 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: Not a Robot Phish
Chef’s Special: Contract Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
Not a Robot Phish
Got this one Friday May 5 at 2:47 PM. Investigated at 4:54 PM
The sender’s email address was vey long. Long enough to run off the page and conceal the Japanese email domain mwb-sdgw-mts-002c1.ocn.ad.jp. The Confirm! I’m not a Robot button resolved to https://www.sponsorship.com/Marketplace/redir.axd?ciid=Jvp1qL7739&cachename=fU0360&PageGroupId=fU0360V050a3HrD1p6V492495183tPO3Xcmo20383459GLskiaE6322263&url=https%3A%2F%2Frb%2Egy%2Fl9dyw%23V5fU36fU5c3VwcG9ydEB3eXpndXlzLmNvbQ==&GLskiaE6322263tPO3Xcmo20383459a3HrD1p6V492495183 which redirected to https://bfm.mycustomerconnect.com/views/_e-mail.ionos.com_/appsuite.php?2ecec8aa80dff9e47110143250db0f222ecec8aa80dff9e47110143250db0f22&pid=2ecec8aa80dff9e47110143250db0f222ecec8aa80dff9e47110143250db0f22&2ecec8aa80dff9e47110143250db0f222ecec8aa80dff9e47110143250db0f22=2ecec8aa80dff9e47110143250db0f222ecec8aa80dff9e47110143250db0f22&username=c3VwcG9ydEB3eXpndXlzLmNvbQ==&kernel=2ecec8aa80dff9e47110143250db0f22&unix=2ecec8aa80dff9e47110143250db0f22-linux
Here is the phishing email:
The landing page is another typical credential stealing login page. It is easy to mistake this for a legitimate email. Be careful when responding to requests like this one.
Contract Confirmation Phish
Here’s an example of a phish I caught in my anti-phishing nets. There are a lot of interesting screen shots of this exploit that follow.
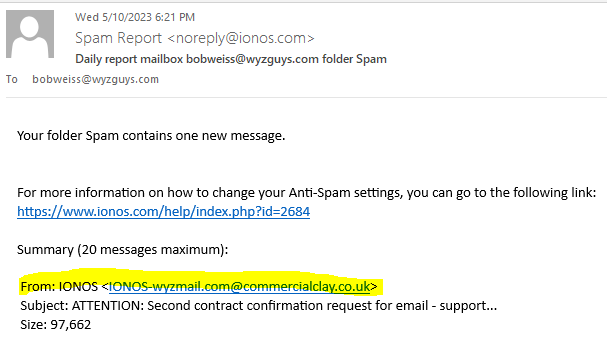
This is the spam report email I receive daily from my email host. The sending email is clearly not expected for email coming from IOMOS
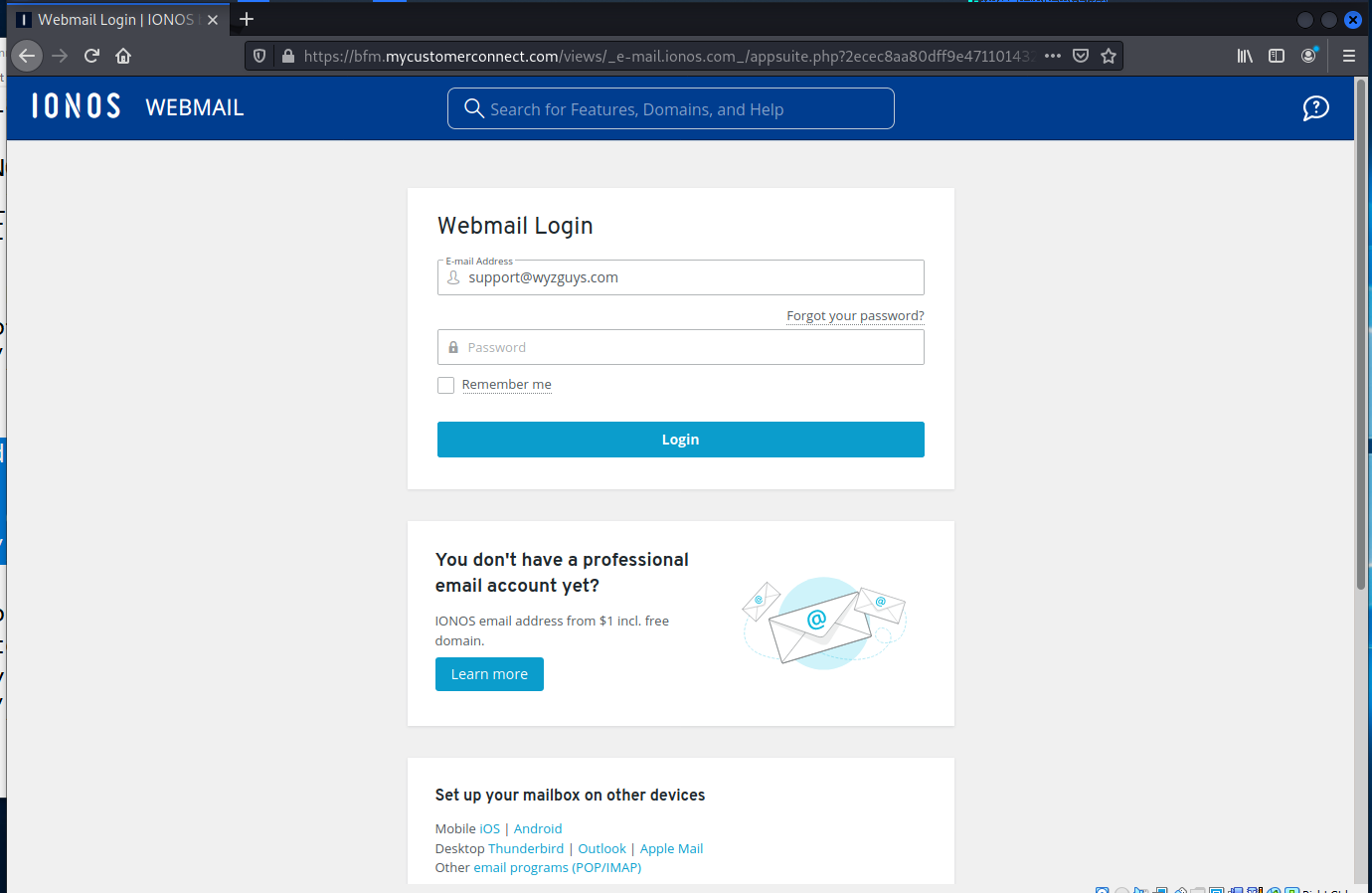
So I logged into my email account using Firefox on Kali Linux
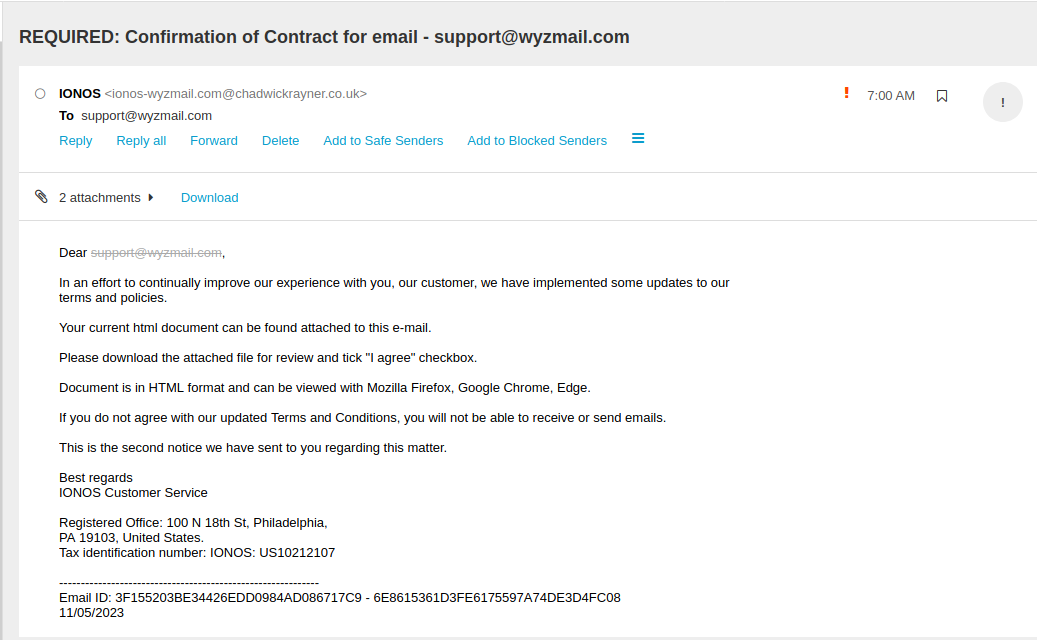
This is a picture of the email itself. There are a couple of attachments to check. The first is just and html file of the email itself
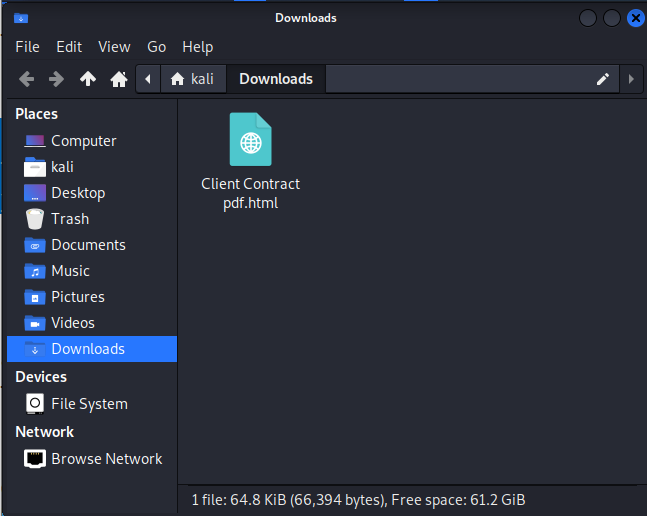
I downloaded the second attachment
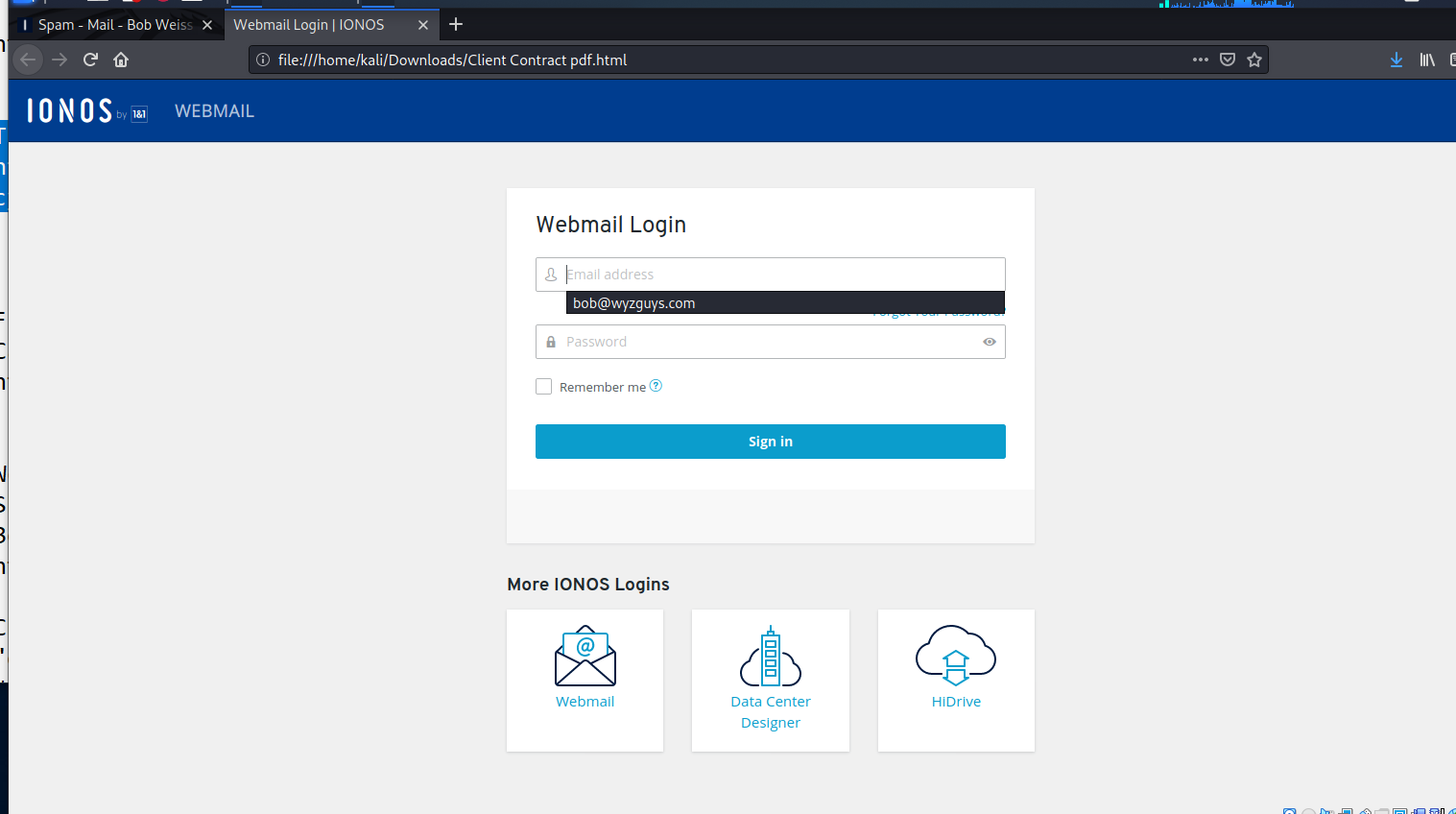
When I opened the attachment I found a self-hosted (see the URL that starts file;//home/kali/Downloads/Client Contract pdf.html) credential stealing login page.
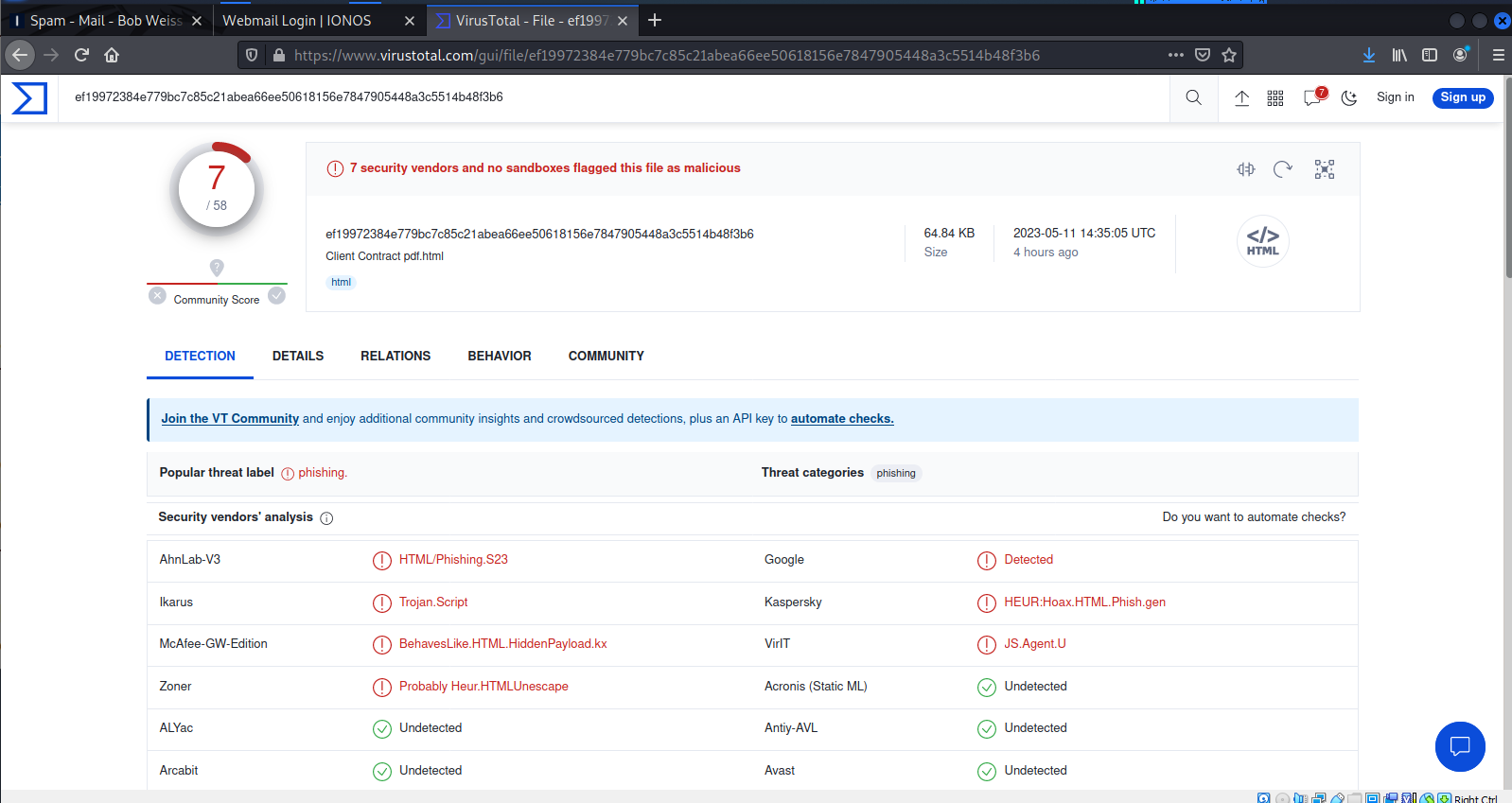
Virustotal identified this as a phishing exploit.
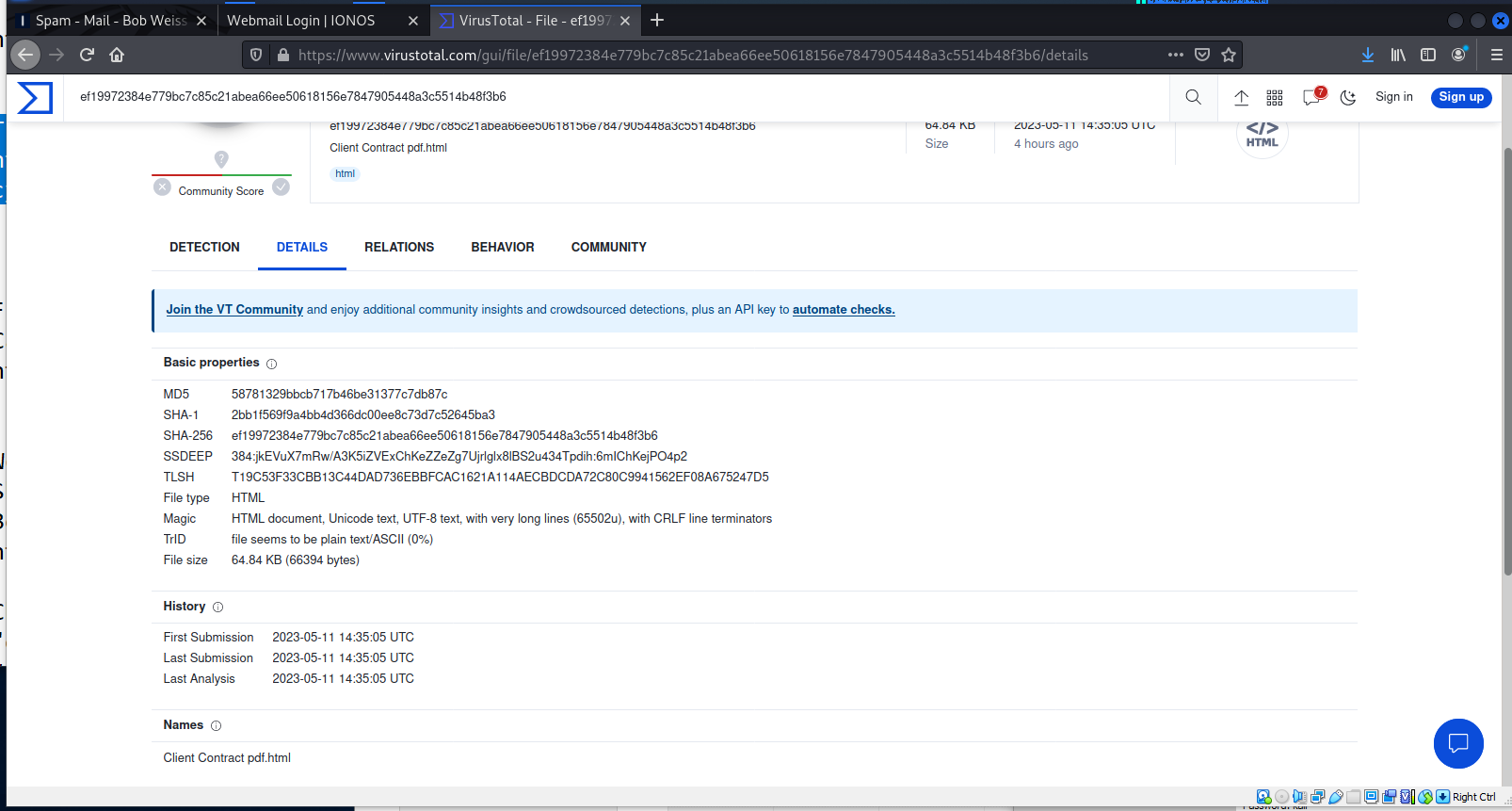
This tab gives us a few extra details including has values and first submission date
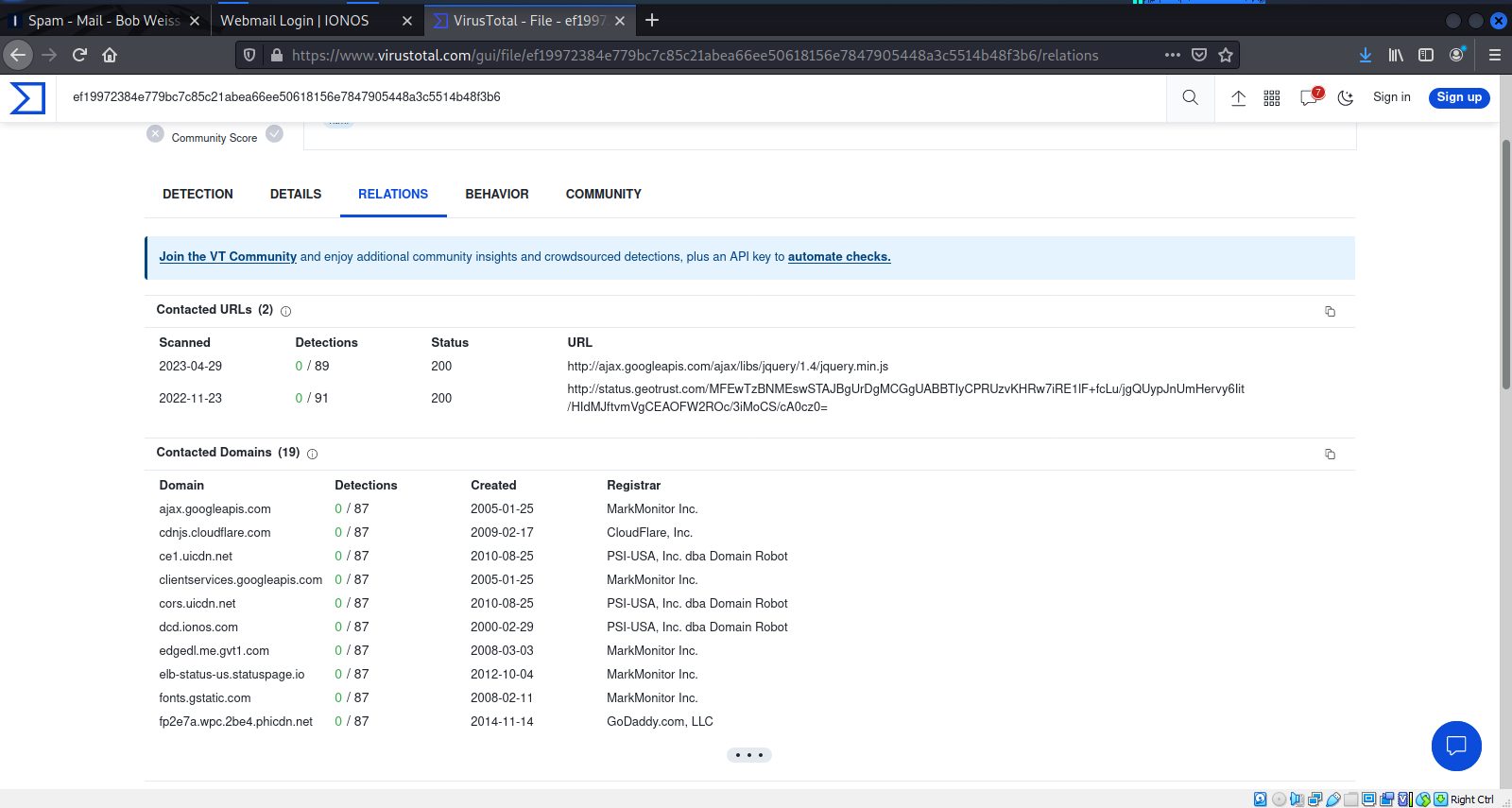
This page provides more details about URLs and domains used in the exploit. These TTPs and IOCs are helpful if you are planning a threat hunting campaign.
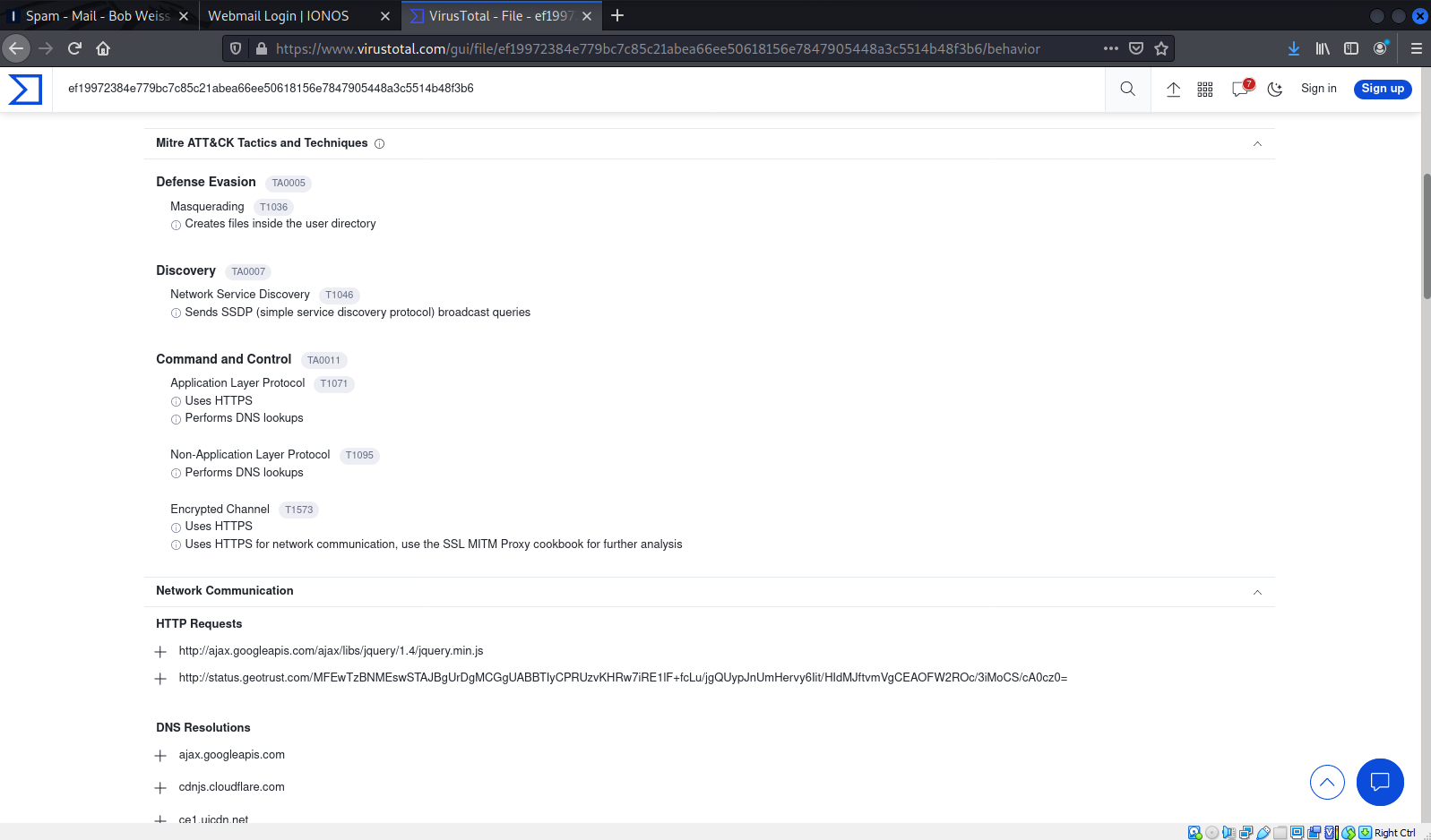
This page details the behaviors exhibited my the malware in MITRE ATT&CK Framework style.
Anyone can engage in this sort of sleuthing. If you are tasked with finding and rooting out this exploit, there is a lot of information here to help you get started.
Share
MAY






About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com