Catch of the Day: Consultant Phish (Nigerian Prince)
Chef’s Special: DMARC Abuse Phish
Also serving:
Examples of clever phish that made it past my anti-spam nets and into my inbox. Some are contributed by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
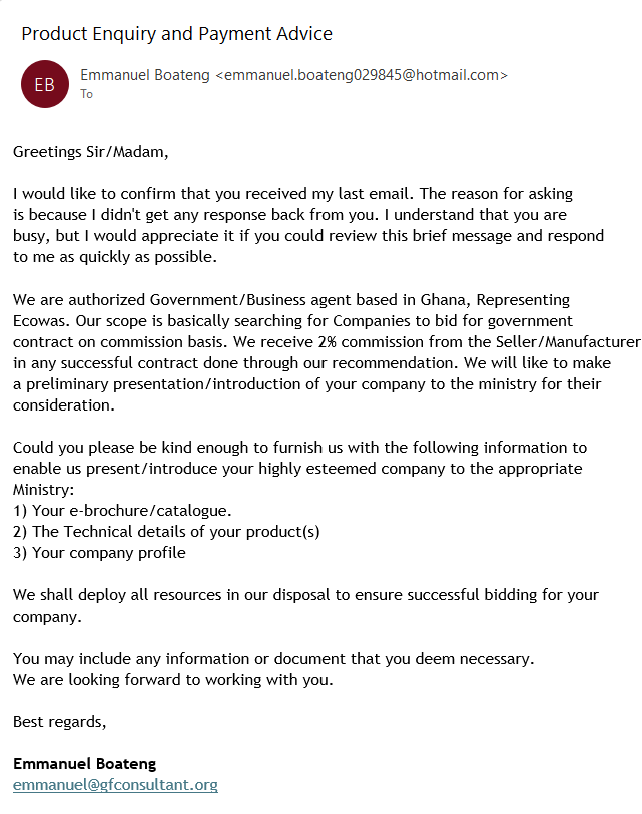
Consultant Phish (Nigerian Prince)
This email arrived today 2024-03-06, and was devoid of any active content, except for the email address and phone number of the sender. This appears to be an extended exploit/con game of the Nigerian Prince variety. I have sent a response and will be adding the exchange to this post.
Phishers Abusing Legitimate but Neglected Domains To Pass DMARC Checks
By Roger Grimes
A recent great article by BleepingComputer about domain hijacking and DMARC abuse reminded me that many companies and people do not understand DMARC well enough to understand what it does and how it helps to prevent phishing.
And look-alike and neglected domains challenge its protective value to unknowledgeable email recipients. This article is about how to understand and proactively use DMARC.
First, a quick little intro to DMARC for readers not familiar with it. Domain-based Message Authentication, Reporting and Conformance (DMARC), Sender Policy Framework (SPF), and DomainKeys Identified Mail (DKIM) are three related global anti-phishing standards that allow email recipients to verify if an email that claims to be from a particular sending domain is really from the domain it claims.
In short, it helps to prevent email domain spoofing. For example, if an email claims to be from microsoft[.com], is it really from microsoft[.com]? DMARC operations rely heavily on DNS from both a sender’s and receiver’s configuration and use.
[CONTINUED AT]:
https://blog.knowbe4.com/phishers-abusing-neglected-domains-pass-dmarc
MAR





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com