Catch of the Day: Voice Mail Phish
Chef’s Special: Held Message Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
Voice Mail Phish
This email arrived on June 7. Initially, it looked quite similar to genuine Google Voice email alerts. But the HTML attachment is a popular delivery method for phishers.
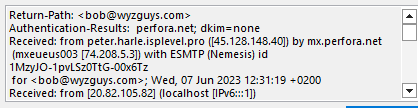
I took a look at the email headers, and it seemed to be something I sent myself, but the server address at 20.82.105.82 is not my email server address. Checking the IP location showed this was a Microsoft server in the Netherlands. At this point I was sure the email was a phish.
Opening t he attachment in Kali took me to a Russian URL
https://xiyrfywfys64762d744138e.inetpr.ru/MYm9iQHd5emd1eXMuY29t
I checked the Cloudflare CAPTCHA. Cloudflare is a nice touch lending some realism to the scam
The next page showed a standard Microsoft365 login screen, so this turned out to be a credential stealing exploit.
A quick trip to Virustotal confirmed that the attachment was used in phishing exploits
This phish email is a simple but most likely effective approach that many email users would accept as legitimate. Make sure you re not one of them. “Whenever there is any doubt, there is no doubt.” – Ronin, Robert de Niro.
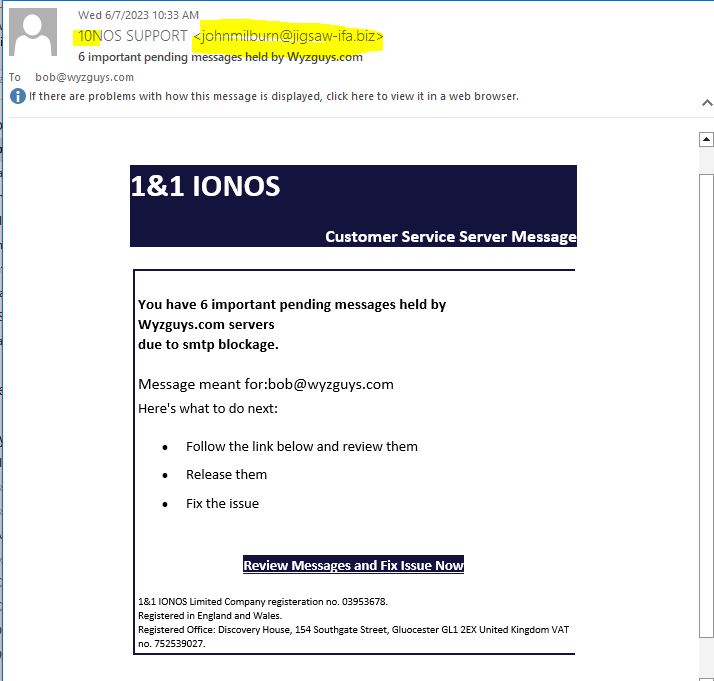
Held Message Phish
I am betting on credential theft, but decide for yourself. Here is another email that I am certain is bogus. First, the return email address is from 10NOS, who is my web and email host. Can you spot the use on the numbers one and zero (10) in steady of the correct spelling of IONOS?
The Review Messages and Fix Issue Now link resolves to https://login.wireless.radio/user/logout?gotoUrl=https://dev4348.d20l5l5brmqo1v.amplifyapp.com/#bob@wyzguys.com and this is redirected to https://dev4348.d20l5l5brmqo1v.amplifyapp.com/#bob@wyzguys.com.
The cookie agreement is in German, which is odd.
As is some of the other content.
Virustotal has not flagged this URL yet, but this email only just arrived in my inbox 2 hours ago. Maybe I’ll check later to see how soon this gets taken down.
I was right about this phishing email is for stealing the logon credentials of IONOS customers. There were early clues that an attentive reader would catch. Not the best work by this phishing crew.
Share
JUN











About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com