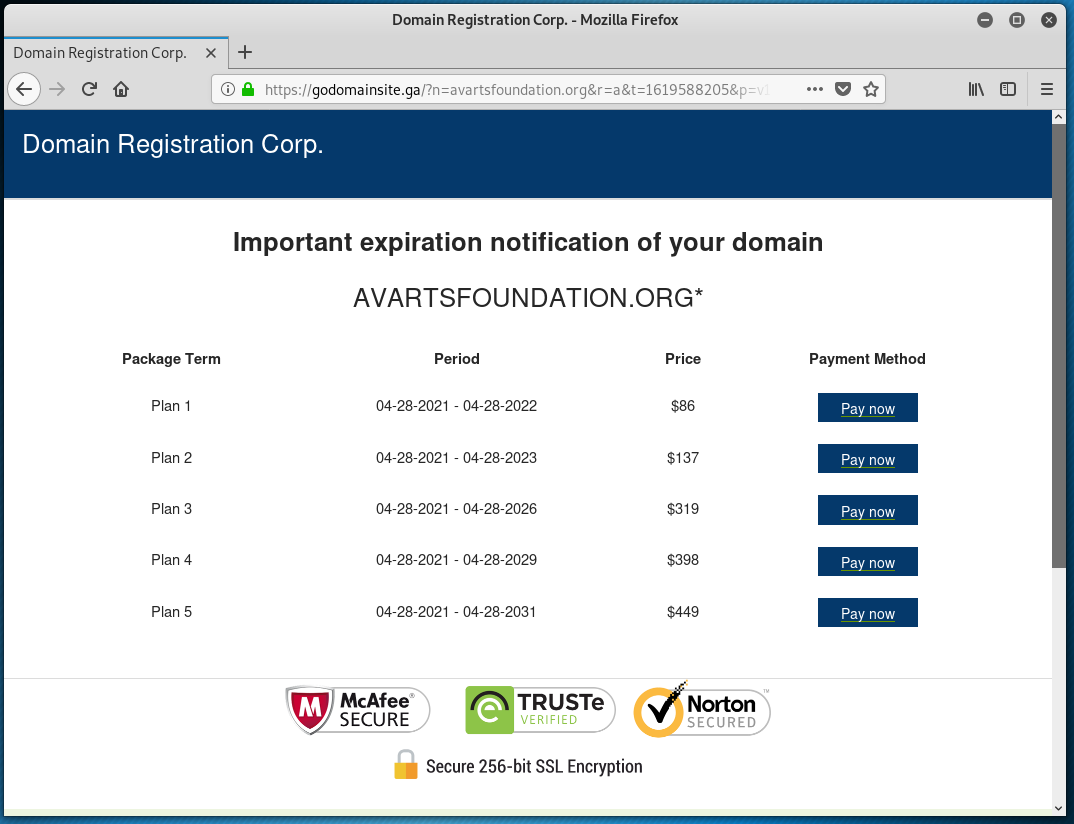
We have featured these scammers before. This apparently is a “Domain Registrar” out of the African nation of Gabon. I think they are just simply interested in getting you to pay the fake invoice. Other domain scams attempt to get the domain name transferred, but these scammers just want the money. Good cash flow and no inventory to maintain. The main URL in the email is a direct link to their payment page. https://godomainsite.ga/?n=<redacted.org>&r=a&t=1619588205&p=v11
This email was sent via the contact form on the target’s website, I’m not sure this is even illegal. If you get an invoice, and pay it without confirming, that’s your fault.
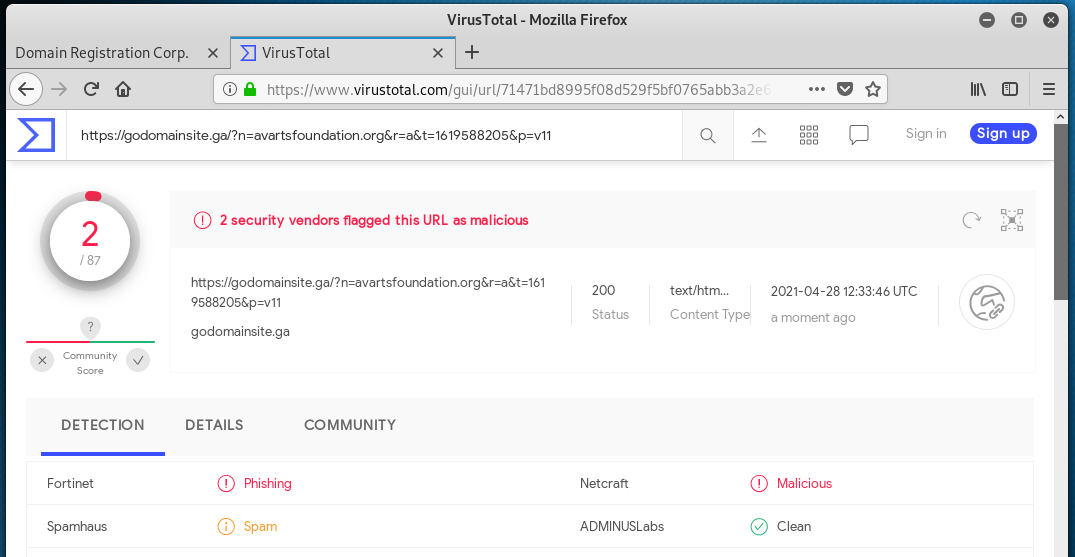
VirusTotal identified the link as a phishing or spam link.
Here is the first landing page with a nice selection of payment options. The URL is not redirected in any way, these pages are on their own domain name and website.
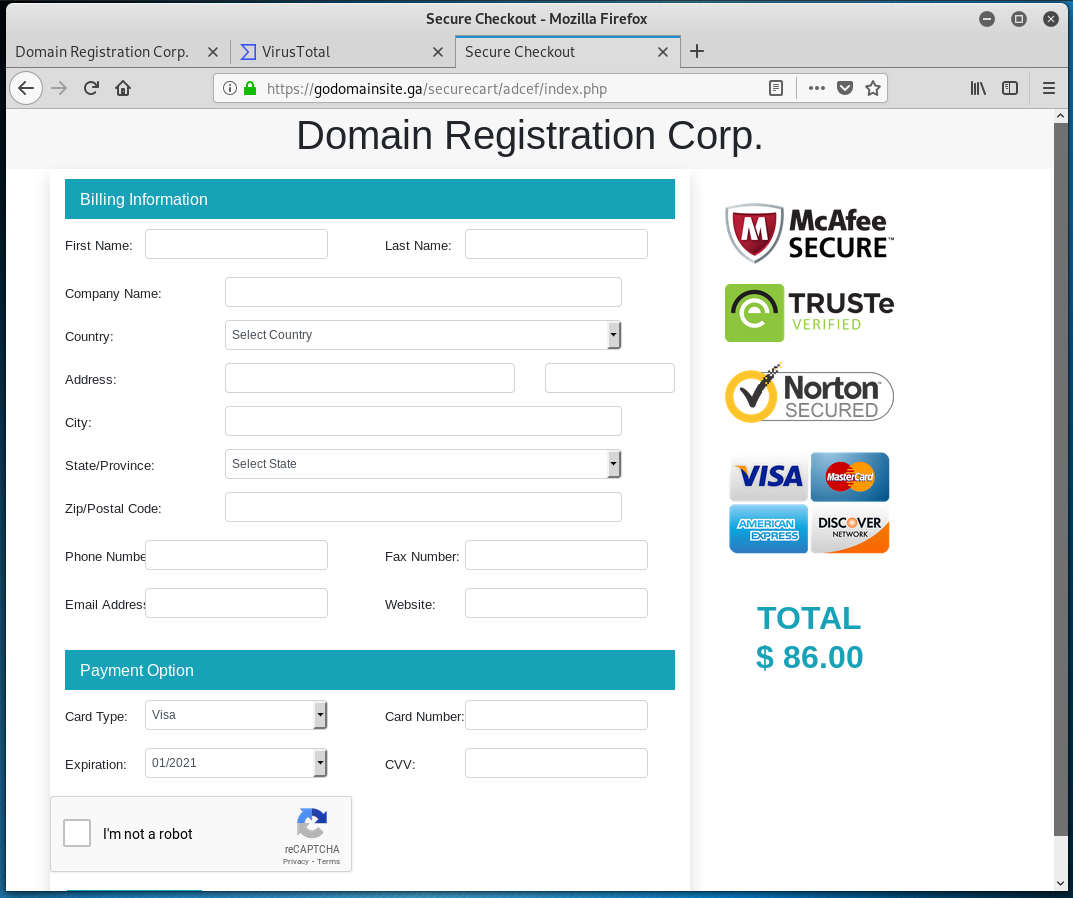
The next page presents a pretty typical payment form. Since they collect your credit card information here, if they use your credit card to make other purchases or payments, that would be a criminal fraudulent act. But since this scam appears to be located in Gabon, which does not have an extradition treaty with the US. Since the individual dollar amount are small, law enforcement would be uninterested in this little scam.
It’s a gumball business (lots of little purchases) but if the scammers get 100 people to fall for this every day, that is $8600 a day or slightly over $3 million per year.
This scam works because businesses, especially small businesses, have a very limited understanding of how domain names and website hosting works, and many don’t know who their Registrar or Web Host are. Considering how important domains and websites are for marketing and ecommerce, many victims just pay to be “on the safe side.” Don’t you be one of them.
COVID-Related Phishing Attacks Return to Mid-Pandemic Heights
New data from Palo Alto Network’s Unit42 provides a wealth of insight into specifically how cybercriminals have leveraged COVID-related theming to ensure a successful phishing attack.
Throughout the last 14 months, the bad guys have consistently kept pace with the state of the pandemic. They have been looking for the best aspects of the COVID saga to get the attention of individuals and businesses alike for these attacks.
According to Unit42’s new COVID-19 themed phishing attack data, these scammers know exactly how to press the buttons of their potential victims at just the right time. For example, the current concern is around vaccines. According to Unit42:
- Vaccine-related phishing attacks rose by 530% from December 2020 to February 2021
- Phishing attacks targeting pharmacies and hospitals rose by 189% during that same timeframe
Over the past 14 months phishing attacks have changed their stripes to meet the current state of the potential victim’s concerns, fears, needs, and hopes – as shown below.
Blog post here:
https://blog.knowbe4.com/covid-related-phishing-attacks-return-to-mid-pandemic-heights/
Currently Popular Social Engineering Tactics
Criminals are exploiting new technology to launch updated versions of old attacks, according to Derek Slater at CSO. George Gerchow, CSO at Sumo Logic, told Slater that threat actors are sending spear phishing emails that impersonate real employees within the organization.
“It’s not easy to defend what you can’t see, and you are only as strong as the weakest link,” said Gerchow. “For example, there have been a plethora of targeted emails coming in that look like they are from your trusted partners but are in fact bad actors posing as employees you may know within your network.”
Gerchow added that attackers are putting more effort into making their social engineering techniques extremely convincing.
“Now we see these long, sophisticated attempts to build trust or relationships with some of our outbound-facing teams whose entire job is to help,” Gerchow said. “The bad actors have even posed as suppliers using our product with free accounts and have gone through use cases and scenarios to engage expertise within our company.”
Oz Alashe, CEO of CybSafe, told CSO that some attackers exploited the pandemic by sending malicious versions of remote work and collaboration tools.
“The threat actors send over a Visual Studio Project containing malicious code,” Alashe said. “The user self-runs the program, and their device is infected pretty quickly. This attack essentially exploits the desire or need to assist or help others with passion projects.”
Full blog post with links:
https://blog.knowbe4.com/currently-popular-social-engineering-tactics
Share
APR




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com