Phishing Email Alerts
Catch of the Day: Request for Quote Phish
Chef’s Special: PDF Attachment Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
Last week was kind of a quiet week. Nothing to report, so there was no Friday Phish Fry
Request for Quote Phish
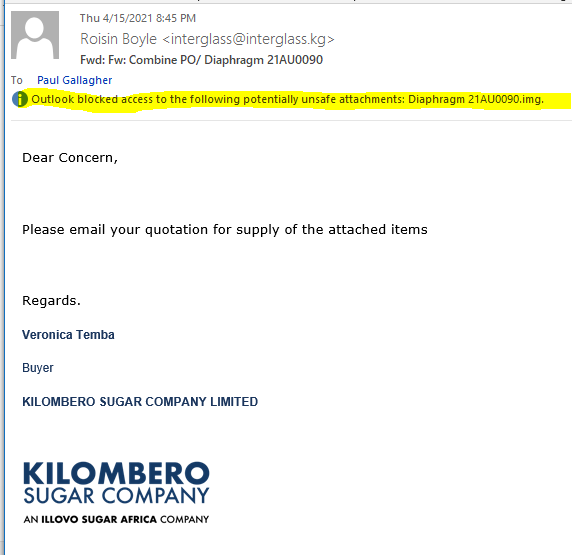
Sometimes as an investigator, I have to bypass my own security to conduct the investigation. I got this email in Outlook, which blocked the attachment.
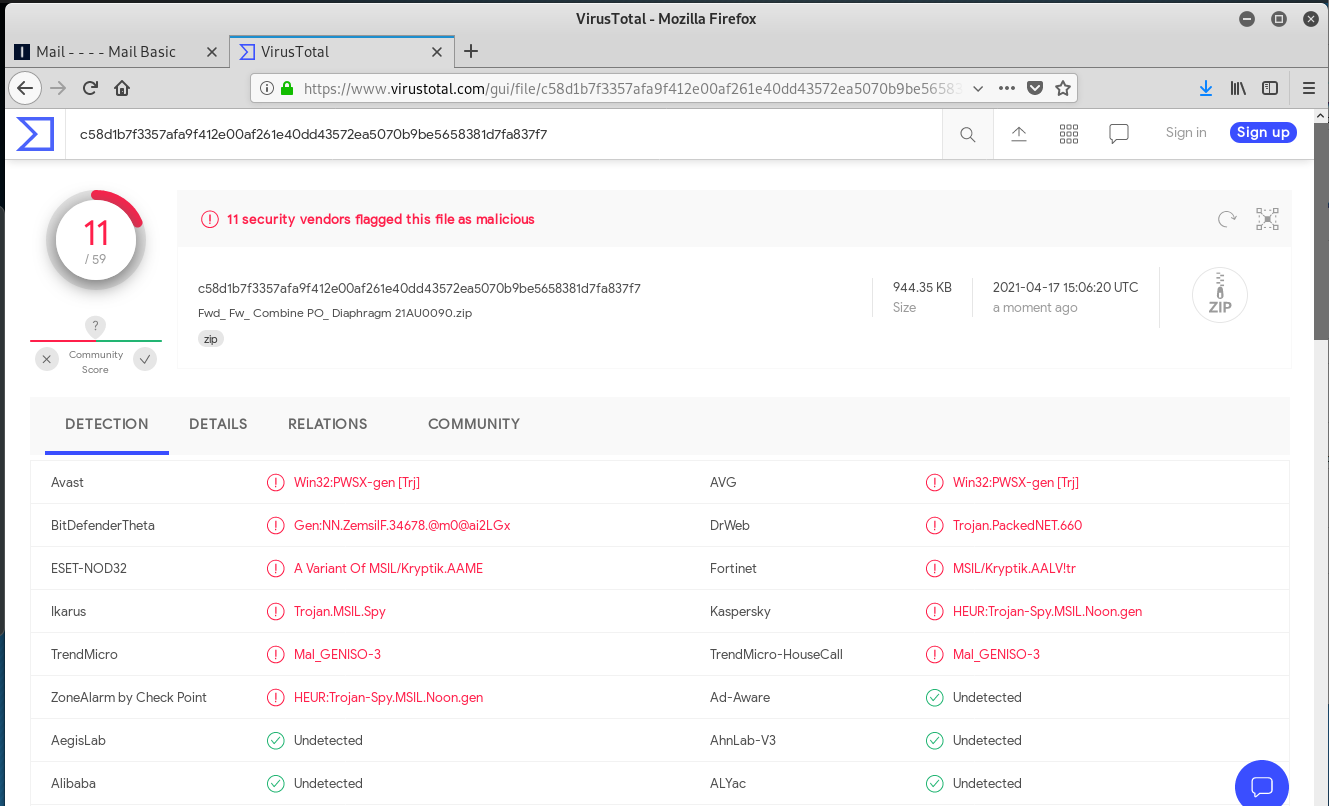
I opened my Kali Linux VM and went to retrieve the email in the webmail portal. I noticed the email was sent to Paul Gallagher, so I checked the sender and recipient information in the email headers. The sender address was for a domain in Krygyzstan. The mail server is from Tanzania.
Return-Path: <interglass@interglass.kg>
Received: from medeortz.co.tz ([196.41.32.157]) by mx.perfora.net (mxeueus003
[74.208.5.3]) with ESMTPS (Nemesis) id 1MTiXx-1l5sZx0Szt-00U3lO for
<bob@wyzguys.com>; Fri, 16 Apr 2021 03:46:02 +0200
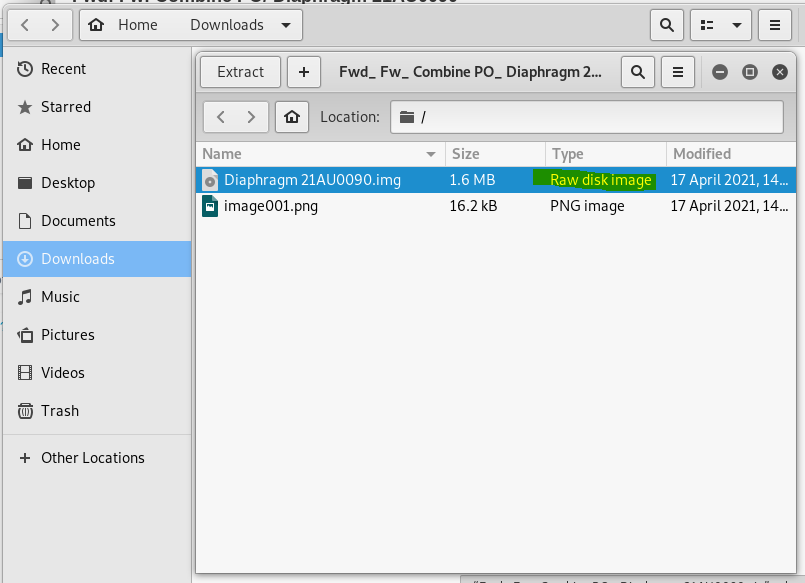
I was able to open the email with the attachments in webmail.
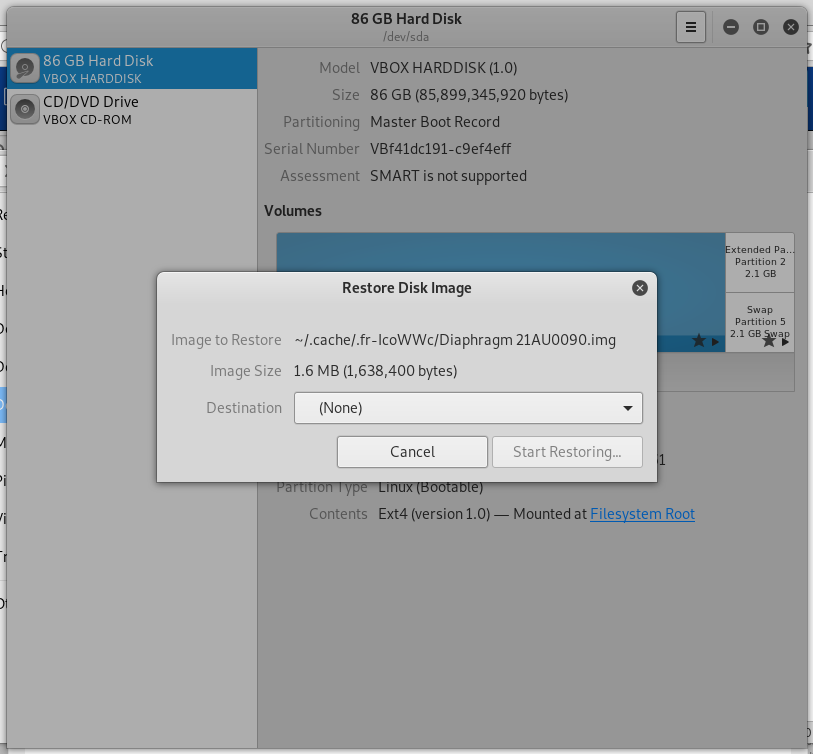
My attempt to pen the first attachment Diaphragm 21AU0090.img presented a ZIP file instead of an image. Unzipping the archive revealed an disk image hidden in the attachment.
When I tried to open the disk image, it attempted to reimage (reformat and install a new operating system) the virtual drive of the Kali VM. So I cancelled that process.
The other attachment WAS an image.
VirusTotal identified this as a Trojan horse, and this appears to be a version of polymorphic malware that changes its source code with every installation to avoid detection.
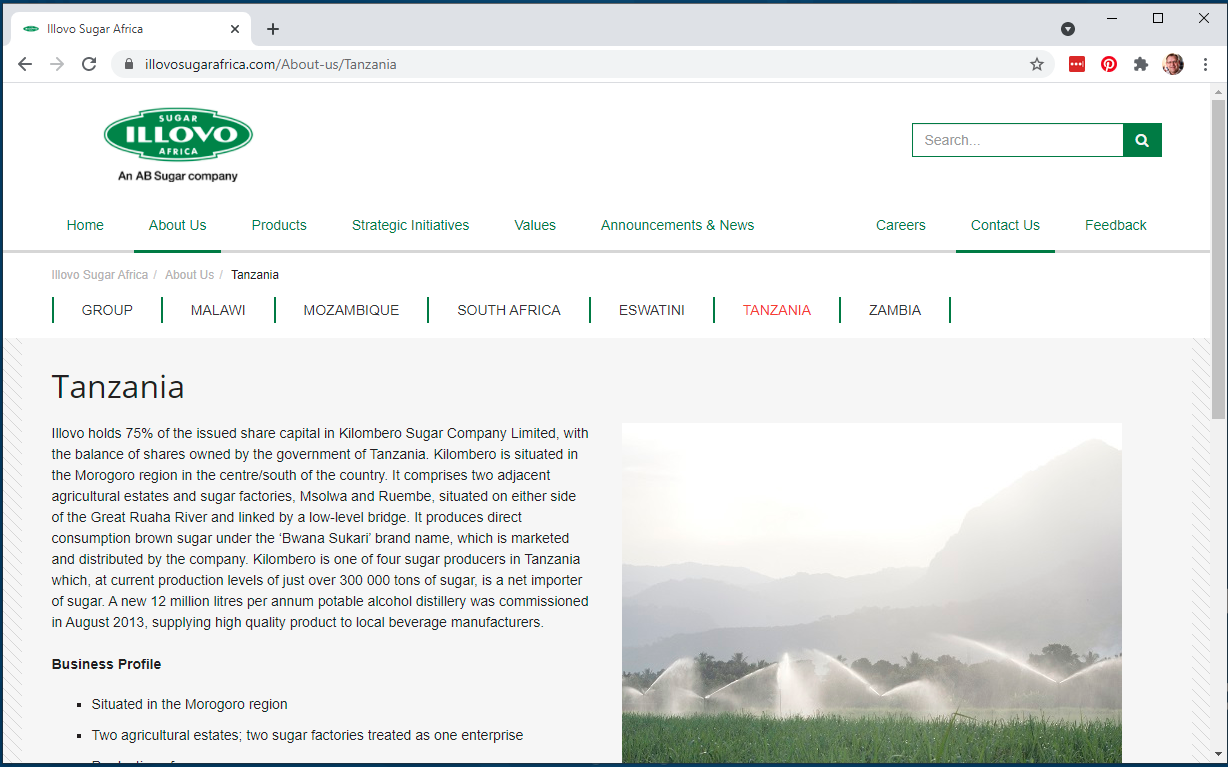
There are so many inconsistencies between the spoofed sender address, the recipient addresses, and the signature block on the email, that I decided to try and find a website for Kilombero Sugar Company, and Google search gave me the home page for Illova Sugar.
So in this exploit I have a Kyrgyz sender, through a Tanzanian mail server, from a Tanzanian sugar company (allegedly). The payload would have reimaged my hard drive, had I continued. All in all, a very interesting exploit.
Recent Phishing Attacks Using PDF Files Have Skyrocketed More Than 1,000%
Phishing attacks using PDF files have spiked over the past year, according to researchers at Palo Alto Networks’ Unit 42.
“From 2019-20, we noticed a dramatic 1,160% increase in malicious PDF files – from 411,800 malicious files to 5,224,056,” the researchers write. “PDF files are an enticing phishing vector as they are cross-platform and allow attackers to engage with users, making their schemes more believable as opposed to a text-based email with just a plain link.”
The most common form of PDF phishing lures used an image of a fake CAPTCHA to trick victims into clicking the “Continue” button, which led to a malicious site. Another variant used an image that purported to be a coupon, and told victims to click the image in order to get 50% off on a product.
A third type of PDF phishing attack used images that appeared to be paused videos, but led to a phishing site when users clicked on them.
New Phishing Attack With .TXT Attachment Can Steal All Your Secrets
The 360 security blog just came up with an eye opener. Recently, 360 Security Center’s threat monitoring platform has detected a new email phishing attack. This attack uses a secret-stealing Trojan called Poulight. The Poulight Trojan has been put into use since last year and has complete and powerful functions. This attack proved that it has begun to spread. Blog post with links and full attack plus code analysis:
https://blog.knowbe4.com/heads-up-new-phishing-attack-with-.txt-attachment-can-steal-all-your-secrets
Share
APR






About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com