Catch of the Day: DMARC Policy Changes
Chef’s Special: Square Review Phish
Examples of clever phish that made it past my anti-spam nets and into my inbox. Some are contributed by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
Fewer Phish in the Net
What are the new DMARC policy requirements that took effect in February 2024?
Starting February 2024, Gmail, Yahoo, Outlook.com and other mail services will require email authentication (SPF, DKIM, and DMARC) to be in place when sending messages to Gmail, Yahoo, and Microsoft accounts. If you’re a bulk sender who sends more than 5,000 emails per day to Gmail accounts, you’ll have even more email authentication requirements to meet.
This is especially important if you have email on your own domain. My email domain for instance is wyzguys.com. I have been busy setting up Sender Policy Framework (SPF), Domain Keys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC) records for clients with custom domains. Failing to do so will cause your email messages to be dropped or discarded by the recipient’s email system. The sender receives a non-delivery message. By requiring all legitimate senders to conform to this new policy, it helps to cut down or eliminate SPAM and phishing emails from ever making it to your inbox. Bogus, spoofed or malicious senders will have a hard time adding these DNS records, and consequently their phishing messages are be dropped in higher percentages.
The upshot for me and other phishing researchers is that there are fewer messages like the one below making it to my inbox..
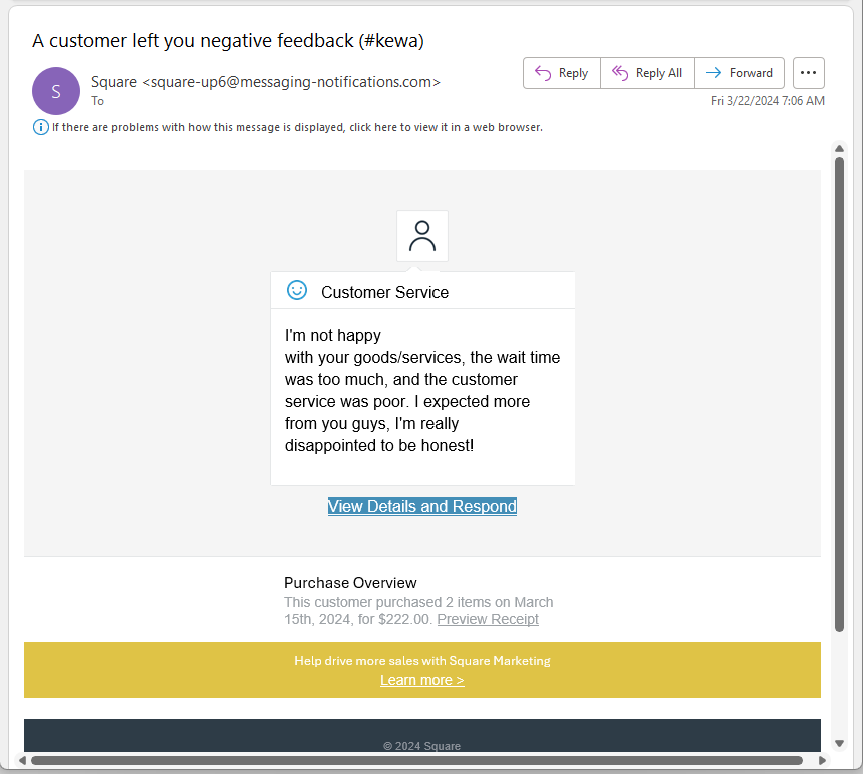
Square Review Phish
But this one made it. This appears to be a negative review from card processor Square. I received this on 2024-03-22
There are two domains in play here. The sender’s email domain is a generic-looking messaging-notifications.com. The sender’s ID of square-up6@ makes the sender’s email look reasonably authentic. It is not uncommon for a business to use the email domain of a marketing service rather than their own
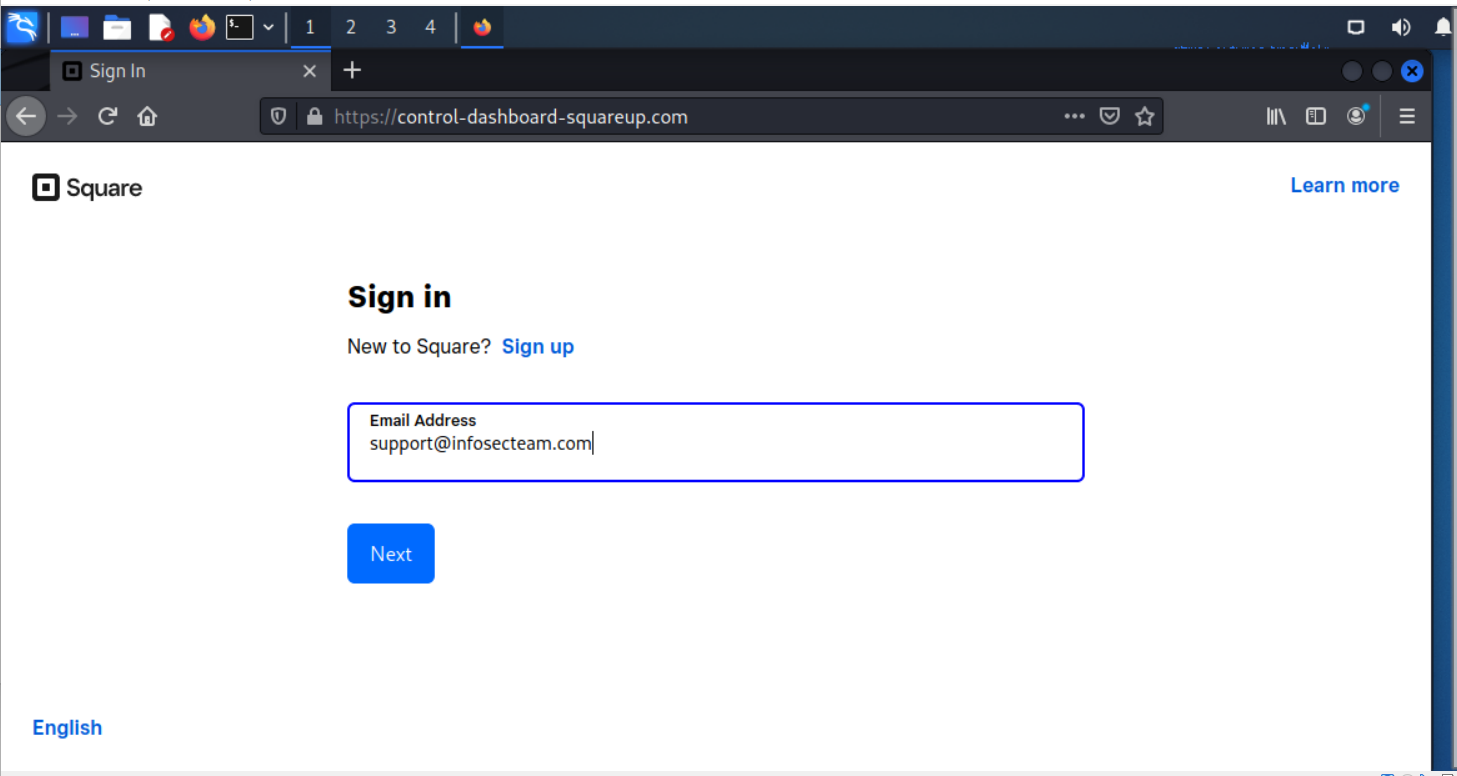
Hidden under the View Details and Respond link and the Preview Receipt link is the landing page URL https://control-dashboard-squareup.com/. It looks like we are going to legitimate domain square-up-com, but the entire string control-dashboard-squareup.com is the domain to the web site hosting the landing pages.
The domains messaging-notifications.com and control-dashboard-squareup.com were registered yesterday 2024-03-21
Today we will examine the Internet mail headers to see if we can figure out how this phishing message got past the new email identification requirements.
The first landing page. I entered an email address I use for these kinds of credential stealing scams.
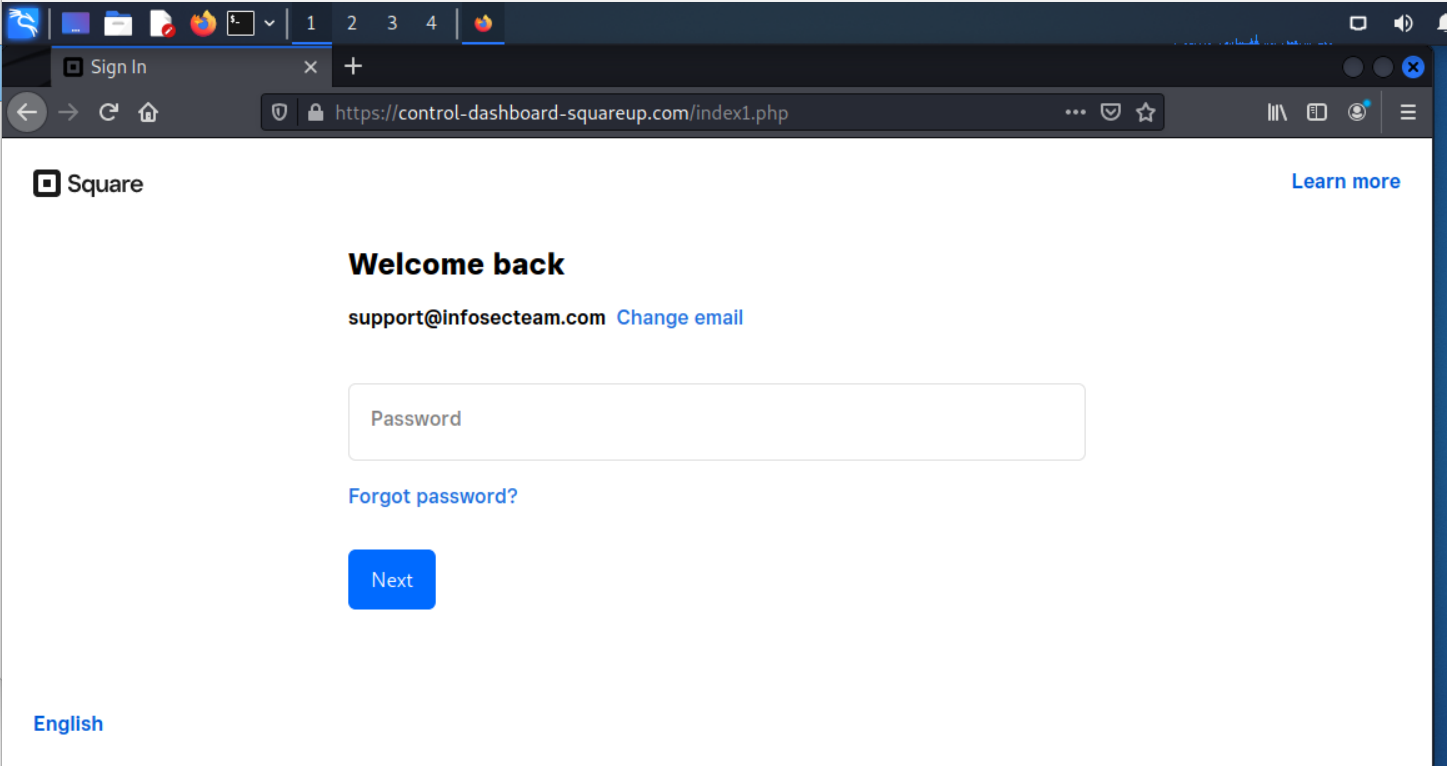
The second landing page captures my password.
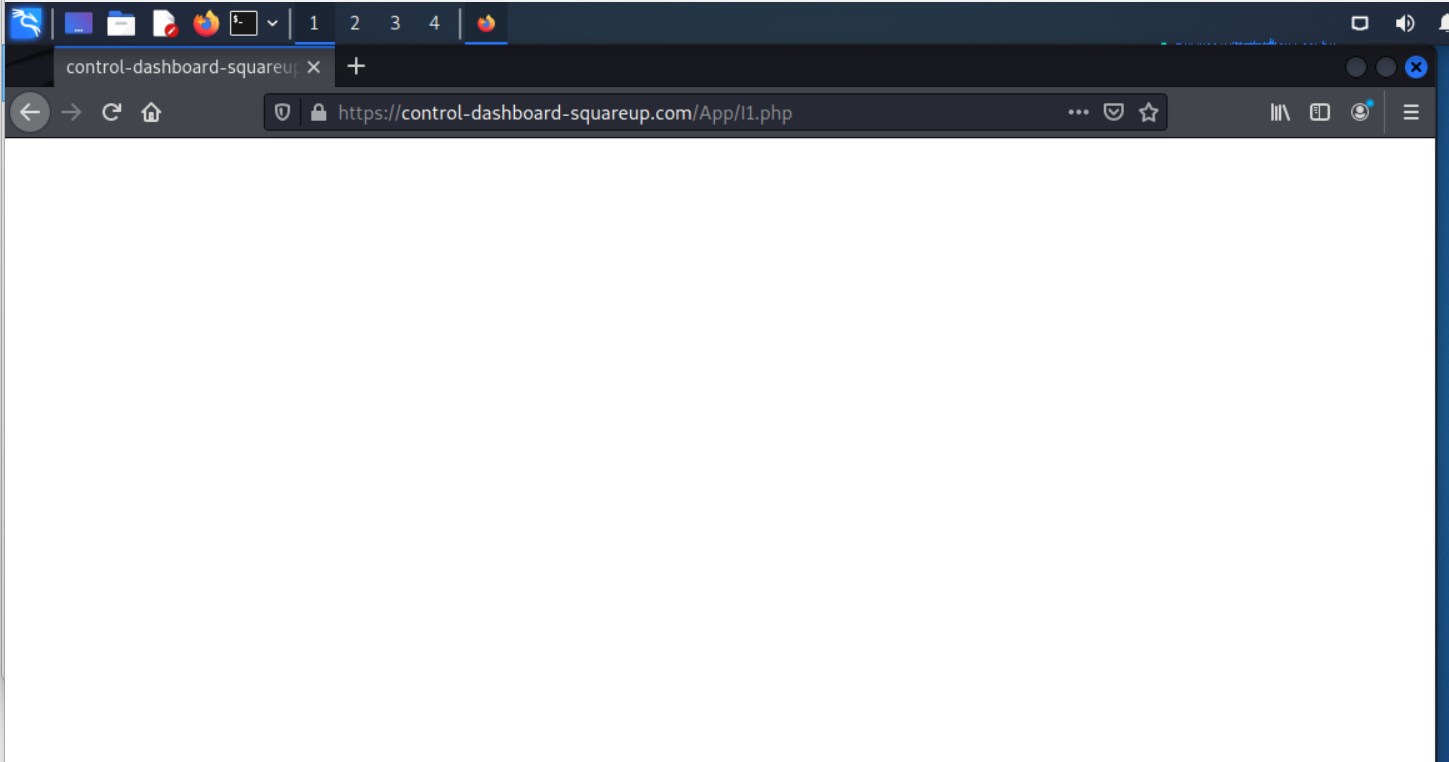
And the third landing page is blank. To make this more effective the attacker could have put in a form to dispute the negative review and collect a whole lot more personally identifiable information (PII). This blank page immediately screams SCAM. If you get here, you should change your Stripe password right away and set up two-factor authentication if you haven’t already.
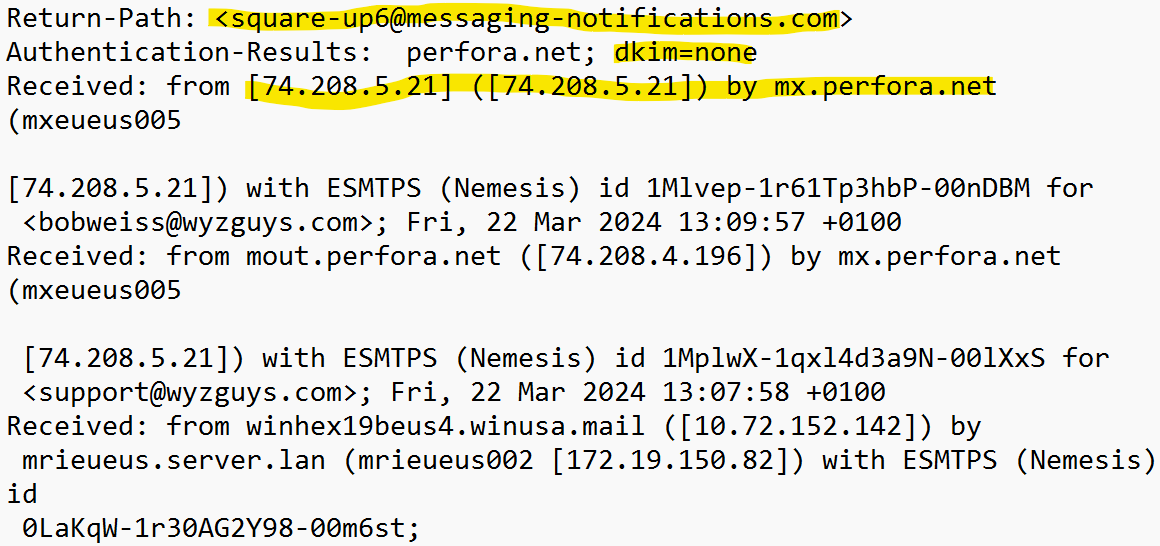
Mail Header Analysis
The first thing we noticed was the absence of a DKIM record (dkim=none). The IP address is my mail server
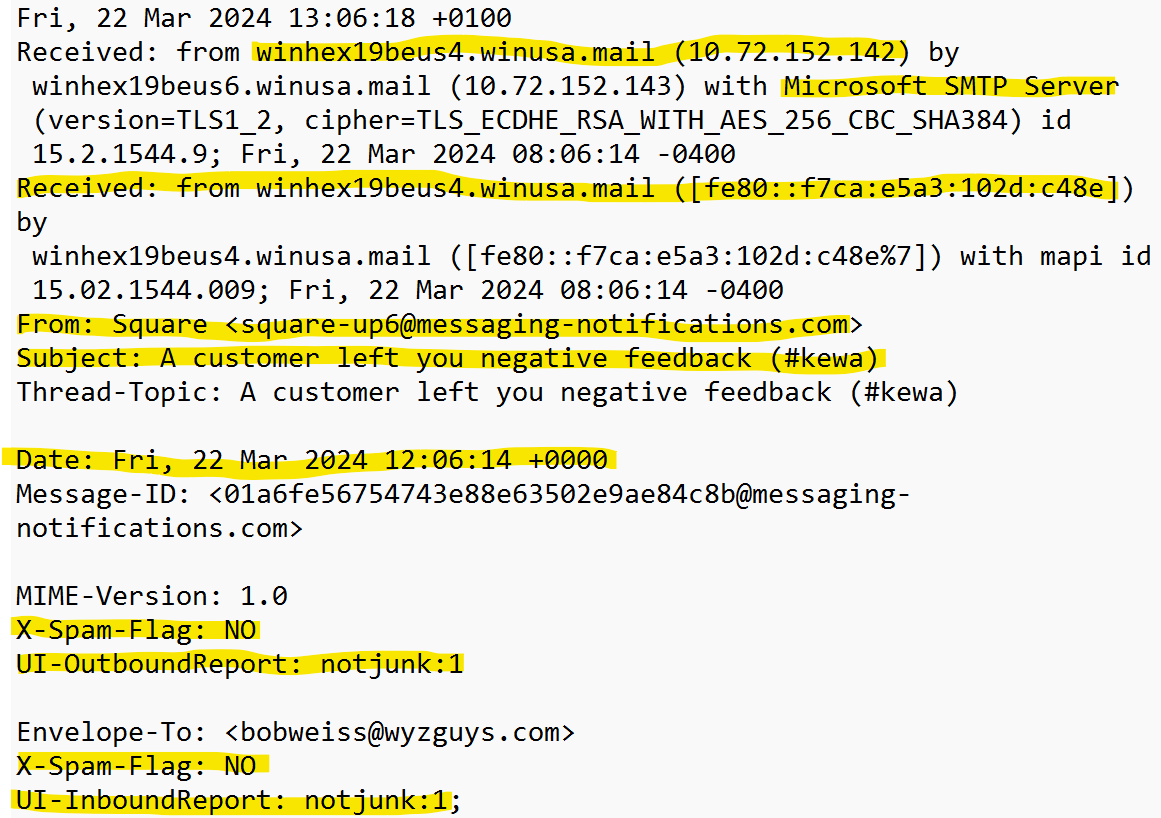
The first highlighted text below is for the sender’s mail server. I noticed that they are using a Microsoft SMTP Server which is probably how this email slipped through the approval process. These sender was also marked as not junk.
This exploit worked by using a server that would be preapproved (Microsoft) and some recently registered generic looking domains (messaging-notifications.com and control-dashboard-squareup.com) registered yesterday 2024-03-21.
I thought this was a pretty convincing phishing attack. If you are using Square as your card processor, it is always safer to log into you Square account directly rather than using the links provided in the email.
Share
MAR





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com