Catch of the Day: Facebook Scam Phish
Chef’s Special: Payment Verification Phish
Examples of clever phish that made it past my anti-spam nets and into my inbox. Some are contributed by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
BleepingComputer describes a phishing scam that’s been running rampant on Facebook for the past several months, in which threat actors use hacked accounts to post links to phony articles implying that someone has been killed in an accident.
The Facebook posts have captions like “I can’t believe he is gone,” accompanied by thumbnails of news articles involving car accidents or crime scenes. Users are more likely to click on the links since they’ve been posted by a friend’s account. The links lead to phishing sites that ask users to enter their Facebook credentials in order to view the videos.
“To entice a visitor to enter their password, they show what appears to be a blurred-out video in the background, which is simply an image downloaded from Discord,” BleepingComputer says.
“If you enter your Facebook credentials, the threat actors will steal them, and the site will redirect you to Google. While it is not known what the stolen credentials are used for, the threat actors likely use them further to promote the same phishing posts through the hacked accounts….This phishing scam is widely spread, with BleepingComputer seeing numerous posts created each day by friends and family who unwittingly had their accounts hacked through the same scam.” More…
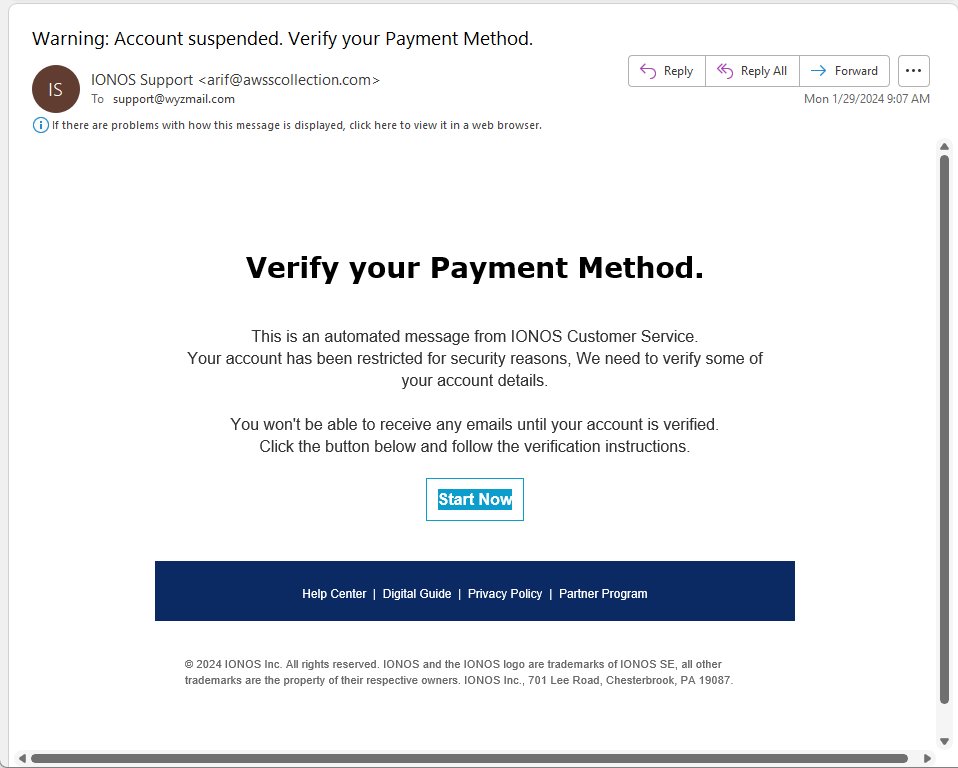
Payment Verification Phish
This phishing email is a new wrinkle in an old credential stealing ploy. The sender address is obviously spoofed. The Start Now but resolves to https://trinityfreightco.com/lc/sc/c.php?username=support@wyzmail.com. Unfortunately, nothing useful is at that site, it seems to be a domain name parking lot for https://sedoparking.com. So either this exploit has been taken down already or it was never set up completely.
Here is the email
Share
FEB





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com