 Friday Phish Fry Episode 200
Friday Phish Fry Episode 200
This episode marks the 200th edition of our weekly Friday Phish Fry. Hopefully you have enjoyed these posts and learned how to recognize and protect yourself from these exploits.
Phishing Email Alerts
Catch of the Day: IONOS Account Suspended Phish
Chef’s Special: IONOS Voicemail Phiosh
Also serving: Zero-Click Phish with GenAI Worm, Geek Squad Phish
Examples of clever phish that made it past my anti-spam nets and into my inbox. Some are contributed by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
IONOS Account Suspended Phish
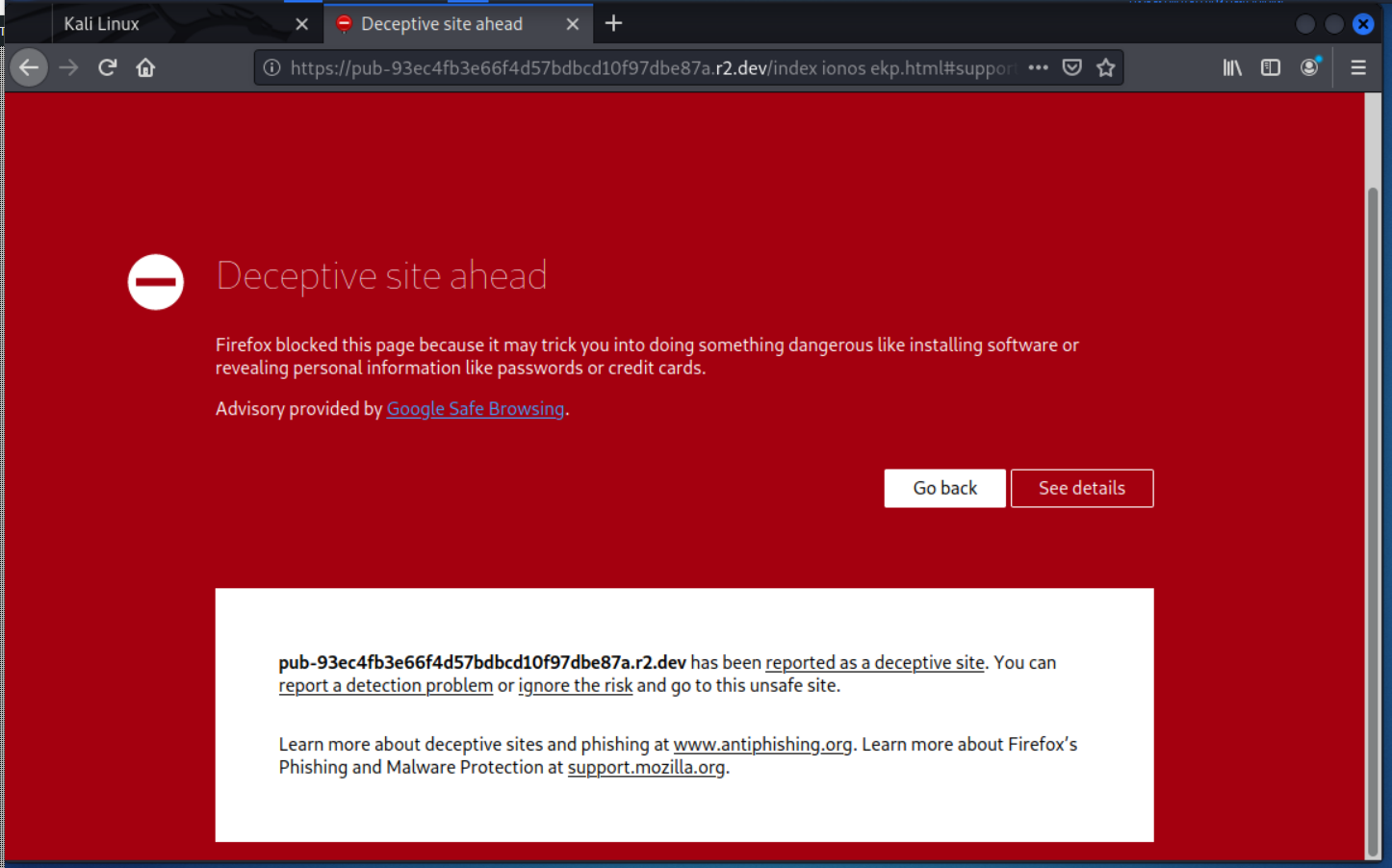
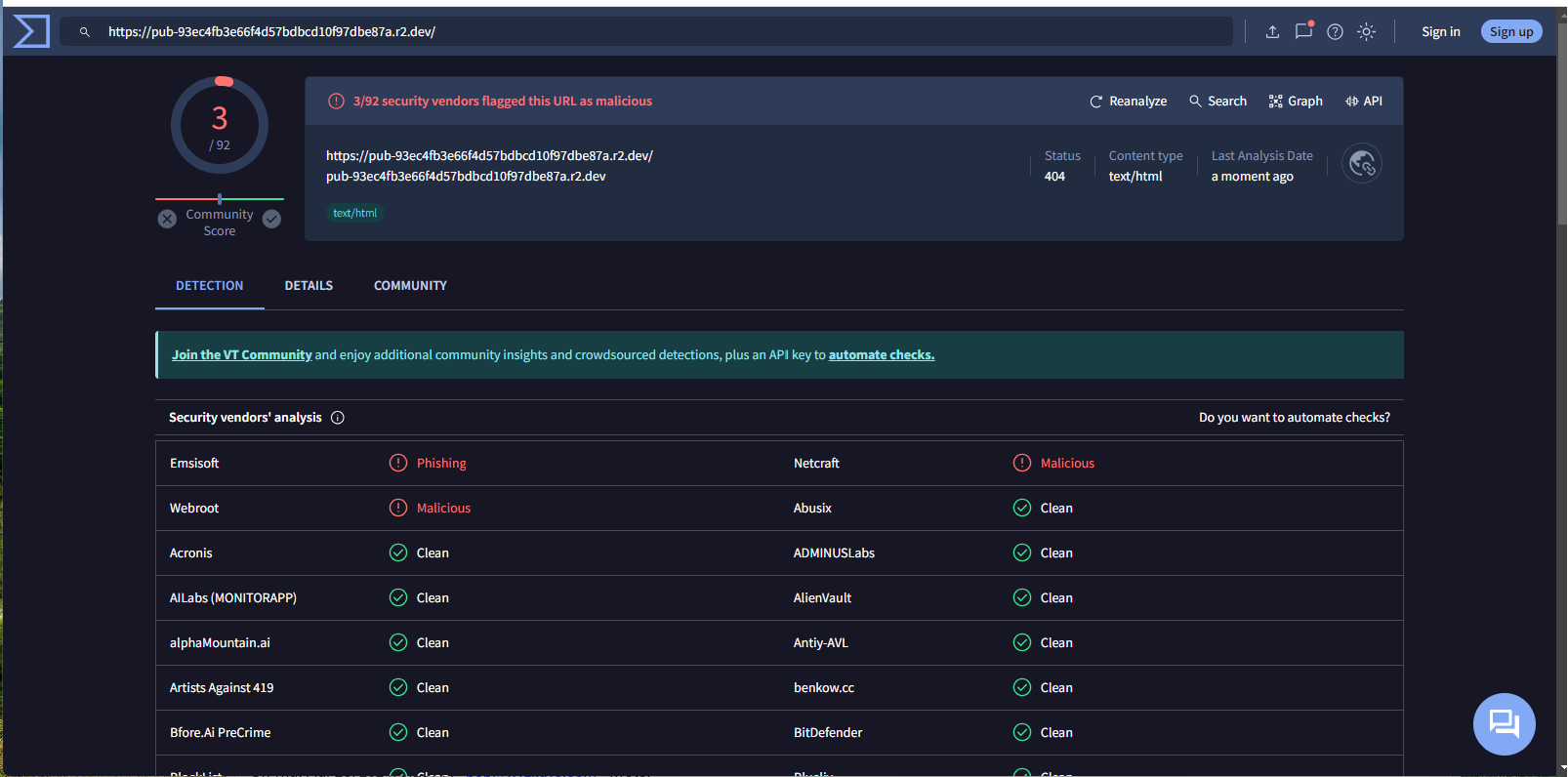
Here we have what is probably the beginning of a credential stealing exploit, although Firefox identified the landing page at https://pub-93ec4fb3e66f4d57bdbcd10f97dbe87a.r2.dev/index ionos ekp.html#support@wyzguys.com as malicious, as did Virustotal.
Here is the warning I got when trying to go to the landing page at the confirm sign in link. Firefox did not allow me to bypass the warning and enter the landing page.
And here is the Virustotal report.
IONOS Voicemail Phish
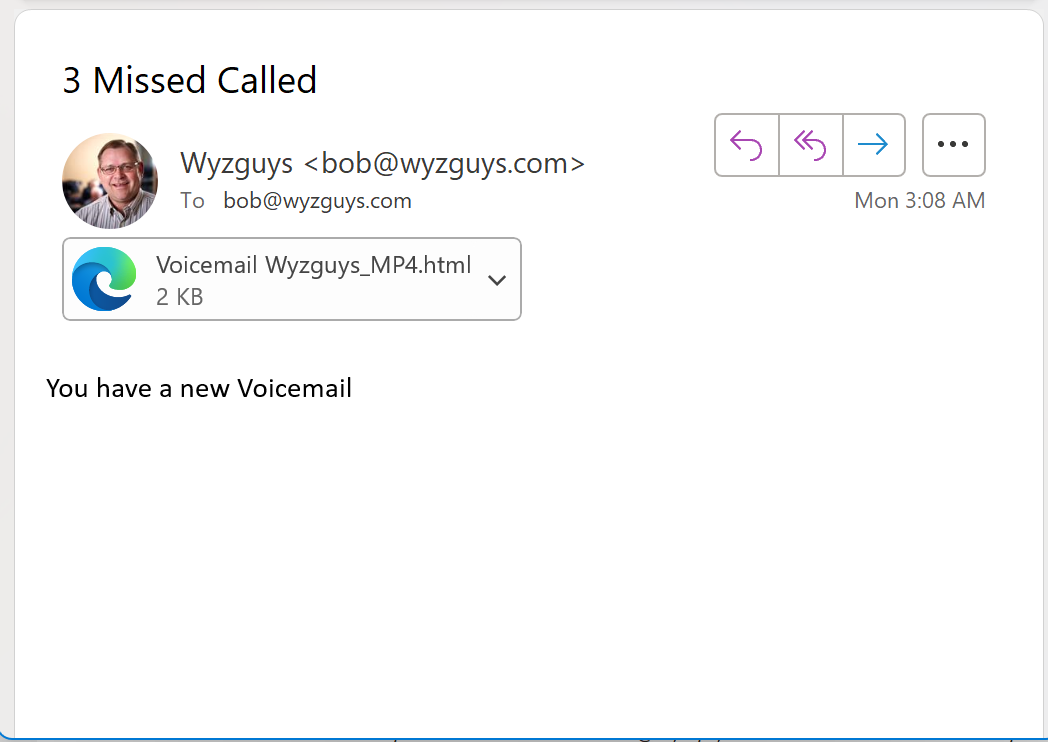
Here’s another phishing email that undoubtedly was supposed to steal my credentials. It features the double file type (mp4.html) to help this look like a legitimate voice message. My attempts at a safe opening of the HTML attachment failed, and from the activity on the screen, this may have been an attempted malware installation, as well.
A very simple email design. Be careful not to fall for messages like this one.
Here’s the phish:
Geek Squad Phish
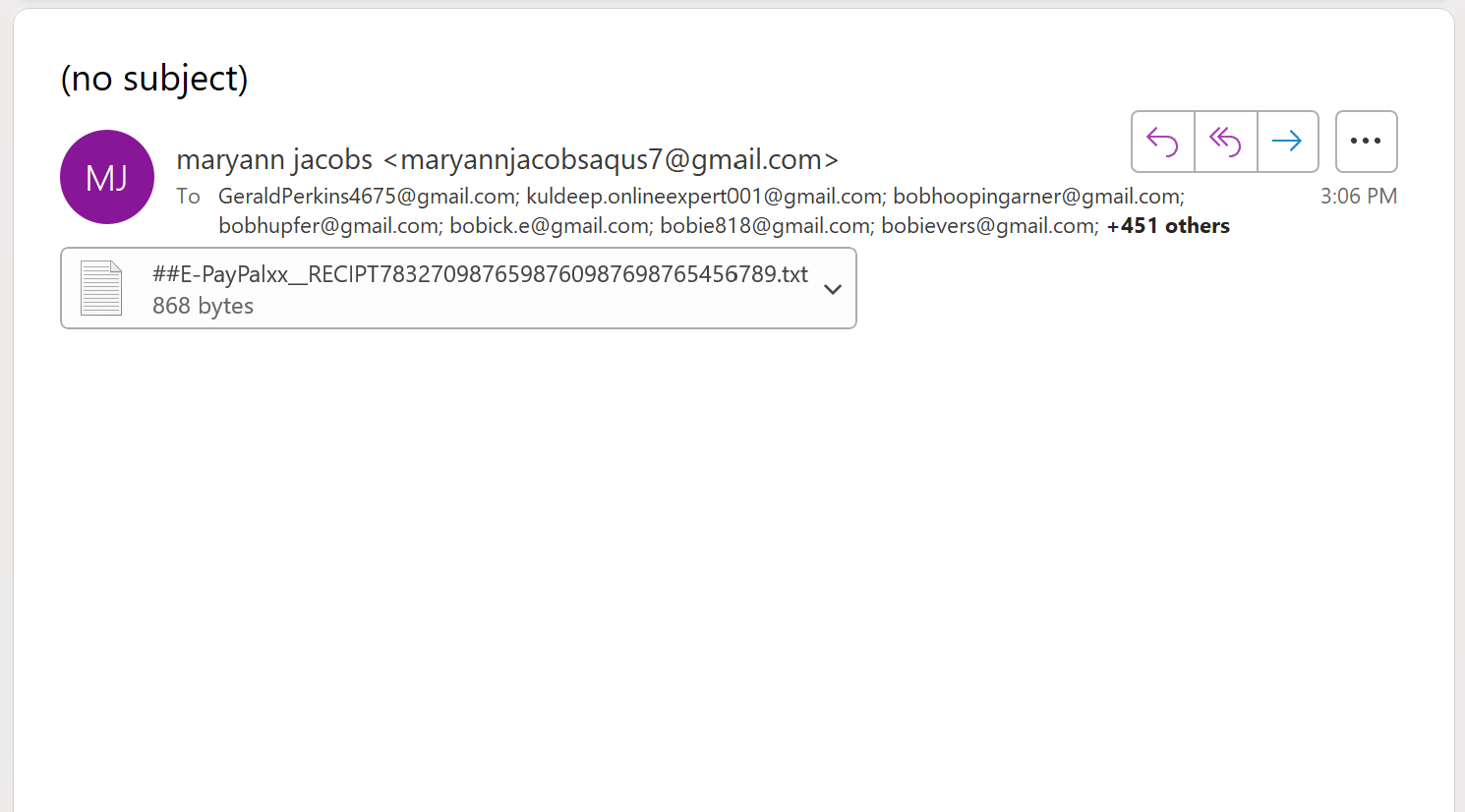
Another short and simple email, this one is a fraudulent Geek Squad invoice for $379.87. Some clues that his is fake:
- (No Subject)\
- Using a large distribution list for the recipients. This crew is not technically savvy. Real commercial invoices would be individually addressed.
- Using unformatted text editor such as Notepad for the invoice attachment.
This sort of phishing exploit is supposed to agitate the recipient enough to get them to call the toll-free phone number to the Cancellation Department.
Here’s the email:
Downloading the attachment.
Here is the content of the TXT invoice attachment. Not the professional full HTML or PDF rendering you would expect in a commercial invoice.
Israeli researchers came out with a hell of a thing just now. Here is a bit of the abstract and a video. YIKES.
In the past year, numerous companies have incorporated Generative AI (GenAI) capabilities into new and existing applications, forming interconnected Generative AI (GenAI) ecosystems consisting of semi/fully autonomous agents powered by GenAI services.
While ongoing research highlighted risks associated with the GenAI layer of agents (e.g., dialog poisoning, privacy leakage, jailbreaking), a critical question emerges: Can attackers develop malware to exploit the GenAI component of an agent and launch cyber-attacks on the entire GenAI ecosystem?
This is a 3-minute video that shows the whole thing.
Their paper introduces Morris II, the first worm designed to target GenAI ecosystems through the use of adversarial self-replicating prompts. The study demonstrates that attackers can insert such prompts into inputs that, when processed by GenAI models, prompt the model to replicate the input as output (replication) and engage in malicious activities (payload).
Additionally, these inputs compel the agent to deliver them (propagate) to new agents by exploiting the connectivity within the GenAI ecosystem. We demonstrate the application of Morris II against GenAI-powered email assistants in two use cases (spamming and exfiltrating personal data), under two settings (black-box and white-box accesses), using two types of input data (text and images).
The worm is tested against three different GenAI models (Gemini Pro, ChatGPT 4.0, and LLaVA), and various factors (e.g., propagation rate, replication, malicious activity) influencing the performance of the worm are evaluated.
Here is the site itself with the video and also the paper. You may need an incognito window to get there.
https://sites.google.com/view/compromptmized
ShareAPR







About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com