Phishing Email Alerts
Catch of the Day: PPC Fraud Phish
Chef’s Special: Domain Name Registration Scam Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
So many good phish this week. The nets have been empty with slim pickings for a while. Not this week, nets are full of phish. Be sure to take a moment to enjoy this week’s catch.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
What Google learned from 1 billion evil email scams
Google teamed up with researchers from Stanford University to analyze 5 months’ worth of emails. This is what they found. Keep reading
This is an interesting, detailed, and relatively short article and definitely worth the read. Also
New research reveals who’s targeted by email attacks
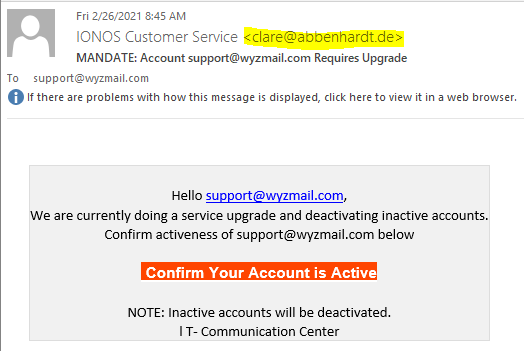
Pay-Per-Click Fraud Phish
This is special. Clicking on the link in the email sent my query through at least three web site portals. The web site all had something in common: they were “information” or “search” sites, and they are designed to make money for their site owners through PPC or pay-per-click advertising. I am pretty sure that the phisher who sent the original email to me also got a PPC payment for driving traffic to these three search sites.
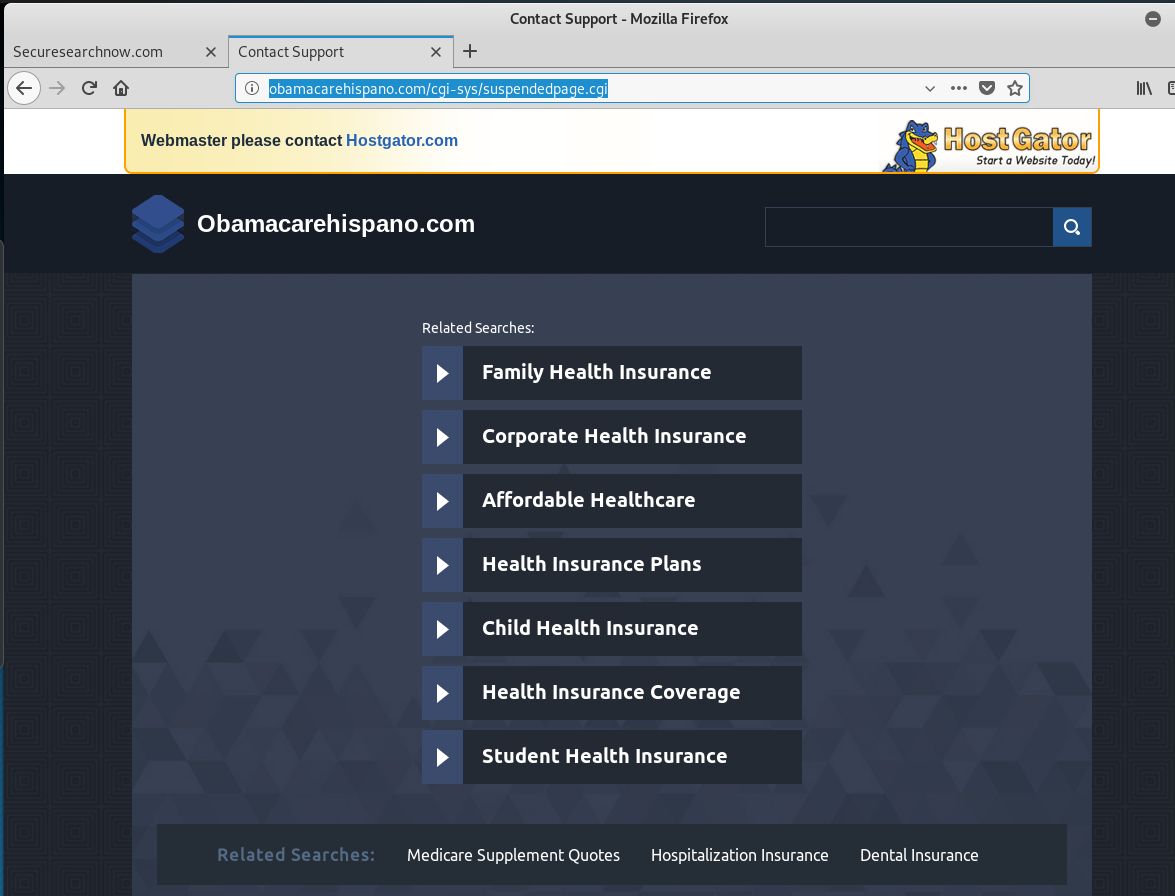
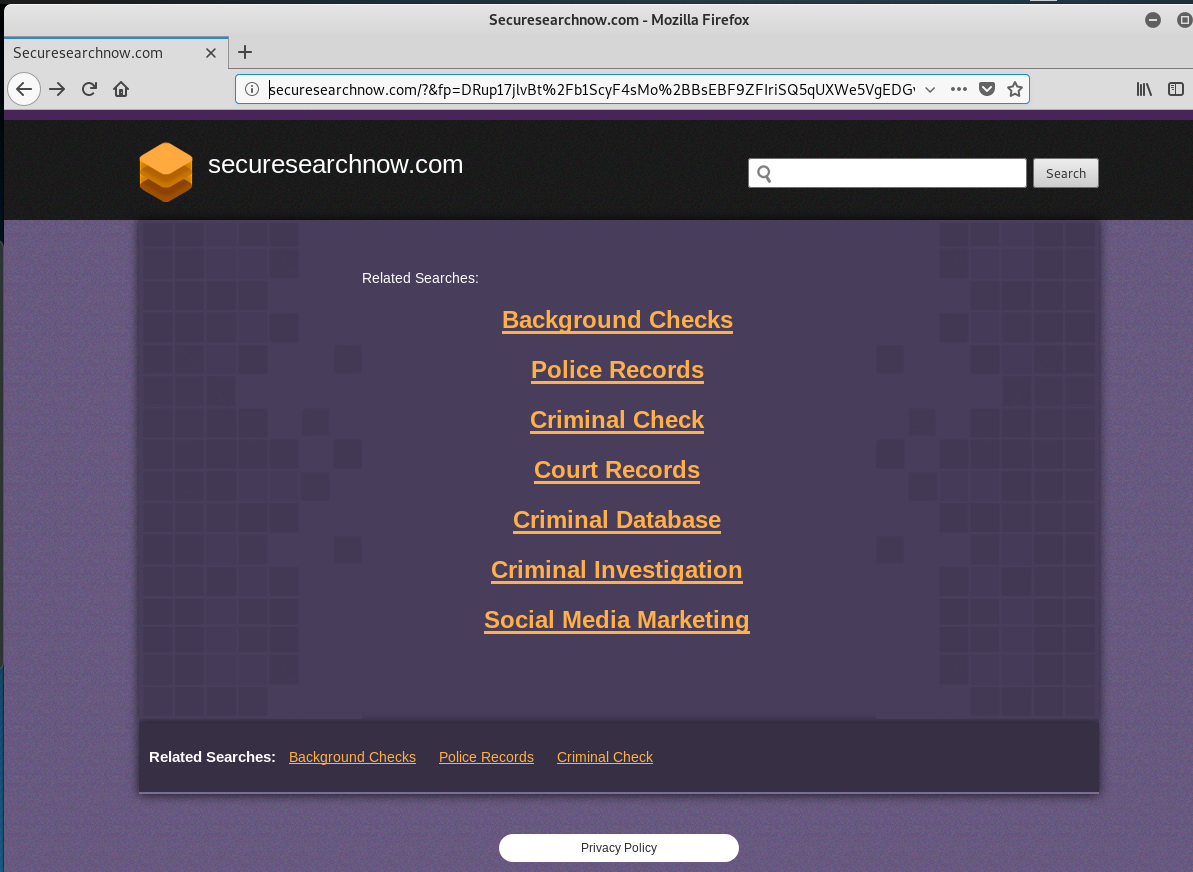
The email link sent me to the web sites below, in quick succession, one after the other. We can see the the original link to obamacarehispano.com was been taken down by HostGator for fraud. I suppose it is a matter of time for the other two.
In this case the recipient of the phishing email (me) was just an agent to generate the clicks and get the phisherman paid.
Rapidly clicked through these URLS, which I have obfuscated a bit:
<http>://obamacarehispano.com/so7/source/?email=support@wyzmail.com
<http>://obamacarehispano.com/cgi-sys/suspendedpage.cgi (Page suspended by HostGator)
<http>://securesearchnow.com/?&fp=DRup17jlvBt%2Fb1ScyF4sMo%2BBsEBF9ZFIriSQ5qUXWe5VgEDGv8NAi%2FGPpxVz0drK2Bh8nvujuOBog2M8BtYcSnlUIGRk2l5wSSIHu1ACALDvT7lr3tIzAygfIu%2FHEh8tZbseOwbc8%2FtZd7CWn3PsIL4iT1YHJoB%2FLcRyhQ74S5o%3D
<https>://www.finder.com/compare-auto-insurance?utm_source=adnet&utm_medium=cpc&utm_term=a0135831982117491242135479935188489215107&anid=0135831982117491242135479935188489215107
And these are the three pages.
Domain Name Registration Scam Phish
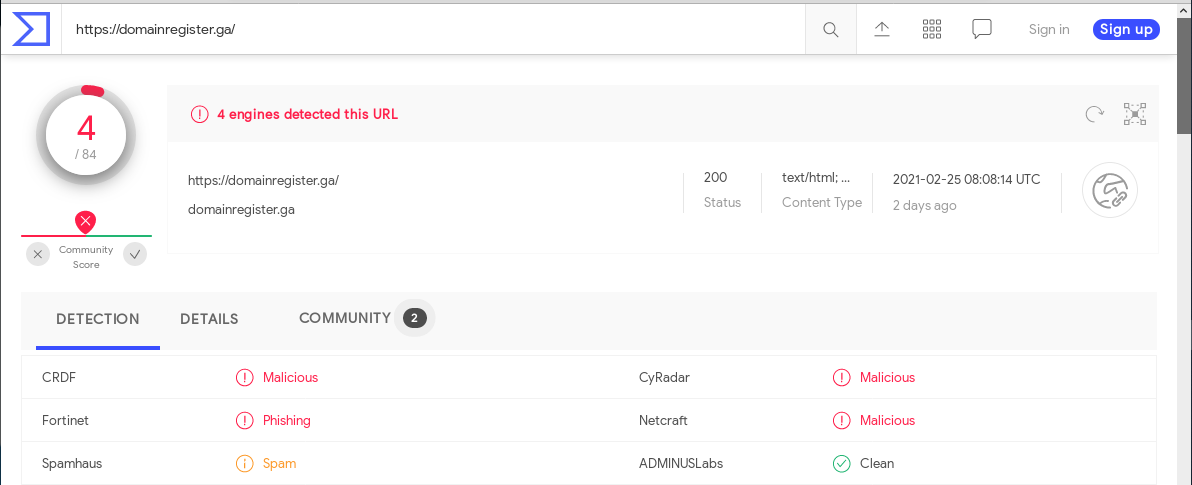
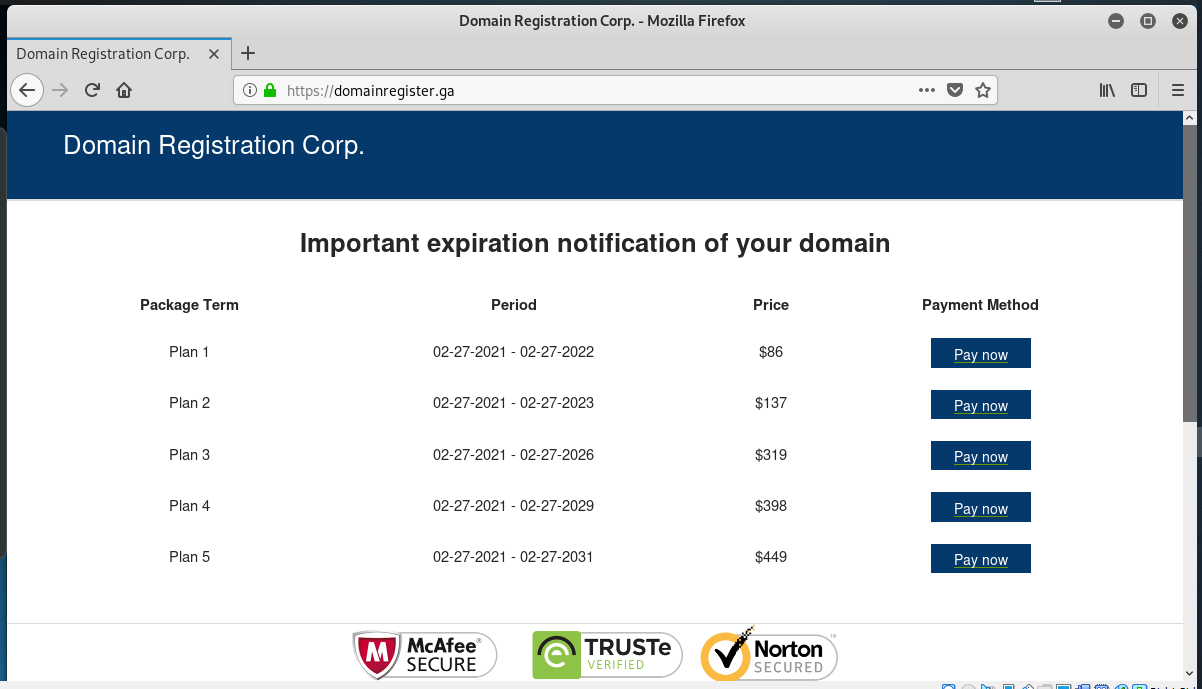
Its been a while since I’ve received a domain name registration scam. This phishing email was actually sent from my own web site using the contact web form. The links are legitimate, they resolve to a page at domainregister.ga. The GA country TLD is for the African nation of Gabon. Virustotal reports this as a spams and phishing scam The page is set up to look like a domain name renewal order form, but any payments made to this page just go in the pockets of the scammer.
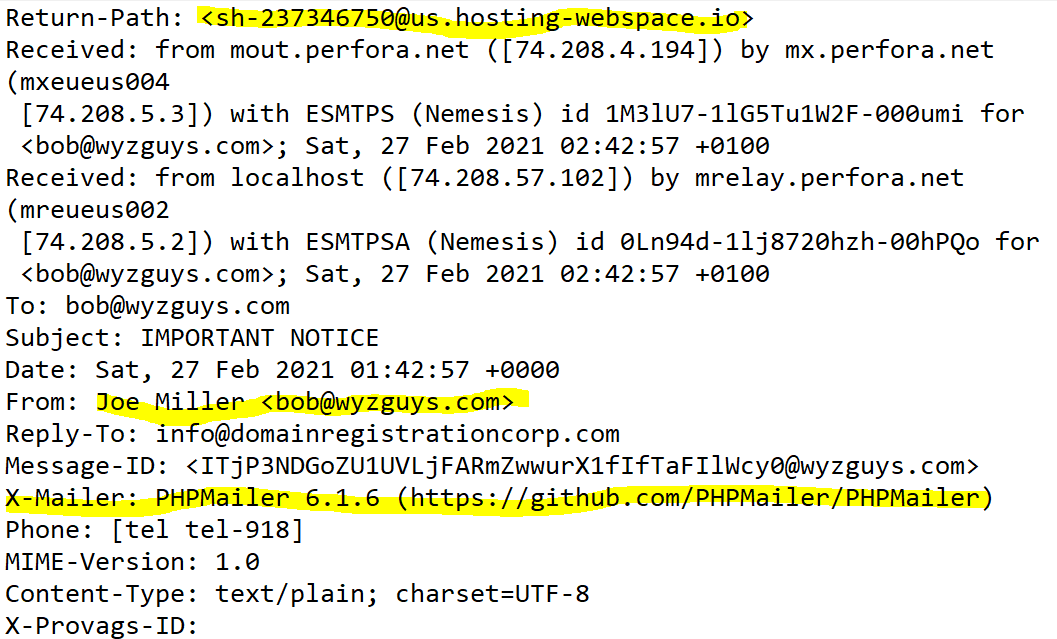
Here is the phishing email that was generated from my web form:
The return address of the sender is revealed in the email headers
Below is the Virustotal report
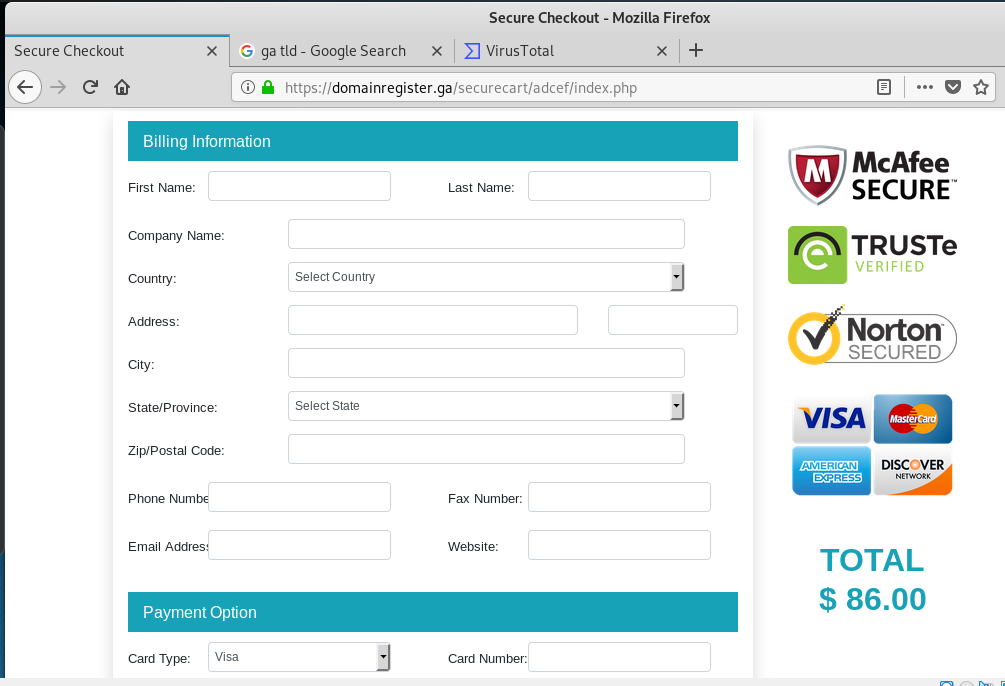
And here is the “registration” landing page. The good news is that this does not appear to be a domain transfer and registration scam, just a straight up payment scam designed to take your money. And a little PII and a credit card number.
DocuSign Phish
Here’s a threat feed from AlienVault OTX that might be referring to this little phishy.
DocuSign Malspam Delivers Qakbot and Leads to Cobalt Strike
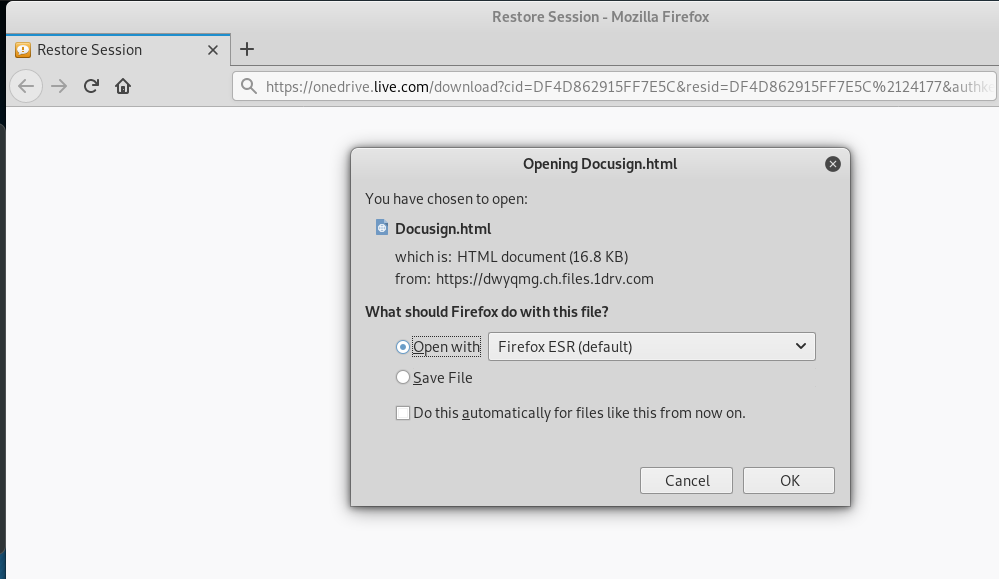
The first clue that this is a phish is the fact that the link resolves to a OneDrive page at https://onedrive.live.com/download?cid=DF4D862915FF7E5C&resid=DF4D862915FF7E5C%2124177&authkey=ACqSLMggfVhNCR8. A download box appears, and when I clicked through an HTML page appeared. The web page I am displaying was actual delivered to my Kali Linux VM and displayed from a temporary location.
Here is the phish. Notice the sender’s address, it has nothing to do with Docusign. Actually, no part of the exploit involved Docusign. Both links resolve to OneDrive. Virustotal reports the link as malicious.
Here is the download dialog. I will be downloading a web page, which I show below.
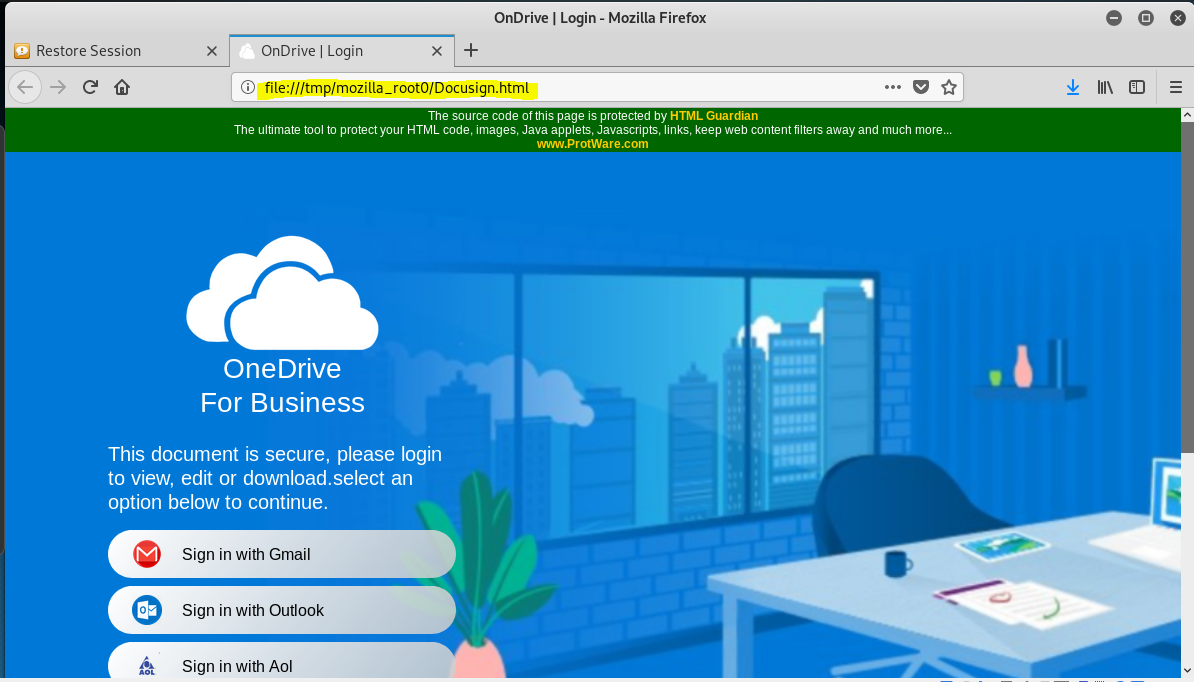
The landing page looked like this
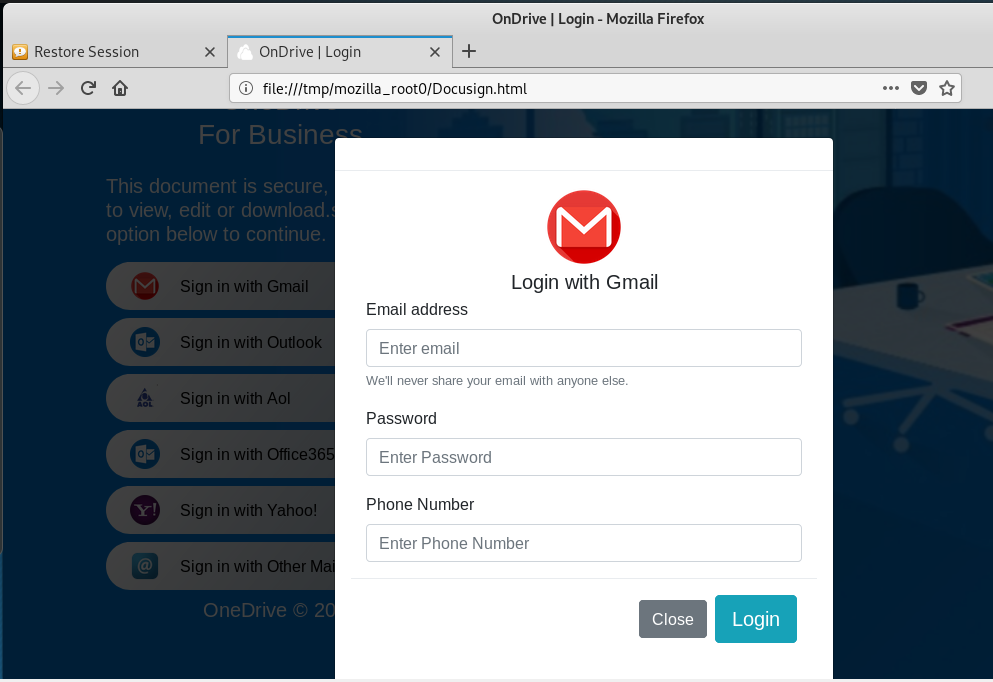
A lot of fine credential stealing options are possible.
Then I submitted some fake credentials
I got a quick look at a fake invoice, then an error message.
What was most interesting about this exploit was the downloadable HTML landing page. No hijacked web server was required.
OneDrive Phish
This is another scam set up to convince the recipient to download a file waiting at OneDrive. This email sat in my inbox for a day, before I had time to analyze it, and the “Excel” file was no longer available download. Instead I got an error message. The download would have probably been a Trojan horse or some other malware code.
The link resolves to https://dutadamaisulawesiselatan.id/MicrosoftOneDrive/OneDriveupdated/OneDrive. The country TLD ID is for Indonesia. The landing pages are hosted on a hijacked Indonesian website.
Email is below:
And here is the first landing page.
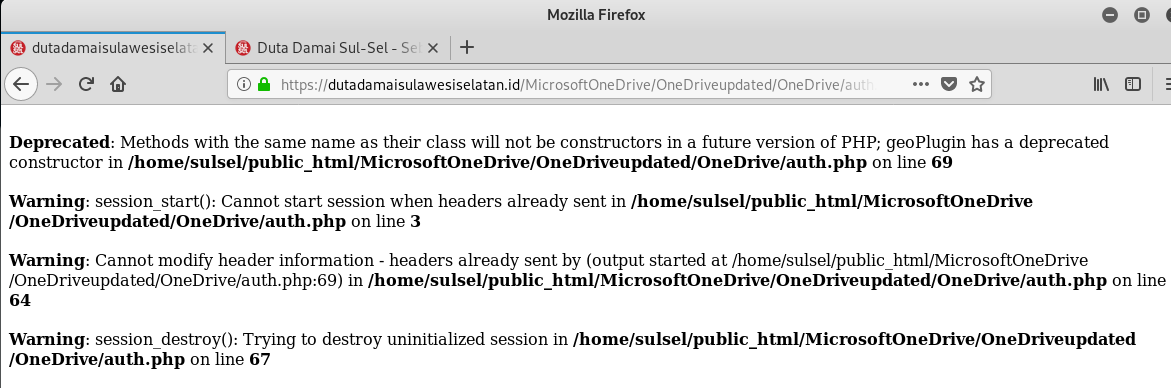
This is what happened when I attempted to download the file into my Kali Linux virtual machine.
And the error response.
And here is the other victim, the hijacked Indonesian website.
Share
MAR













About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com