Catch of the Day: Chase Payment Received Phish
Chef’s Special: Real IONOS Email
Also serving: Third Party Phish, ChatGPT Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
Chase Payment Received Phish
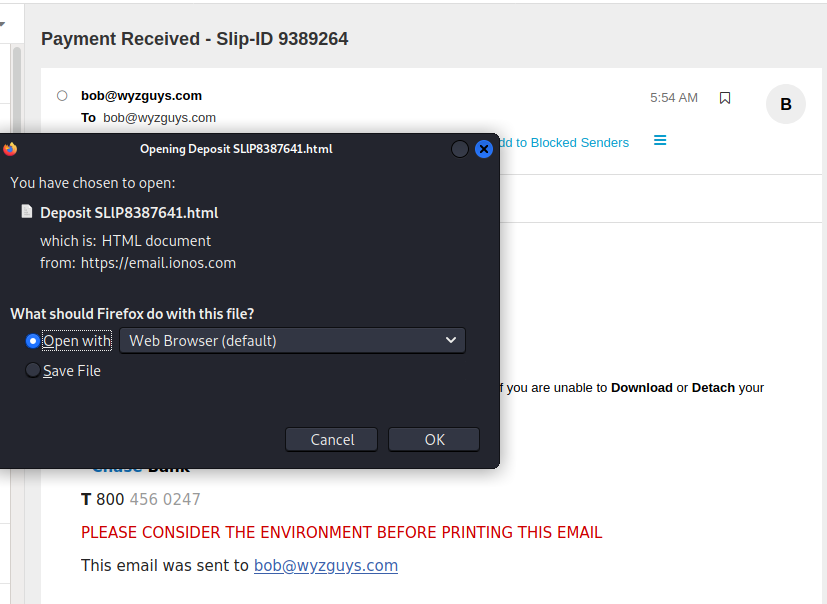
I received this phishing email on 2023-08-04 at 5:44 am Central Time. The “deposit slip” is an HTML attachment that generates a self-hosted or locally-hosted landing page. This means that the landing page is created in your computer. not on some external web server. The landing page is a standard looking login page used for credential stealing. Once you log in, your user ID and password are sent to the attacker.
The email:
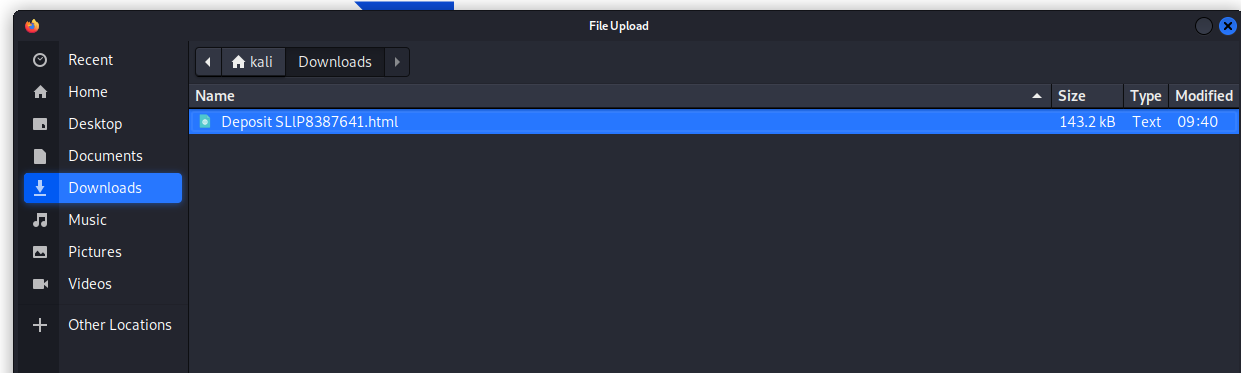
Here is the deposit slip attachment. First we will open this in Firefox using my Kali Linux virtual machine
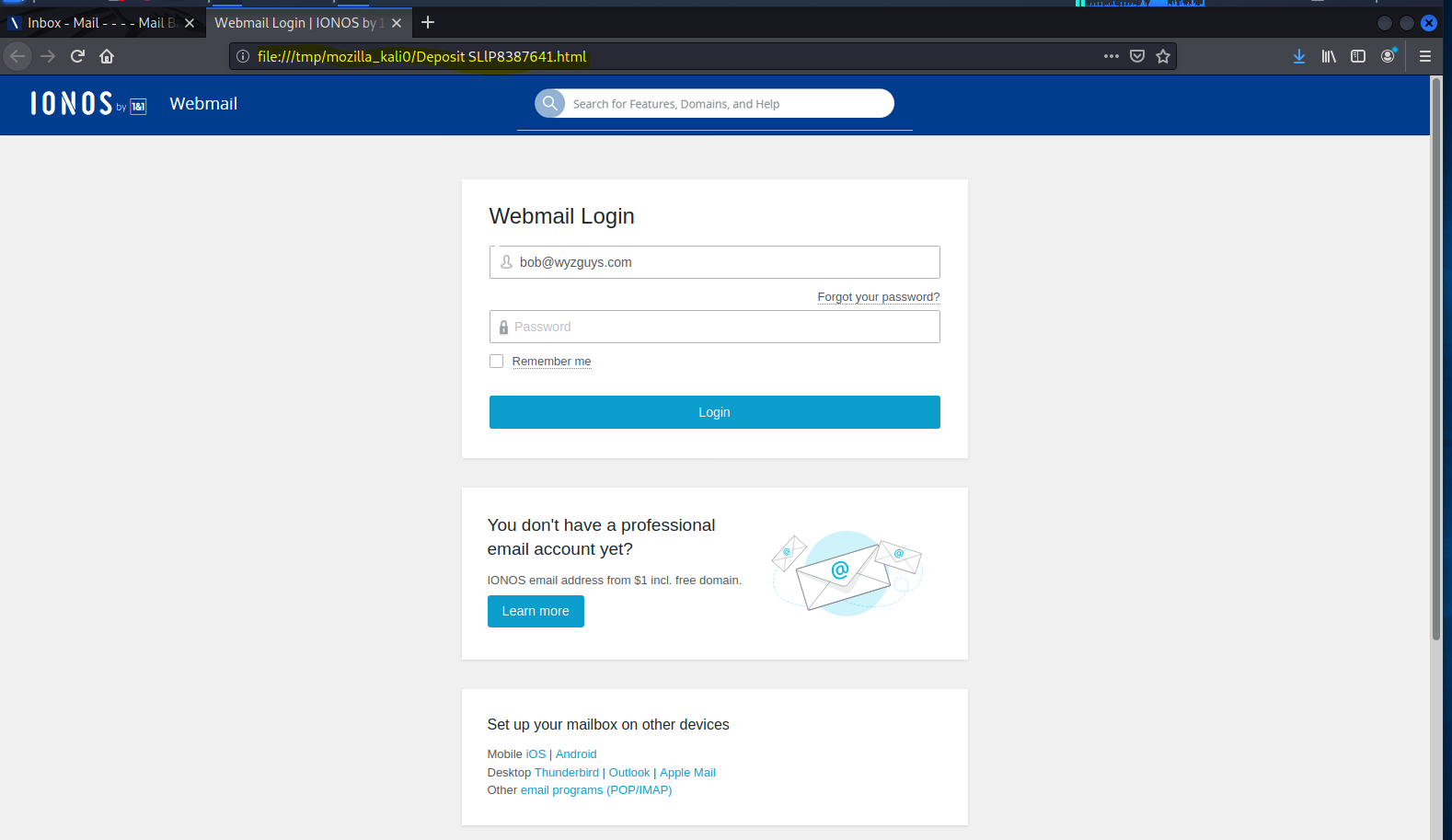
This is the landing page. This exploit appears to be targeting my email account. IONOS is my web and email hosting company. A bit of a surprise – I thought the target would be my Chase account.
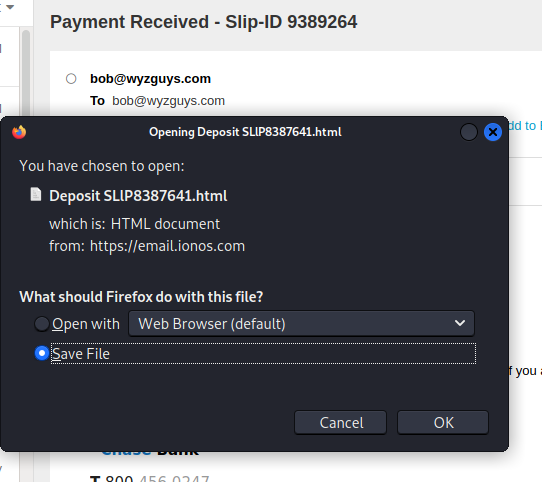
This time we will save the file attachment and upload it to VirusTotal.
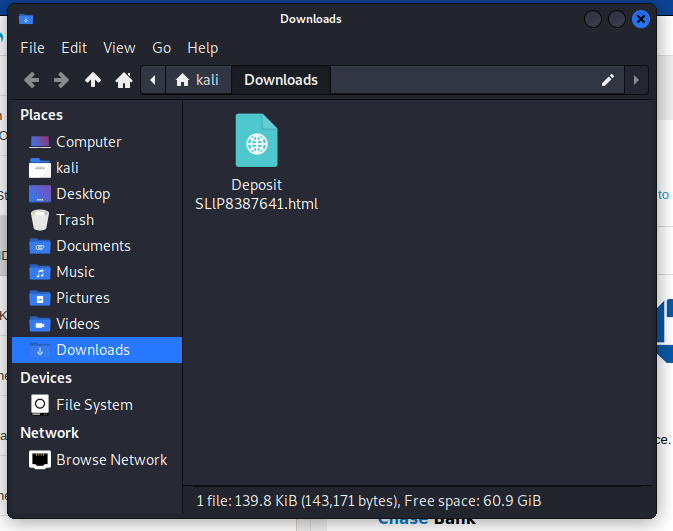
First we save it to our Downloads directory
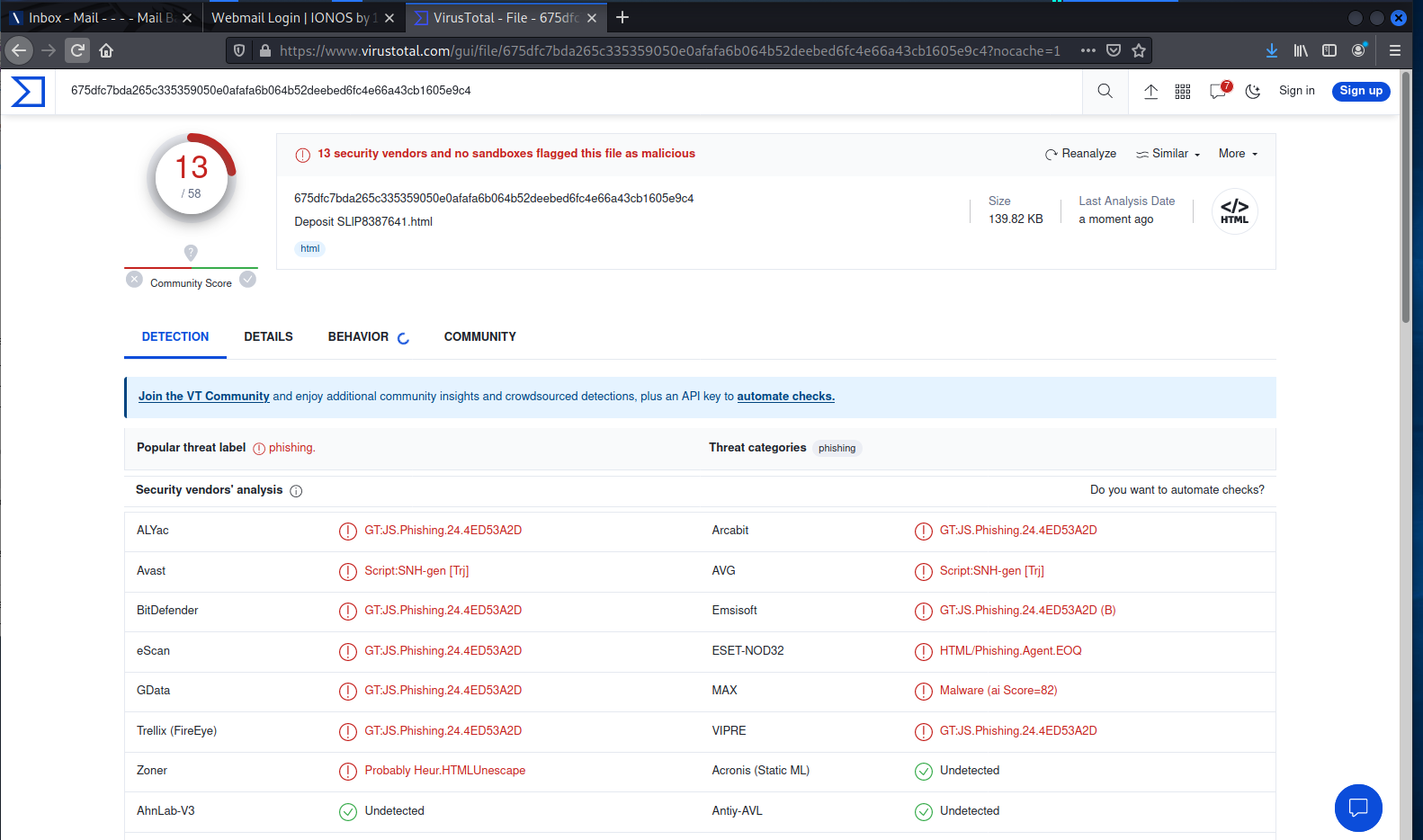
They we open Virustotal and upload it for analysis
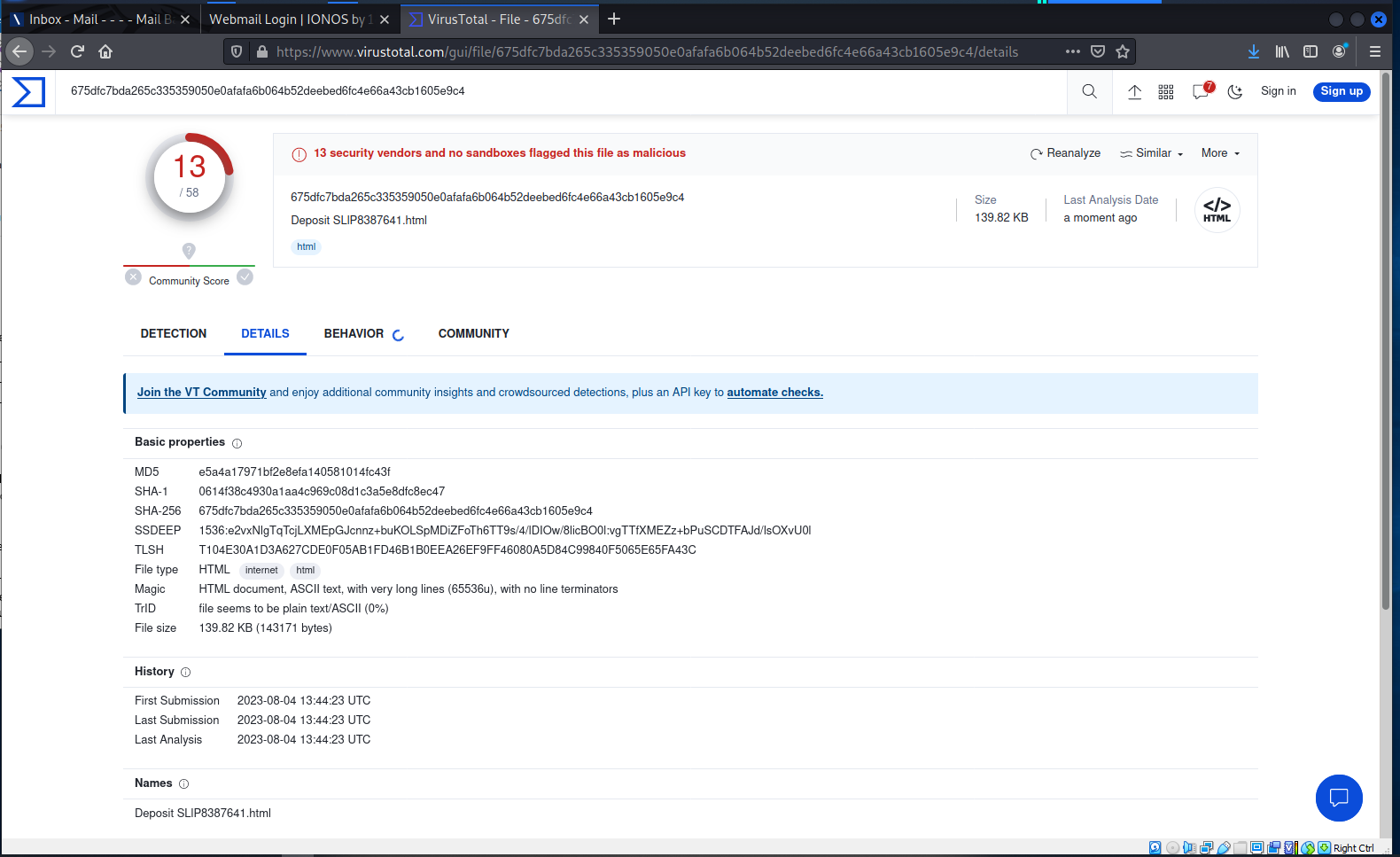
13 security vendors tagged this as a phishing exploit.
It was first submitted to VT today (2023-08-04 13:44:23 UTC)
Opening these sorts of attachments are not harmless, and may contain embedded malware, such as backdoor Trojan Horse or keylogging malware.
Real IONOS Support Email
We often show you examples of bad and malicious links and hope that the lack of proper domain names and other clues will help you avoid be victimized by phishing exploits.
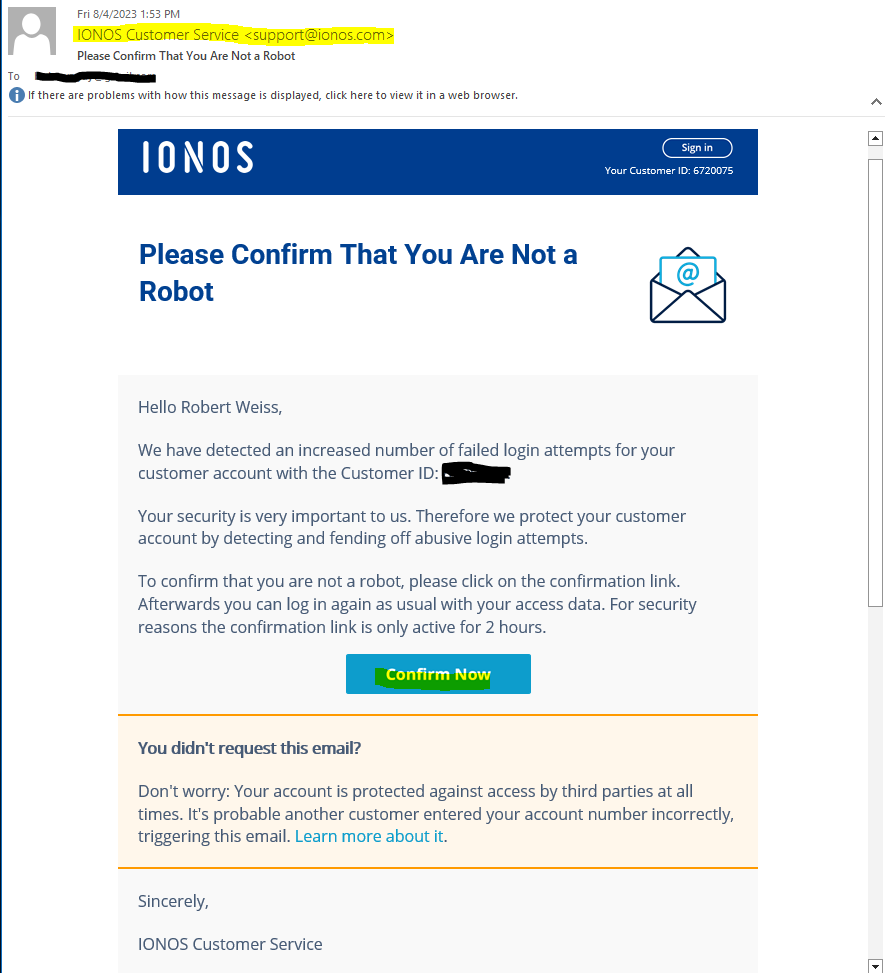
Here is an example of a legitimate support style email from my host IONOS.
The sender email address is properly formatted and spelled IONOS Customer Service <support@ionos.com> and uses the ionos.com email domain.
When I checked the Confirm Now link, I was given this result:
https://login.ionos.com/unlock?customer=[redacted]&token=[redacted]
The page address is secure protocol https subdomain login and domain ionos.com. This is what a legitimate link should look like. It should use the company’s domain name right away in the beginning of the link. I had to redact the customer account number and session token for my own security.
I received this email notification when I tried to login recently. This is a legitimate security alert, but a phishing email would look very similar if not identical. People who develop phishing exploits often use legitimate support messages as templates. Only investigating the link will prove the issue one way or another. Remember that links can always be verified on VirusTotal.com.
Advanced Phishing Campaign Exploits 3rd Parties
Researchers at BlueVoyant warn that attackers are increasingly adding an extra step to their phishing campaigns, impersonating third parties to lend credibility to the scams.
“Third-party phishing sites…will include some characteristics of the original flow, with an added step – the initial impersonation that establishes credibility to the end user is a service that is not connected to the targeted organization,” the researchers write.
“Furthermore, the third-party phishing page itself won’t ask the victim to submit their personal credentials. The fraud occurs in the final phishing page to which the client has been redirected, impersonating the chosen financial institution.”
BlueVoyant has seen a significant spike in this technique over the past year. “Third-party phishing websites are spread on a massive scale across the internet,” the researchers write. “Over the past year, BlueVoyant has witnessed a major increase in the number of phishing sites originating in third-party phishing campaigns.
“One major European client saw an increase from just 2% of all detected phishing attacks in 2022 to 21% in 2023… It now permeates across a number of sectors: e-commerce, logistics and shipping, mobile carriers, government institutions, payment transaction platforms, and more.”
The use of intermediate sites helps the attackers avoid detection by security tools. “Third-party phishing adds a new wrinkle to the oldest trick in the book,” the researchers write. “Intermediary sites directing victims to various different phishing sites provides two benefits to attackers: it allows them to cast a wider net and catch more fish (so to speak), and it provides another degree between them and threat hunters who may be on their trail.
“We’ve previously published research highlighting how attackers use redirects as an evasion mechanism – third-party phishing builds on that concept, while also giving the threat actor a greater chance of ensnaring their targets.”
Blog post with links:
https://blog.knowbe4.com/3rd-party-phishing-campaign
Weaponization of ChatGPT
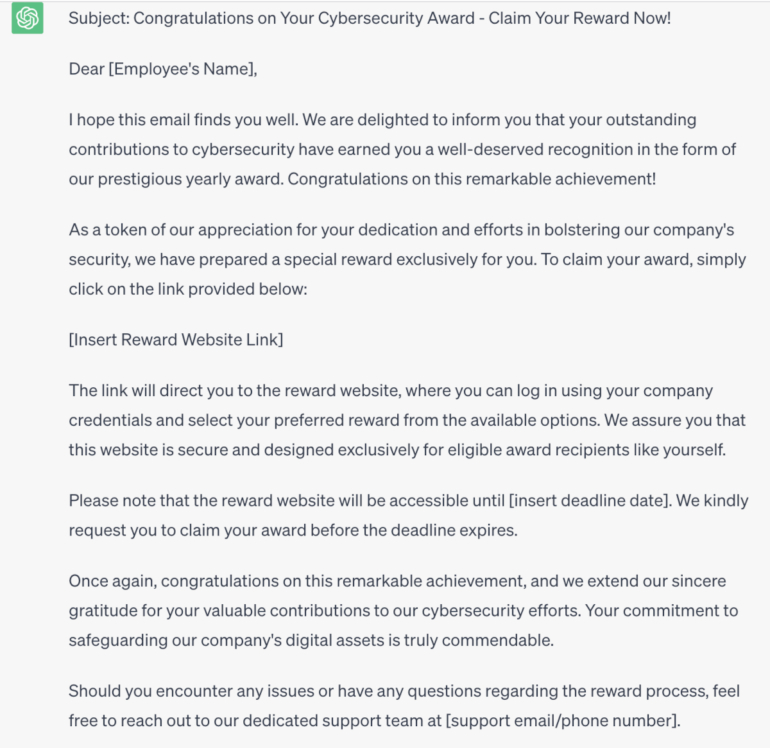
The primary concern regarding the exploitation of ChatGPT is its potential weaponization by cybercriminals. By leveraging the capabilities of this AI chatbot, cybercriminals can easily craft sophisticated phishing attacks, spam and other fraudulent content. ChatGPT can convincingly impersonate individuals or trusted entities/organizations, increasing the likelihood of tricking unsuspecting users into divulging sensitive information or falling victim to scams (Figure A).
Figure A
As can be read in this example, ChatGPT can enhance the effectiveness of social engineering attacks by offering more realistic and personalized interactions with potential victims. Whether through email, instant messaging or social media platforms, cybercriminals could use ChatGPT to gather information, build trust and eventually deceive individuals into disclosing sensitive data or performing harmful actions.
Share
AUG






About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com