 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: Geek Squad Renewal Phish
Chef’s Special: QuickBooks Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
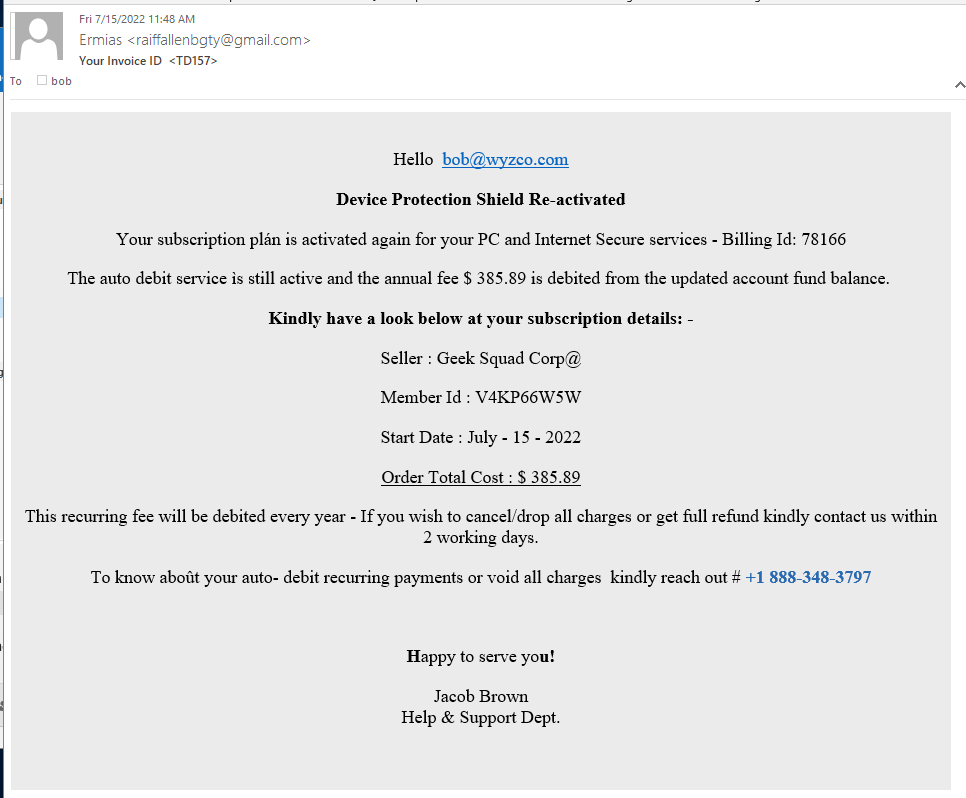
Geek Squad Renewal Phish
This is a little twist on a familiar scam. This appears to be coming from a third-party or internal support team, not directly from the Geek Squad. Again, it is relying on your indignation for the fraudulent charge, and an 800 number to a support team. See tomorrow’s article in Weekend Update on telephone scam centers, and how these sweatshops take advantage of their employees too.
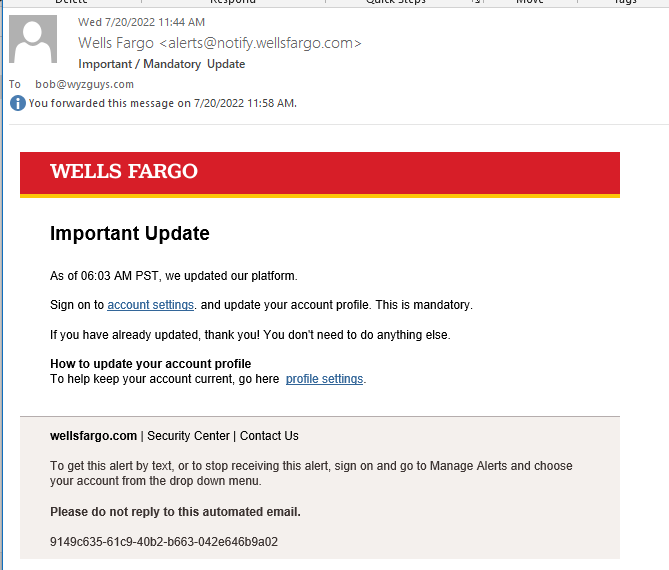
New Wells Fargo Phish
Wells Fargo is a popular account for cybercriminals to go after. Here is a new one that is after more information than just your logon credentials.
The first thing to notice is the sender address, which is spoofed to a legitimate Wells Fargo email address alerts.wellsfargo.com.
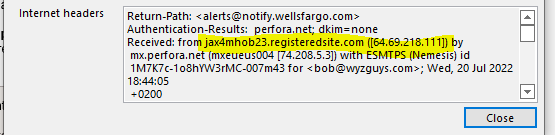
The email headers showed that the spoofed sender really came from a web server at 64.69.218.111 which is in Jacksonville, FL, the Web.com Group. This shows as a Network Solutions site
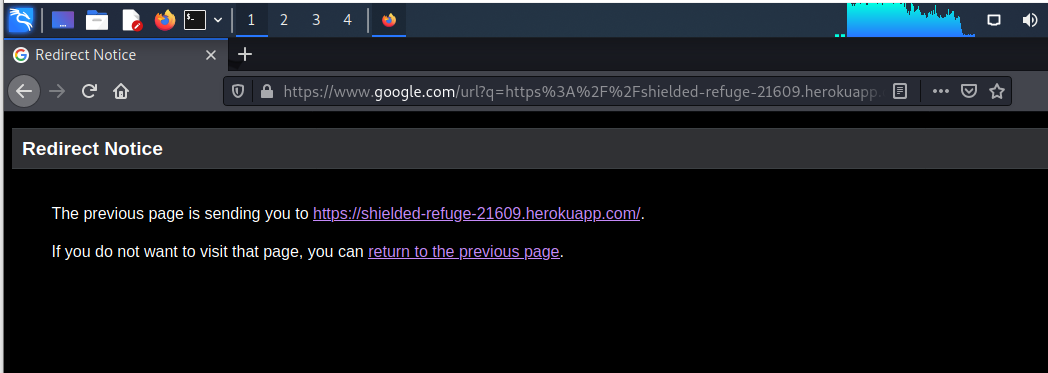
The links resolved to a google.com address to comfort any eagle-eyed potential victims:
https://www.google.com/url?q=https%3A%2F%2Fshielded-refuge-21609.herokuapp.com%2F&sa=D&sntz=1&usg=AOvVaw2ox_r_91Jxw-_nunxbv2fZ
and was redirected to https://shielded-refuge-21609.herokuapp.com/
I ignored the redirection warning
I entered a fake user ID and password which would complete a logon credential stealing scam. But wait, there’s more!
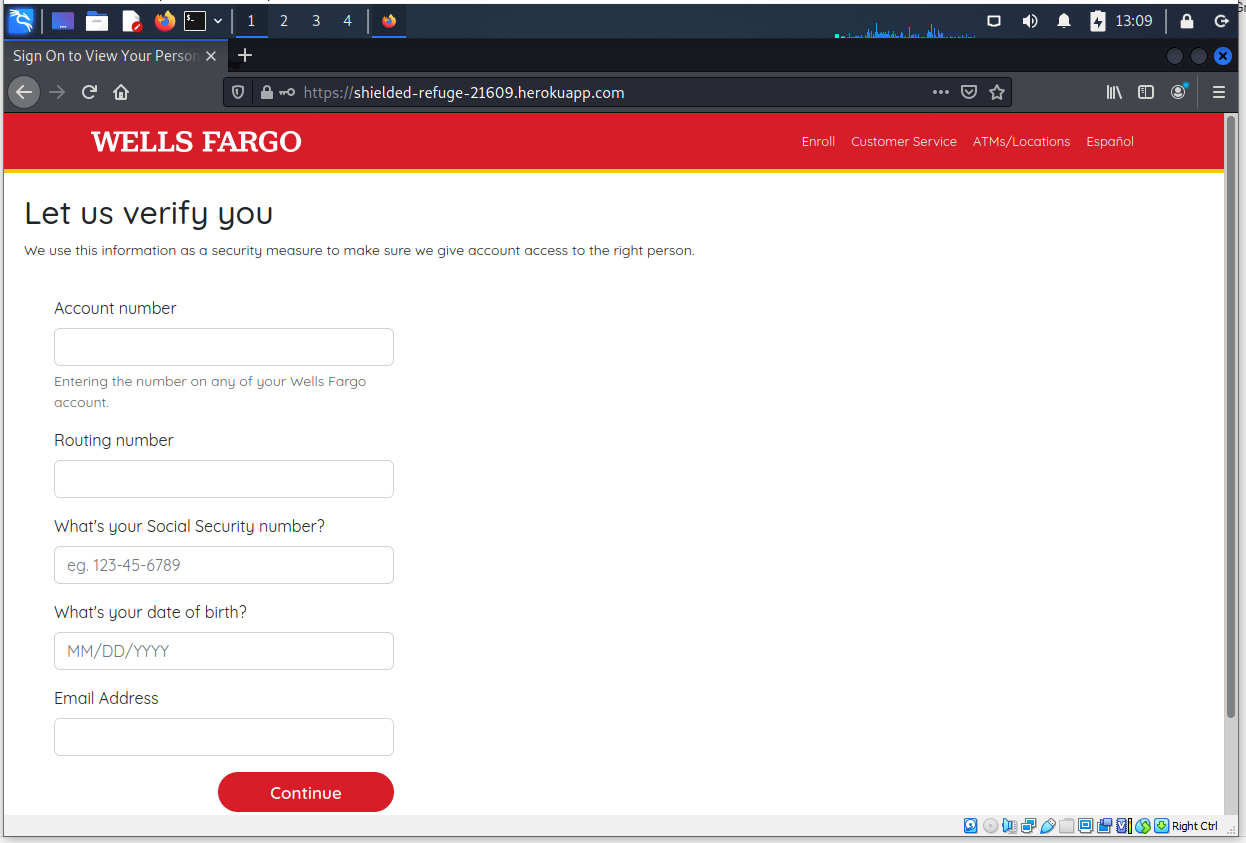
This page is designed to separate you from your account number and bank routing information. I would imaging that Wells Fargo already knows their own bank routing number?
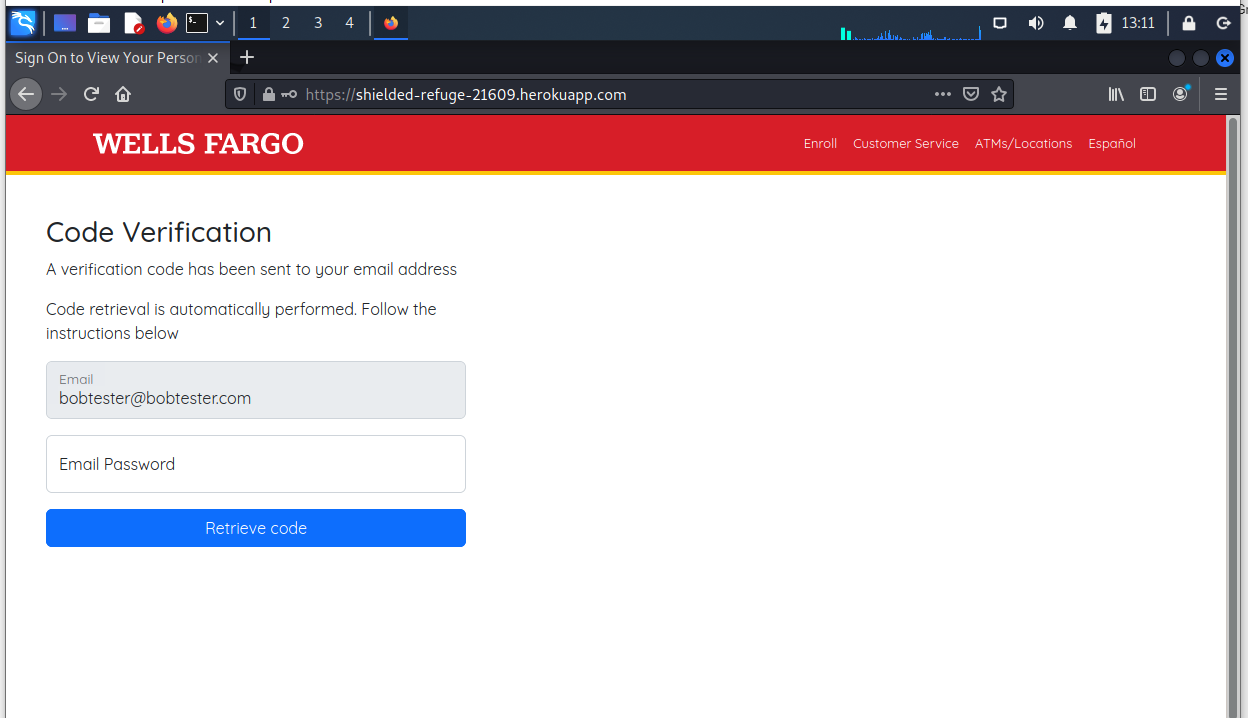
This page is designed to collect your email address and password as well. Another popular target that opens the door to email account hijacking, and many other exploits
My fake email account and password pulled an error screen. Game over, but the attacker collected a lot of useful personal and financial information.
New Phishing Attacks Shame, Scare Victims into Surrendering Twitter, Discord Credentials
A new wave of social media phishing attacks are now using scare tactics to lure victims into sending their logins.
First, a Twitter phishing attack was reported earlier last week. Threat actors would send direct messages to the victims, flagging the account for use of hate speech. They would then be redirected to a fake Twitter Help Center to input their login credentials.
Then, a Discord phishing campaign was discovered by sending user a message from friends and/or strangers accusing the user of sending explicit photos on a server. The message also included a link, and if clicked would then lead to a QR code. This resulted in the account being taken over by the cybercriminals.
Social media have always been used for successful phishing attacks, using social engineering to manipulate victims to disclose confidential logins. And if successful, social media attacks can open the flood gates to the company network. More…
QuickBooks Phishing Scam Is Back and Sails Through Your Filters
Scammers are continuing to abuse the QuickBooks tax accounting software to send phishing scams, according to Roger Kay at INKY.
“All versions of QuickBooks have the ability to send invoices, and in this case, the bad guys turned this capability into an attack vector for a low-tech phone scam,” Kay writes. “In the past year, phone scams have been on the rise as phishers respond to the increasing sophistication of anti-phishing defenses: defenders go high, phishers go low. A simple mechanism is a phone number that the phishers want the mark to call. When they do, an operative will try to extract valuable information from them.”
The messages are impersonating Amazon, Apple, Best Buy, PayPal, Norton and McAfee. Users are instructed to call a phone number to cancel a purchase they didn’t make.
“INKY began to see instances of this particular attack in December 2021,” Kay says. “They accelerated significantly in March 2022. Although we have detected 2,272 to date, that number is surely an undercount. The exact count is difficult to determine since the subtle scam emails and legitimate QuickBooks notifications all originate from the real QuickBooks notification site: quickbooks[@]notification.intuit[.]com.”
Since QuickBooks is a legitimate software product, the phishing messages were able to bypass security filters. “These attacks were highly effective at evading detection because they were identical to non-fraudulent QuickBooks notifications, even when examining the emails’ raw HTML files closely,” Kay says.
“All notifications originated from authentic Intuit IP addresses, passed email authentication (SPF and DKIM) tests for intuit[.]com, and only contained high-reputation intuit[.]com URLs.”
Kay concludes that users should pause and think before reacting to messages that instill a sense of urgency. “The effectiveness of these techniques relies on the panic a victim might feel if they received an invoice for goods or services that they did not purchase,” Kay writes. “The emotional reaction to notification of this sort can be strong and may impair judgment.
“The natural response is to get right on the phone and try to back the order out, or barring that, find a way to obtain a refund. The phishers take advantage of this disrupted emotional state to extract personal or financial information before the victim realizes that something is off.”
Blog post with links:
https://blog.knowbe4.com/quickbooks-phishing-scam-is-back
Callback Malware Campaigns Impersonate CrowdStrike and Other Cybersecurity Companies
On July 8, 2022, CrowdStrike Intelligence identified a callback phishing campaign impersonating prominent cybersecurity companies, including CrowdStrike. The phishing email implies the recipient’s company has been breached and insists the victim call the included phone number. This campaign leverages similar social-engineering tactics to those employed in recent callback campaigns including WIZARD SPIDER’s 2021 BazarCall campaign.
This campaign will highly likely include common legitimate remote administration tools (RATs) for initial access, off-the-shelf penetration testing tools for lateral movement, and the deployment of ransomware or data extortion.
The callback campaign employs emails that appear to originate from prominent security companies; the message claims the security company identified a potential compromise in the recipient’s network. As with prior callback campaigns, the operators provide a phone number for the recipient to call.
Share
JUL






About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com