Catch of the Day: IONOS Security Alert Phish
Chef’s Special: MS Teams Phish
Examples of clever phish that made it past my anti-spam nets and into my inbox. Some are contributed by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
IONOS Security Alert Phish
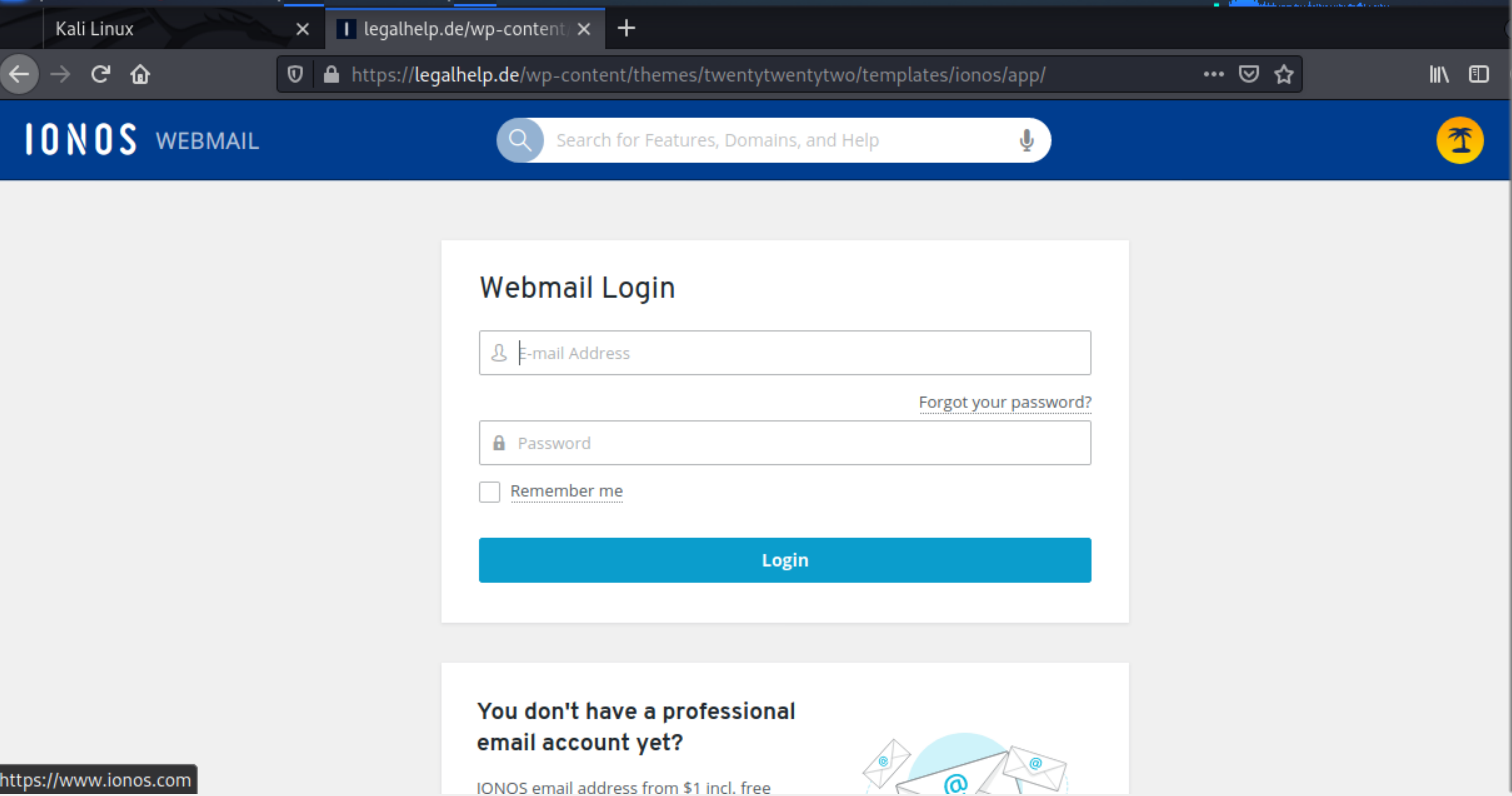
I received this phishing email . As threatening as this sounds, the sender address and domain were incorrect for an IONOS security email. The See Login Activity button resolved to https://legalhelp.de/wp-content/themes/twentytwentytwo/templates/ionos/app/ . This was a credential stealing landing page.
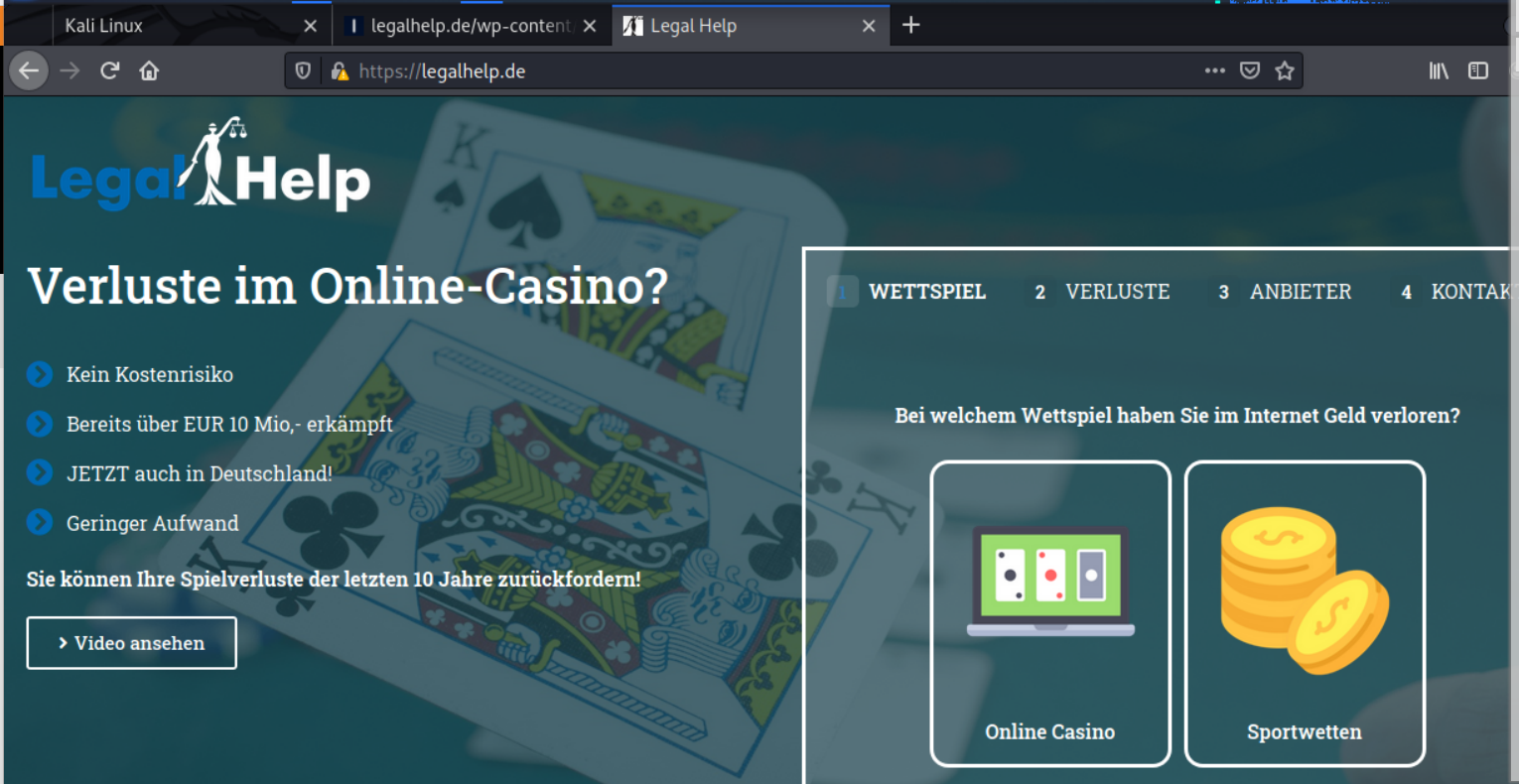
The landing pages were hosted on a hijacked web site for https://legalhelp.de, a German website with gambling ties. See the images below.
The phishing email
Landing page for stealing your login credentials
Home page of hijacked website
[New Threat] Attackers Are Now Using MS Teams to Phish Your Users
Attackers are abusing Microsoft Teams to send phishing messages, according to researchers at AT&T Cybersecurity.
“While most end users are well-acquainted with the dangers of traditional phishing attacks, such as those delivered via email or other media, a large proportion are likely unaware that Microsoft Teams chats could be a phishing vector,” the researchers write.
“Most Teams activity is intra-organizational, but Microsoft enables External Access by default, which allows members of one organization to add users outside the organization to their Teams chats. Perhaps predictably, this feature has provided malicious actors a new avenue by which to exploit untrained or unaware users.”
In the case observed by AT&T Cybersecurity, the attackers used a compromised domain to send the messages.
“An important detail to note here is the “.onmicrosoft[.]com” domain name,” the researchers write. “This domain, by all appearances, is authentic and most users would probably assume that it is legitimate.
“OSINT research on the domain also shows no reports for suspicious activity, leading the MDR SOC team to believe the username (and possibly the entire domain) was likely compromised by the attackers prior to being used to launch the phishing attack.”
In this case, the attackers sent users a malicious file with a double extension designed to trick users into thinking it is a PDF file. This file, when opened, would install the DarkGate malware.
“The MDR SOC team continued to drill down on the phished users to determine the precise nature of the attack,” the researchers explain. “They subsequently discovered three users who had downloaded a suspicious double extension file. The file was titled ‘Navigating Future Changes October 2023[dot]pdf[dot]msi.’
“Double extension files are commonly used by attackers to trick users into downloading malicious executables, as the second extension, .msi in this case, is usually hidden by the filesystem. The user believes they are downloading a PDF for business use, but instead receives a malicious installer.”
Blog post with links:
https://blog.knowbe4.com/microsoft-teams-phishing-attacks
Share
FEB






About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com