Phishing Email Alerts
Catch of the Day: Dr Oz CBD Phish
Chef’s Special: Infosec Phishing Sim
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
Phish from a Friend
I received an email from a long time friend with nothing more than a Bitly link, two marketing messages that were unusual for her, and two addition cryptic lines of text, See the image below. Her information has been redacted for privacy.
This on first glance appeared to originate from my friend’s Yahoo mail account, but I wanted to be sure before I contacted her to advise her to check her email account and change the password. The email originated from a compromise email account at cramerfabrics.com. My friend’s email address was simply spoofed on this email. I am including the email headers. The headers show the email servers that were involved in sending the message. Notice the first email server is the one at Cramer Fabrics, and the Yahoo email server is nowhere to be found
Return-Path: <pete@cramerfabrics.com>
Received: from mail.cramerfabrics.com ([64.140.248.216]) by mx.perfora.net
(mxeueus006 [74.208.5.3]) with ESMTPS (Nemesis) id 1M3TyA-1kO1iI3PJS-000cdY
for <bob@wyzguys.com>; Wed, 30 Sep 2020 06:12:44 +0200
X-Ninja-PIM: Scanned by Ninja
X-Ninja-Antispam: Policy 1 – Allowed – Final Score – 0,0,0 (0)
X-Ninja-AttachmentFiltering: (no action)
X-Ninja-AttachmentFiltering: (no action)
Received: from mail.cramerfabrics.com (27.72.240.159) by
mail.cramerfabrics.com (192.168.254.3) with Microsoft SMTP Server (TLS) id
14.3.487.0; Wed, 30 Sep 2020 00:12:42 -0400
Subject: [redacted for privacy]
From: [redacted] <[redacted]@yahoo.com>
Content-Type: multipart/alternative;
boundary=”Apple-Mail-BAA3F6FC-082D-4562-B9B1-3C20037A6897″
X-Mailer: iPhone Mail (17B84)
Message-ID: <9BEE6BC5-06F4-467E-B282-5F006FAE3BA4@yahoo.com>
Date: Tue, 29 Sep 2020 20:12:16 -0800
To: Robert and Cheri <bob@wyzguys.com>
Content-Transfer-Encoding: 7bit
MIME-Version: 1.0 (1.0)
Envelope-To: <bob@wyzguys.com>
X-Spam-Flag: NO
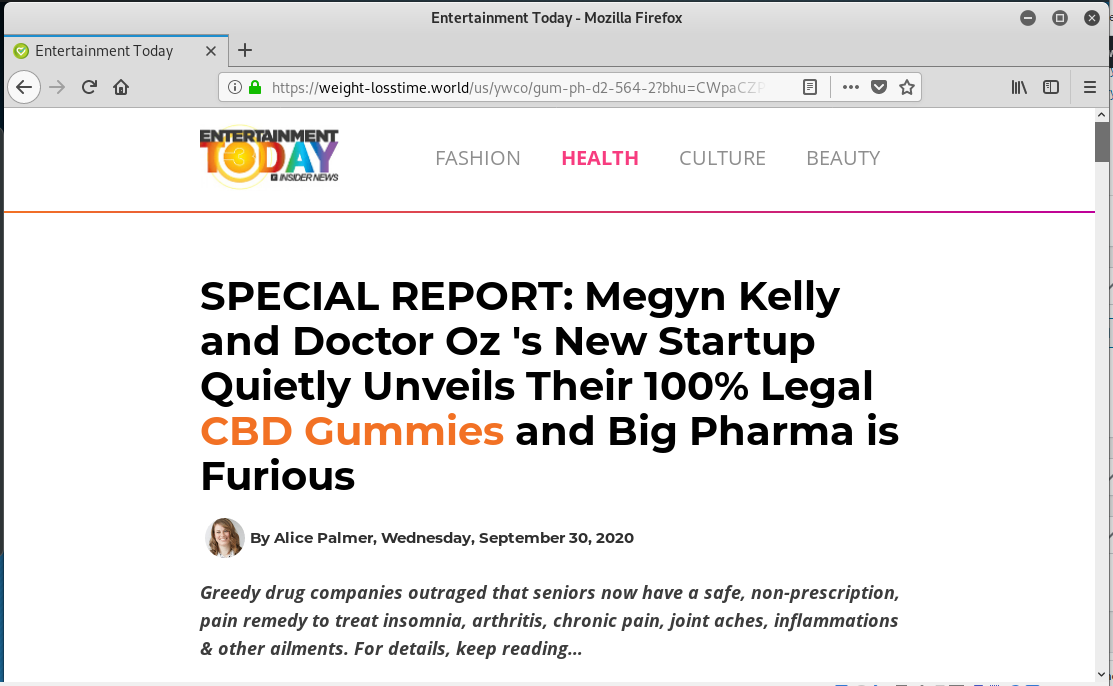
The Bitly link tested positive as a phishing link on VirusTotal. The link resolved to https://weight-losstime.world/us/ywco/gum-ph-d2-564-2?bhu=CWpaCZPRv1r3gaN92DQQtcgTzbShhcWYUo6Lu When I clicked through using my Linux virtual machine, I landed on this Dr Oz Weight Loss landing page that was pimping CBD gummies. This may be more of a spam than a phish, and it certainly seems to be part of some affiliate marketing scheme, rather than a credential grab. Just remember to keep an eye out with atypical emails from people you know.
Phishing Simulation from Infosec
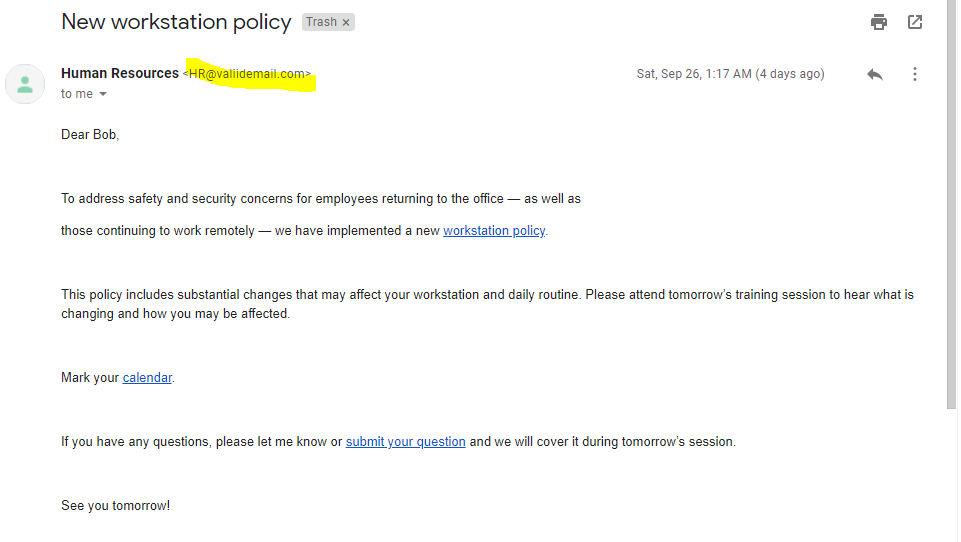
Yesterday I was catching up on my Infosec inbox, and took a quick look at the following email, and clicked the calendar link. I failed to notice the unusual sender email address. It was a simulated phishing email sent by my employer. The penalty for my inattention was watching a 15 minute video training module. When you are allegedly and “expert” in the field, getting caught is embarrassing.
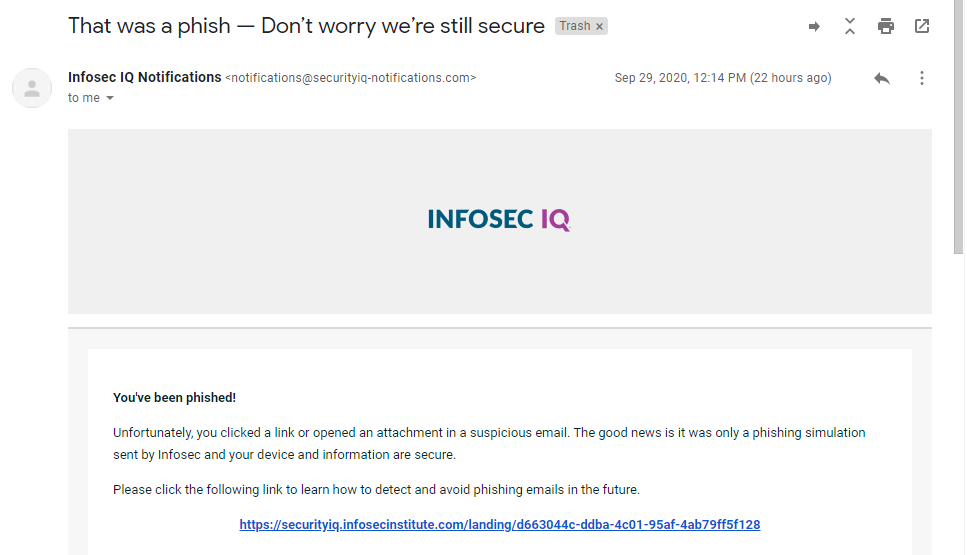
I immediately received an email with a training link. This is the kind of simulated phishing email test you should be running in your organization. As they say, if you are interested, I know a guy.
What Is the NIST Phish Scale?
The National Institute of Standards and Technology (NIST) has developed a new method to help prevent organizations and their employees from falling victim to phishing cyberattacks, which it calls the Phish Scale. A tool like the Phish Scale could be very useful for organizations in the fight against phishing. Research shows that more than 90% of cyberattacks start with a phish. The costs are adding up… Read more
ShareOCT






About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com