 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: Voice Mail Phish
Chef’s Special: IONOS Account Update Phish
Also serving:
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
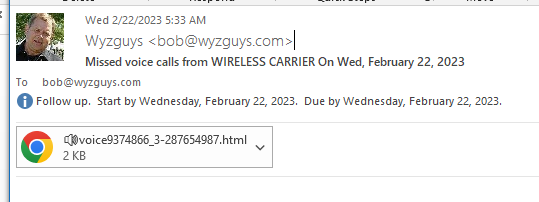
Voice Mail Phish
What appears to be a voice message file attachment is actually an HTML web page with an embedded JavaScript Trojan Horse malware file. Here’s how it starts:
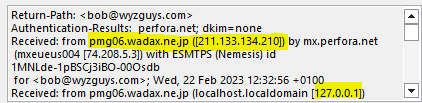
The email headers show this originated from Japan, and is anot an internal voice message alert
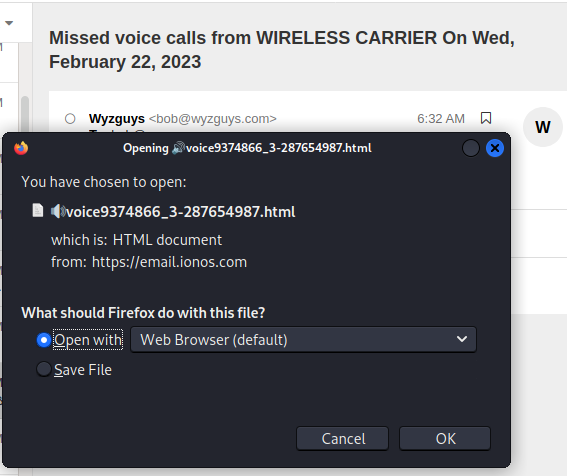
I tried to open the file with Firefox in Kali Linux
But this was blocked by security protections in Firefox. This is starting to happen a little too often, I am going to have to find an alternate browser that has no security.
Not to be deterred, I downloaded the attachment and sent it to VirusTotal. They found a Trojan redirector file embedded in the web page.
Even innocuous emails like this one can be used for a phishing exploit. Be careful out there.
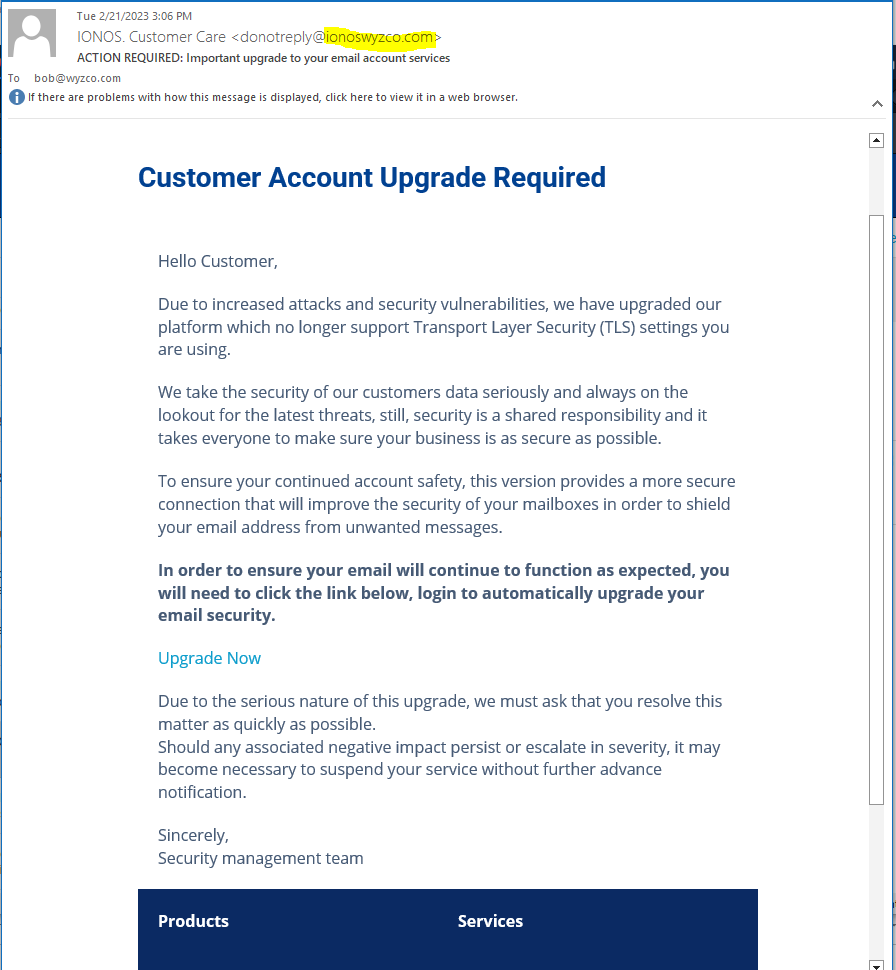
IONOS Account Update Phish
Here is a very realistic looking phishing email. Realistic enough that I failed to notice the sender email address donotreply@ionoswyzco.com was spoofed. A conflation of two legitimate domains I would recognize – ionos.com and wyzco.com.
The story is pretty good, and I was holding this email in my inbox until I could take action with the request. I was lucky I caught this as a phish before I clicked through.
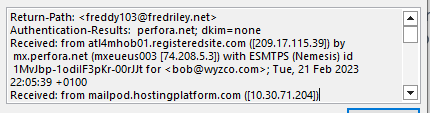
The actual sender of this email is <freddy103@fredriley.net> and the IP address 209.17.115.39 is for Jacksonville Florida. The domain fredriley.net was registered on 2002-03-09. Hard to day if this is hijacked or if Fred Riley is the perpetrator of this phishing scam. I have sent freddy103 an email in an effort to gather more information. Unfortunately, I have not received a response, so maybe Fred Riley is a fake identity.
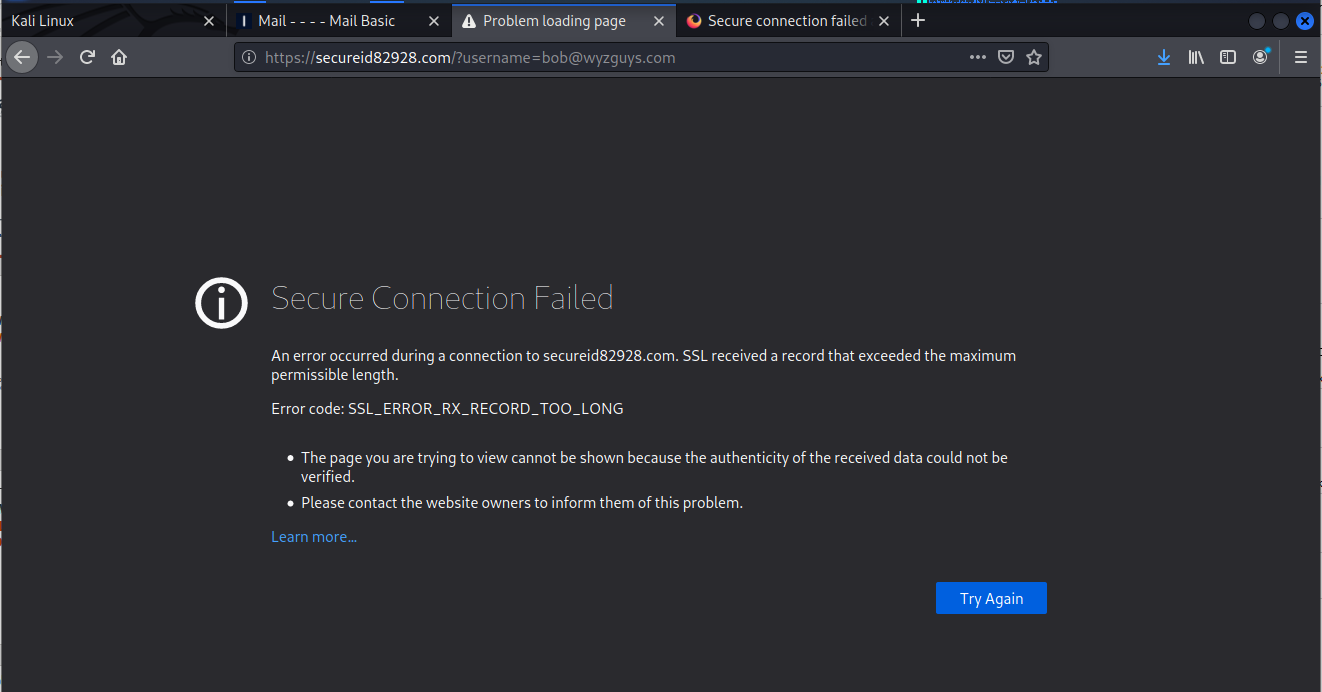
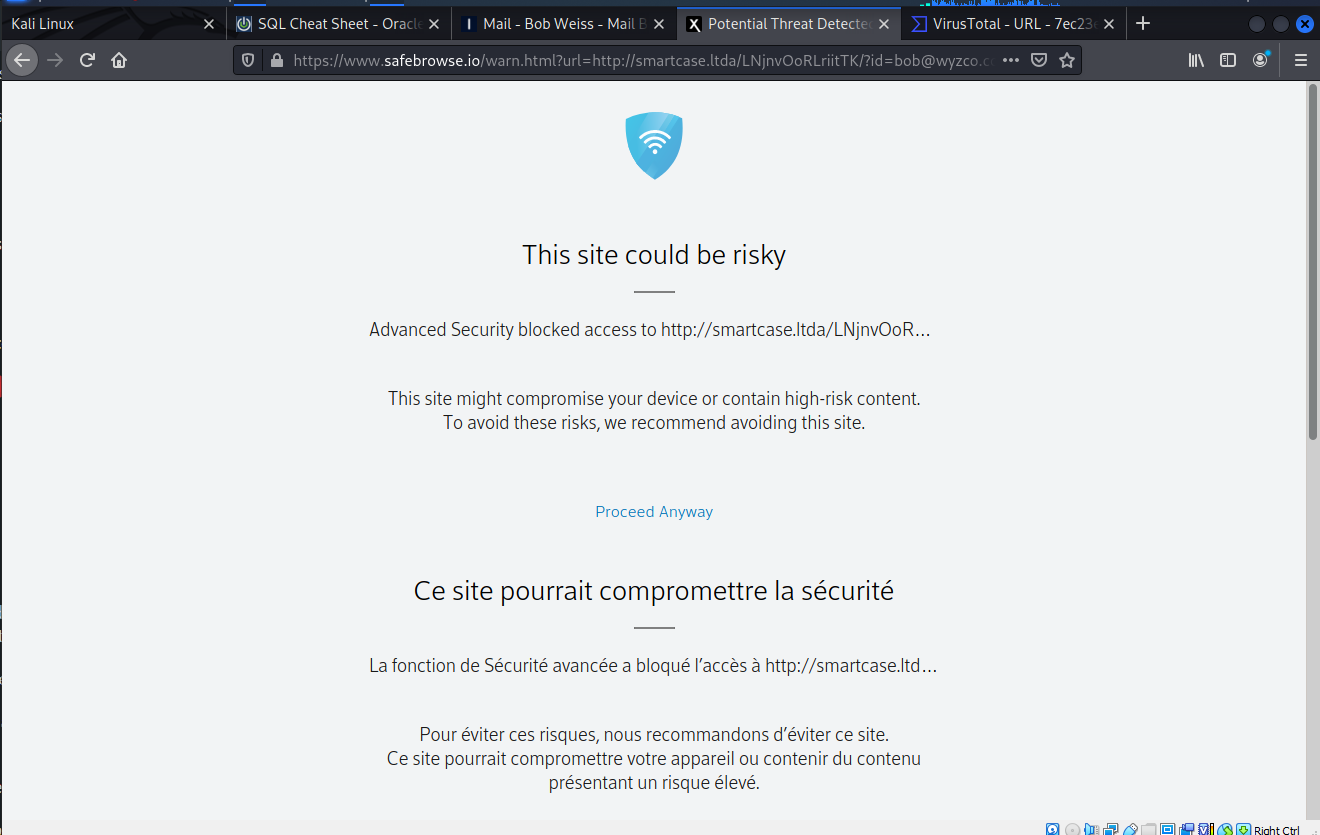
The link Upgrade Now resolved to https://smartcase.ltda/LNjnvOoRLriitTK/?id=bob@wyzco.com. Unfortunately the landing page is unavailable or blocked by the overly aggressive (for my purposes) security of Firefox. Here’s what I did get.
I tried again removing the “s” from “https” and was redirected to a French web address at https://sairaziainteriors.com/dsfghjuk/index.php?id=bob@wyzco.com. This undoubtedly was a hijacked domain. I did get this warning:
So no landing page examples for this exploit. But I sent the link to VirusTotal.com and got this response:
This phishing email was amazingly deception and quite realistic. The fact that I nearly was tricked into clicking the link was kind of scary. I’m supposed to be better than that. The story was so long and detailed that it added to the authenticity and believability of this exploit. All I can say is “be careful out there.”
Share
MAR







About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com