Catch of the Day: Foreign Language Phish
Chef’s Special: Sextortion Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
Foreign Language Phish
Normally, if I get an email in a foreign language, I just delete it. You probably do too. I am fluent in English, of course, and I have some skills in French and Latin, but not much. So when I am looking for the meaning of some bit of foreign language test, I rely on Google Translate.
This email is in German. I decided to tackle this phishing email because there is a remote possibility that it might have been legitimate. Anyway, I was curious enough to go through my usual process.
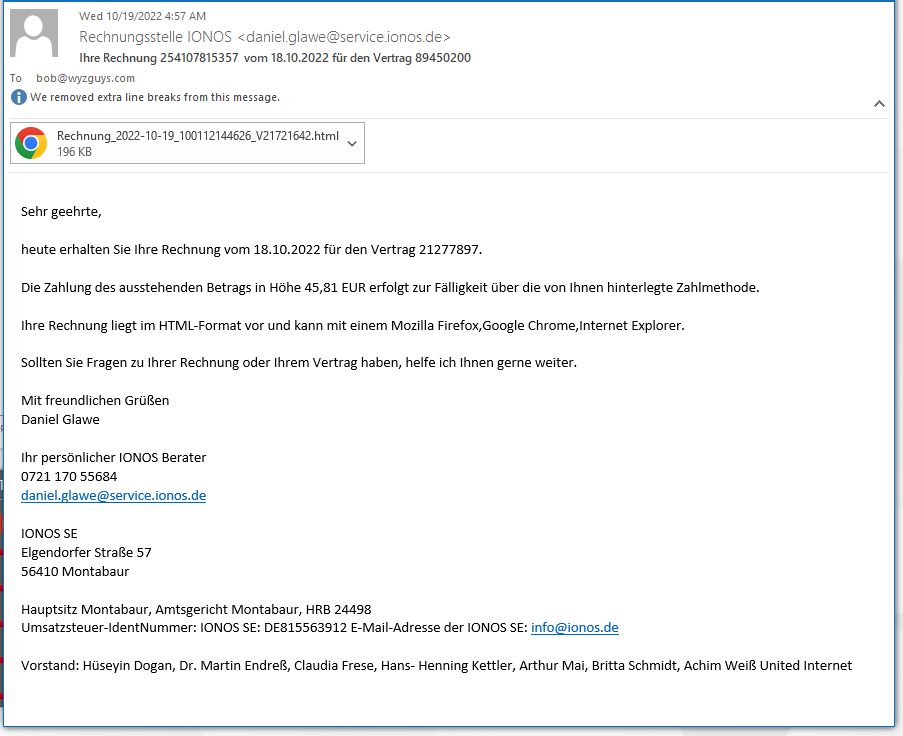
This is supposed to be an email with and invoice attachment. Google Translate did a nice job converting German into English.
The email headers make this look like it very well could be a legitimate email from my web host, which is in fact headquartered in Germany.
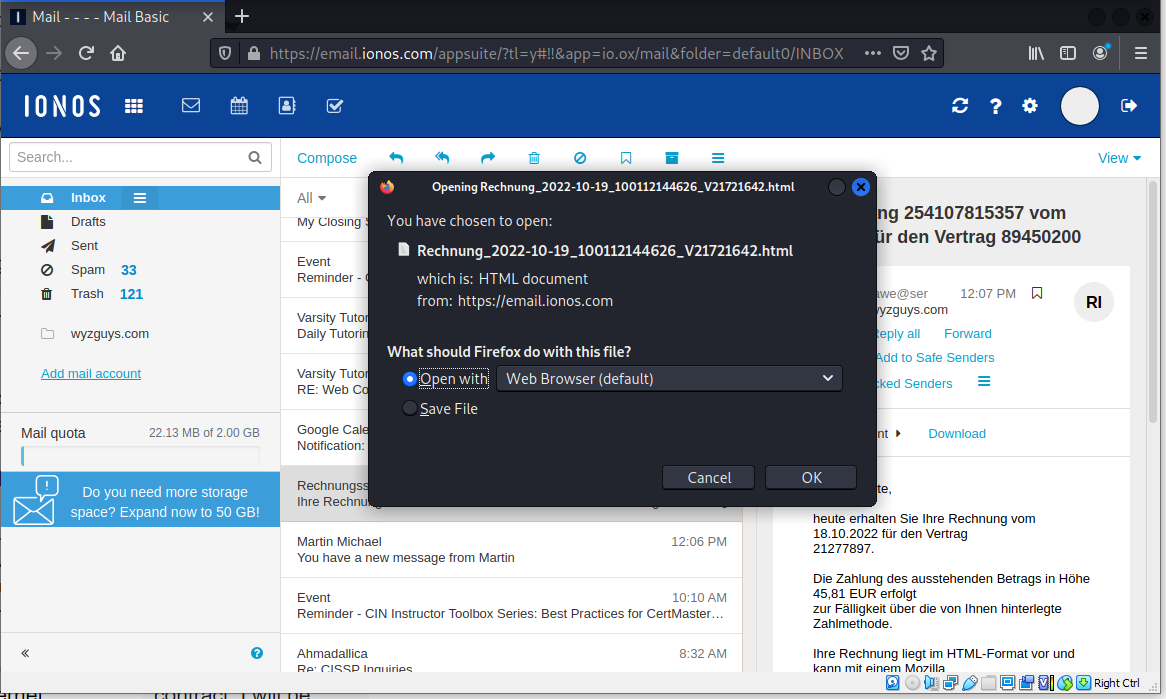
So I tried to open the “invoice” attachment in Kali Linux ( to be on the safe side).
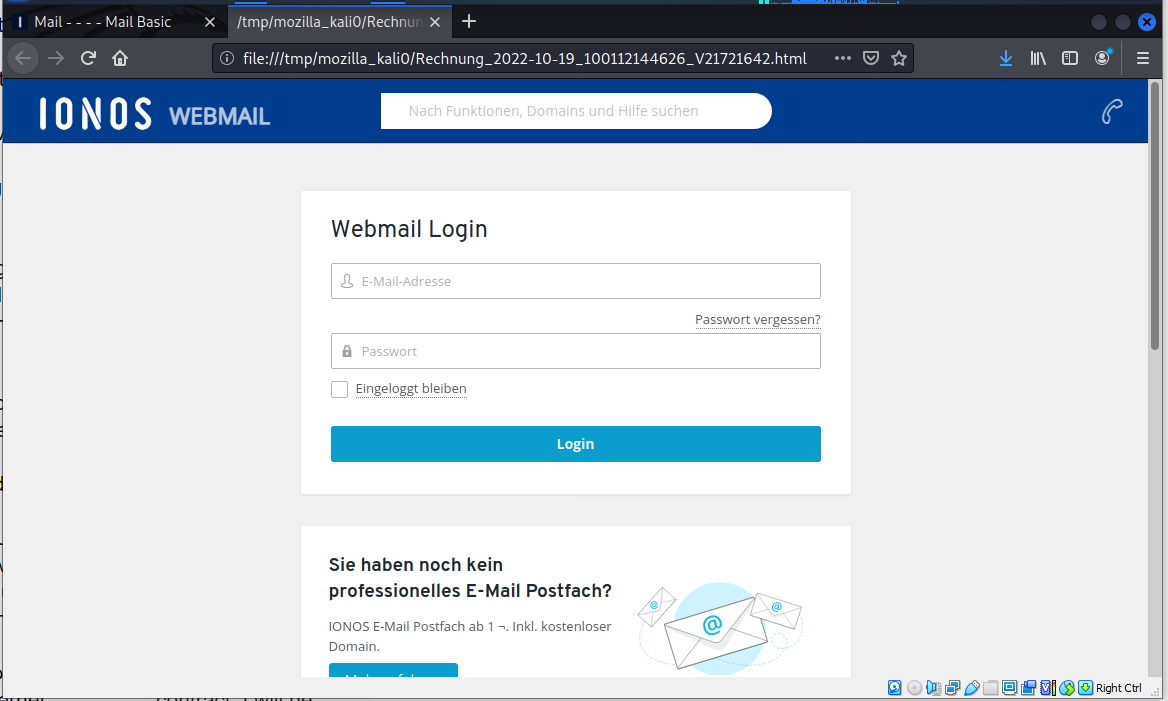
What opened was not an “invoice”, but a self-hosted web page on my local laptop. This looks like a login page, not an invoice, and evidently is just another credential stealing exploit.
I don’t image many of my readers would open an email attachment on a foreign language email, but if you are temped, please don’t.
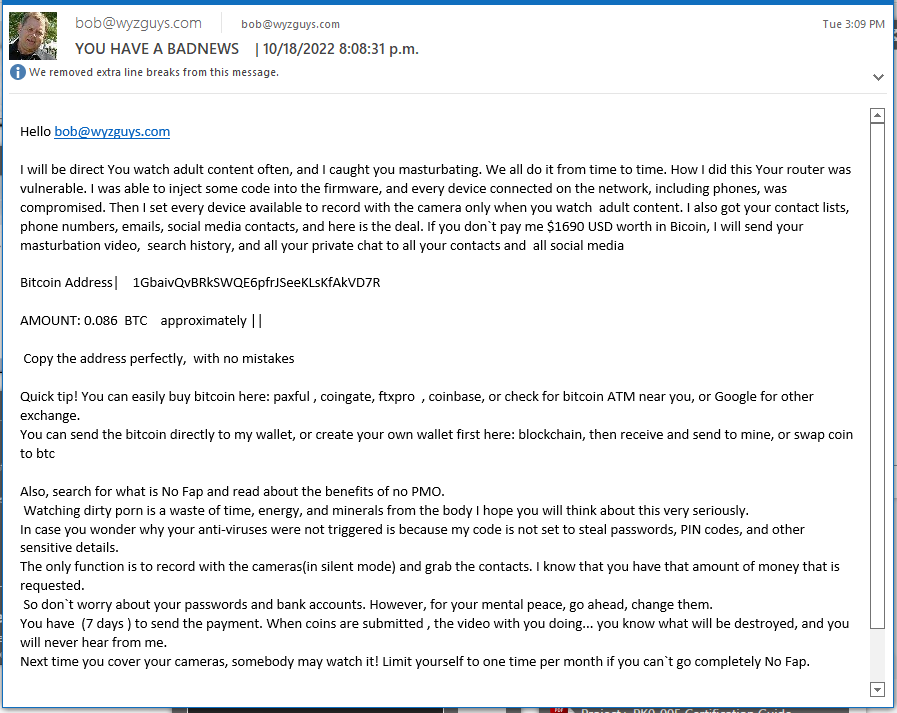
Sextortion Phish
You can safely ignore these blatant attempts at extortion.
Virus Alert Email
My email host blocked a couple like this. Beware the sender if this should turn up in your inbox.
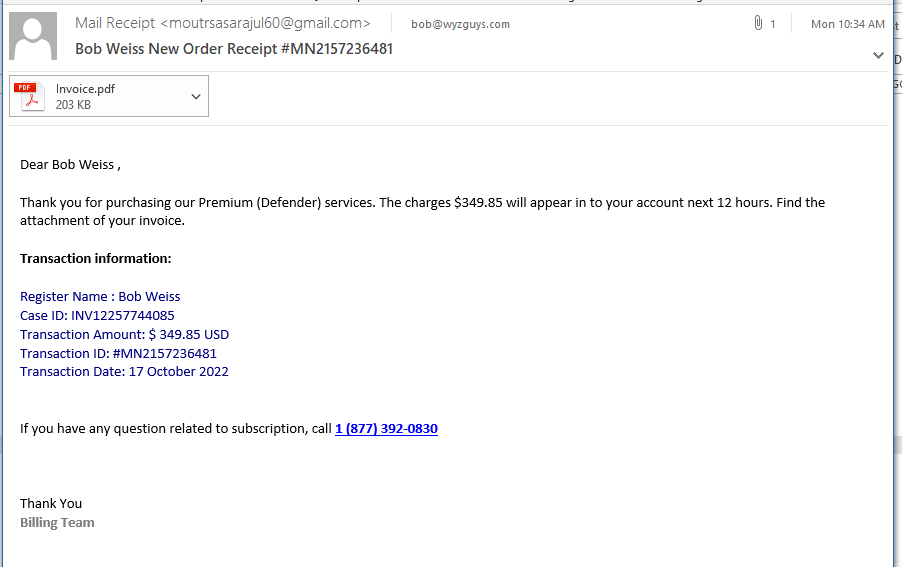
Fake Invoice Phish
Another attempt at tricking you to call the support team at the toll-free number. Just don’t do it. Check your credit and bank accounts for a spurious transaction, but these are FAKE.
Check Point Software is one of the world’s best-known and largest infosec companies. In September 2021 they acquired email security company Avanan and recently they updated Check Point’s initial 2020 research about the email security effectiveness of Microsoft 365 and Defender.
The report is very good and strikes the right tone. They start out by saying: “In general, Microsoft 365 is a very secure service. That is a result of a massive and continuous investment from Microsoft. In fact, it is one of the most secure SaaS services on the market. This report does not indicate otherwise.
What this report does note is the challenge that Microsoft has. As the default security for most organizations, many hackers think of email and Microsoft 365 as their initial points of compromise. A good example of how hackers focus on Microsoft 365 comes in a series of blogs from Microsoft that details the attempts of a state-sponsored group to compromise their services. More…
Share
OCT








About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com