Catch of the Day: Two AMEX Phish
Chef’s Special: TripAdvisor Review Phish
Also serving: LinkedIn Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
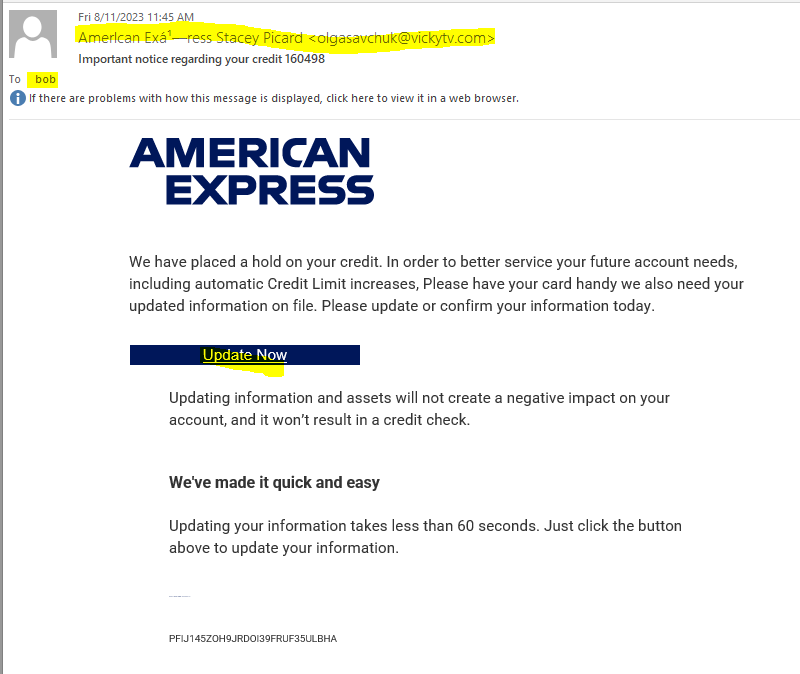
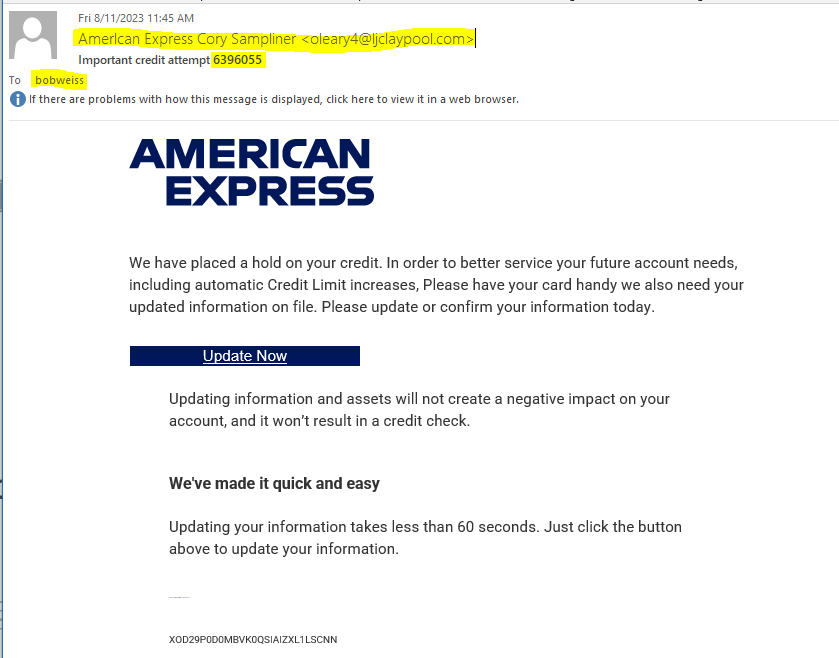
Two American Express Phish
I got two email phish with American Express trade dress. Each has a slightly different message. Each was sent to a different email address of mine. Look at the following emails, and notice the differences I have highlighted.
The Update Now button do resolve to different web addresses
- https://ecwo.sz-cc.com/?focythjx
- https://q4o3.ucelkimya.com/?focythjx
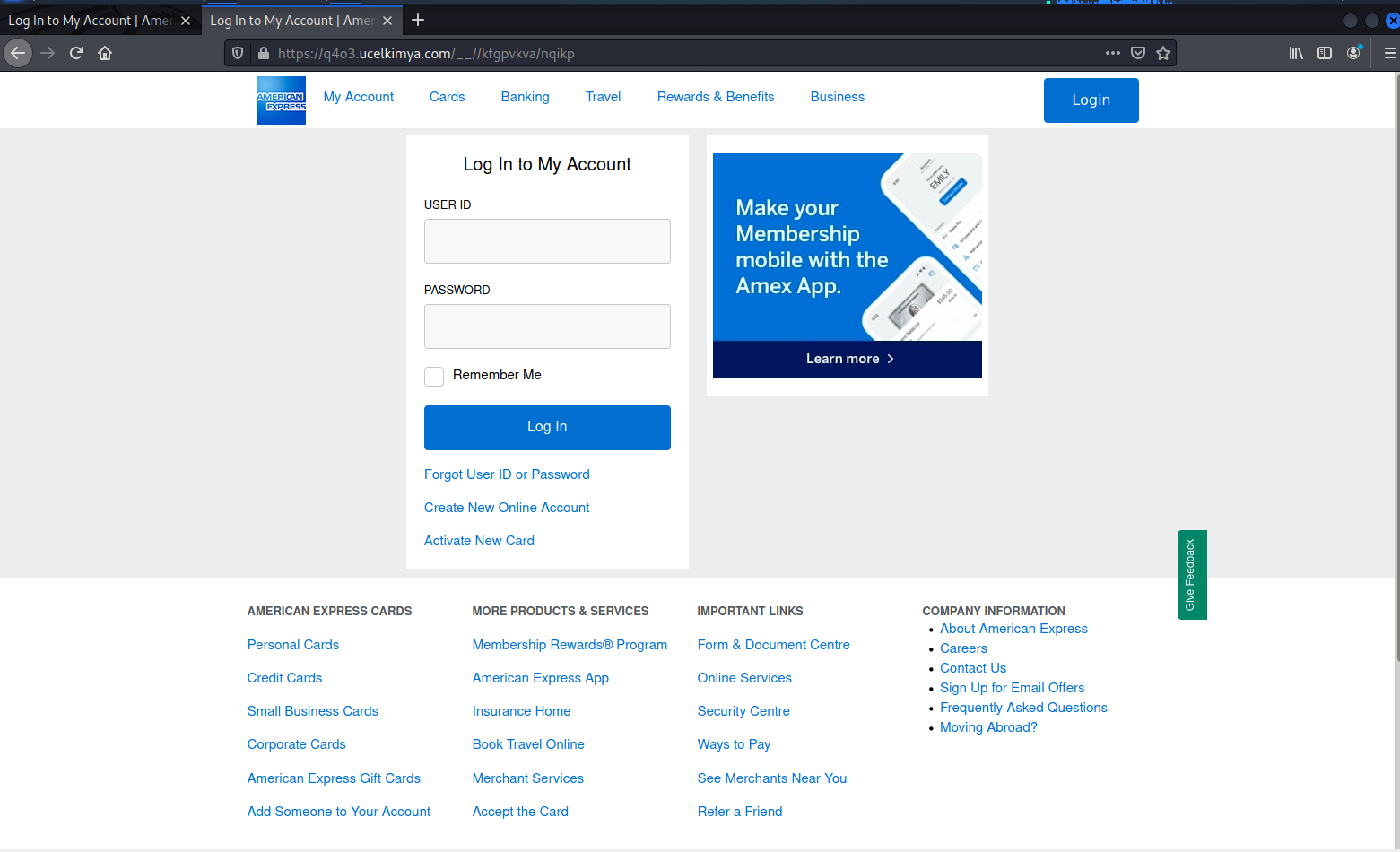
But the landing pages were identical
This exploit is designed to separate you from your American Express credentials. I don’t carry an AMEX card, so this exploit did not fool me for a second.
TripAdvisor Review Phish
Ransomware Distributed by Fake Tripadvisor Reviews
The Knight ransomware-as-a-service offering (formerly known as “Cyclops”) is using phony TripAdvisor complaints to deliver its malware, BleepingComputer reports.
“A newer version of this campaign spotted and analyzed by BleepingComputer now includes an HTML attachment named ‘TripAdvisor-Complaint-[random].PDF[dot]htm,'” BleepingComputer says. “When the HTML file is opened, it will use Mr.D0x’s Browser-in-the-Browser phishing technique to open what appears to be a browser window to TripAdvisor.
“This fake browser window pretends to be a complaint submitted to a restaurant, asking the user to review it. However, clicking the ‘Read Complaint’ button will download a malicious XLL file: TripAdvisor_Complaint-Possible-Suspension”
The Excel file attempts to trick the user into enabling an add-in, which will trigger the ransomware.
“When you open the XLL, Microsoft Excel will detect the Mark of the Web (MoTW), added to files downloaded from the Internet, including email,” BleepingComputer says. “If it detects the MoTW, it will not enable the .NET add-in built into the Excel document, nullifying the attack unless a user unblocks the file.
“However, if there is no MoTW flag on the file, Excel will prompt the user as to whether they want to enable the add-in….Enabling the add-in will cause the Knight Lite ransomware encryptor to be injected into a new explorer[DOT] exe process and begin to encrypt the files on your computer.”
BleepingComputer notes that in the ransomware’s current iteration, the threat actors won’t be able to tell which victims have paid the ransom, so it’s doubtful that they have any intention of sending decryption keys.
“The ransomware will create a ransom note named ‘How To Restore Your Files.txt’ in each folder on the computer,” BleepingComputer says. “The ransom note in this campaign demands $5,000 be sent to a listed Bitcoin address and also contains a link to the Knight Tor site.
“However, every ransom note in this campaign seen by BleepingComputer utilizes the same Bitcoin address which would make it impossible for the threat actor to determine which victim paid a ransom.”
New-school security awareness training helps prevent ransomware from getting onto your systems in the first place by teaching your employees to recognize phishing attacks.
Blog post with links:
https://blog.knowbe4.com/ransomware-fake-tripadvisor-reviews
LinkedIn Phish
[Must Know] Cybercriminals May Already Have Hacked Your LinkedIn Account. How to Secure.
New reports show many LinkedIn users have reported complaints about accounts being taken over by bad actors. In a statement from Cyberint researcher Coral Tayar, “Some have even been pressured into paying a ransom to regain control or faced with the permanent deletion of their accounts.”
5,000% increase in the last few months of search terms for LinkedIn hack or recover record
The reported complaints are on other social media forum platforms such as Reddit, Microsoft, and X with users expressing frustration due to the lack of response from the LinkedIn support team. Per Cyberint they have also seen an increase of 5,000% in the last few months of search terms for “LinkedIn hack” or “recover record.”
The access points cybercriminals are taking to infiltrate are through leaked credentials and/or brute-force to attempt to access a large number of LinkedIn accounts.
A high percentage of your C-level positions are using LinkedIn
If a user used strong passwords and/or two-factor authentication, it would only result in a temporary account lock. If your account was poorly protected, then cybercriminals can be able to quickly swap your listed email so then you can no longer have access. When a high percentage of your C-level positions are using LinkedIn—and almost everyone is—this hack could pose a huge risk for your org’s reputation if the attack is successful.
It is highly recommended to enable 2FA, and tell your employees it’s time to update their LinkedIn password to something unique and long, ideally a pass-phrase of 25 characters or more. New-school security awareness training teaches your users how to spot the red flags and provides frequent education that they can use to secure their social platforms.
Blog post with links:
https://blog.knowbe4.com/cybercriminals-hacked-linkedin-account
Share
AUG





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com