Catch of the Day: Account Verification Phish
Chef’s Special: BEC Phish
Also serving: Mail Delivery Error Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
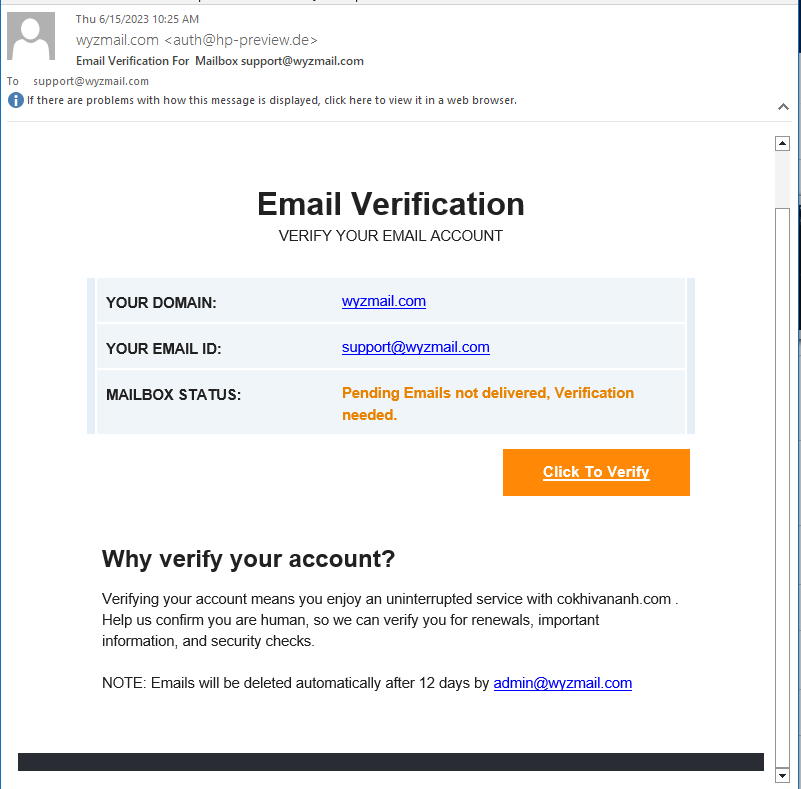
Account Verification Phish
I received this one on 2023-06-15 10:25 am CDT.
The Click to Verify link resolved to https://fleek.ipfs.io/ipfs/QmTxMCn9HYcdTHgZdUrhCbxCyXcd3FQTVV8d3SLD3PciRx?filename=ucto.htmll#support@wyzmail.com.
This revealed a login page hosted on a legitimate service provider ipfs.io.
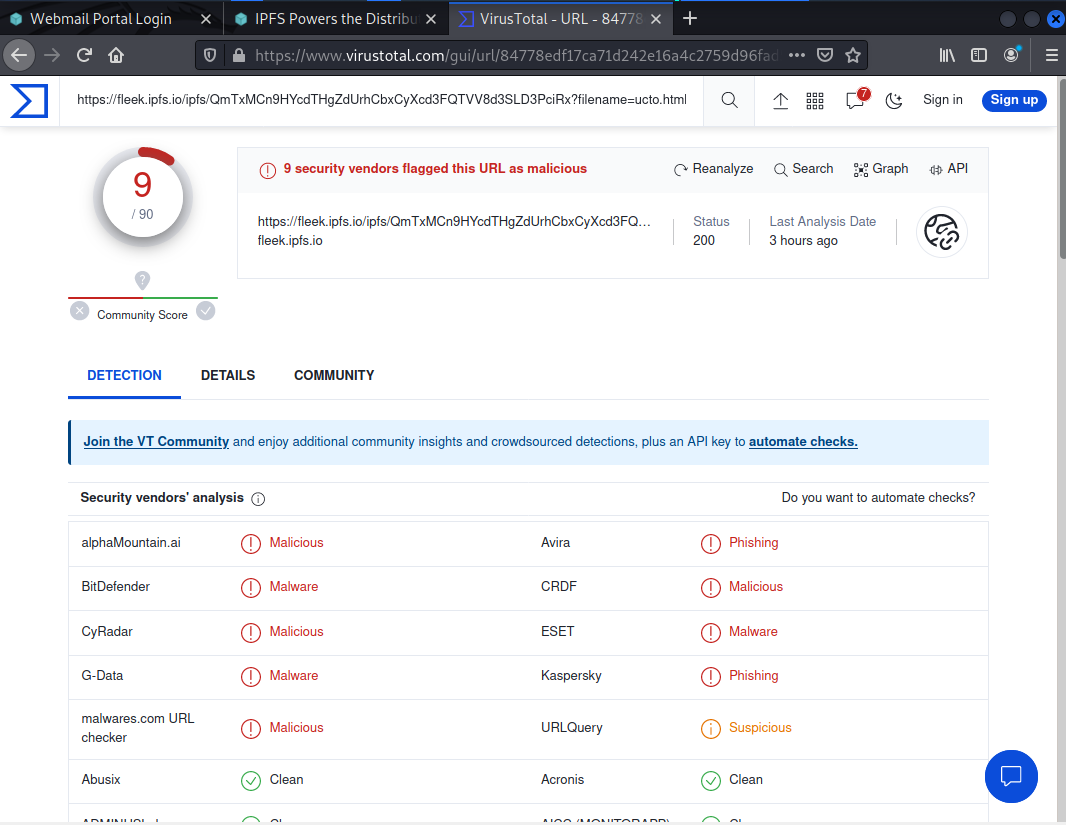
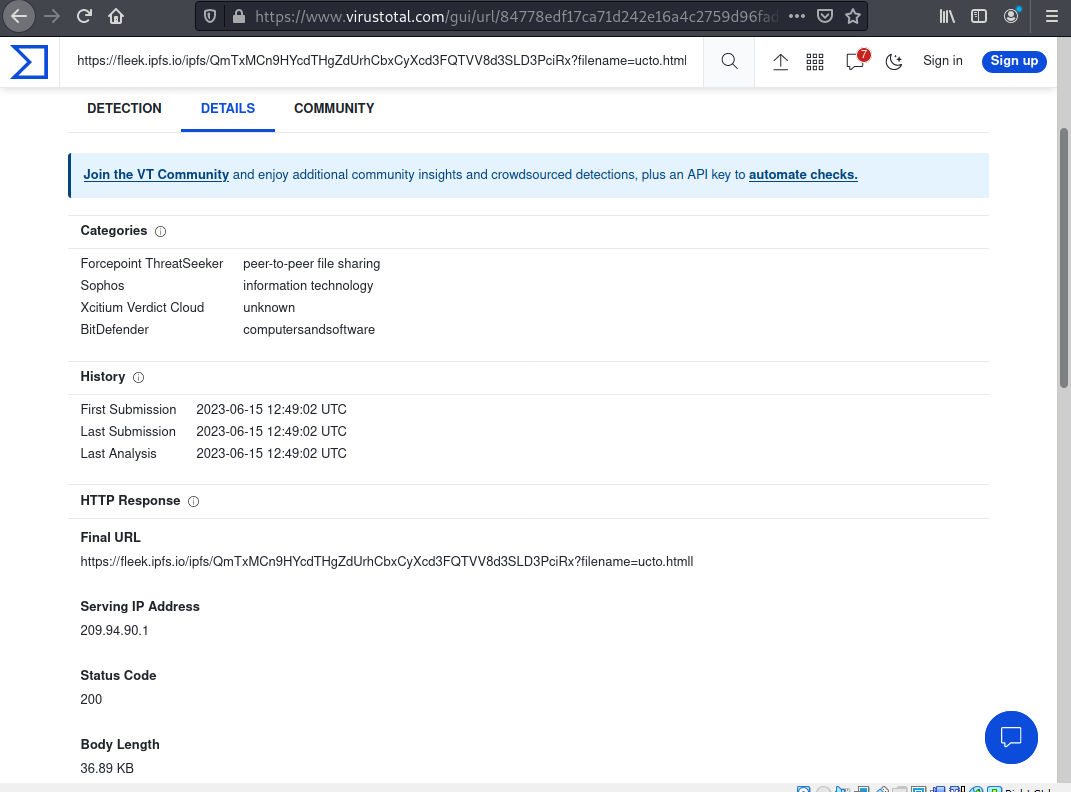
A quick look at the URL in Virustotal showed the link to be a known malicious phishing address.
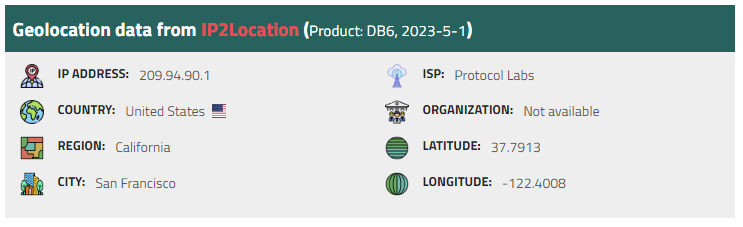
The hosting server is at 209.94.90.1. and provided by a service provider called Protocol Labs.
This is a credential stealing exploit. Pretty easy to spot because of the generic looking trade dress and the sender address.
New phishing and business email compromise campaigns increase in complexity, bypass MFA
Read the technical details about a new AiTM phishing attack combined with a BEC campaign as revealed by Microsoft, and learn how to mitigate this threat.
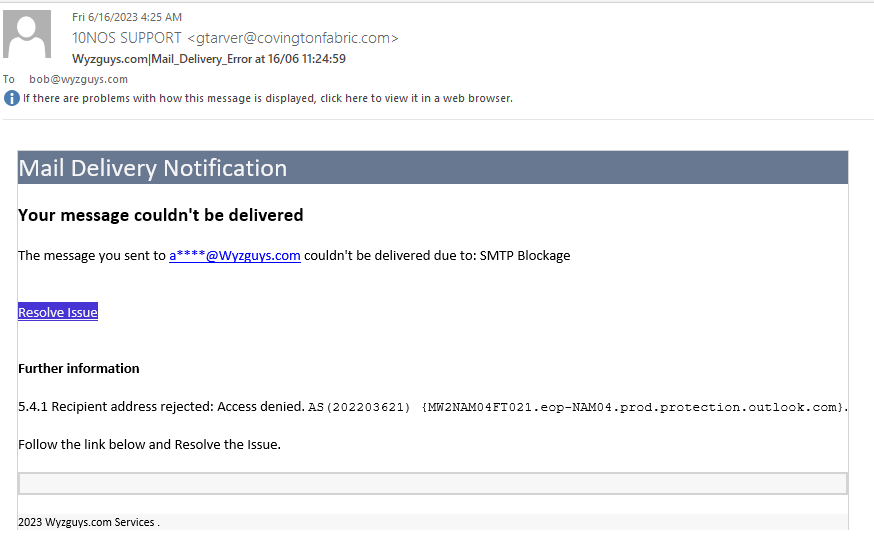
Mail Delivery Error Phish
Received this Friday 2023-06-16 4:25 AM CDT. Exploit still active when I started exploring it at 8:30 AM.
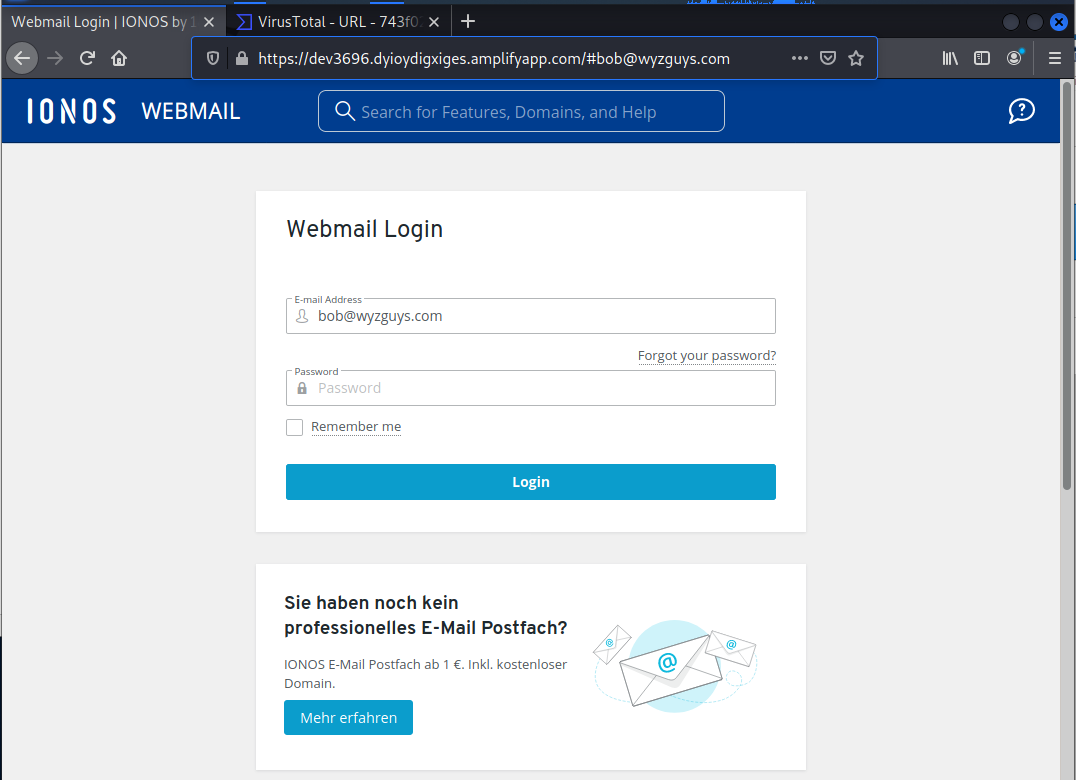
The Resolve Issue button resolves to https://href.li/?https://dev3696.dyioydigxiges.amplifyapp.com/#bob@wyzguys.com
which redirects to
https://dev3696.dyioydigxiges.amplifyapp.com/#bob@wyzguys.com
A fairly standard IONOS logon landing page for credential stealing. In this case the attackers want the log on to my web mail
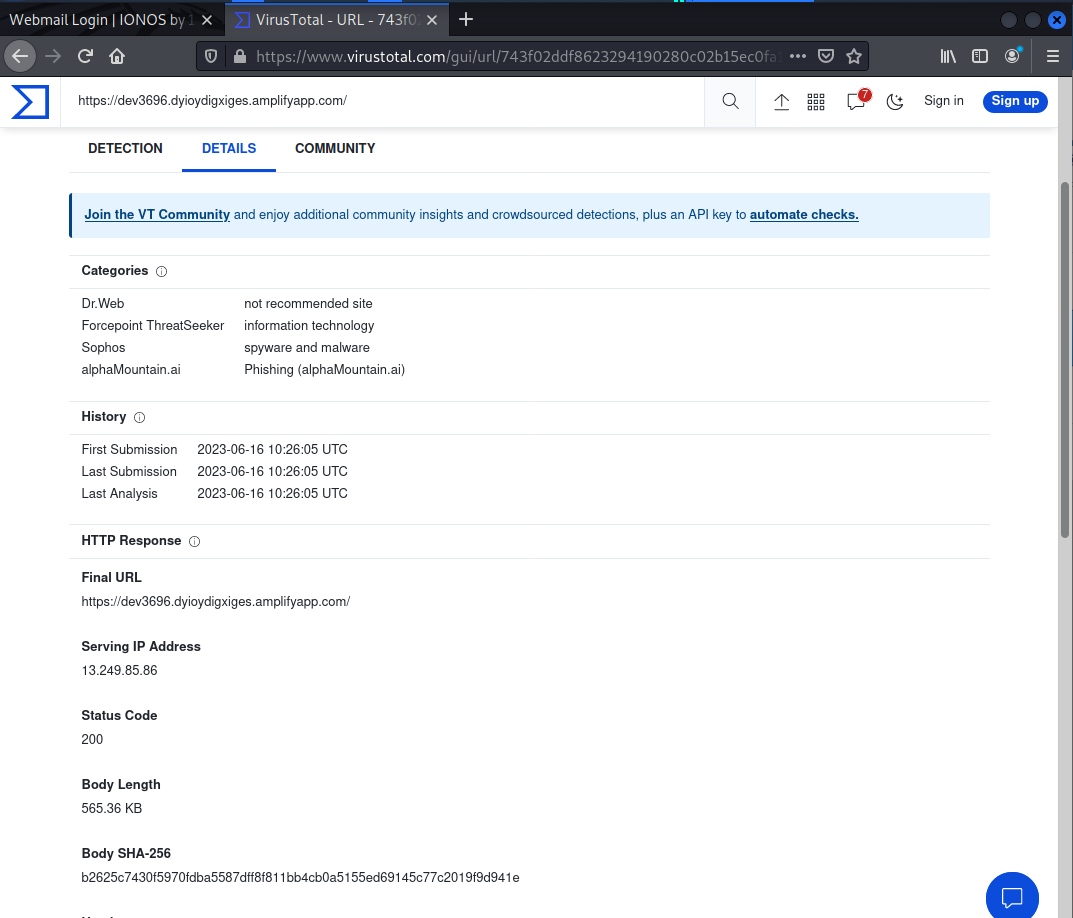
Virustotal identified the link as a phishing link
Other details include the server’s IP address
This exploit is evidently being hosted on Amazon Web Services
Keep your eyes out for exploits such as this one. The logon landing page may show GoDaddy, BlueHost, or other web mail and web hosting companies
Share
JUN








About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com