Catch of the Day: Email Delivery Phish
Chef’s Special: QR Code Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
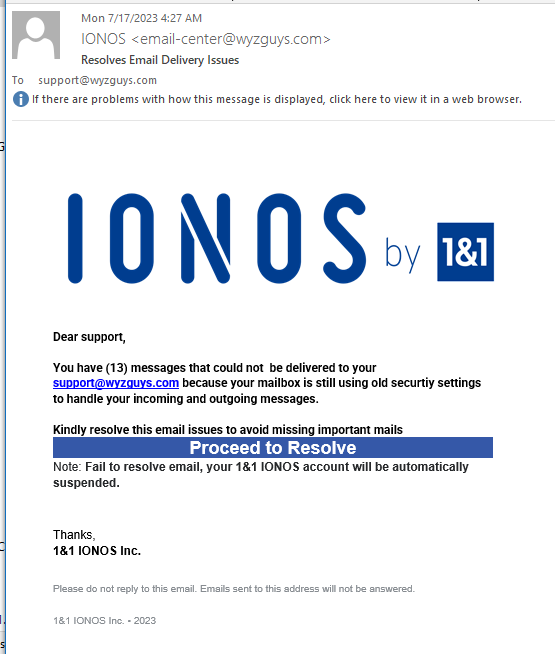
Resolves Email Delivery Issues
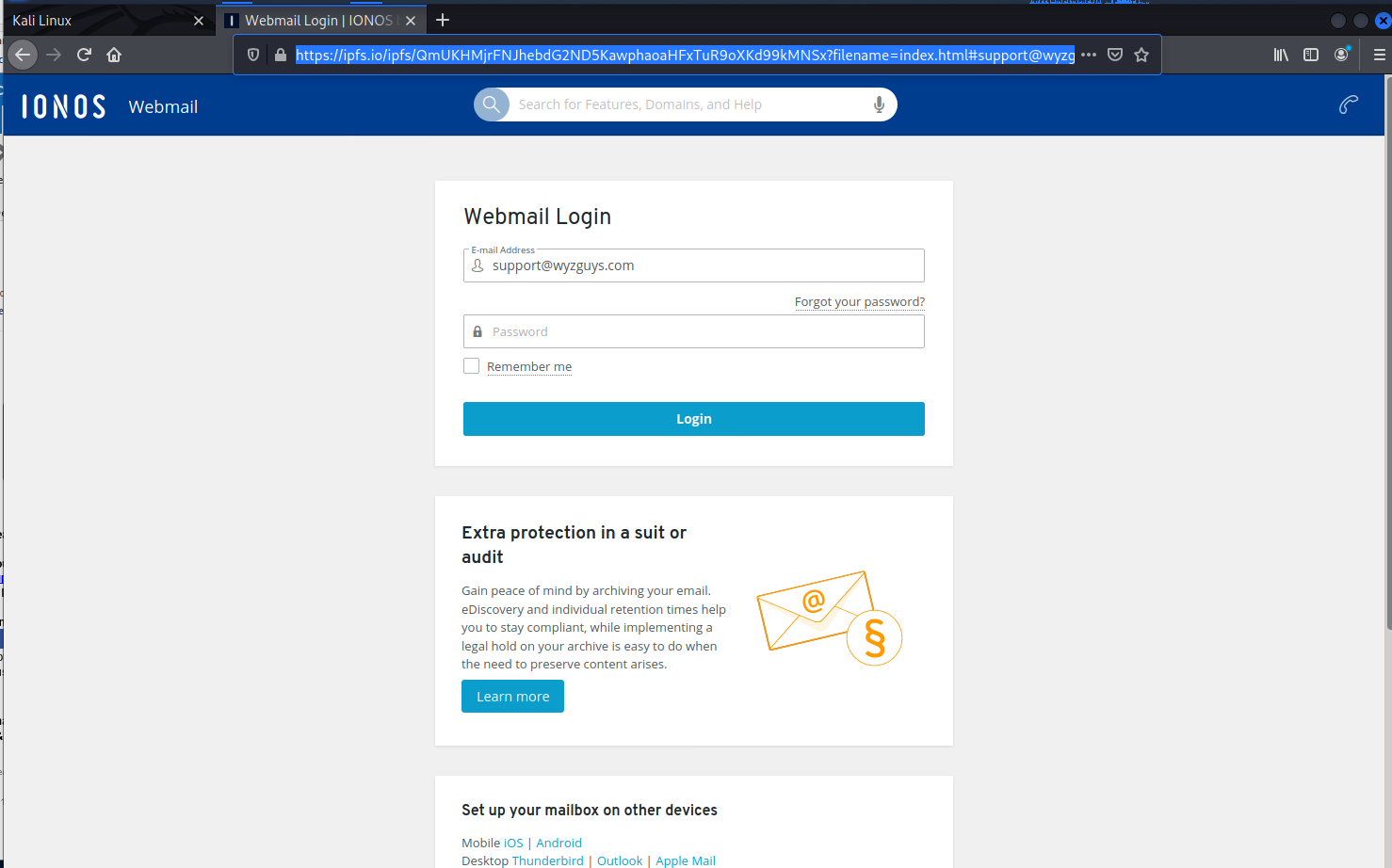
I received this on Monday 2023-07-17 at 4:27 AM. The Proceed to Resolve button resolved to https://bnnx.page.link/1#support@wyzguys.com, and then was redirected to https://ipfs.io/ipfs/QmUKHMjrFNJhebdG2ND5KawphaoaHFxTuR9oXKd99kMNSx?filename=index.html#support@wyzguys.com.
Here’s the email. The sender address appears to come from my own email domain, but it from a fictitious sender email-sender@wyzguys.com.
This is the landing page. It is an excellent rendition of the legitimate IONOS login page. Just enter your password and your email credentials is stolen, and the attacker can now impersonate you using your real email account.
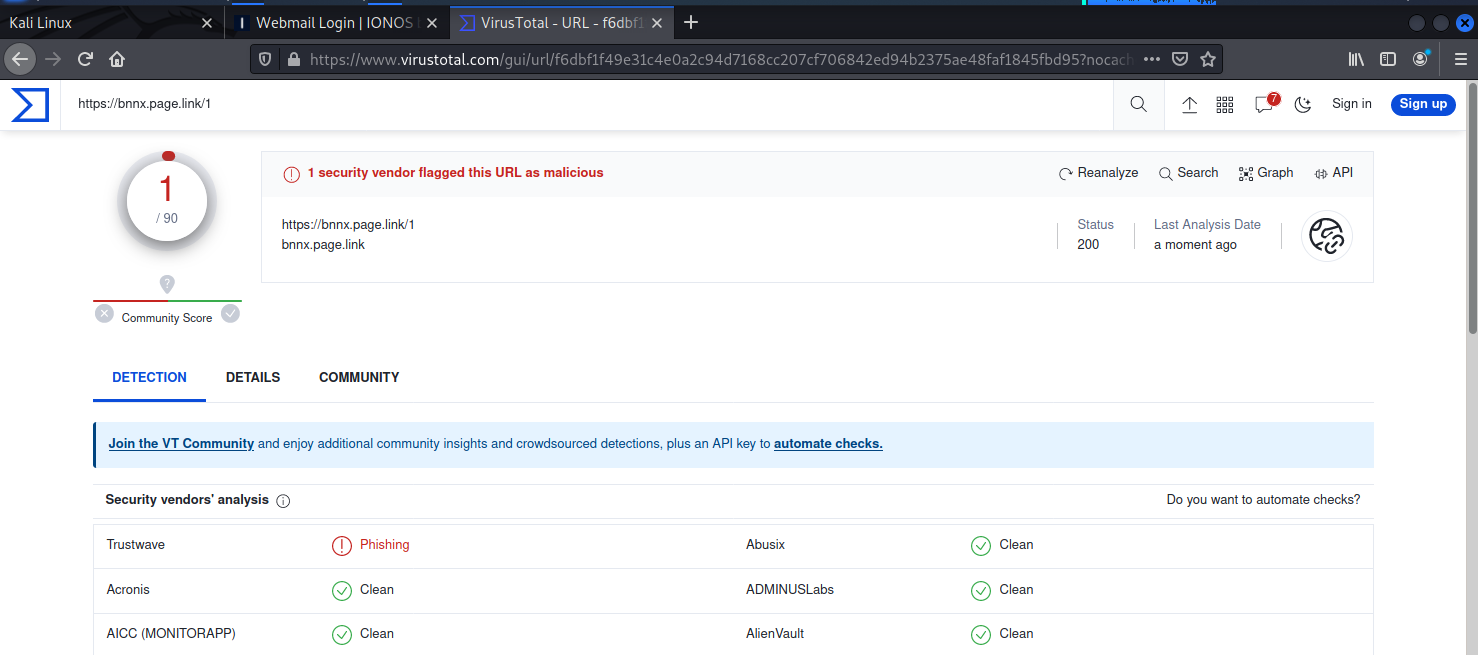
I sent the first link from the Proceed button to Virustotal. Since this is a new exploit, detection rates by VT are still low.
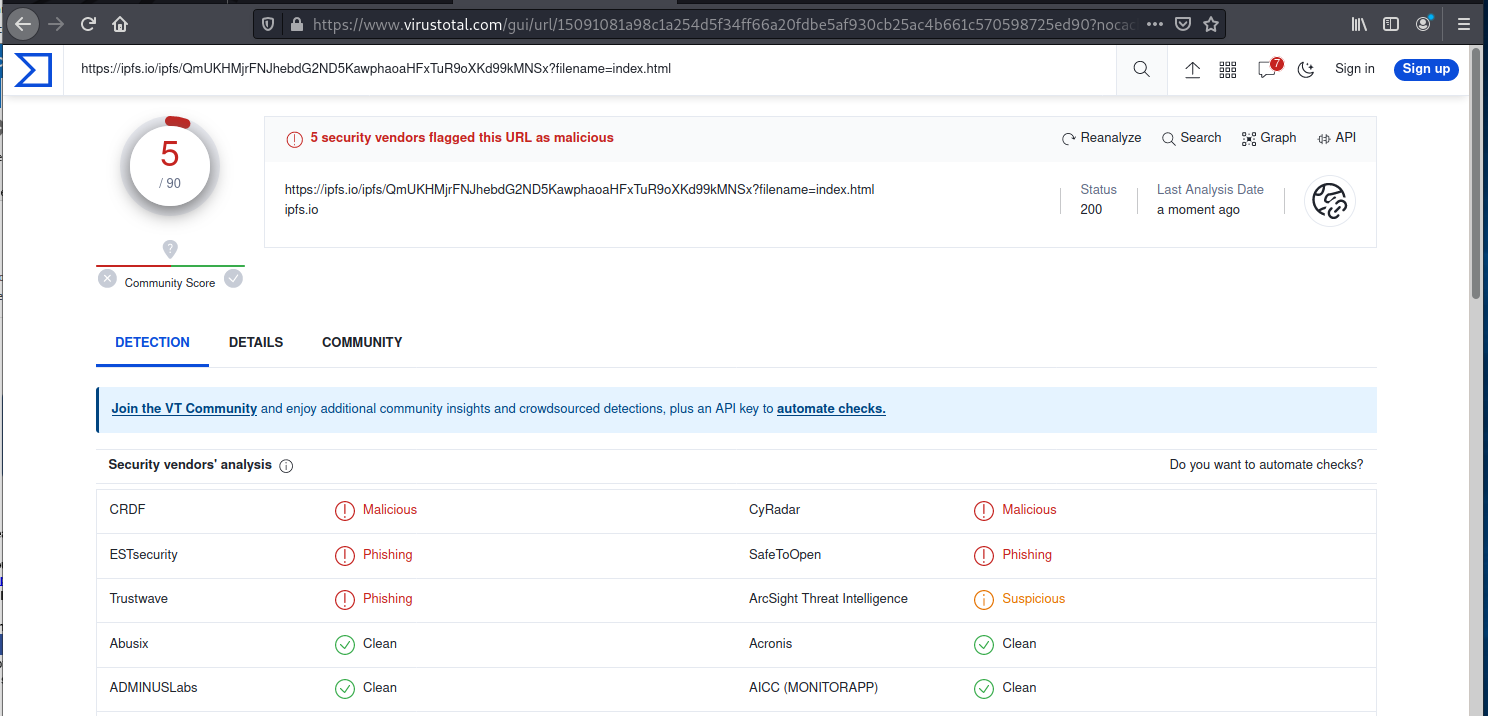
But the redirection link to the landing page is better known with 6 scanners identifying this as a phishing exploit.
The whole point of this redirection game it to use a new link on the email that will not be detected by file signatures or detection engines in email spam filters. The redirected link to the landing page is not detected by most spam and phish filters
Again, be careful when dealing with these sorts of “You got a problem” email. When in doubt, check it out with your vendor using a trusted link in your browser bookmarks. Login in too your account, and look for the “problem.” If you can’t find one, then you don’t have one.
Using a new twist to bypass detection from security solutions, cyber attacks are now employing QR codes that your users will not recognize as anything suspicious.
Threat actors need some means of getting a user to engage with malicious content – whether an attachment, link, or phone call, there needs to be some content within an email that provides the victim user with their next step.
Right behind this are the security solutions which have employed scanning those attachments, following the links to their end, etc. in an attempt to provide the user and their organization with a first layer of defense to stop such attacks before they start.
A new phishing attack method spotted by security researchers at Inky includes the use of a QR code, prompting a victim user to take a picture of the image and navigate to the resulting impersonated login page. More…
ShareJUL





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com