Catch of the Day: Authentication Expired Phish
Chef’s Special: BEC Trend Phish
Also serving: Open Redirect Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
What’s the average number of phishing emails sent per day? 3.4 billion
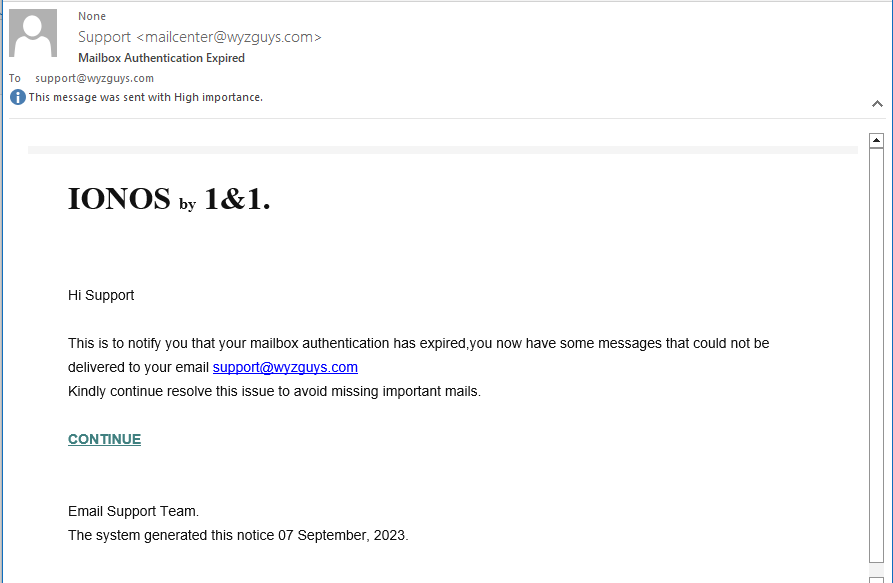
IONOS Mailbox Authentication Expired Phish
I received this phishing email on 2023-09-06 10:39 am Central time. The sender appears to be mailcenter@wyzguys.com but the mail headers showed my email domain was spoofed.
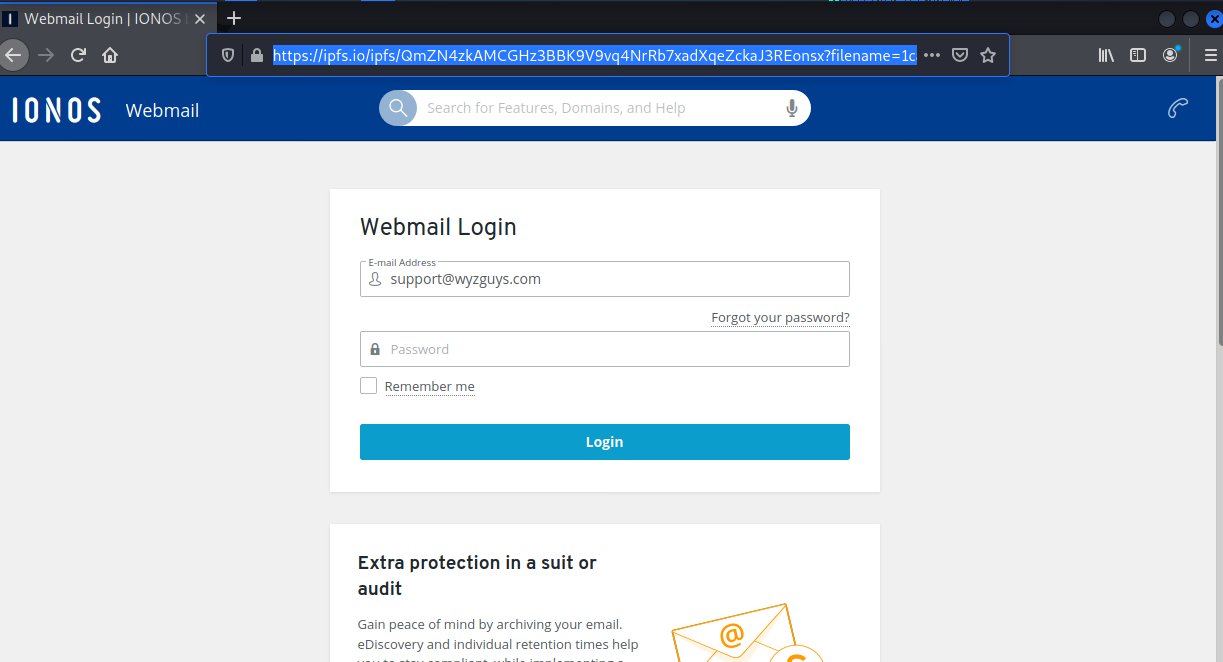
The CONTINUE link resolves to https://rb.gy/4atpx#support@wyzguys.com which redirects to https://ipfs.io/ipfs/QmZN4zkAMCGHz3BBK9V9vq4NrRb7xadXqeZckaJ3REonsx?filename=1can%20index.html#support@wyzguys.com
The https://rb.gy indicates the link first passes through Guyana. GY is the country code top-level domain (ccTLD) for Guyana.
The redirection go to a site on https://ipfs.io, which we have seen before, and is a publicly available web service.
Here is the email:
Clicking the link got us to this landing page
Another example of a credential stealing exploit, this time for an email account. This continues to be the vast majority of phishing attacks I see. You need to be on guard for links in emails, and find out where they go before clicking. As I have described before, you can investigate a link safely by right clicking on it, selecting copy hyperlink from the drop down menu, and pasting it into Notepad or another text editor. Notepad does not support active links, which makes it a safe choice. Sometimes simply hovering over the link will spawn a tooltip window that shows the link destination.
[Must Know] Top 10 Trends in Business Email Compromise for 2023
Researchers at Trustwave have published a report outlining trends in business email compromise (BEC) attacks, finding that these attacks spiked in February of 2023.
“For the first quarter of the year, we saw a 25% increase in unique attacks compared to the last quarter of 2022,” the researchers write. “February accounted for the highest volume of BEC emails in the first half of the year.
“January is the second most active month for BEC. Based on our historical data, BEC emails appear to increase during the first quarter after the December holiday slump. As the year begins, people are gearing up for the tax season and the start of new endeavors. Fraudsters are sure to take advantage of this.”
Threat actors abused various free email services, particularly Gmail, to launch these attacks.
“Google was the free email service provider of choice for BEC spammers in H1 2023, with a whopping 84% of all the free webmail addresses used,” the researchers write. “Other webmail services observed include: iCloud, VK, and Optimum (optonline[.net]).
“Aside from free email services, new-born domains that were created to mimic legitimate company domains in the From and Reply-to header fields were also used by spammers. 35% of newly registered BEC domains also use Google as their registrar, followed by NameCheap Inc. with 25%.”
The Trustwave researchers note that most BEC attacks attempt to dupe users via the following topics:
- “Payroll Diversion – Asks to change their bank account, payroll, or direct deposit information.
- Request for Contact – Asks for the recipient’s mobile number or personal email address.
- Task – Requesting assistance for urgent tasks or favors.
- Availability – Very short emails asking if the victim is available, at the desk or at the office.
- Invoice Transaction – Fraudulent emails about overdue invoice statements.
- Gift Purchase – Talks about surprising employees with a gift, usually asks the recipient to buy a gift card.
- Wire Transfer – Orders the recipient to prepare a certain amount of money for wire transfer.
- Request for Document – Requests for a copy of aging report, w2, or vendor list.”
KnowBe4 has two to add, making it a round 10:
- HR: Important – New Return To Office Policy
- HR: Please update your W-4 for our records
Here is an INFOGRAPHIC for Q2 2023 Top-Clicked Phishing Test Results:
https://blog.knowbe4.com/q2-2023-top-clicked-phishing
Blog post with links:
https://blog.knowbe4.com/trends-business-email-compromise
Open Redirect Flaws: The Newest Phishing Trick
No surprise: phishing attacks are on the rise, and an old technique is now—again—getting increasingly popular: open redirect flaws. These flaws allow attackers to redirect victims to malicious websites, even if the link in the phishing email appears to be legitimate.
How do open redirect flaws work?
Open redirect flaws occur when a website permits users to input their own URLs into a redirect link. If the website does not validate or sanitize these inputs properly, attackers can use the flaw to redirect victims to malicious websites.
For instance, attackers may send phishing emails that contain a link to a legitimate website, such as bankofamerica[dot]com. However, the link could actually redirect recipients to a malicious site that resembles the real Bank of America site.
To protect yourself from open redirect attacks, follow these steps:
- Be cautious of links in emails from unknown senders
- Don’t click on links in emails with typos or grammatical errors
- Hover over the links in emails to see the actual URL before clicking on them
- Use a security solution that can detect and block open redirect links
Organizations can also take measures to protect themselves from these types of attacks, such as providing security awareness training for employees on how to identify social engineering and phishing emails.
Here are some additional tips for recognizing open redirect flaws in phishing emails:
- Look for a URL shortener service. Attackers often use URL shorteners to conceal malicious links in phishing emails
- Always examine the URL of the link carefully. If it contains strange characters or parameters, it is best not to click on it
- Hover over the link before clicking on it. This will allow you to verify that the link points to the website it claims to be rather than malicious content
- When in doubt, it’s always best to be cautious and avoid clicking on it
By educating employees on open redirect flaws and paying close attention to the links in emails, you can reduce the risk of becoming a victim of these flaws in phishing attacks.
Blog post with links:
https://blog.knowbe4.com/open-redirect-flaws-phishing-trick
Share
SEP





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com