Catch of the Day: IONOS IP Error Phish
Chef’s Special: MacBook Air Phish
Also serving: Spearphish, Redline Stealer Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
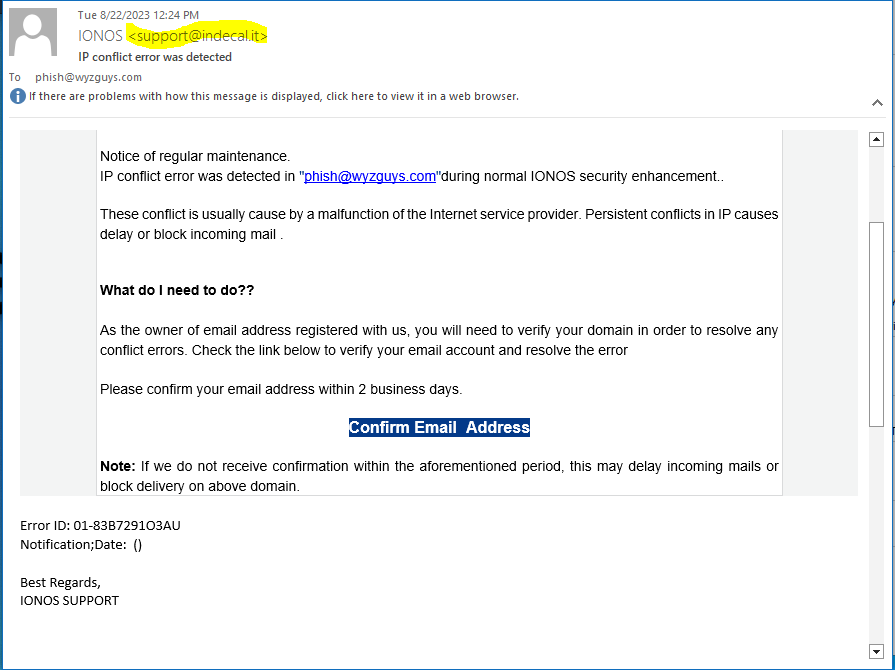
IONOS – IP Conflict Error Was Detected
I received this on 2023-08-23, but did not get around to investigation until the 23rd, which prevented me from seeing the landing page. But the Firefox warnings we very entertaining. Plus this is the first time I have seen the Tonga country code “.to” used in an exploit.
The email
First warning was the sender email address IONOS <support@indecal.it> This domain get flagged by Firefox in the next slide.
The Confirm Email Address link resolves to https://spt.to/ld4pwl (Tonga country code TO) which redirects to an Italian domain https://www.indecal.it/en/air-conditioning-radiant/ionos/.
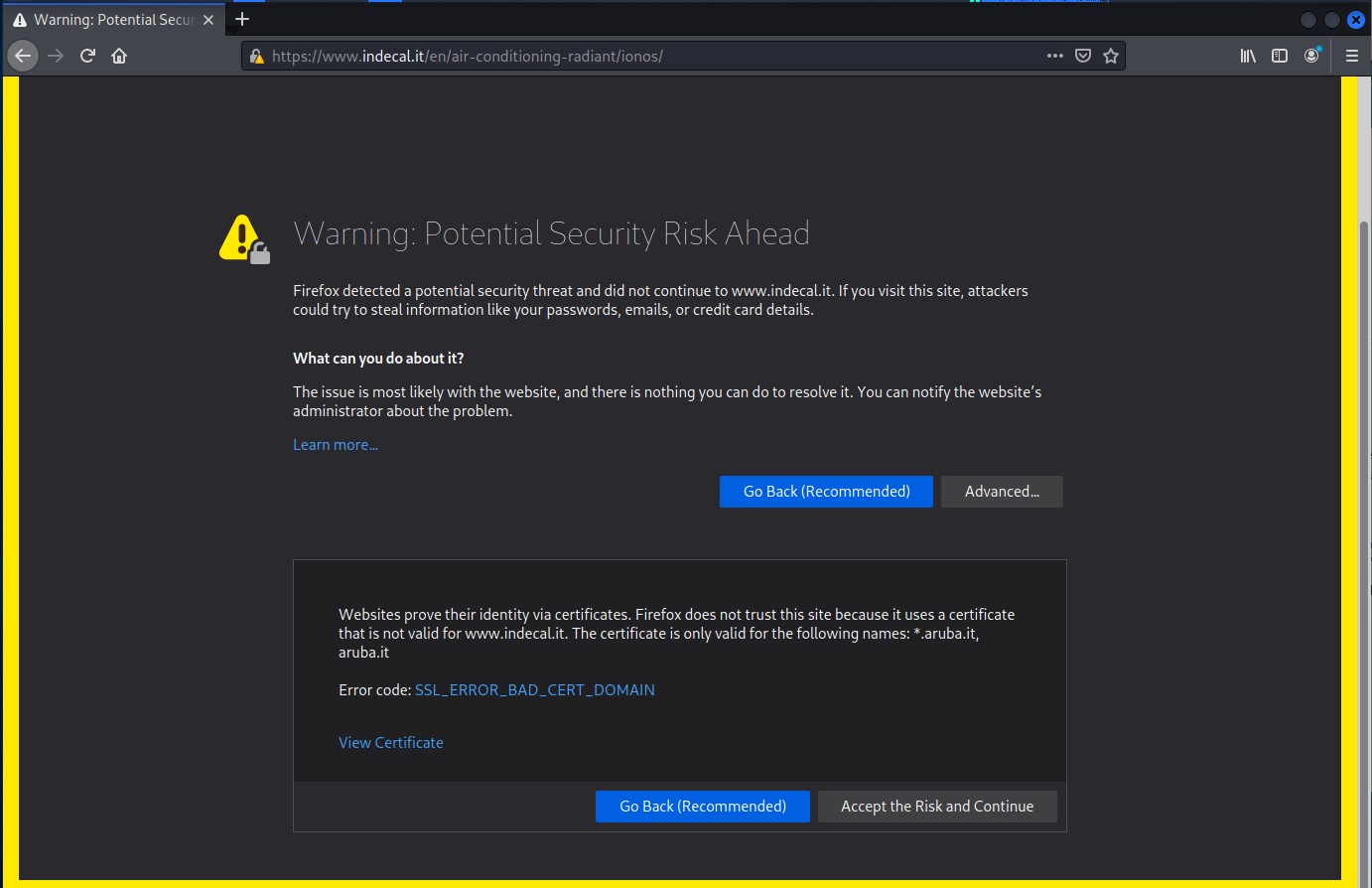
The domain indecal.it was flagged for using someone else’s digital certificate. I of source accepted the risk and continued – but not far.
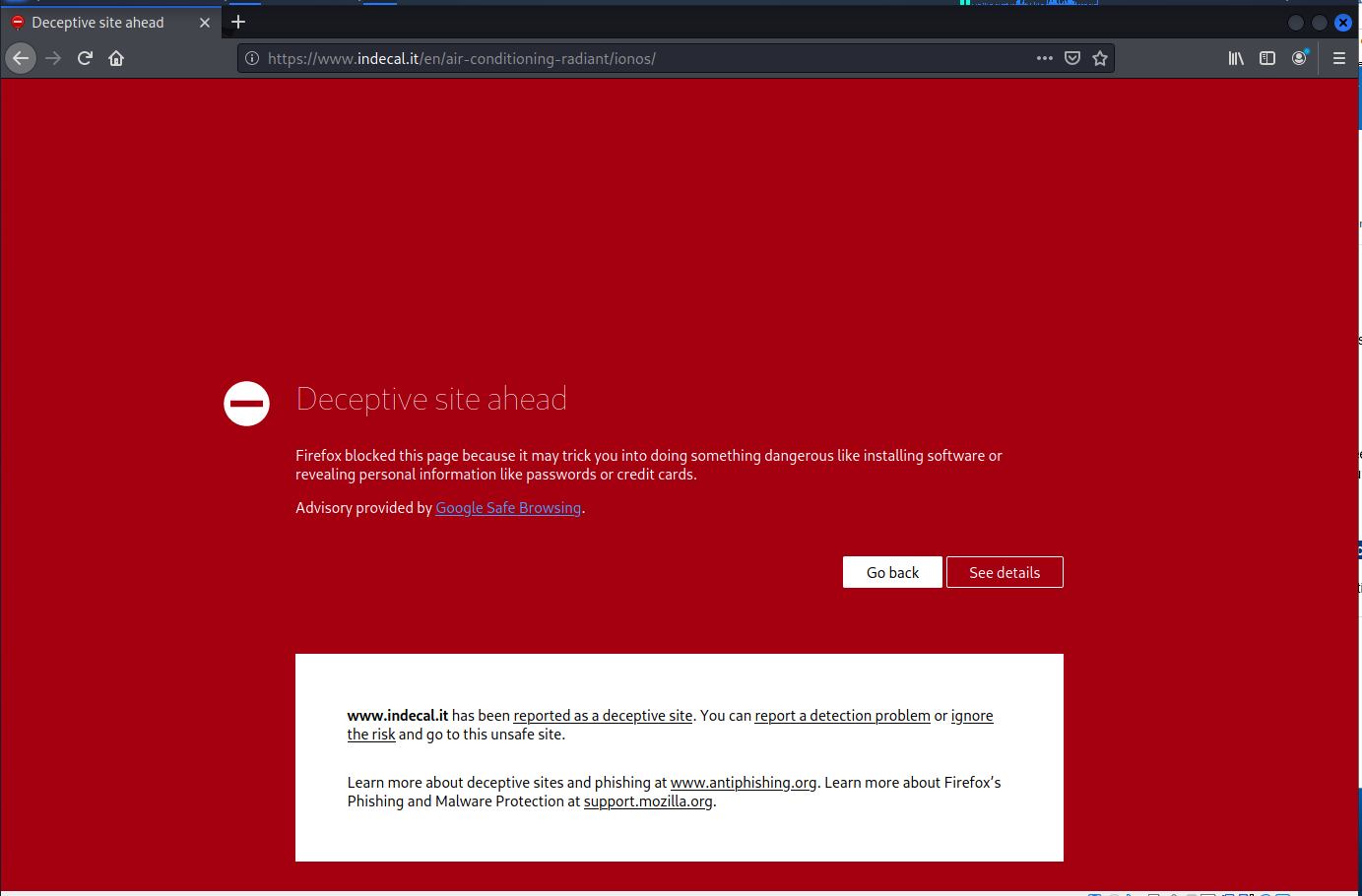
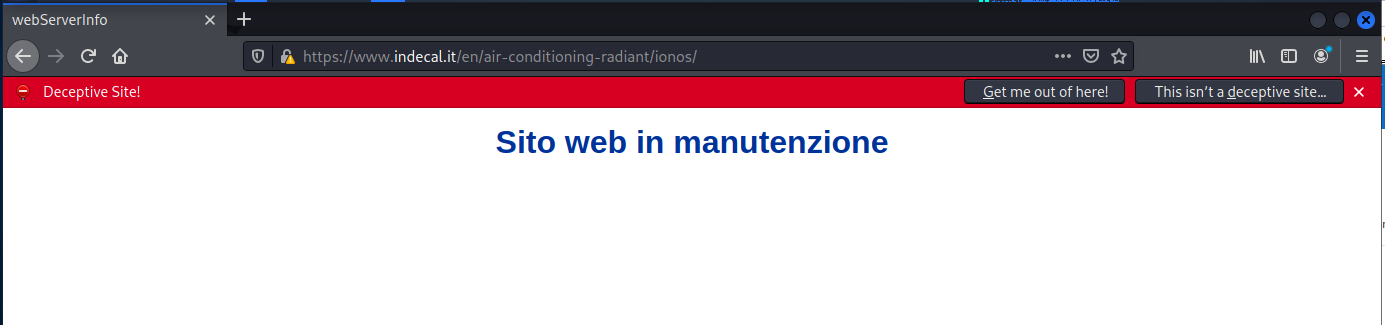
Firefox warning number two. I chose to “ignore the risk,” but the next page showed the the landing page had bee taken down. I tried to go to the home page at idecal.it but the same site maintenance page showed up. So the site owner evidently has taken down the whole site for cleaning.
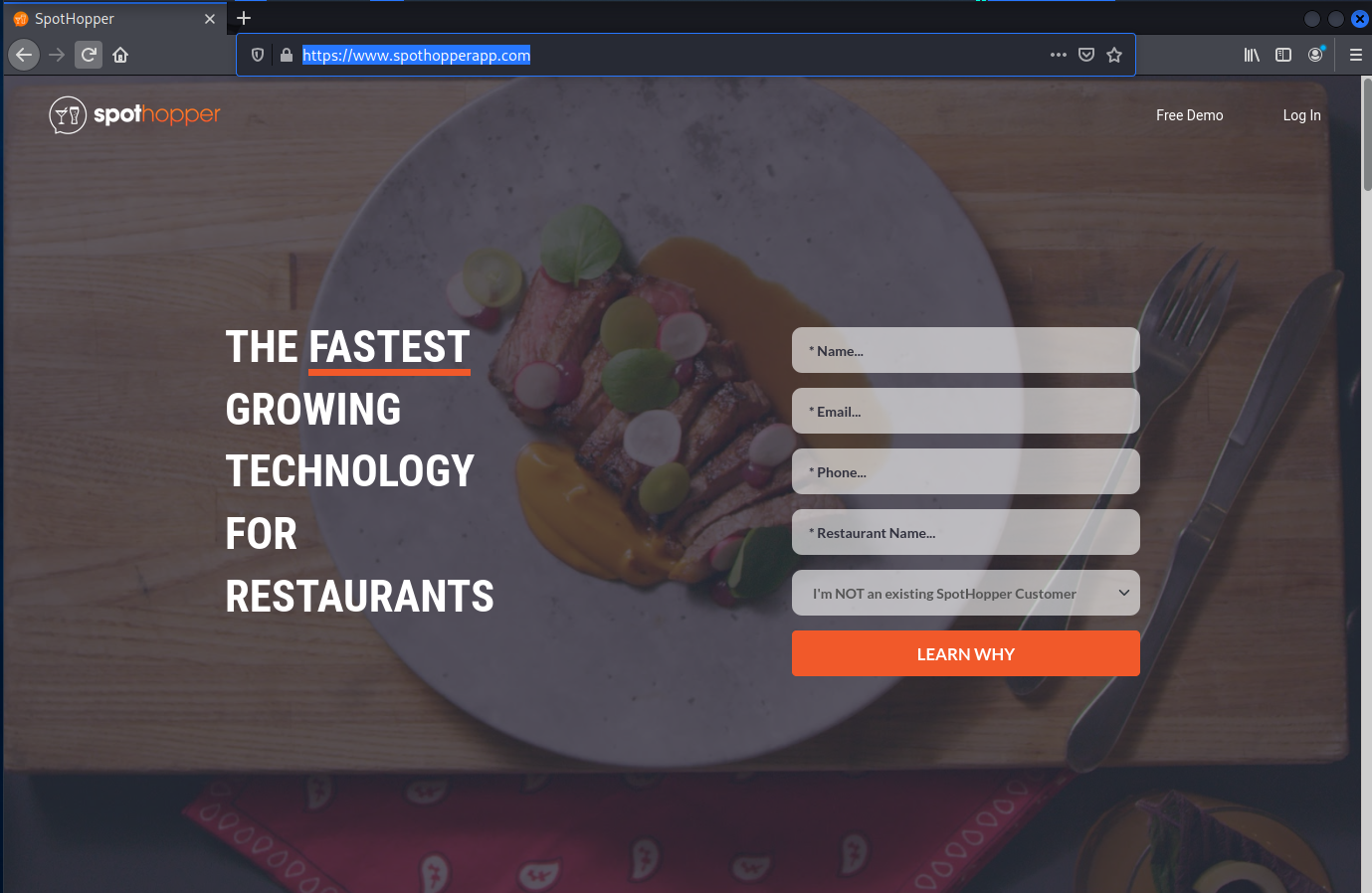
I tried the same thing with spt.to. Stripped off the /ld4pwl and was redirected to https://www.spothopperapp.com/. Very curious. Not sure how these sites are related, but it does not look good for our friends with the restaurant app
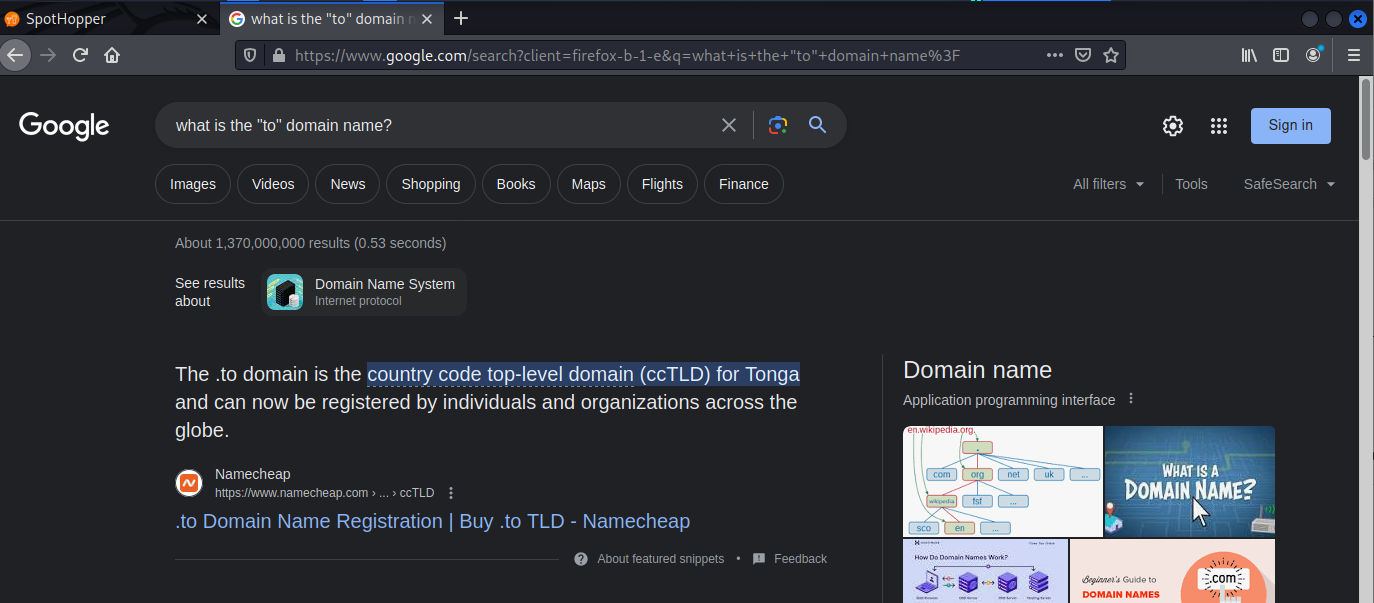
I was curious about the .to country code domain, so I did a quick web search.
I am assuming, from the story in the email, that this was a typical credential stealing exploit. To get there I had to basically drive through two “Road Closed” signs to get as far as I did. Hopefully you are not doing the same (unless of course you are a cybersecurity researcher).
The stories change by the goal remains the same, they want you to log in to their fake page so they can get your user ID and password. Just. Don’t!
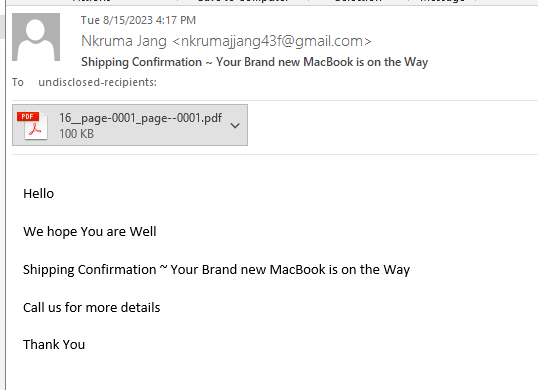
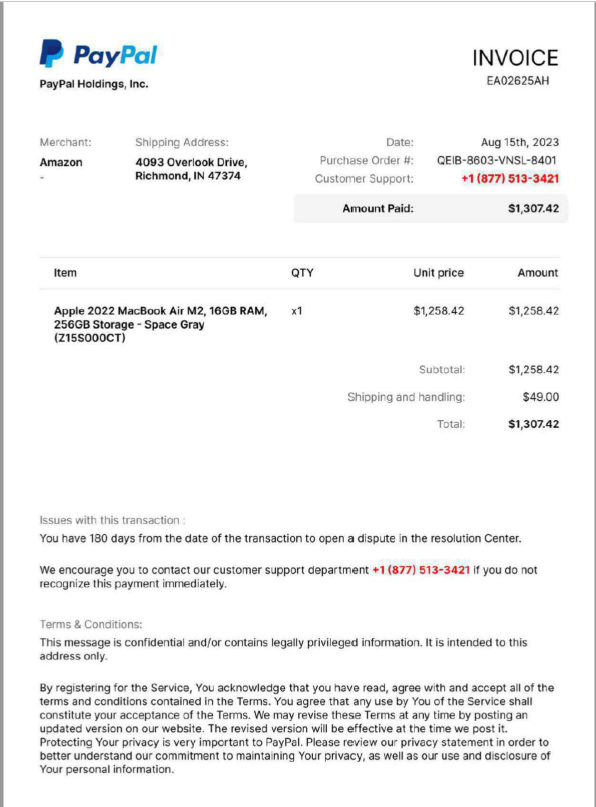
MacBook Air Is On The Way
This turned out to be a seriously low-tech exploit. Just the email and the PDF attachment with an 800 number to call, staffed by a bunch of friendly social engineers.
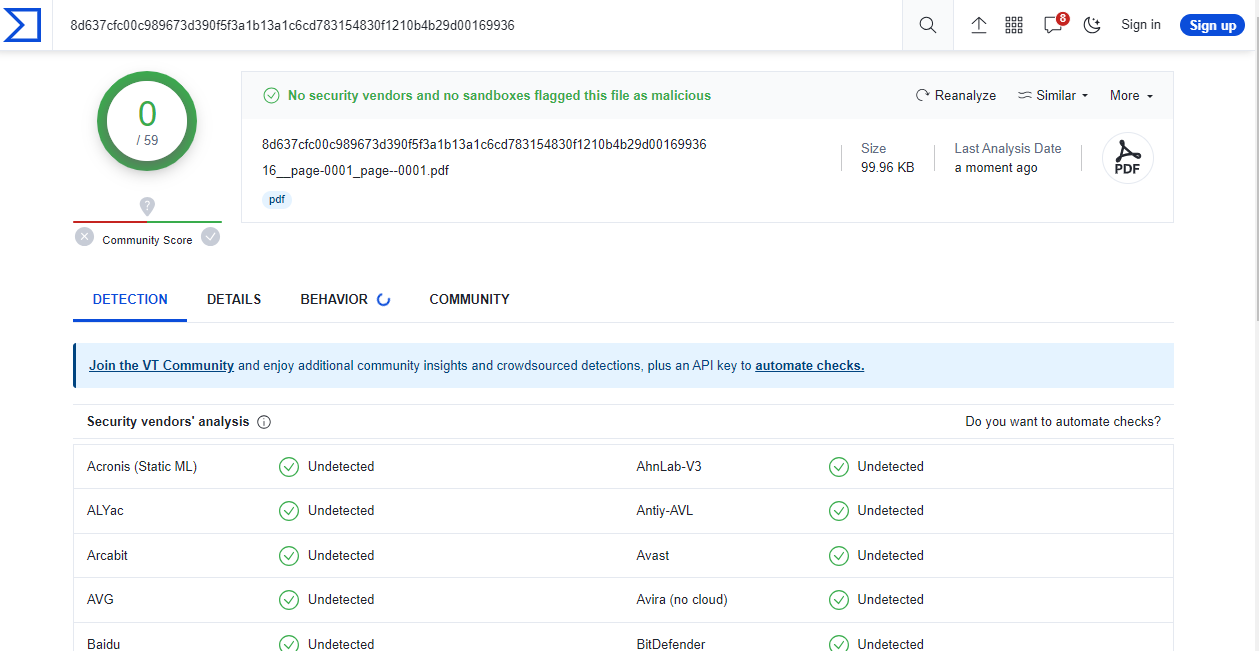
The email message is short and sweet. You are supposed to be curious or outraged enough to open the attachment. I ran the attachment through VirusTotal to be sure it was safe before I opened it and it was just a PDF invoice, without any embedded malware.
The invoice contains at toll-free support number to call. These exploits are designed to get your adrenalin flowing and have you calling to find out “what is this all about.” Canceling the order will be easy, as long as you can provide a credit card to apply the refund, Once they con you out of your card information, it will be resold, or used to purchase high-end goods that are easily resold.
Spear Phishing Prevention: 10 Ways to Protect Your Organization
Spear phishing is a more targeted and effective phishing technique that attempts to exploit specific individuals or groups within an organization. Read on to learn how to protect your company from these attacks.
Malware-as-a-Service: Redline Stealer Variants Demonstrate a Low-Barrier-to-Entry Threat
Aleksander W. Jarosz–August 23, 2023
EclecticIQ analysts collected samples from a RedLine stealer spam campaign between April and August 2023. The campaign has been successful through shifting command and control among recently created domains hosted on IP addresses with legitimate traffic. Redline developers provide minor iterations to previous variants. Disrupting the malware’s living off the land tactics is the best practice for security teams.
Share
SEP





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com