 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: Password Expiry Phish
Chef’s Special: Login Alert Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
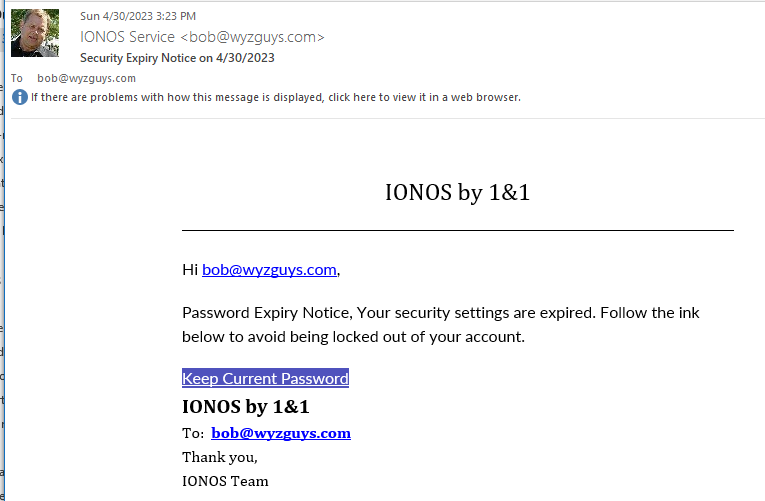
Password Expiry Phish
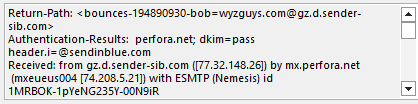
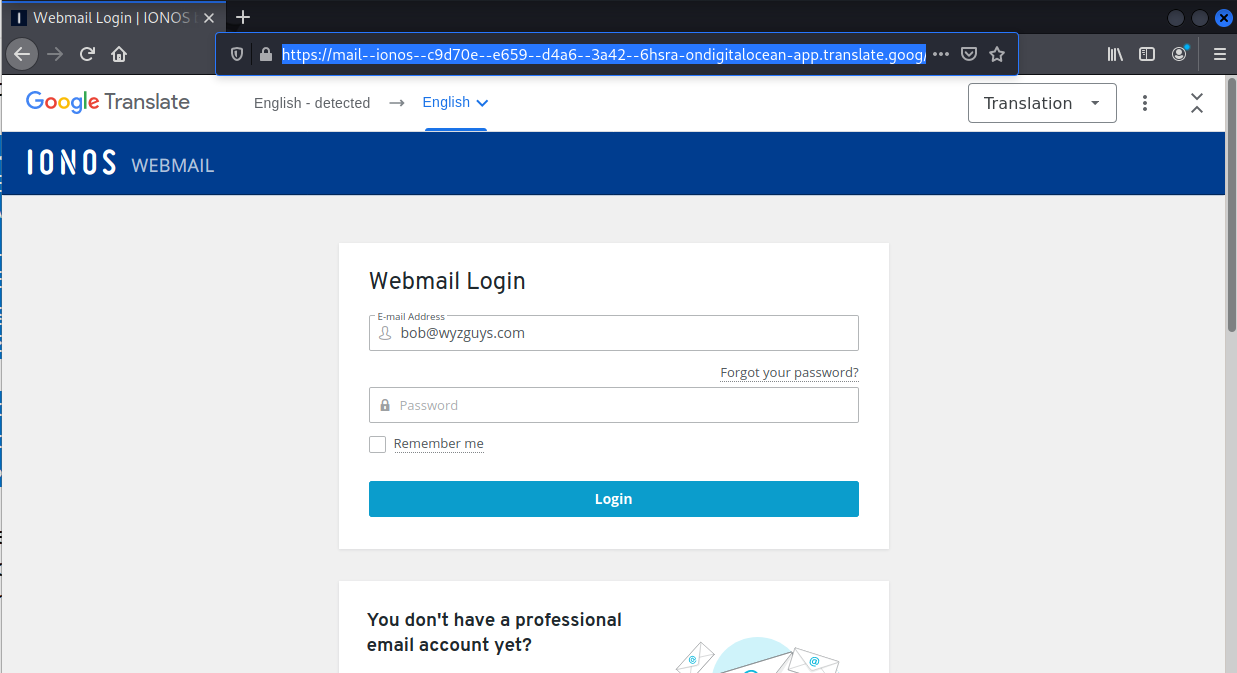
I received this on 2023-04-30. I’ve seen this credential stealer before. The Keep Current Password anchor text and link resolve to https://ffdcibc.r.bh.d.sendibt3.com/tr/cl/IveXle-6W8UBavX8fVLq4pBm5kOZcrazbWk8iJmOUgBItbLFz6TV7ct3u_w0NlN7g975iXz4X5QSGaFWKvp6mEloxRDOzG0Q_z5vZSM0fM0bq58piQFRo8vMv-Z8AdiUkKU2wbrrYyR-kiKcZZIOxTak4MLuWJDmZTd1cWX_bRVpoPCOcgUG7rWSCHWBWmMyK0M0Cq2zBmhZN3tfG7GC6MGBLNjCY1_QCCVy_F1JxMlEo3HHnZGI_Q3VtMzcCu1GElBQK1VCHw8O0YgkfxGcBcDPGrcDYP8BbZ6aFmPH1cgyj_rC8m1CyPEl91hgEFjjvmGpN0u3sxqRJ5ALE1hwsT_8W-1kLjGN2m5prewF7AhQwlE6aE5B_-3HhHrQdHurrYvli8l4Q4_gUEtz6q9YXqPgk228XM5_Z7R1CuSe-kYJ1ho and then is redirected to https://mail–ionos–c9d70e–e659–d4a6–3a42–6hsra-ondigitalocean-app.translate.goog/?_x_tr_sl=auto&_x_tr_tl=en&_x_tr_hl=en&_x_tr_pto=wapp#bob@wyzguys.com.
Here’s the email:
The email headers show that the sender address is spoofed.
The link takes us to this landing page, a typical webmail credential stealing page.
Credential stealing still shows up more frequently than any other type of phishing email, and is the opening move in something like a Business Email Compromise exploit, which is the most profitable exploit according to the latest 2022 FBI Cybercrime Report. Don’t get fooled by this one.
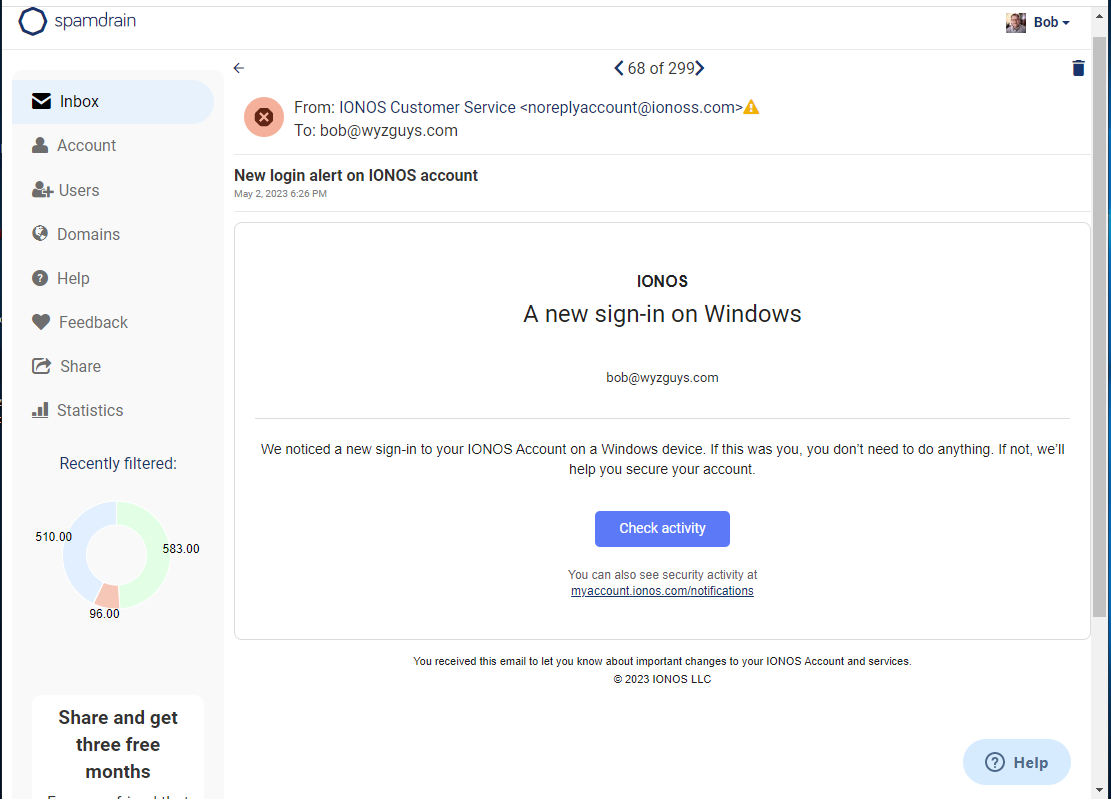
Login Alert Phish
This one was captured in my Spamdrain account. Spamdrain is an email filtering service that I have been using for more than a decade, and I can strongly recommend as a spam blocking and phish blocking service.
The sending domain has an extra s in it (ionoss.com). Nice job of typosquatting.
The Check activity anchor text and link resolve to https://blog.gama.academy/wp-admin/css/colors/blue/ionos/app/index.php?email=bob@wyzguys.com.
Here’s the email as found in Spamdrain. Spamdrain does disable links but also allows users to unblock the links for exploratory purposes
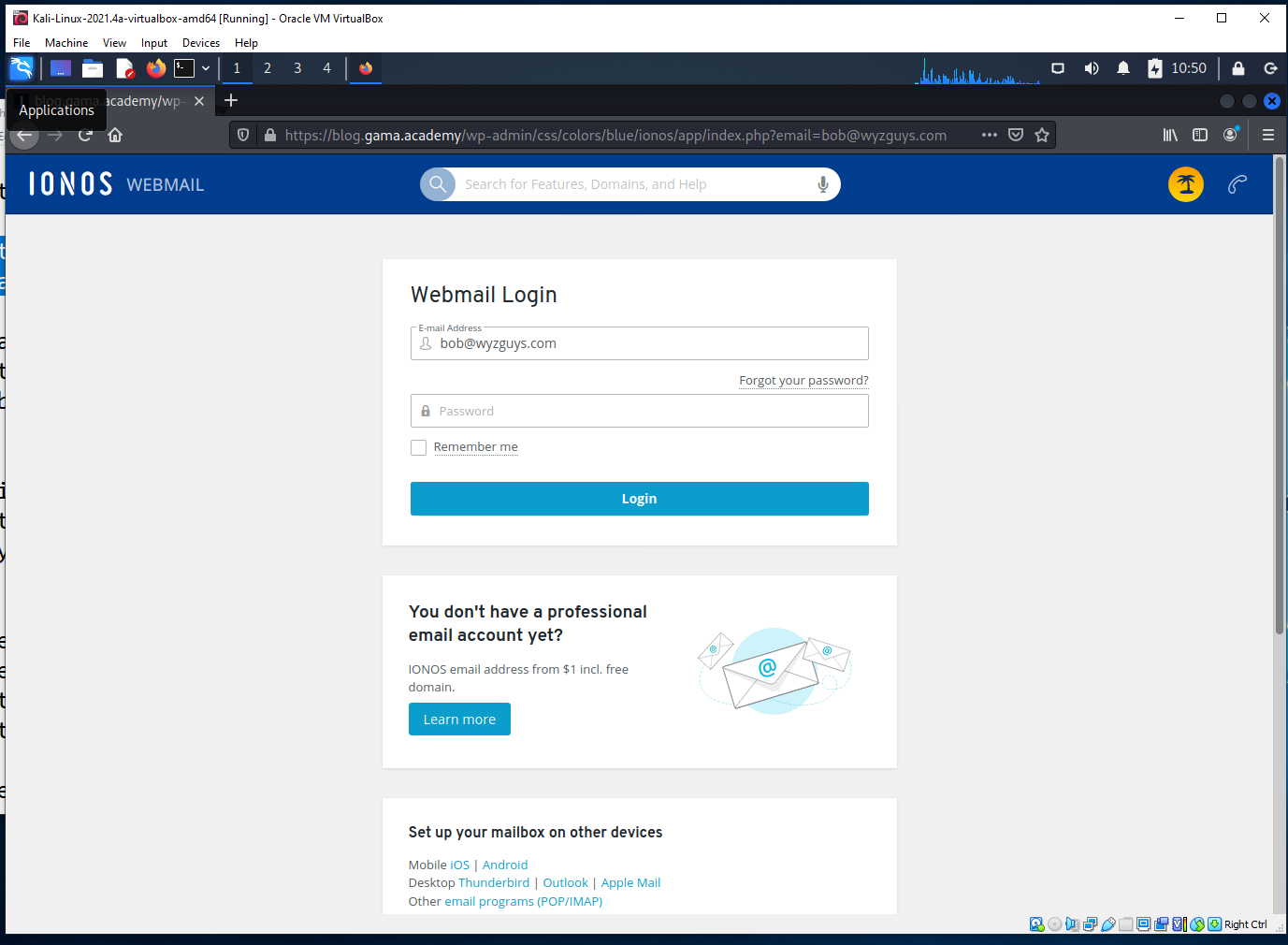
The landing page is below, and again what we find is another credential stealing exploit.
This website was hijacked to host the landing page
This is URL uses percent encoding to represent the :// (%3A=colon, %2F=slash, %2F=slash) for part of the URL since these symbols are actionable.
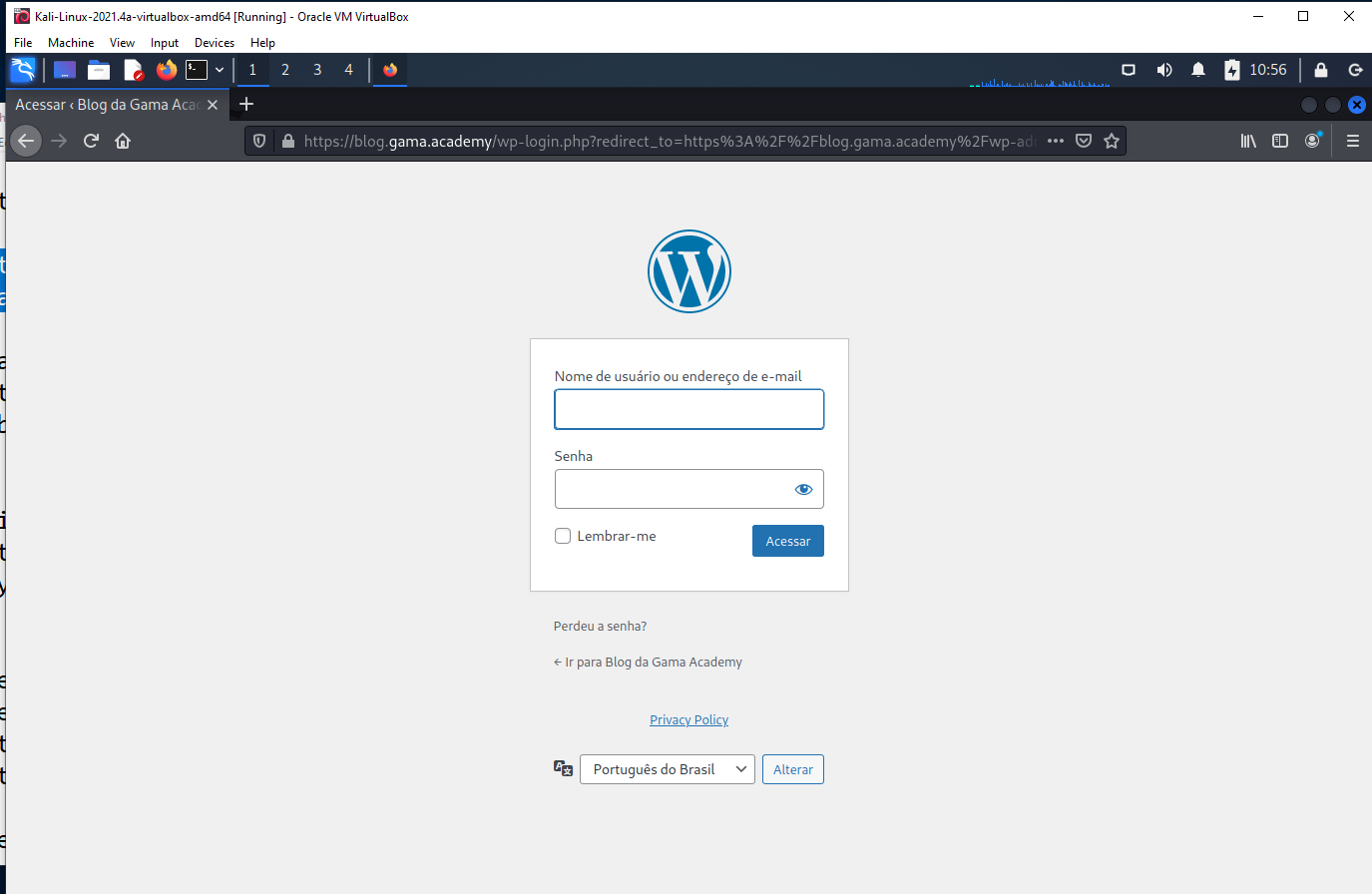
https://blog.gama.academy/wp-login.php?redirect_to=https%3A%2F%2Fblog.gama.academy%2Fwp-admin%2F&reauth=1
The element that makes this exploit a little more danerous is the use of the near-miss domain name ionoss.com. Even a careful reader might miss this and assume the email is legitimate.
Share
MAY




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com