Phishing Email Alerts
Catch of the Day: Morse Code Attack
Chef’s Special: IONOS Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
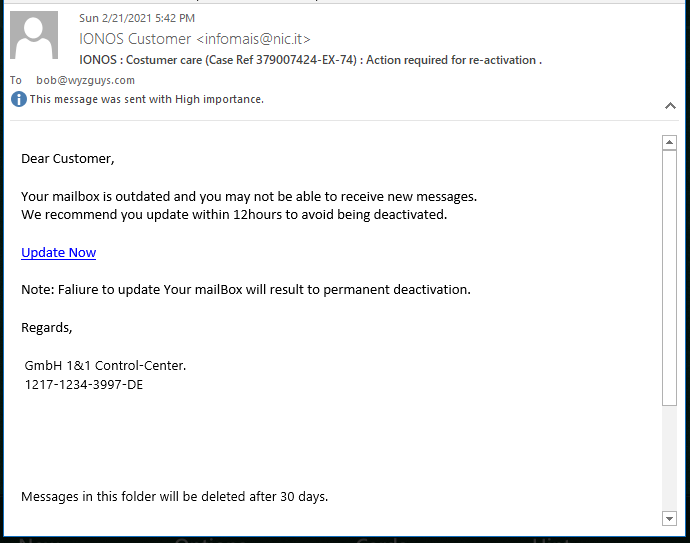
IONOS Credential Stealer
Here’s another example of a credential stealing phish and web page combination. From the examples I’ve gathered, credential stealing does appear to be the leading purpose of most phishing emails. Credential stealing leads directly to account hijacking, and the most targeted account is your email account. With access to your email account an attacker can generate password reset requests on your other accounts, and access your social networks, e-commerce, and even work accounts.
The phish:
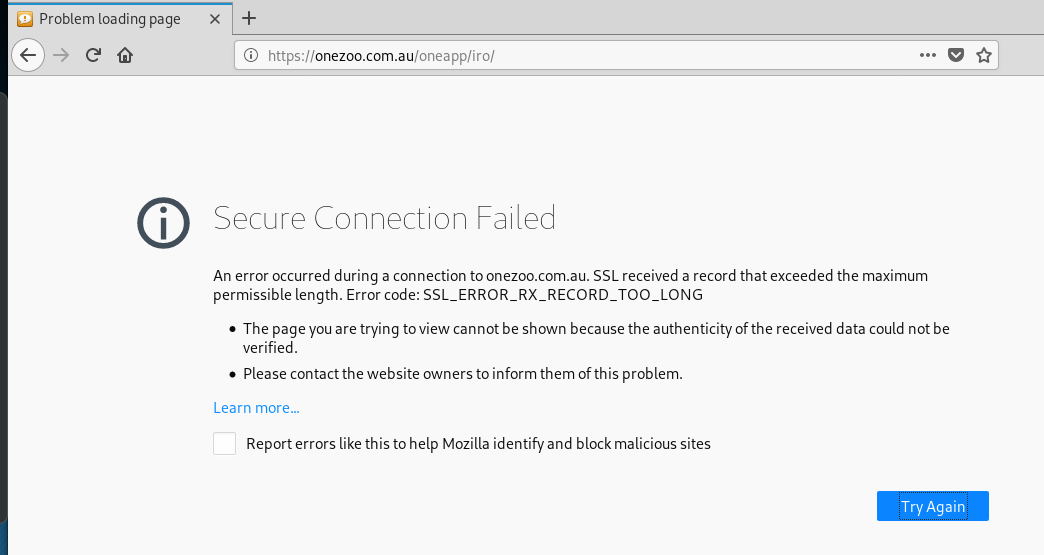
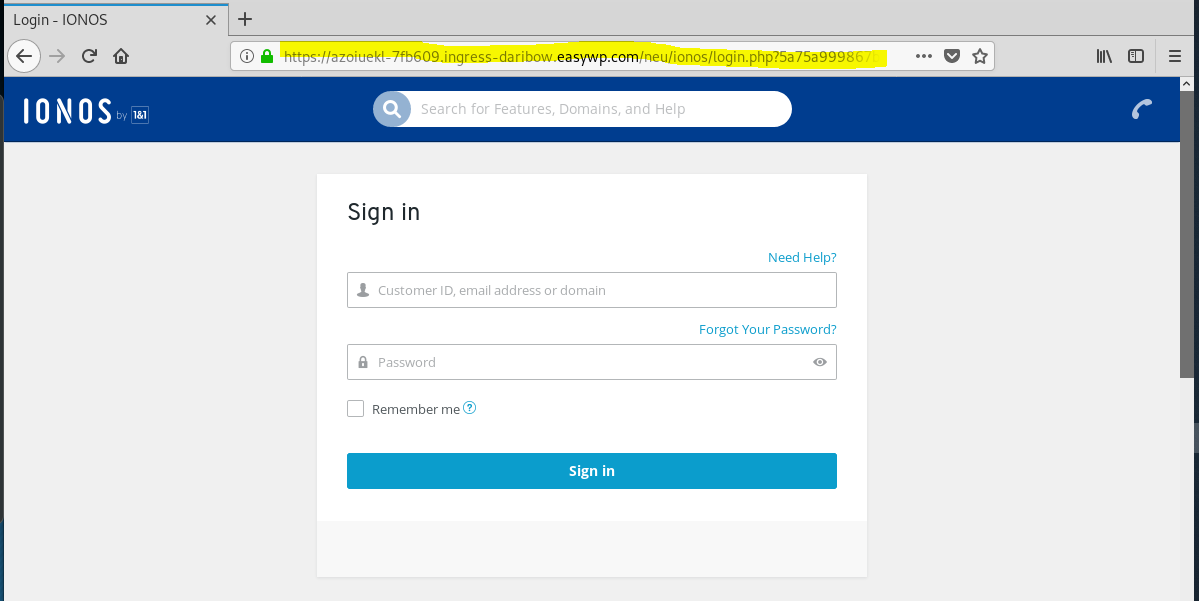
The Update Now link resolves to https://onezoo.com.au/oneapp/iro/ which redirected to https://azoiuekl-7fb609.ingress-daribow.easywp.com/neu/ionos/login.php?5a75a999867bb6039468980021ad69d3797af9bd. Virustotal reported this as a phishing link.
The first attempt to connect to the landing page was blocked by Malwarebytes, so I closed MB and tried again. The error page and the landing page follow.
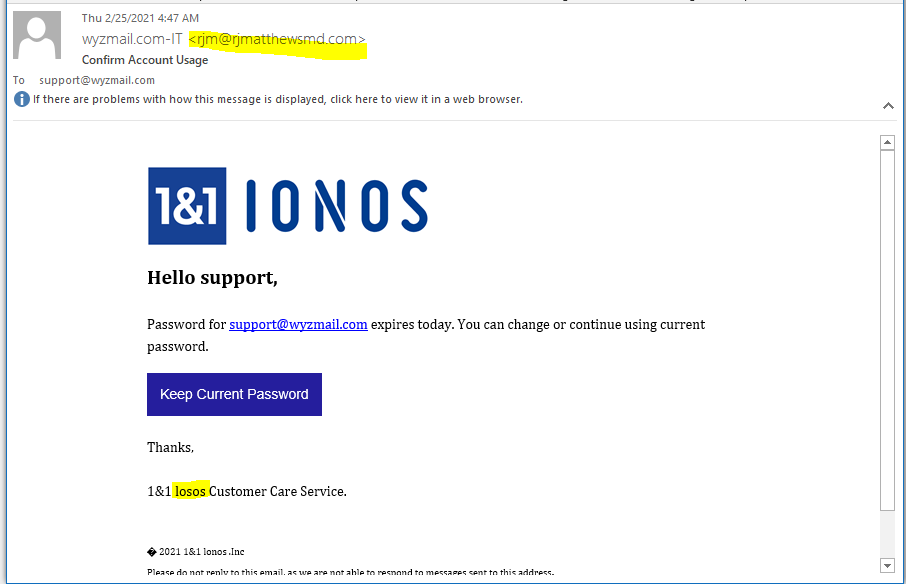
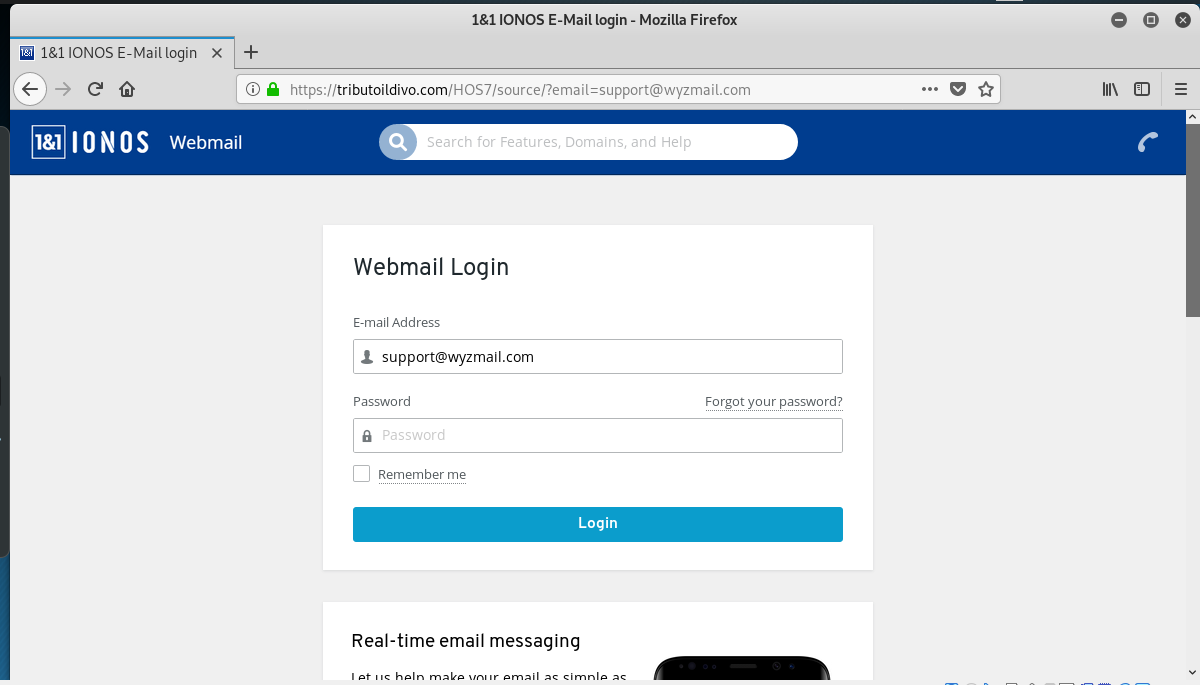
Another IONOS Phish
Below is the email, and the button links to this address: https://tributoildivo.com/HOS7/source?email=support@wyzmail.com. Virustotal did not flag this link,
The landing page.
[HEADS UP] New Phishing Attack Uses Morse Code to Avoid Detection By Your Email Scanners
Yes – you read that right: Cybercriminals have found a way to use 1830’s technology to trick 2020s security solutions into not identifying phishing attachments as malicious.
Like you, when I first read about this I shook my head and through “no way – how would that even work?!?”” But according to a post on reddit, the bad guys realized they could digitally encode their malicious java script in Morse Code, effectively bypassing any email scanners.
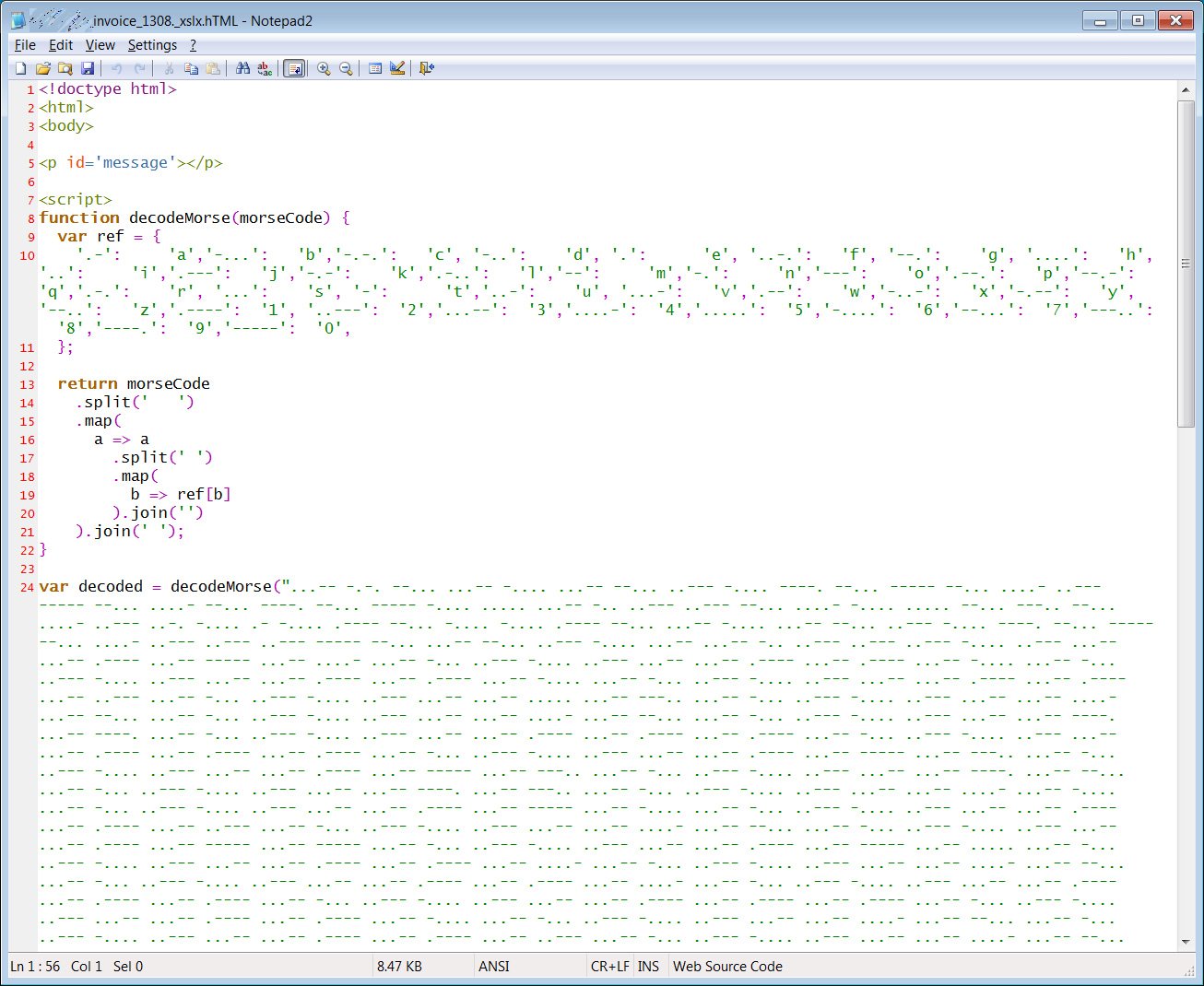
The phishing attack starts out like any other, using some basic social engineering around paying an invoice and hosting an attachment made to look like an invoice with the filename ‘[company_name]_invoice_[number]._xlsx.hTML.’
But upon further inspection of the attachment, it leverages JavaScript, containing a basic decoding function where each letter and number is assigned a Morse code value, and then calls to decode a massive amount of Morse code stored within the file.
The result is when the html attachment is scanned, its contents appear benign to a security solution. But when run, the script converts the Morse code into two additional JavaScript tags that are injected into the page and executed.
The result of all this is a pretty creative rendering of a fake Excel document and an Office 365 logon screen, stating the user’s session had timed out.
Creative? Yes. Unique? No – bad guys can derive even their own simple character replacement encoding (e.g., ‘A’ would be replaced with ‘D’, ‘B’ with ‘E’, etc.) and one can achieve the same result.
The real stopping point here is the bogus email theming and horrible attachment name. Users that get stepped through security awareness training are able to quickly see this for what it is and stop the attack before it goes any further than making it past your filters.
Blog post with example screen shot:
https://blog.knowbe4.com/new-phishing-attack-uses-morse-code-to-avoid-detection-by-email-scanners
Cannabis Company Loses Millions in BEC Scam
Australian medicinal cannabis company Cann Group has lost $3.6 million in a business email compromise (BEC) attack, Stockhead reports. The company had thought it was paying an unnamed “overseas contractor,” but the payments were actually going to “an unknown third party.” The attack was discovered overnight on February 4th, and the fraudulent payments were related to the construction of the company’s 34,000 sq/m growing facility in Mildura, Victoria.
Cann Group said it’s “working with its bank to determine if any of the payments can be halted and if any of the funds involved are recoverable.” The company added that “[t]he matter has been reported to police in Victoria, Australia, the Netherlands and Hong Kong, as well as the Office of Drug Control.” The company’s stock price fell 6% upon the news.
Blog with links:
https://blog.knowbe4.com/cannabis-company-loses-millions-in-bec-scam
Share
FEB






About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com