 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: Microsoft Office Phish
Chef’s Special: Lifelock Invoice Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
Microsoft Office Phish
This is a new one on me. As a personal who owns no Apple gear, the email from brett71805@icloud.com was a surprise. But I noticed that the anchor text on the link invited me to Login to Office. I sincerely doubt that Office354 support personnel would be using an iCloud address. The link resolves to https://crist9anoo.ru.com/s/index.php The simple looking email actually is pretty realistic looking, as if it came from my own IT department.
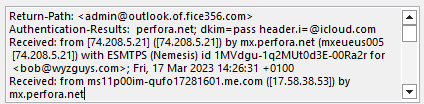
The TO: address is admin@outlook.of.fice356.com. I registered fice356.com back in 2014 as a spoofy domain to use in phishing simulation testing. The use of sub domains outlook.of. makes this a “looks like” domain. I was surprised that the sender used all the the subdomains in my email address.
So an iCloud using tech sending an Office email to my spoofy email address. Intriguing.
The email headers show that this email was sent from ms11p00im-qufo17281601.me.com ([17.58.38.53]). This is an Apple mail server based in the US. Apparently the sender’s email is not spoofed.
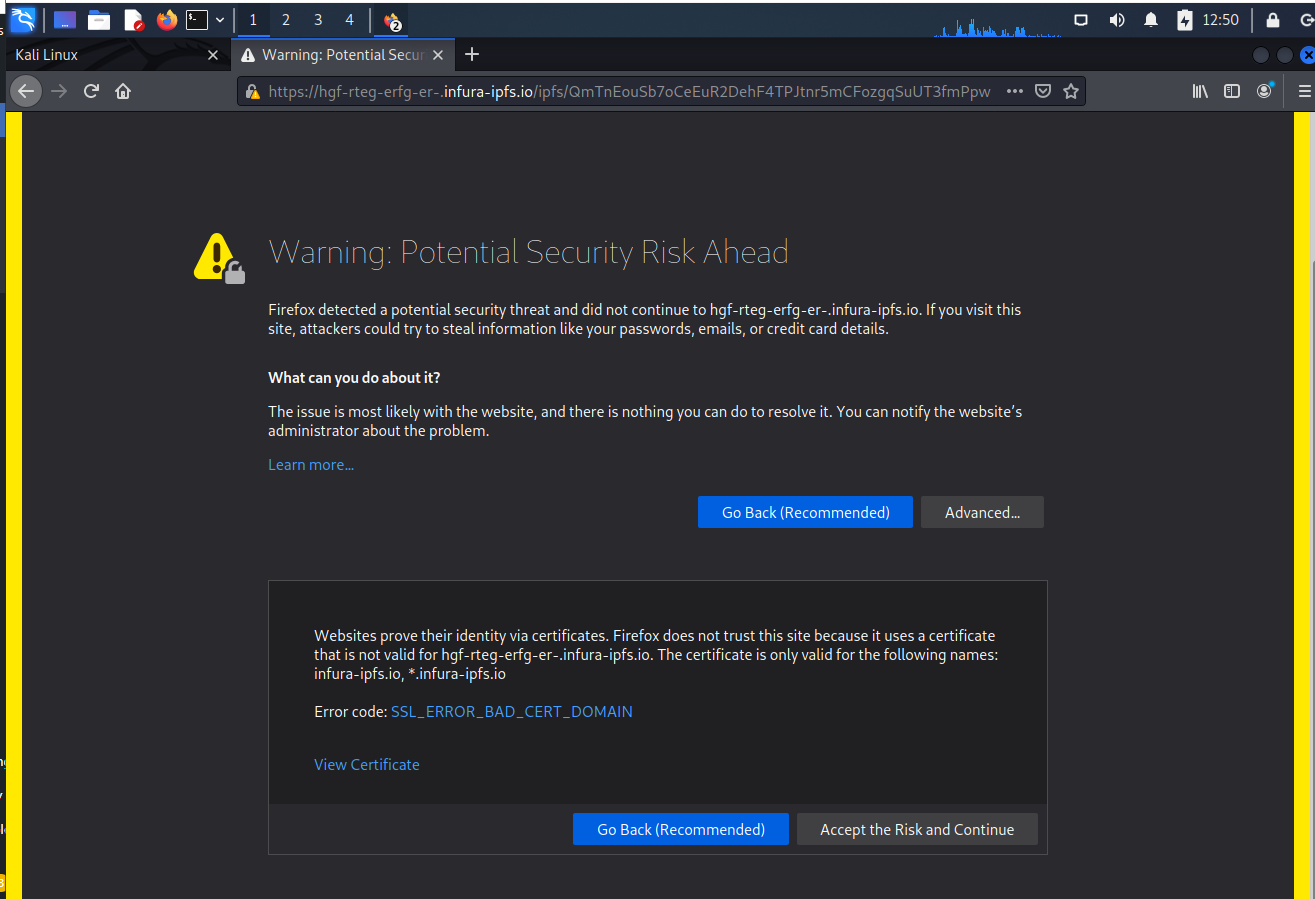
The link was redirected to this address on https://hgf-rteg-erfg-er-.infura-ipfs.io/ipfs/QmTnEouSb7oCeEuR2DehF4TPJtnr5mCFozgqSuUT3fmPpw. The URL looks like it contains a lot of Base64 encoding.. Firefox definitely did not like this link, but being adventurous, and having finally researched an email early enough to find all the components, I decided to accept the risk.
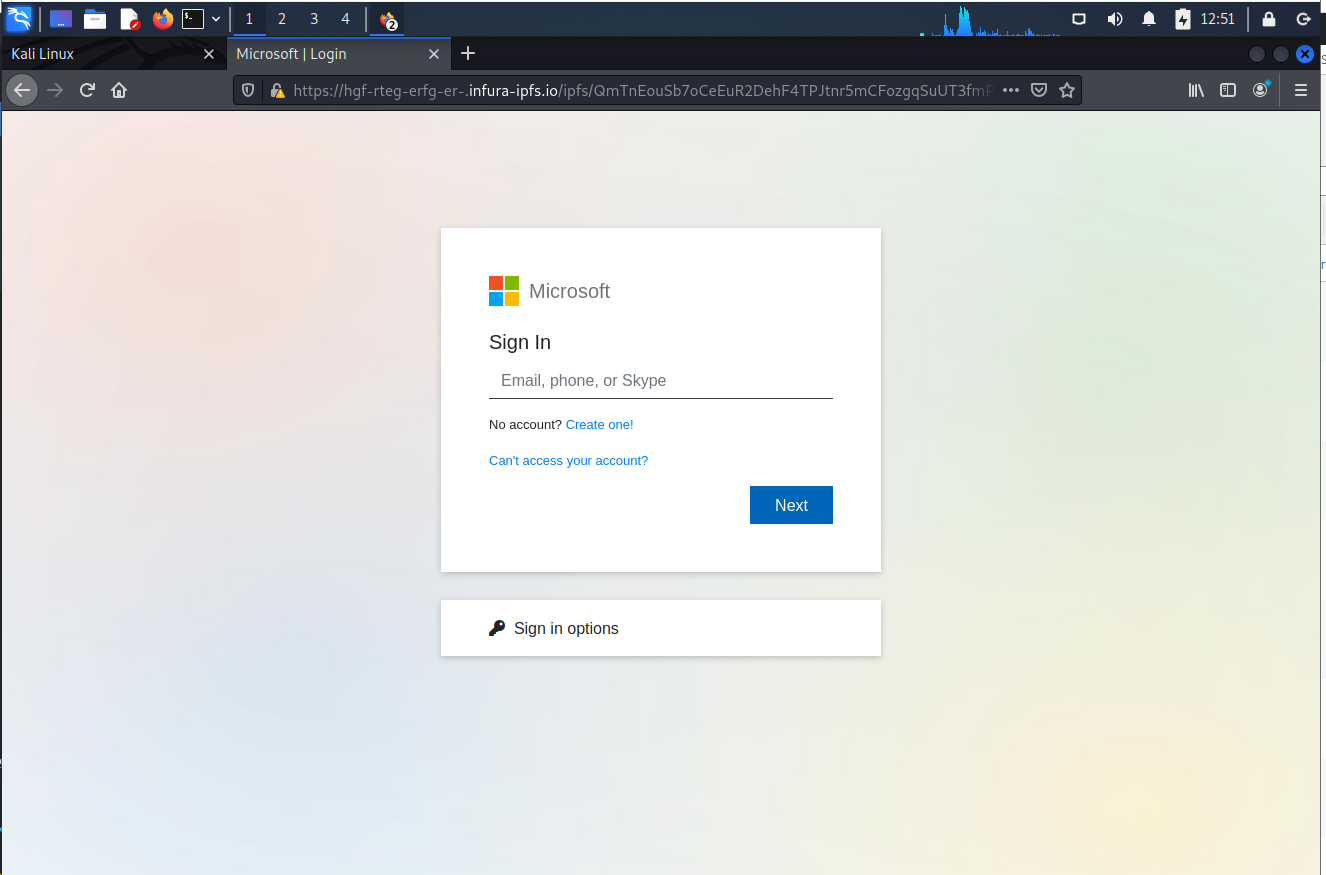
This set of realistic looking login pages came with a nice GIF animated transition page that I was unable to screen capture, but lent to the authenticity of the pages.
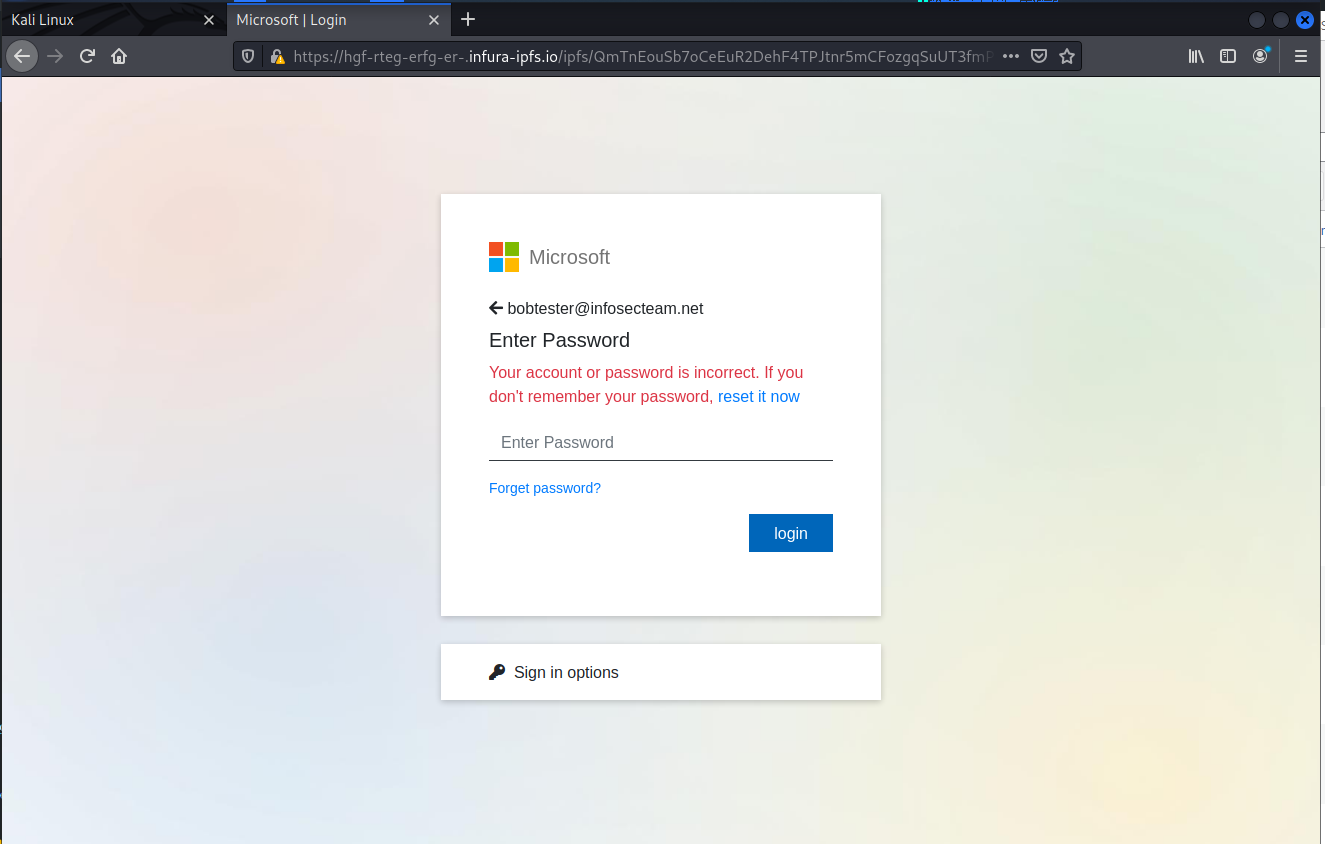
Of course the user and password were “incorrect”. The credentials I provided to the phisher were fake credentials
Another example of a credential stealing exploit targeting people with Microsoft Office 365 accounts.
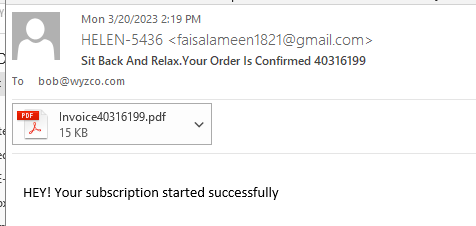
LifeLock Subscription Invoice Phish
This is another invoicing scam designed to get you to call the toll free number on the “invoice” to dispute the charges. Typically the customer service rep is only too happy to help. But first they need your credit card number to reverse the charges. Once you give that up, well…they get to go shopping with your car. Or sell it to some other cyber-thug.
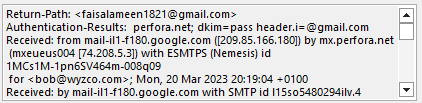
The complete lack of trade dress, logos, other color images makes this a fairly obvious phish. The email is from “Helen” but the email address is from Faisal Ameen and was sent from a Gmail account. A real LifeLock invoice would come from lifelock.com
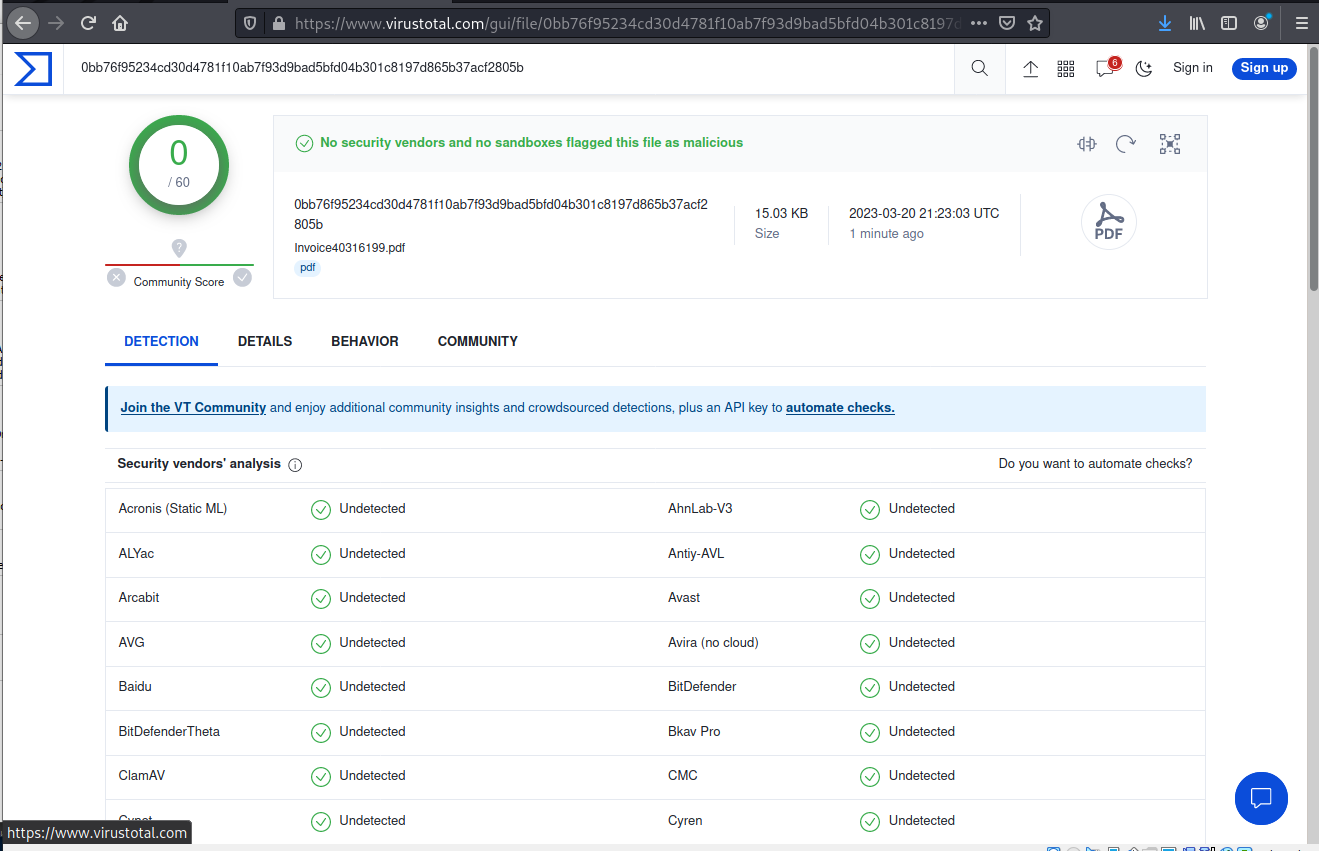
I downloaded the PDF attachment and sent it to VirusTotal for analysis.
VirusTotal did not find any embedded malware
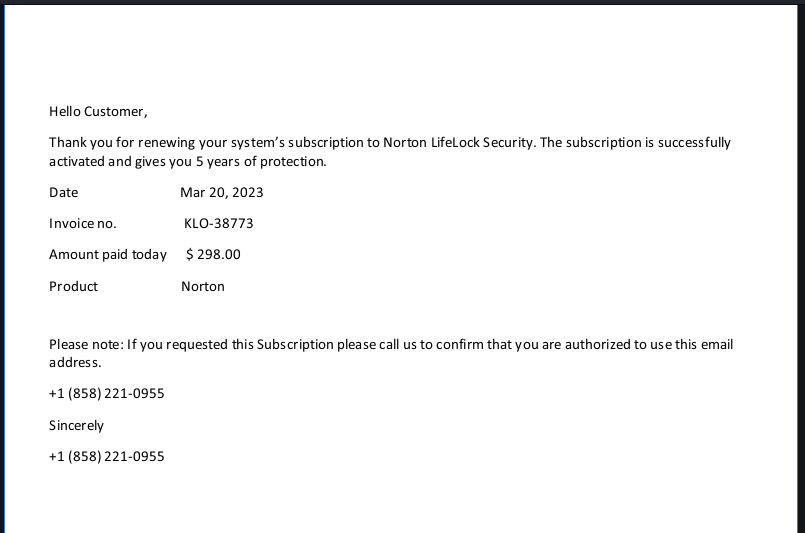
So I opened the PDF attachment and found the “invoice” below. I have to say, five years of coverage for three hundred dollars is a pretty good deal. Too bad this is fake!
The additional ruse “please call us to confirm you are authorized to use this email address” is crazy, but is designed to give the victim another reason to call the “support” team. If I REPLIED to the email, that would be some kind of proof of authority. But a phone call?
Customer service: “Is this really your email address?”
Customer: “Yep.”
CS: Ok, good enough for me!
How does that verify anything?
This email is completely bogus, but simple enough that probably works. Do not call the provided phone number, these people are very skilled at talking you out of your personal information and credit card number.
Massive adversary-in-the-middle phishing campaign bypasses MFA and mimics Microsoft Office
Microsoft has already seen millions of phishing emails sent every day by attackers using this phishing kit. Learn how to protect your business from this AitM campaign.
[Bob says: I think my two examples from this week are both using this exploit kit. Read more on Tech Republic
Share
MAR





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com