Phishing Email Alerts
Catch of the Day: DHL Shipping Phish with a side of Trojan Horse
Chef’s Special: Exchange Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
DHL Shipping Phish with Trojan
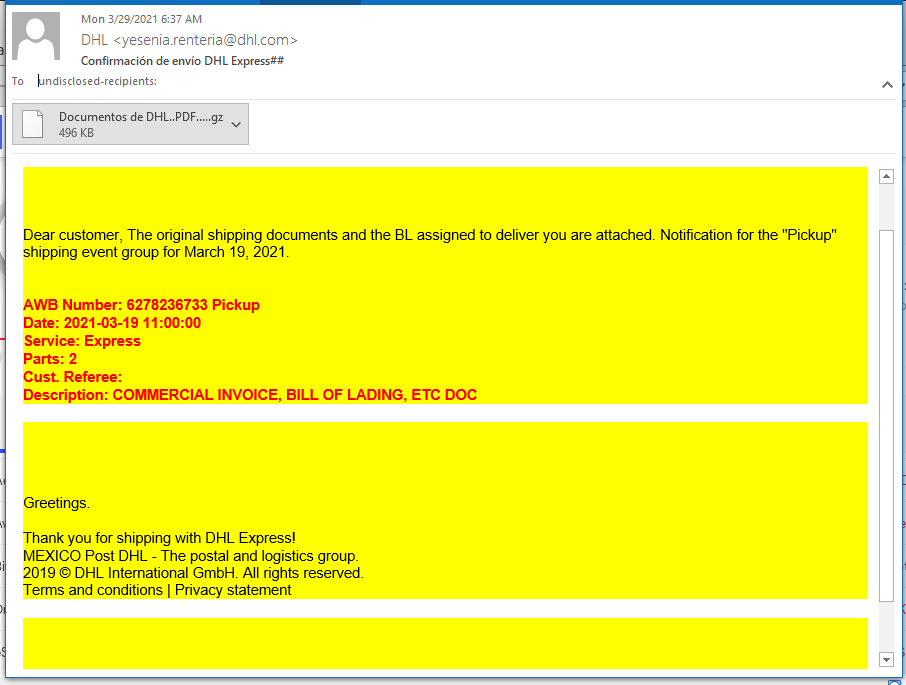
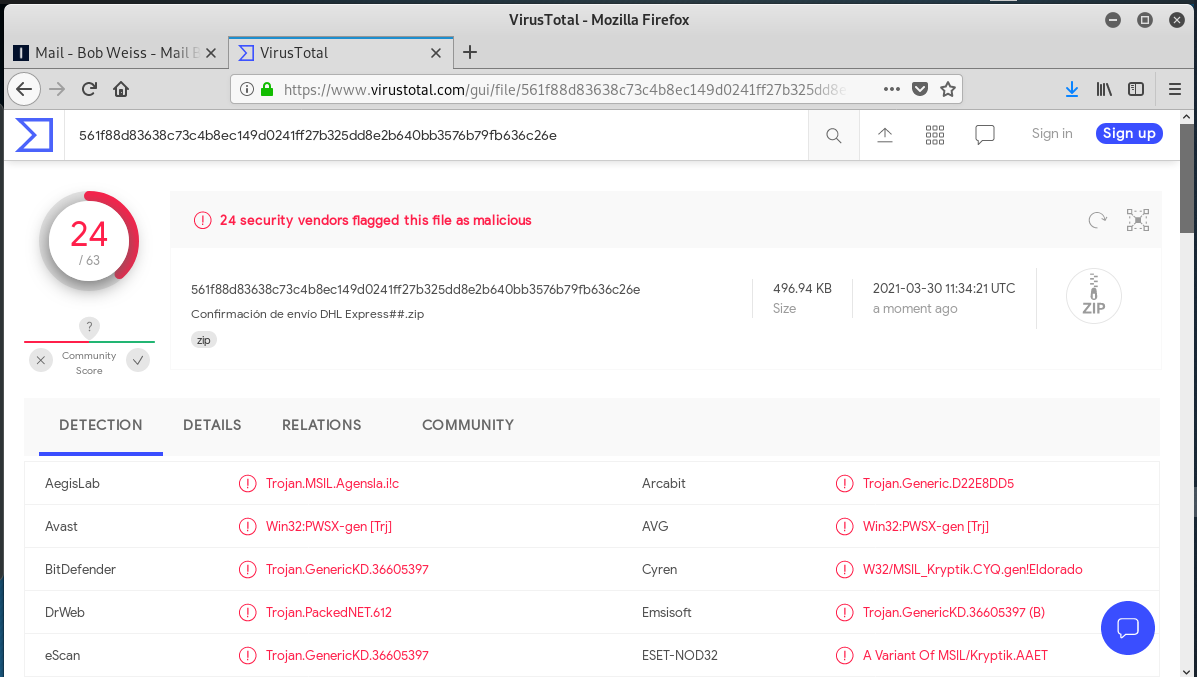
This phishing email gets low marks for artistic ability. DHL colors but no logo to provide authenticity. The DHL Mexico email address appears to be authentic, not spoofed, according to the email headers. But the .GZ (.zip) file attachment lit up the board at Virustotal. The attachment was a zipped up version of a remote access Trojan horse.
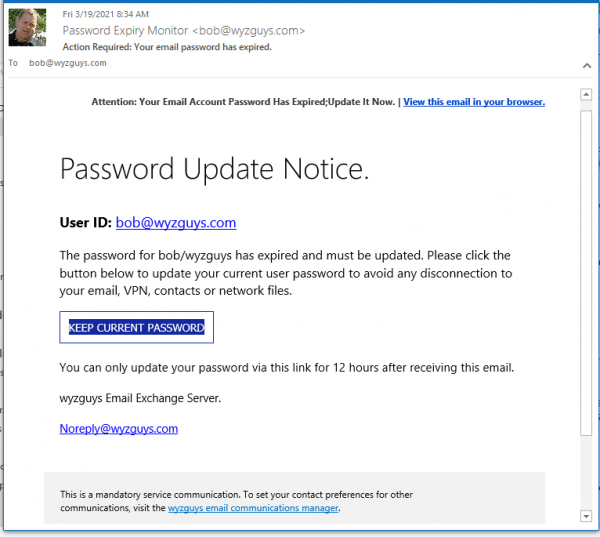
Exchange Phish
With the Chinese APT Exchange exploit currently on the loose, I wonder if this little phishy is a part of that exploit. I was teaching this week, and by the time I got around to analyzing it, the exploit appears to have been taken down.
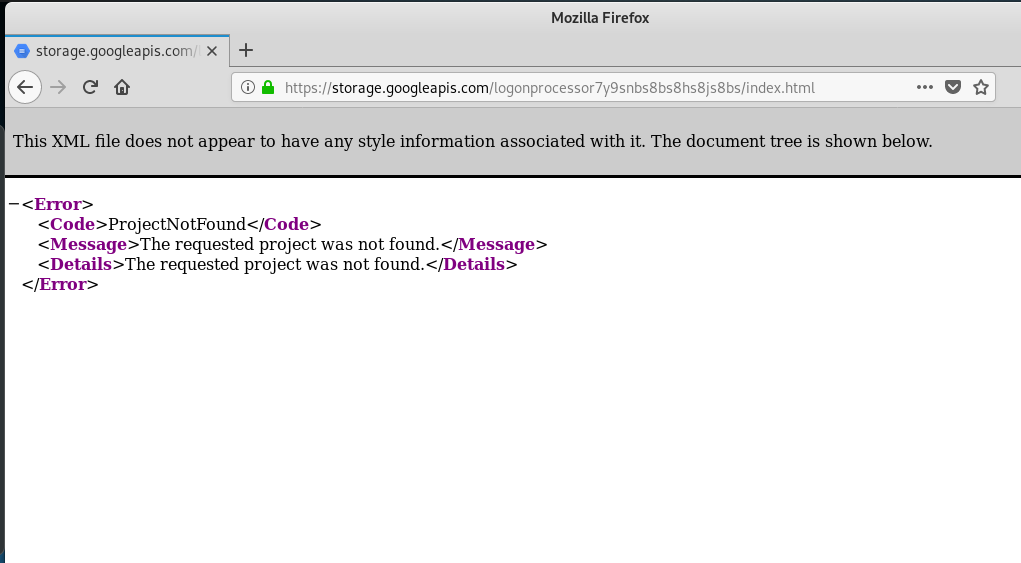
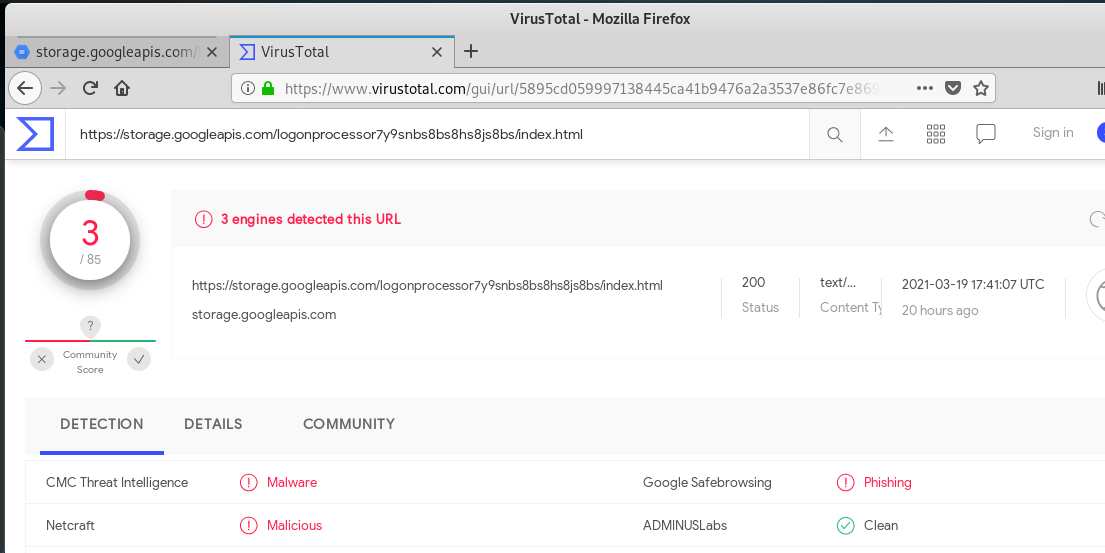
The link in the email resolved to https://storage.googleapis.com/logonprocessor7y9snbs8bs8hs8js8bs/index.html.
But the site was down when I got there.
Virustotal declared the link to be malicious.
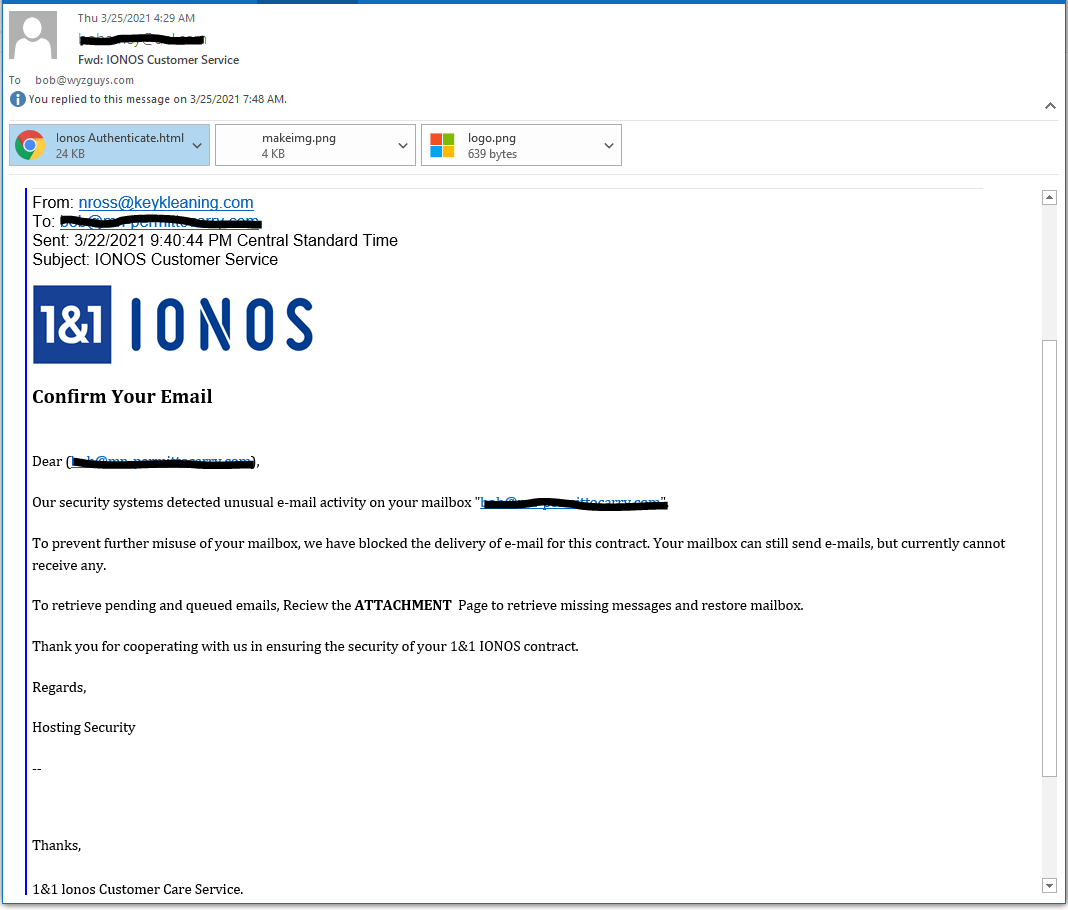
IONOS Email Blocked Phish
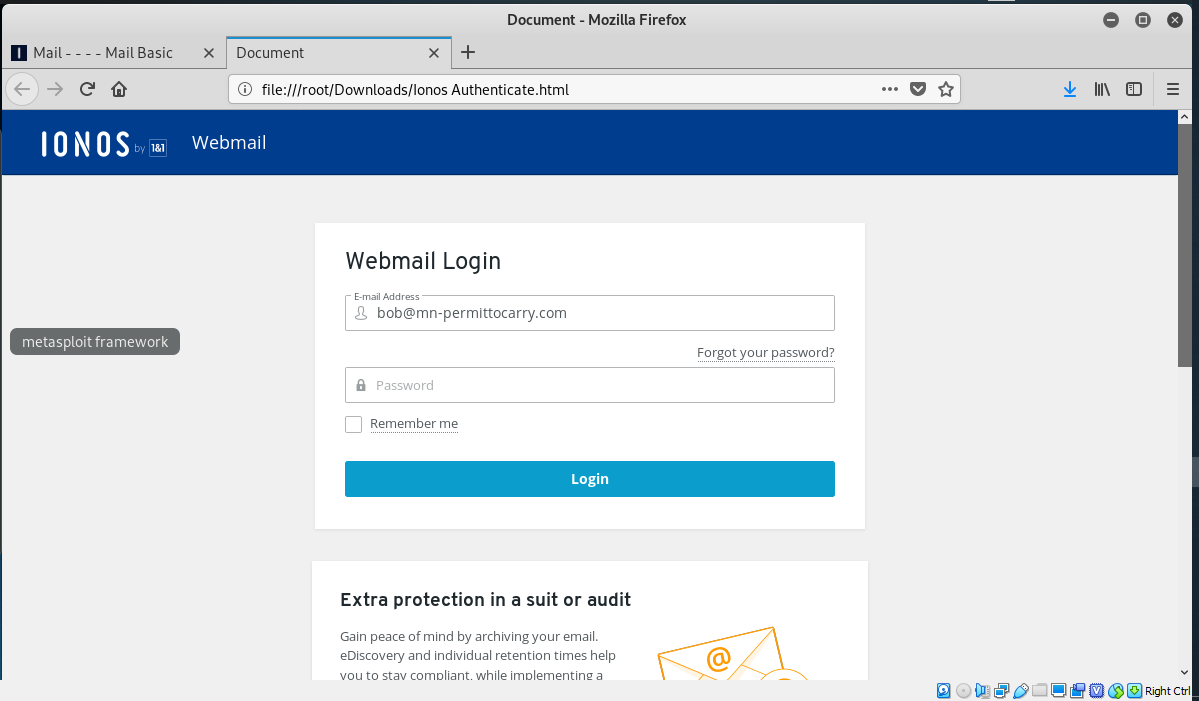
I got this forwarded from a client who wanted to know if this is a scam, and it is. The senders email address is on the wrong domain keyleaning.com. Instead of a link to a fake login page on a hijacked website, this exploit carries it’s own web page as an HTML attachment. The web page is built inside your computer browser. Clever but weird. But in the end, just another credential stealer.
And the HTML page. Notice the address in the browser address bar – from my own computer.
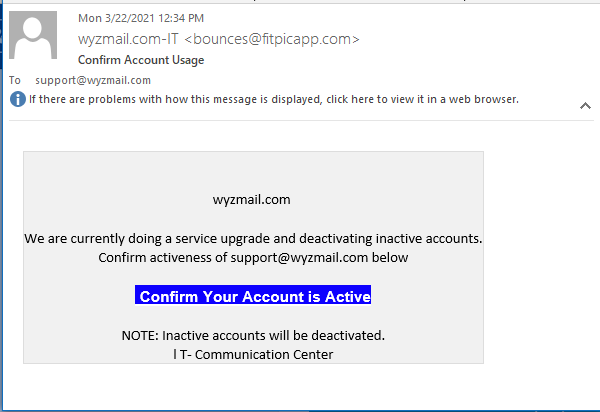
Account Activation Phish
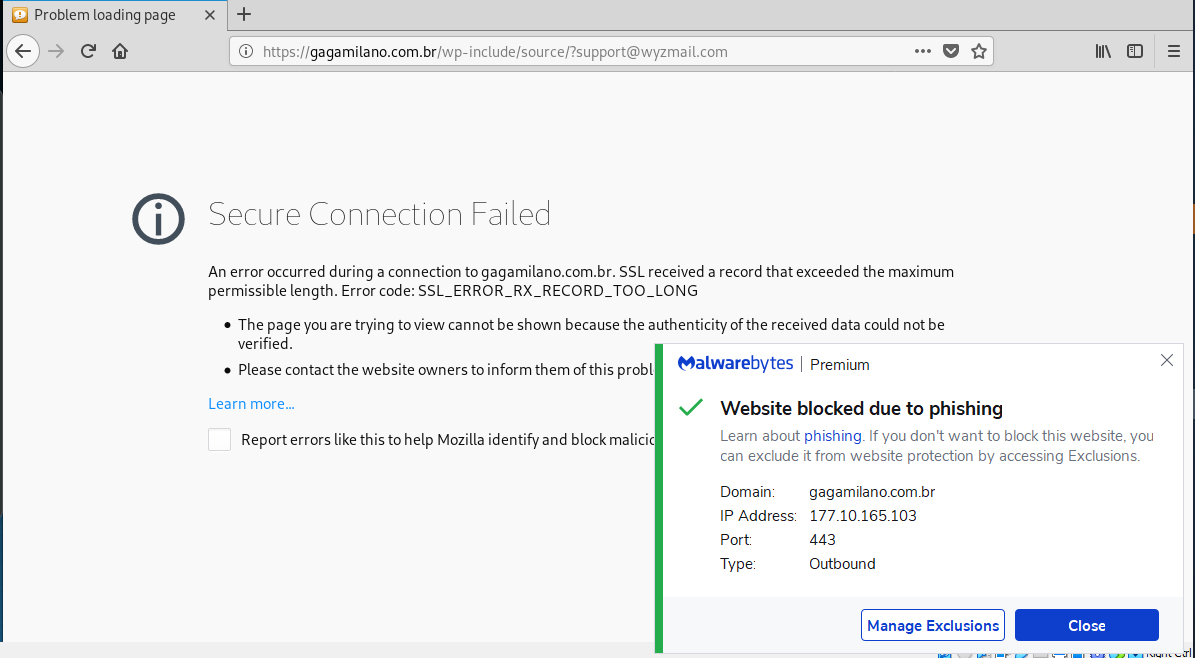
Another credential stealer. The button link resolved to https://gagamilano.com.br/wp-include/source/?support@wyzmail.com.
My first attempt to click through was blocked by Malwarebytes. Not a good sign.
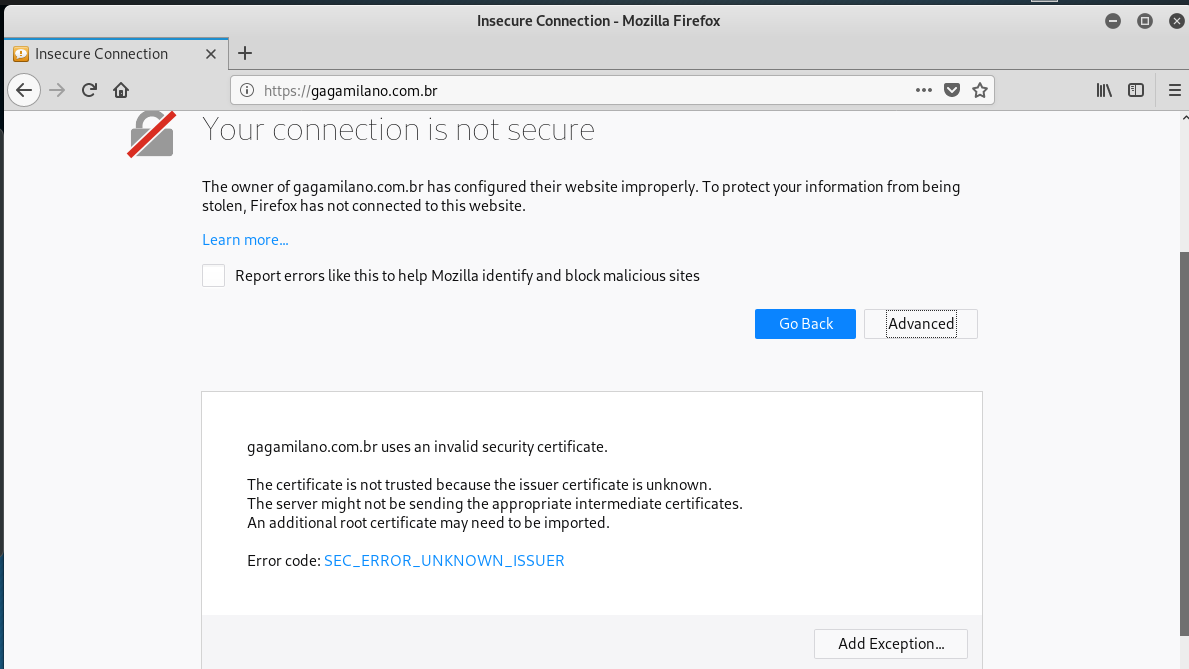
After I turned off Malwarebytes, I was directed to the usual login page. A close look at the address bar reveals the destination
I tried to get to the hijacked web site’s home page but ended up with another warning.
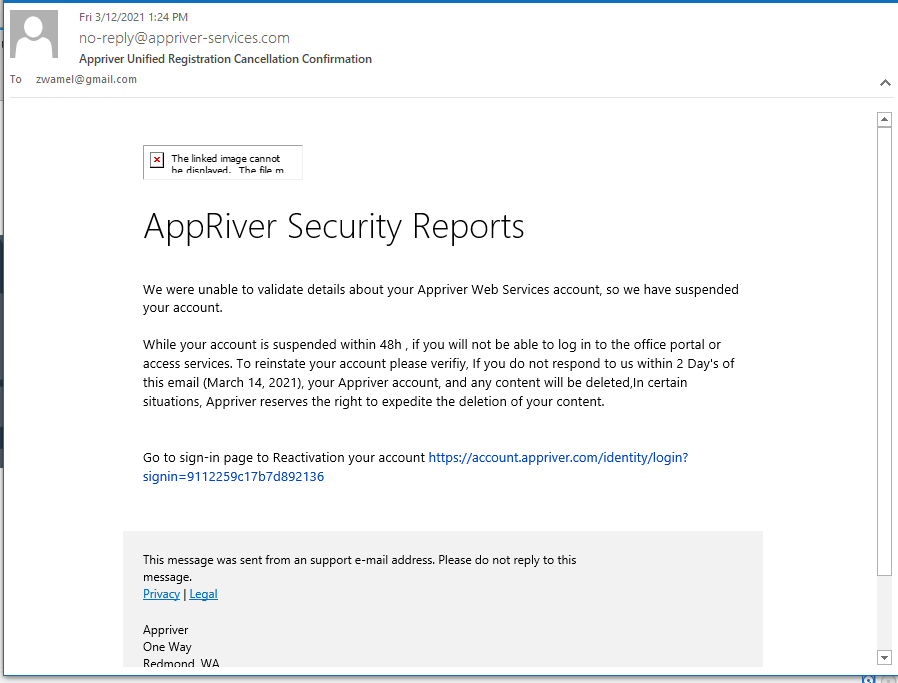
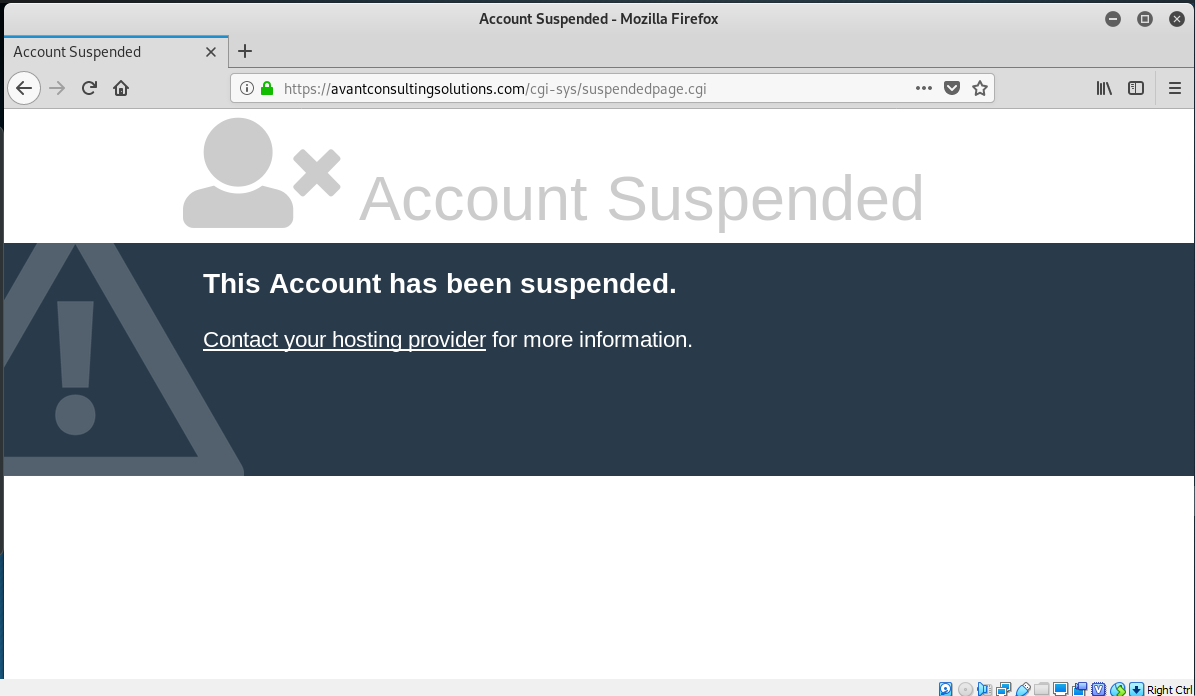
AppRiver Renewal Phish
Again I got around to looking at this exploit too late, and the mechanism was disassembled already. Proof that phish exploits are like mushrooms after a rain, popping up for a day or too, and then gone. The link https://account.appriver.com/identity/login?signin=9112259c17b7d892136 resolves to https://avantconsultingsolutions.com/lt5133, but the landing page site is down.
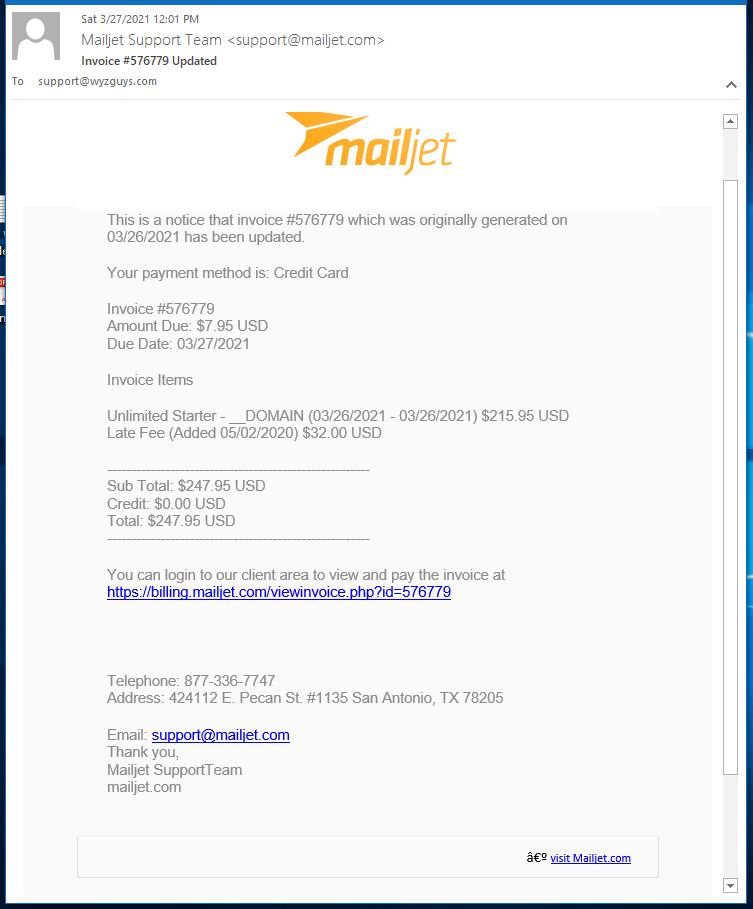
MailJet Phish
Another credential-stealer. The Mailjet link resolved to a Sendgrid location https://u14833240.ct.sendgrid.net/ls/click?<redacted>. Too new to be detected by VirusTotal yet. Email and landing page follows.
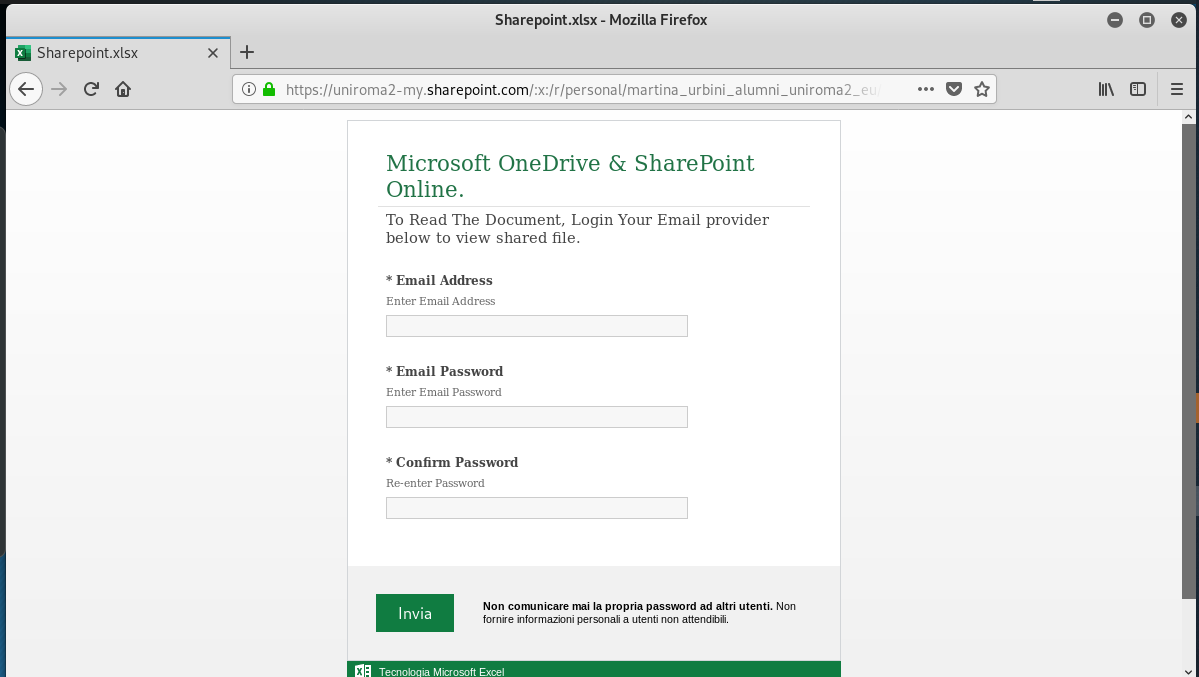
OneDrive/SharePoint Phish
Yet another credential stealer – this time for your all important Microsoft account. This has the potential for a Business Email Compromise (email account hijacking.) The OneDrive link resolved to https://uniroma2-my.sharepoint.com/personal/martina_urbini_alumni_uniroma2_eu/_layouts/15/guestaccess.aspx?<redacted>. The email and landing page follows. No alerts on Virustotal yet.
Share
APR








About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com