 Happy 40th Birthday Star Wars!
Happy 40th Birthday Star Wars!
Phishing Email Alerts
Catch of the Day: Amex Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
American Express Phish
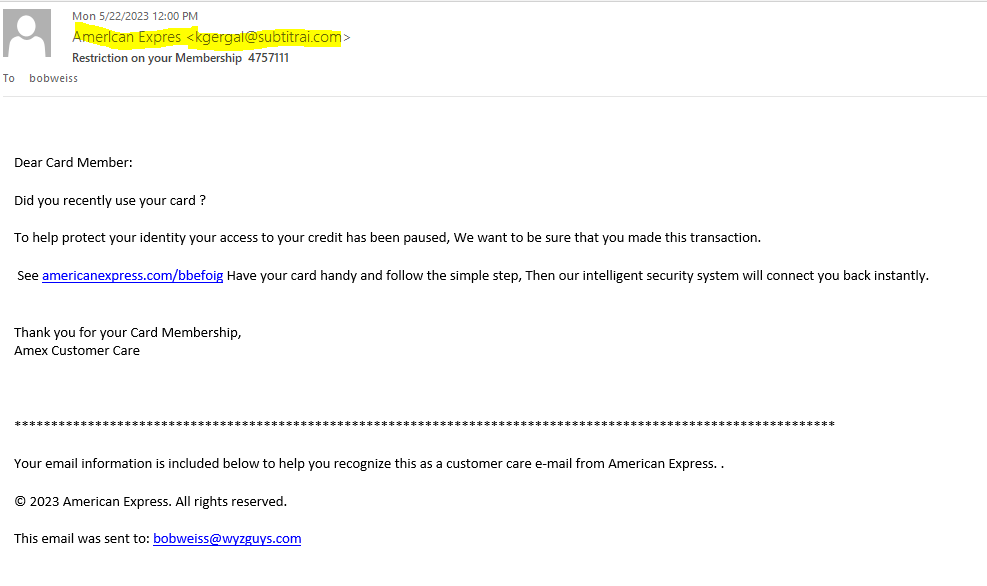
Received this on May 22 at 12:00 pm and got to dissecting this exploit before 12:30, so everything was still there. The sender name is misspelled Amerlcan with an L instead of an I and Expres with only one S’ The actual email account is not from Amex either.
The mail headers show an unusual return address.
Return-Path: <ebeaa0f5.AVwAABfVNM8AAAAAAAAAAO_whmcAAYCtYf0AAAAAACO-vgBka5-A@a2342590.bnc3.mailjet.com>
Authentication-Results: perfora.net; dkim=pass header.i=kgergal@subtitrai.com
Received: from o152.p9.mailjet.com ([87.253.234.152]) by mx.perfora.net
(mxeueus004 [74.208.5.3]) with ESMTPS (Nemesis) id 1MHnhq-1pxIsZ39bq-00Exhc
for <bobweiss@wyzguys.com>; Mon, 22 May 2023 18:59:45 +0200
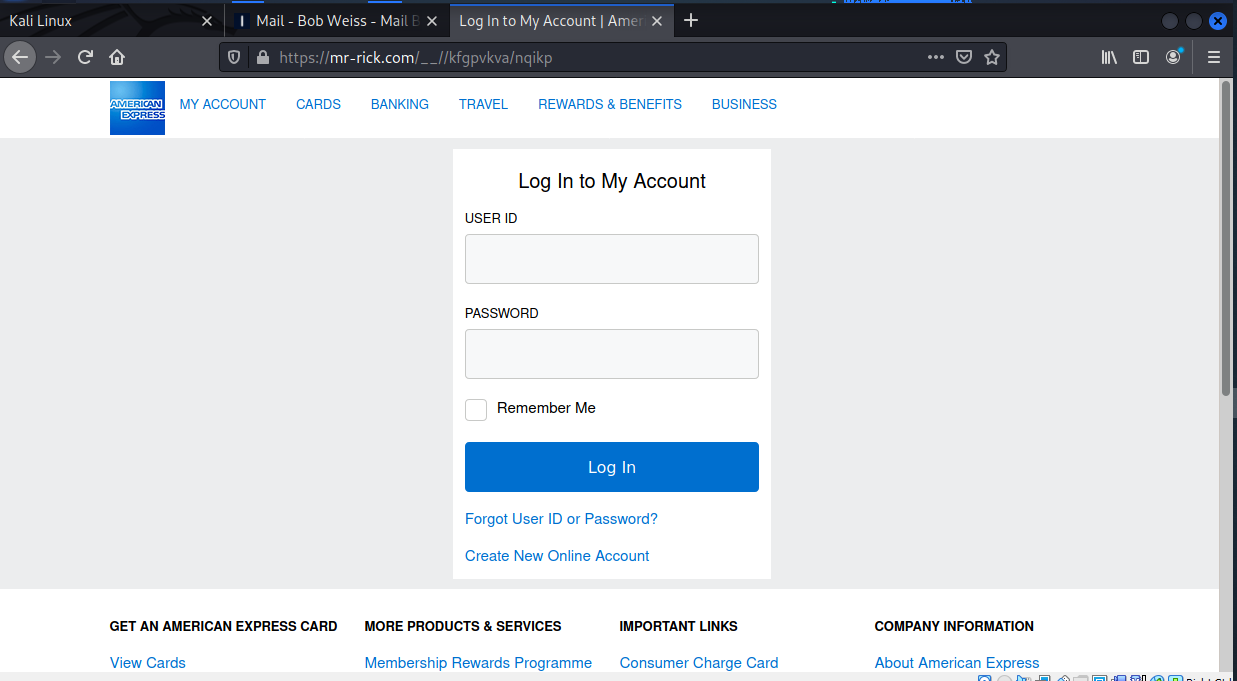
The anchor text americanexpress.com/bbefoig was spoofed by using a tinyURL web address. https://tinyurl.com/buey2d61662s redirects to https://mr-rick.com/__//kfgpvkva/nqikp. This is where the landing page was displayed
Looks like a typical credential stealing exploit. Since it appeared that the mr-rick.com website was possibly being used to host the landing page, I tried to get the home page but it just sent me back to the landing page and displayed this URL in the address bar: https://mr-rick.com/identity/login
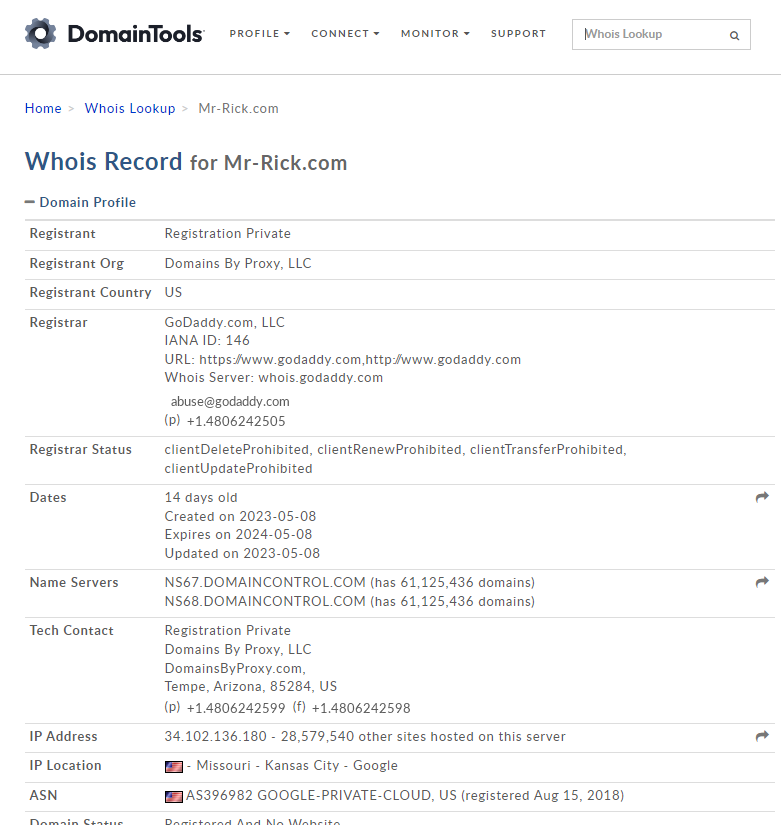
I ran the domain through WHOIS and got the following information. The domain was registered with GoDaddy and is only 14 days old, so this domain was registered for this particular exploit.
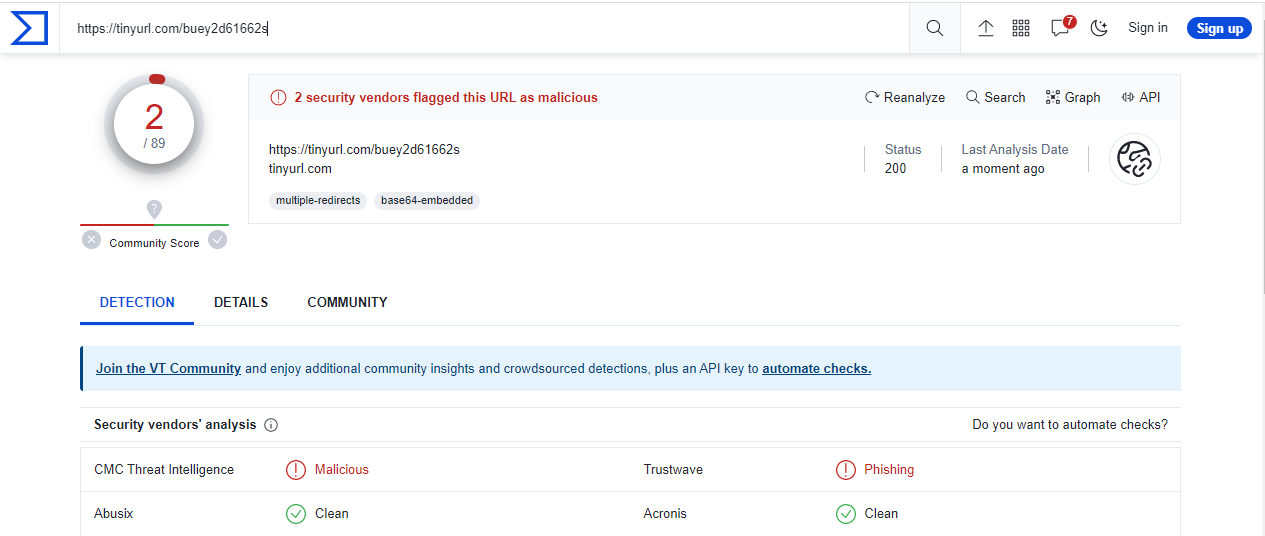
At this point I ran the links through Virustotal. Only 45 minutes into existence, and already one security firm (Trustwave) has the mr-rick.com URL listed as a phishing link.
And the tinyurl.com link as also marked by Trustwave and CMC Threat Intelligence.
So this is how this one came out. In a day or two the entire exploit will have been taken down. We will have to check and let you know how long it lasted.
I checked the next day on May 23 and Firefox on Kali gave this warning. This exploit only lasted hours, its hard to be a pimp.
ShareMAY






About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com