Phishing Email Alerts
Catch of the Day: Chase Suspicious Activities Phish
Chef’s Special: Malwarebytes Fake Invoice Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
Blocked Emails Phish
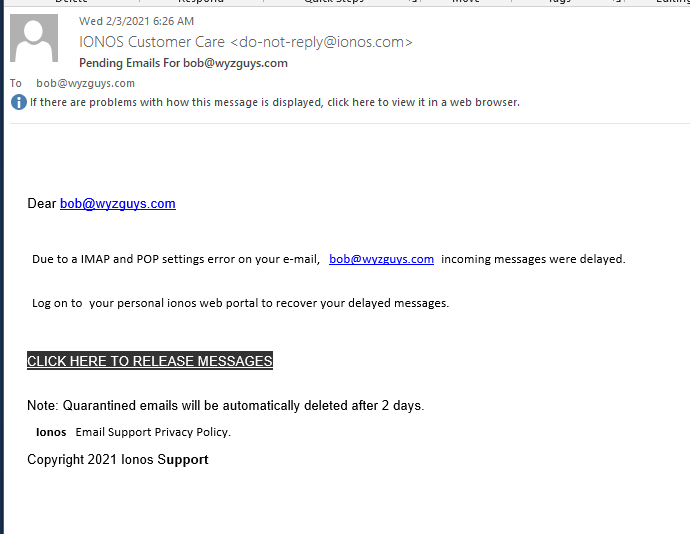
This phish was deliverd to my inbox today. Nice job spoofing the sender address to make the email look authentic. The Click Here to Release Messages link resolves to https://lstimmetals.com/1d457989c863042bfa5bb5d39e04d020/?email=bob@wyzguys.com. Here is the email:
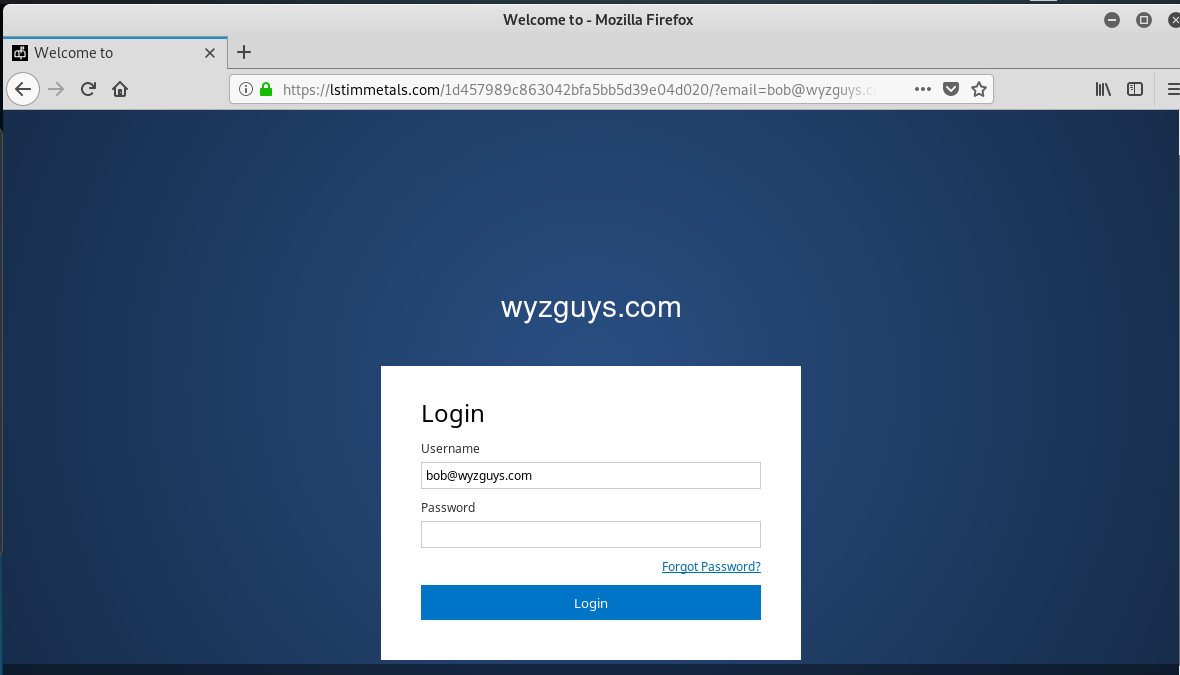
This is the landing page. Again, a fairly straightforward credential stealing exploit using the fear of “lost emails” to convince me to click through.
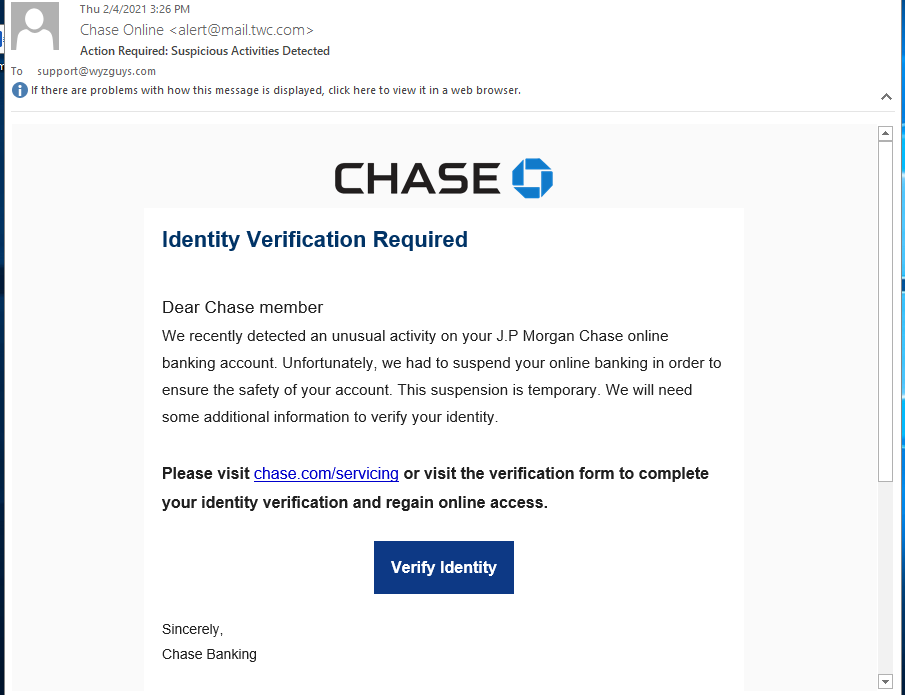
Chase Suspicious Activities Phish
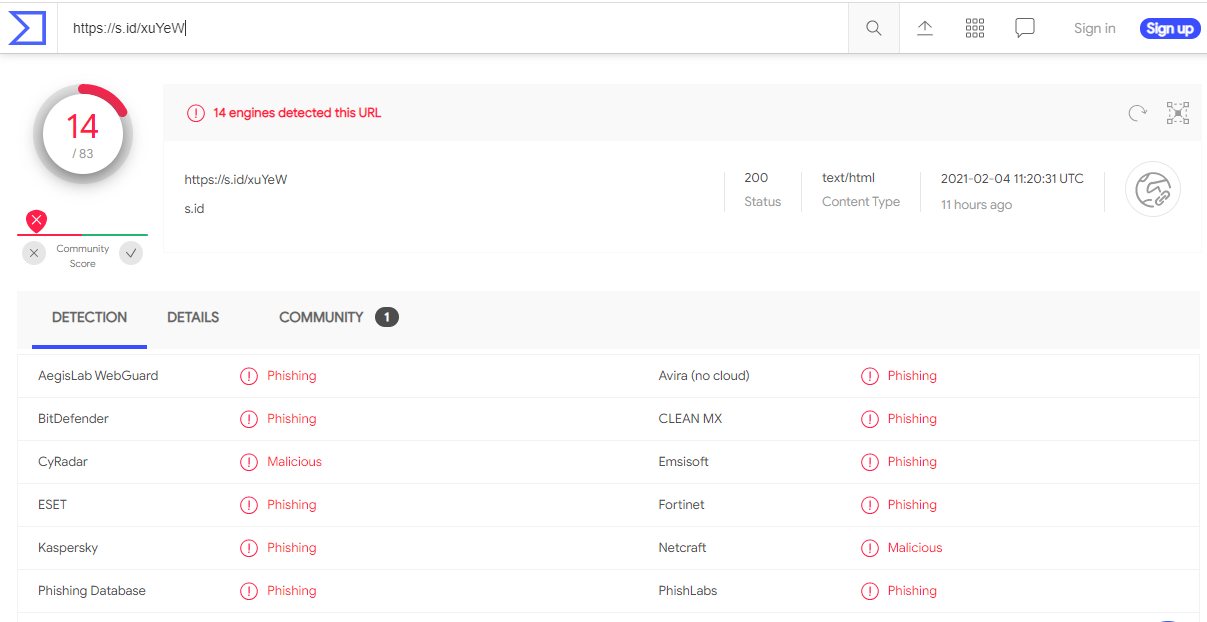
There were a couple of tips that this email from Chase was a phish. The return (sender) address was from a non-Chase domain, mail,twc.com, and this email was send to an email address of mine that I never use for setting up a financial account. The links both resolve to https://s.id/xuYeW. A quick check at Virustotal reported that this URL is a known phishing address. When I tried to follow the link, it redirected me to https://a3ashop.org/user/SpoxV5, but the landing page was already down, Here are the images. The email is pretty convincing just to look at it, which is why I am posting it here.
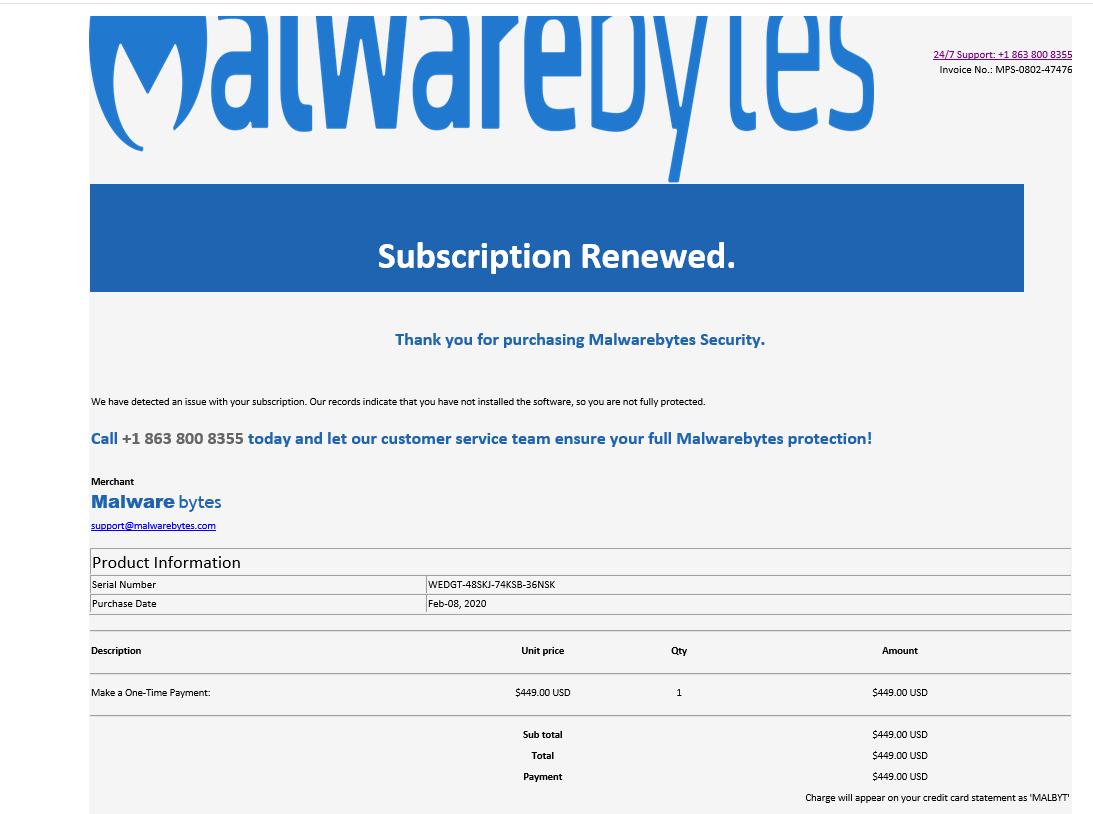
Malwarebytes Fake Invoice Phish
I was forwarded this email by a client. Malwarebytes does not cost $499.00 ! This phish was designed to create a phone call back to the cyber-criminals at the telephone number on the invoice.(862 800-8355) I’m sure this number gave the crooks an opportunity to actuallu get paid, as well as collecting a credit card number they could use elesewhere.
There were obvious problems with the email, the Malwarebytes logo expanded across two screens, which made the email unusually huge..
Vicious New Phishing Kit Spotted on Over 700 Domains
A cybercriminal gang has recently developed a new phishing kit named LogoKit. It changes logos and text in real-time in order to adapt to the targeted victims. This vicious phishing kit has already been released in the dark web according to threat intelligence firm RiskIQ. The firm has tracked it’s progression and in one week the kit was identified in 300 domains, and over 700 within the month.
“Once a victim navigates to the URL, LogoKit fetches the company logo from a third-party service, such as Clearbit or Google’s favicon database,” said RiskIQ security researcher Adam Castleman in a report this week. The firm also shared a screenshot of how this malicious kit works.
This kit can be very tricky to identify from standard phishing templates because most need perfect pixels that mimic the company’s authentication page. RiskIQ is still actively tracking the kit and fear that the kit’s simplicity could significantly improve the chances of a successful phishing attack.
Screenshot and links at the blog:
https://blog.knowbe4.com/heads-up-new-phishing-kit-spotted-on-over-700-domains
Full story at ZD Net
Beware the Long Con Phish
By Roger Grimes
Social engineering and phishing happen when a con artist communicates a fraudulent message pretending to be a person or organization which a potential victim might trust in order to get the victim to reveal private information (e.g. a password or document) or perform another desired action (e.g. run a Trojan Horse malware program) that is against the victim’s or their organization’s best interest.
Most are quick flights of fancy. One email, one rogue URL link, one phone call. The fraudster is counting on the victim’s immediate response as key to the success of the phishing campaign. The longer the potential victim takes to respond the less likely they are to fall for the criminal scheme.
But there is another version of social engineering and phishing that relies on a longer length of time and requires multiple actions by the victim to be successful. There are many sophisticated hackers who intentionally spend weeks or months building up rapport with a potential victim, creating a trusted relationship over time that is eventually taken advantage of.
These long-term cons can often be more devastating to the interests of the victim. Everyone needs to be aware of these types of phishing events, because, although they are far rarer, they do happen. Awareness is the key to fighting them. Let’s take a closer look at how they come to be, examples of long-term con scams and what we can do to better protect ourselves, our teams and our organizations.
CONTINUED:
https://blog.knowbe4.com/beware-the-long-con-phish
Email Phishing Is Now the Top Ransomware Attack Vector
New data shows that pushback from the ransomware victim “market” may be influencing just how much cybercriminals are asking for as ransom and are being paid.
2020 seemed to point to ransomware continuing to grow in devastation and cost; Ryuk reached a $34 million ransom payout, organizations were operationally brought to their knees by many of the prominent ransomware families, and the “as-a-Service” market for various parts of ransomware attacks – including the publishing of exfiltrated data – grew in interest.
But new data from security vendor Coveware in their Q4 2020 Quarterly Ransomware Report shows that phishing is now the prominent ransomware attack vector since RDP compromise is being prevented by potential victims.
There are also some shifts in payment amounts – fortunately in the favor of the victim organizations. According to the report:
- The average ransom payment decreased 34% in Q4 of 2020 to $154,108 from $233,817 in Q3
- The median payment also decreased by 55% in the same timeframe from $110,532 to $49,450
- Threats to disclose exfiltrated data stepped up in Q4, with a whopping 70% of ransomware attacks using this tactic (up from 50% in Q3)
Share
FEB





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com