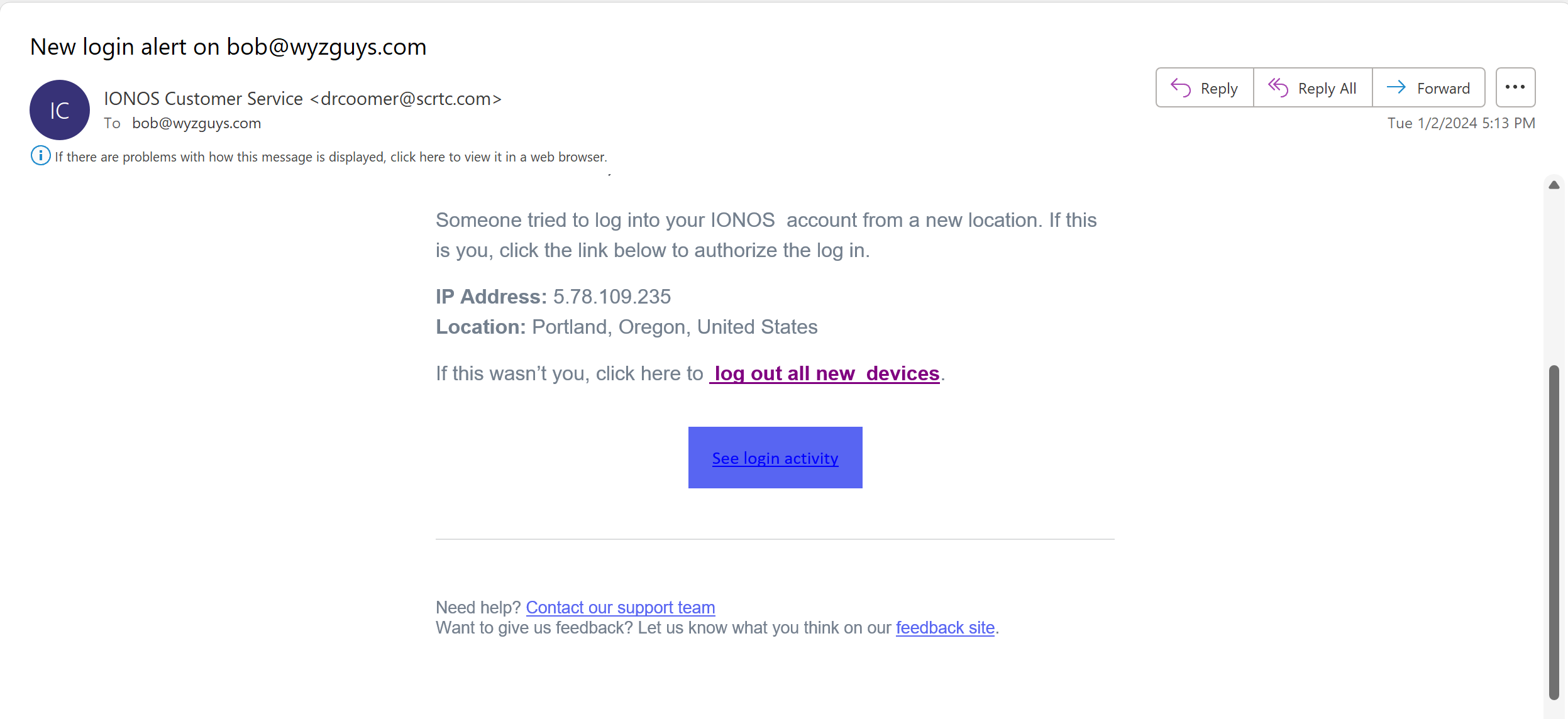
Catch of the Day: IONOS Login Alert Phish
Chef’s Special: SMTP Smuggling Phish
Also serving: AI Social Engineering Phish, Impersonation Attack Phish
Examples of clever phish that made it past my anti-spam nets and into my inbox. Some are contributed by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
IONOS Login Alert Phish
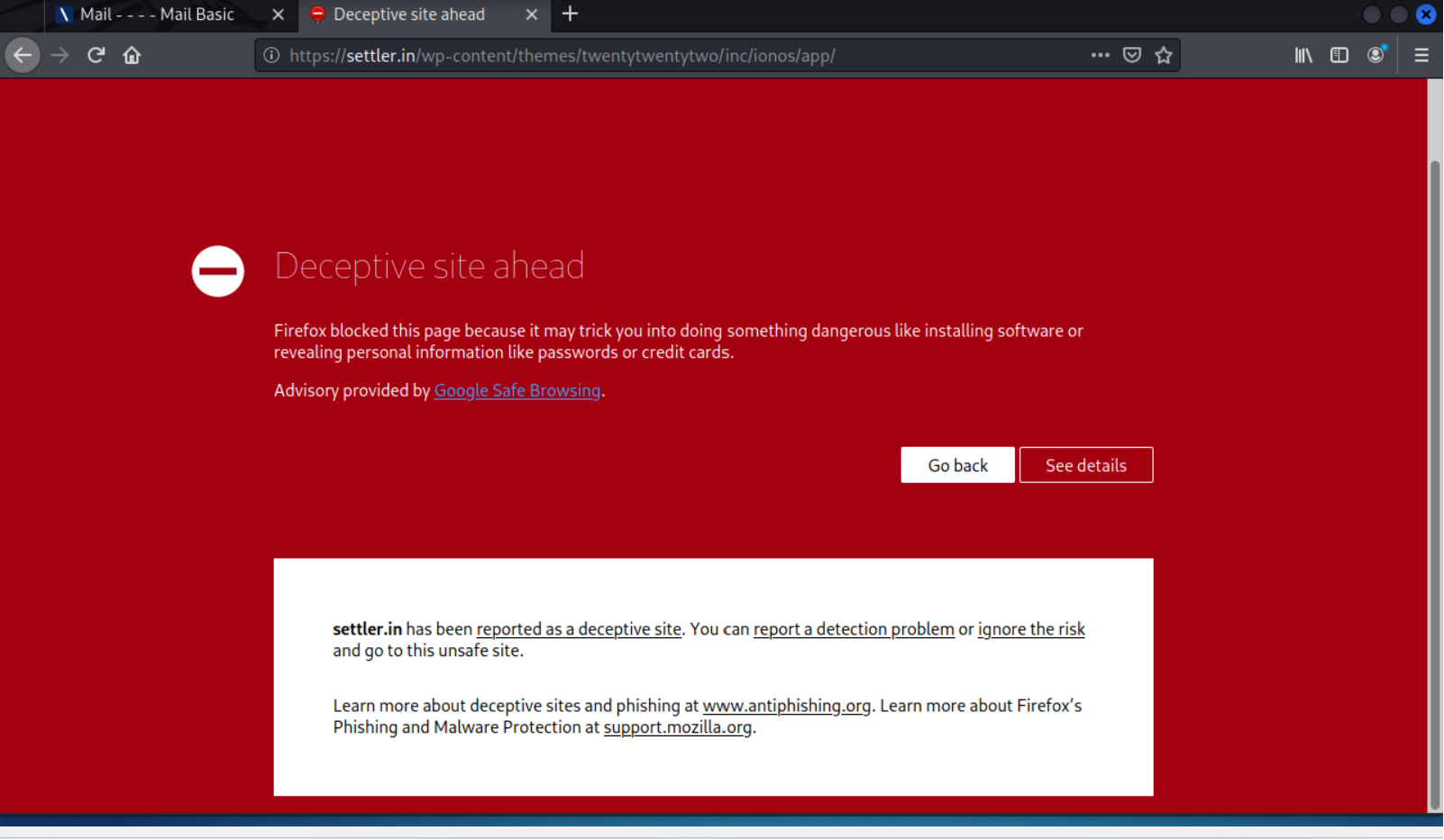
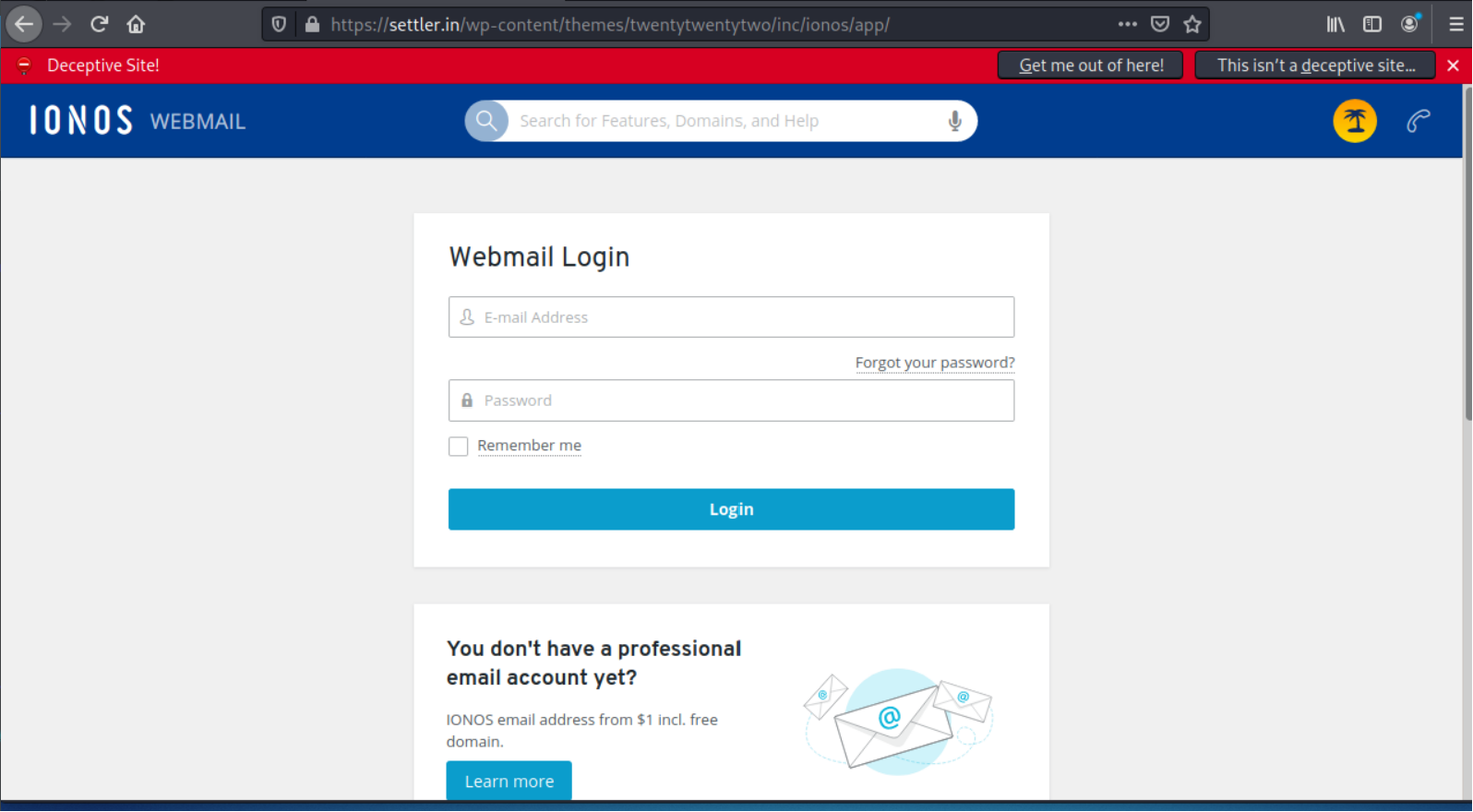
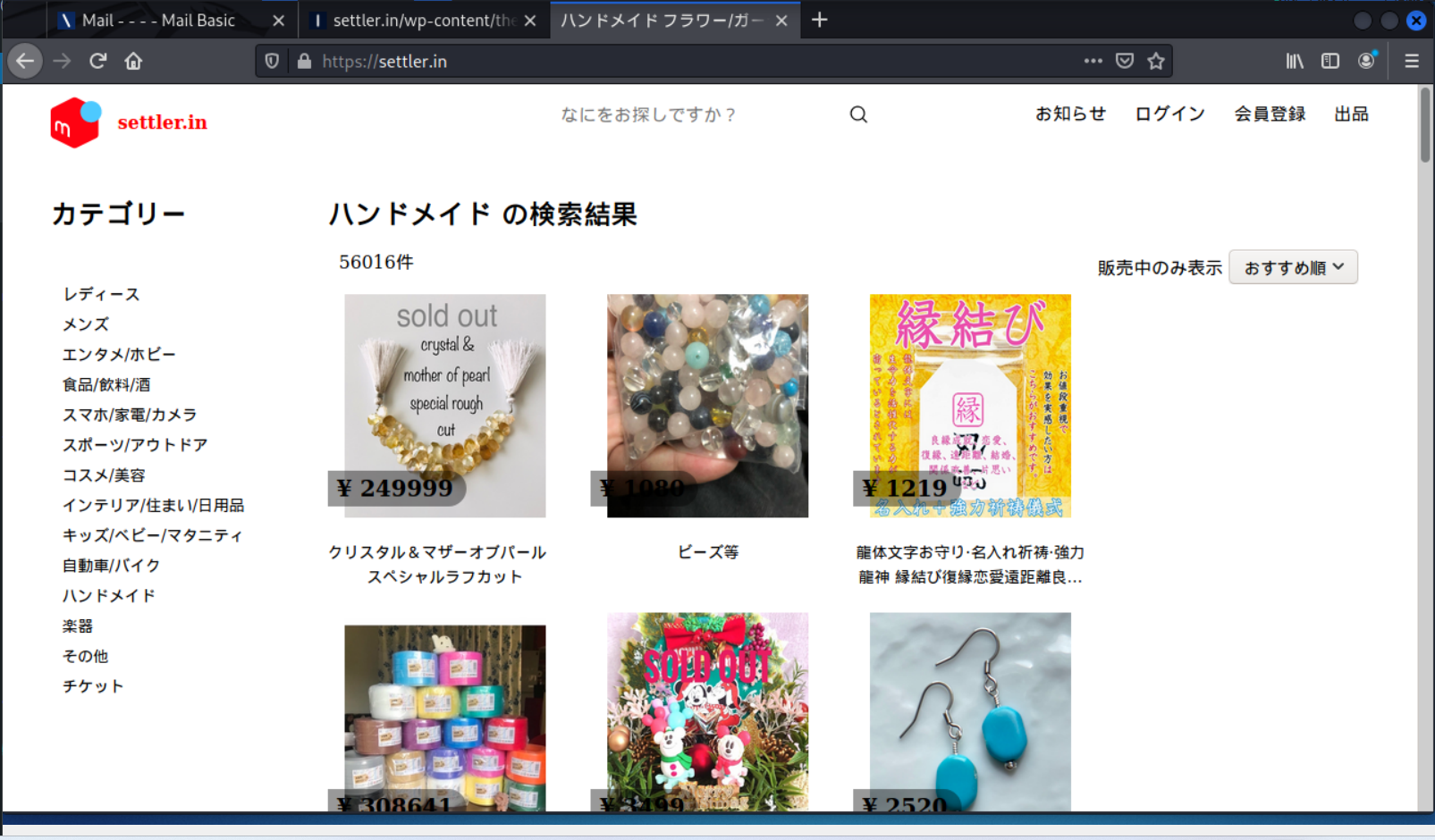
This one nearly had me fooled, since it is a security alert. The sender email address was obviously wrong for the company (IONOS). The Log out all new devices link resolved to https://settler.in/wp-content/themes/twentytwentytwo/inc/ionos/app/. After ignoring the warning page, I got to a typical credential stealing log in page. The fake login page was hosted on a hijacked website at https://settler.in.
Images follow:
Firefox warning page
Credential stealing login page
The home page of the hijacked website. I have not seen the use of a hijacked website in quite a while.
SMTP Smuggling – How It Easily Circumvents Your Email Defenses
A newly-discovered technique misusing SMTP commands allows cybercriminals to pass SPF, DKIM and DMARC checks, allowing impersonated emails to reach their intended victim.
Earlier this month, Timo Longin, security researcher with cybersecurity consulting firm SEC Consult published details on what is now referred to as SMTP smuggling. Simply put, he detected miscommunications using the SMTP protocol that allowed message content to be submitted to a receiving email server in a way that makes the protocol simply accept the message and process its delivery to the intended recipient.
While rather in the weeds in terms of how it works, in essence cybercriminals take advantage of what should be the end-of-data sequence near the beginning of the submission of an email message, entire emails are “smuggled” within the process, therefore bypassing normal steps that include checking SPF, DKIM and DMARC.
In the screenshot in the blog post (link below), you’ll note the initial short email with the email body of “lorem ipsum.” But then there’s this extra email with the email body of “I am the admin now!” The specific content is irrelevant (other than to provide an example of something benign vs. malicious in nature), but it shows how SMTP smuggling occurs.
According to Longin, this method can be used to impersonate emails from any high-profile brand. This is where it becomes a real problem. Users that have not undergone security awareness training will be more prone to believing an email is actually from the company it claims to be, falling for the socially engineered scam within.
The vulnerability was initially reported to vendors in late July. Microsoft has since rolled out a patch, but other vendors, including Cisco, have yet to do so.
Blog post with link and screenshot:
https://blog.knowbe4.com/smtp-smuggling-email-security-impersonation
AI in 2024: The Top 10 Cutting Edge Social Engineering Threats
The year 2024 is shaping up to be a pivotal moment in the evolution of artificial intelligence (AI), particularly in the realm of social engineering. As AI capabilities grow exponentially, so too do the opportunities for bad actors to harness these advancements for more sophisticated and potentially damaging social engineering attacks. Let’s explore the top 10 expected AI developments of 2024 and their implications for cybersecurity.
1. Exponential Growth in AI Reasoning and Capabilities
As Vinod Khosla of Khosla Ventures points out, “The level of innovation in AI is hard for many to imagine.” AI’s reasoning abilities are expected to soar, potentially outperforming human intelligence in certain areas. This could lead to more convincing and adaptable AI-driven social engineering tactics, as bad actors leverage these reasoning capabilities to craft more persuasive attacks.
2. Multimodal Large Language Models (MLLMs)
MLLMs, capable of processing and understanding various data types, will take center stage in 2024. These models could be used to create highly convincing and contextually relevant phishing messages or fake social media profiles, enhancing the efficacy of social engineering attacks.
3. Text to Video (T2V) Technology
The advancement in T2V technology means that AI-generated videos could become a new frontier for misinformation and deepfakes. This could have significant implications for fake news and propaganda, especially in the context of the 2024 elections, or real-time business email compromise attacks.
4. Revolution in AI-Driven Learning
AI’s ability to identify knowledge gaps and enhance learning can be exploited to manipulate or mislead through tailored disinformation campaigns, targeting individuals based on their learning patterns or perceived weaknesses.
5. Challenges in AI Regulation
Governments’ attempts to regulate AI to prevent catastrophic risks will be a key area of focus. However, the speed of AI innovation will outpace regulatory efforts, leading to a period where advanced AI technologies inevitably will be used in social engineering attacks.
6. The AI Investment Bubble and Startup Failures
The surge in AI venture capital indicates a booming market, but the potential failure of AI startups due to business model obsolescence could lead to a set of orphaned, advanced, but unsecured AI tools available for malicious use.
7. AI-Generated Disinformation in Elections
With major elections scheduled globally, the threat of AI-generated disinformation campaigns is more significant than ever. These sophisticated AI tools are already being used to sway public opinion or create political unrest, there are a whopping 40 global elections in 2024.
8. AI Technology Available For Script Kiddies
As AI becomes more accessible and cost-effective, the likelihood of advanced AI tools falling into the wrong hands increases. This could lead to a rise in AI-powered social engineering attacks even by less technically skilled bad actors.
9. Enhanced AI Hardware Capabilities
Jensen Huang, co-founder and chief executive of Nvidia, told the DealBook Summit in late November that “there’s a whole bunch of things that we can’t do yet.” However, the advancements in AI hardware, such as Neural Processing Units (NPU), will lead to faster and more sophisticated AI models. This could allow real-time, adaptive social engineering tactics, making scams more convincing and harder to detect.
10. AI in Cybersecurity and the Arms Race
While AI advancements provide tools for cybercriminals, they also empower more effective AI-driven security systems. This is leading to an escalating arms race between cybersecurity measures and attackers’ tactics, where real-time AI monitoring against AI-driven social engineering attacks might become reality.
The upshot is that 2024 is set to be a landmark year in AI development, with far-reaching implications for social engineering. It is crucial for cybersecurity professionals to stay ahead of these trends, build a strong security culture, adapt their strategies, and keep stepping their workforce through frequent security awareness and compliance training.
Blog post with links:
https://blog.knowbe4.com/ai-in-2024-the-top-10-cutting-edge-social-engineering-threats
Impersonation Attack Data Breaches Predicted to Increase in 2024
With so much of an attack riding on a cybercriminals ability to gain access to systems, applications and data, experts predict the trend of rising impersonation is only going to get worse.
The Identity Theft Resource Center’s 2024 Predictions includes one that organizations should be paying close attention to:
An unprecedented number of data breaches in 2023 by financially motivated and nation/state threat actors will drive new levels of identity crimes in 2024, especially impersonation and synthetic identity fraud.
Data breaches are considered the number one business risk to organizations, giving credence to the beginning part of ITRC’s prediction. And we already have seen the use of impersonation grow as credentials have become the primary target of initial access brokers, with over 10,000 credentials a month being sold on the dark web!
But these credentials aren’t the endgame, according to the ITRC; they are simply a means to gather as much personal information about an individual (sort of a modern-day doxing) so that they can commit much more lucrative crimes that yield more money per victim. Another of the ITRC’s predictions gives some context of how this data may be misused:
The availability of compromised consumer data and the use of large language models (LLMs) may result in AI-created, highly convincing “medical records” that could be submitted to insurance carriers.
But to get access to enough data, cybercriminals need to first gain access to corporate data that may contain personal details for customers, patients, etc. Which brings me back to where I started — cybercriminals need credentials to gain initial access, move laterally, and access sensitive data.
So, stopping a string of attack actions with that very first credential — which likely is compromised as part of a credential harvesting attack — is imperative.
And, with the owner of the credential — one of your users — giving up the credential as part of a socially engineered phishing scam, this critical juncture requires its own type of security control — found in new-school security awareness training. No credentials means no access, which means no data breach, which means no misuse of personal data.
Blog post with links:
https://blog.knowbe4.com/increase-data-breaches-impersonation-attacks
Share
JAN





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com