Catch of the Day: Mailbox Confirmation Phish
Chef’s Special: Smishing Triad Phish
Also serving: Teams Phish, Password Expires Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
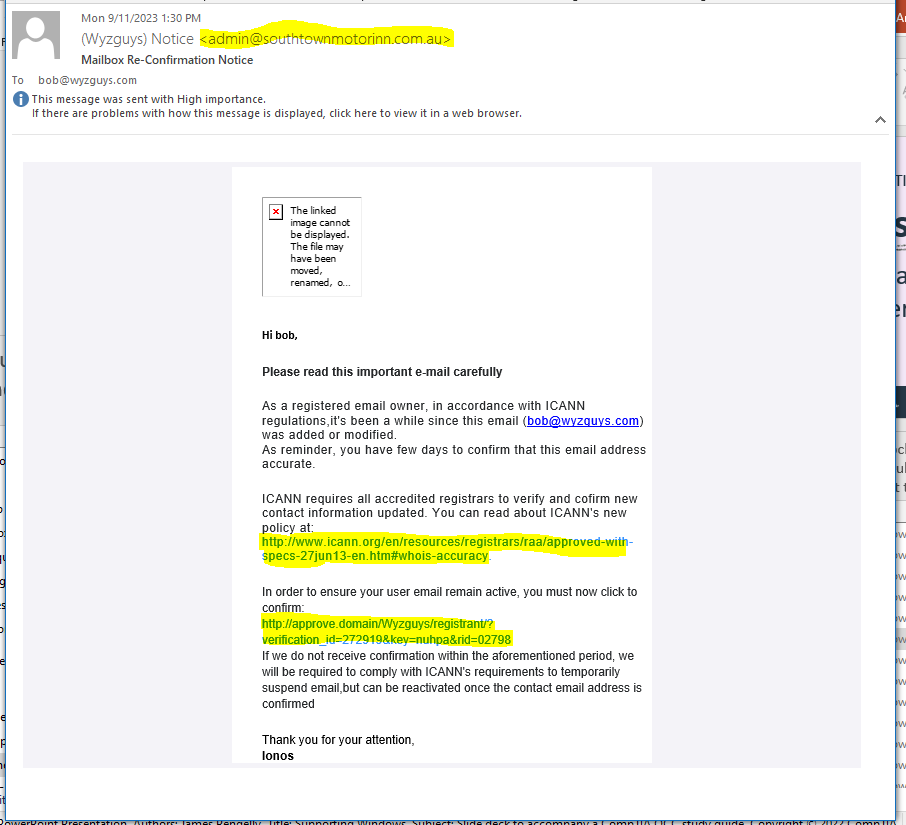
Mailbox Re-Confirmation Phish
I received this phishing email on 2023-09-11. The story basically plays the authority card “in accordance with OCAAN regulations.” There is some interesting slight of hand with the two long URLS, which appear to go to ICAAN. Both of these URLs redirect to https://google.com/amp/s/cropa.org.br/downloads/docs_cds/icann/verify/Ym9iQHd5emd1eXMuY29t and ir redirected further to https://cropa.org.br/downloads/docs_cds/icann/verify/Ym9iQHd5emd1eXMuY29t
The sender email address is totally inappropriate for the alleged sender.
Here’s the email
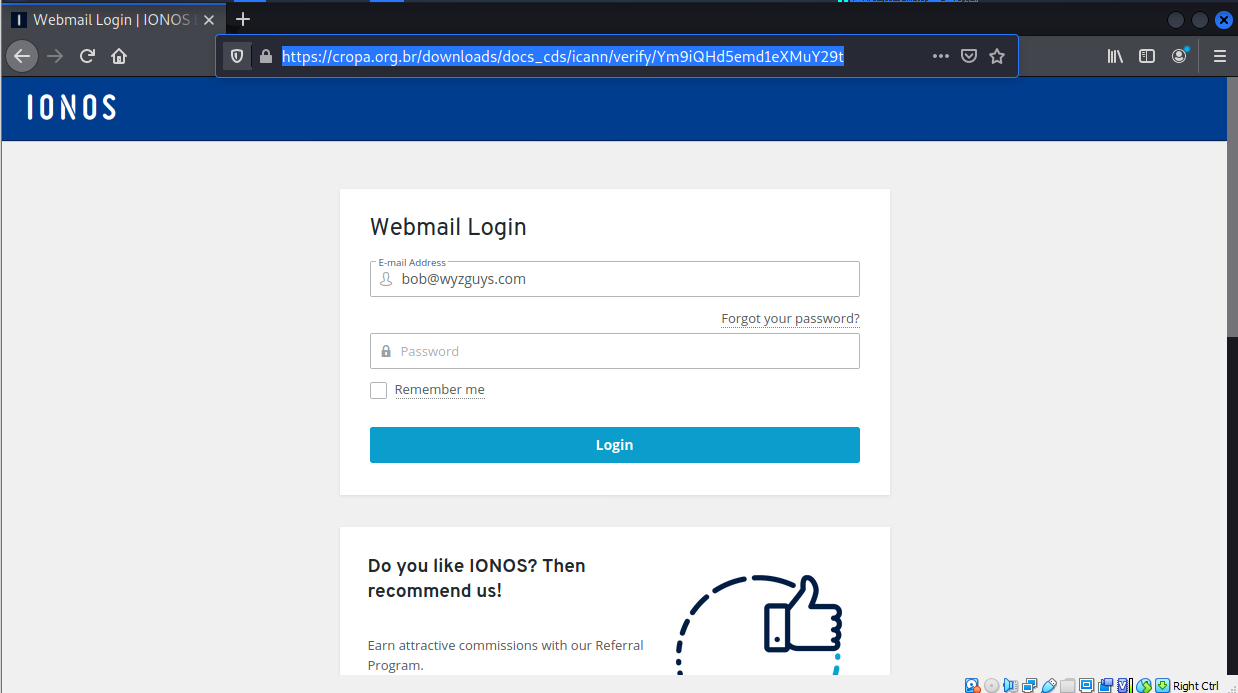
This took us too the landing page below
Again another credential stealing exploit..
This email invoked the authority of ICAAN, a legitimate Internet regulatory agency that is responsible for registering and distributing domain names. Most people would not be familiar with ICAAN, but the name may ring a bell. The voice of authority coupled with the threat of losing your email address might just push a typical user into clicking on the web links.
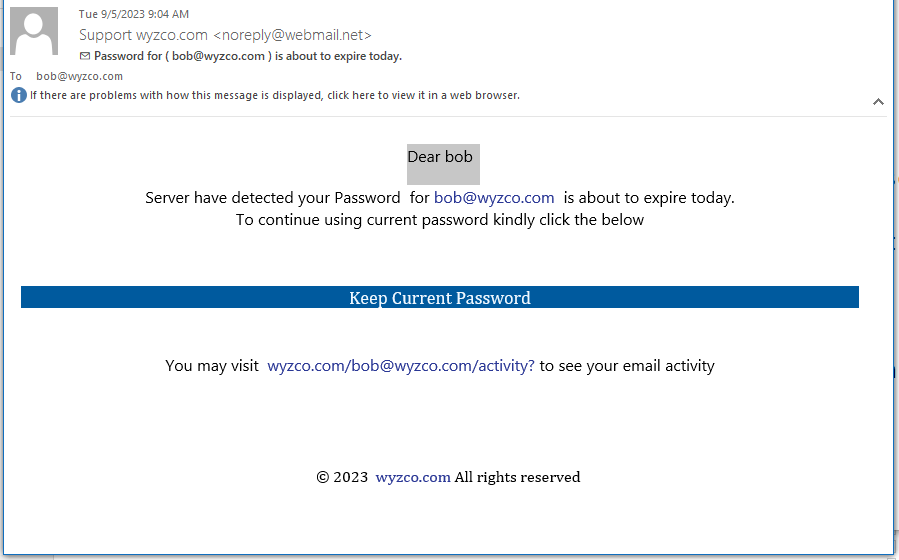
Password About To Expire Phish
This one arrived on 2023-09-12 at 9:04 am, I started investigating a few minutes later, but the landing page was already missing. Or perhaps this is a first timer using a Malware as a Service exploit incorrectly. The keep Current Password link resolves to https://yhygeneraltrading.com/webcenter/#bob@wyzco.com.
In any event, here’s the email
“Smishing Triad” Targeted USPS And US Citizens For Data Theft
 Resecurity has identified a large-scale smishing campaign targeting US Citizens. Previous incidents have impacted victims from the U.K, Poland, Sweden, Italy, Indonesia, Japan, and other countries. The threat group behind the campaign was skillfully impersonating the Royal Mail, New Zealand Postal Service (NZPOST), Correos (Spain), PostNord, Poste Italiane and the Italian Revenue Service (Agenzia delle Entrate). Resecurity observed similar scams previously targeting FedEx and UPS customers. The Chinese-speaking threat actors behind this campaign are operating a package-tracking text scam sent via iMessage to collect personally identifying information (PII) and payment credentials from victims, in the furtherance of identity theft and credit card fraud. The cybercriminal group orchestrating this campaign has been named “Smishing Triad“, as it leverages smishing as its primary attack vector and originates from China. More..
Resecurity has identified a large-scale smishing campaign targeting US Citizens. Previous incidents have impacted victims from the U.K, Poland, Sweden, Italy, Indonesia, Japan, and other countries. The threat group behind the campaign was skillfully impersonating the Royal Mail, New Zealand Postal Service (NZPOST), Correos (Spain), PostNord, Poste Italiane and the Italian Revenue Service (Agenzia delle Entrate). Resecurity observed similar scams previously targeting FedEx and UPS customers. The Chinese-speaking threat actors behind this campaign are operating a package-tracking text scam sent via iMessage to collect personally identifying information (PII) and payment credentials from victims, in the furtherance of identity theft and credit card fraud. The cybercriminal group orchestrating this campaign has been named “Smishing Triad“, as it leverages smishing as its primary attack vector and originates from China. More..
To the right is an example I received on my smart phone. The use of a toll-free number means you will be getting social engineered by “customer service.” “All I need is your credit card number so I can reverse the charges.”
Microsoft Teams phishing attack pushes DarkGate malware
A new phishing campaign is abusing Microsoft Teams messages to send malicious attachments that install the DarkGate Loader malware.
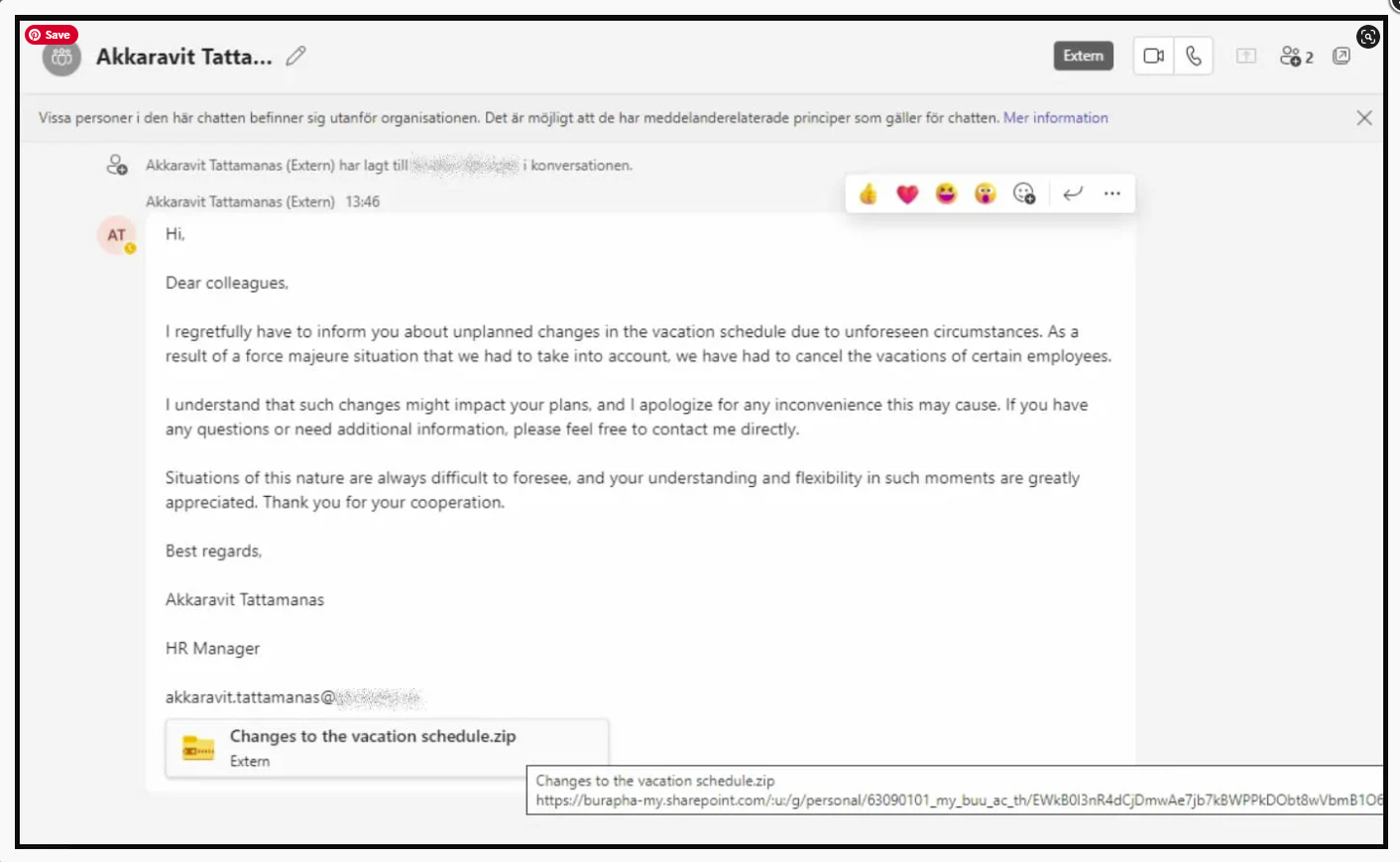
The campaign started in late August 2023, when Microsoft Teams phishing messages were seen being sent by two compromised external Office 365 accounts to other organizations.
These accounts were used to trick other Microsoft Teams users into downloading and opening a ZIP file named “Changes to the vacation schedule.”
Clicking on the attachment triggers the download of the ZIP from a SharePoint URL and contains a LNK file masquerading as a PDF document.
Researchers at Truesec analyzed the Microsoft Teams phishing campaign and found that it contains malicious VBScript that triggers the infection chain that leads to a payload identified as the DarkGate Loader.
To try and evade detection, the download process utilizes Windows cURL to fetch the malware’s executable and script files.
The script arrived pre-compiled, hiding its malicious code in the middle of the file, beginning with distinguishable “magic bytes” associated with AutoIT scripts.
Share
SEP





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com