Catch of the Day: Webmail Upgrade Phish
Chef’s Special: Sextortion Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
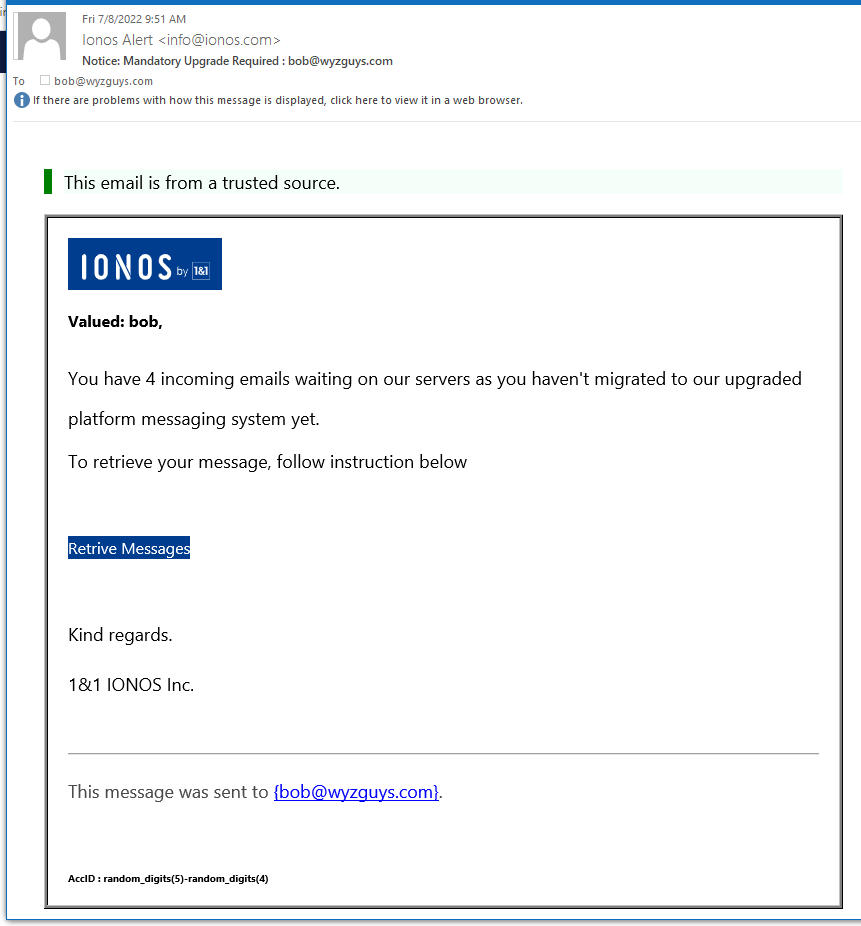
IONOS Webmail Upgrade Phish
Another credential stealing phishing exploit. With all of these I have seen in the last year, you might assume that the bad guys have everyone’s email user ID and password by now.
Kudos on the phishing email. It starts with This email is from a trusted source. So, of course, you should trust it, right? Well of course not, but the power of suggestion is strong. The sender’s email address Ionos Alert <info@ionos.com> looks correct for the source, although IONOS is usually spelled with all capital letters.
The Retrieve Messages link resolves to the landing page at https://morning-hamlet-06981.herokuapp.com/#bob@wyzguys.com. This is not and IONOS URL, so we can assume that this fraudulent. Entering your password here just sends it to the attackers
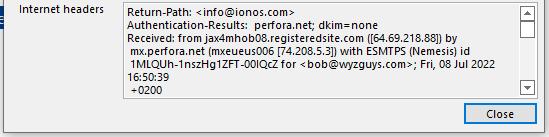
The Internet headers give us the usual mail server information
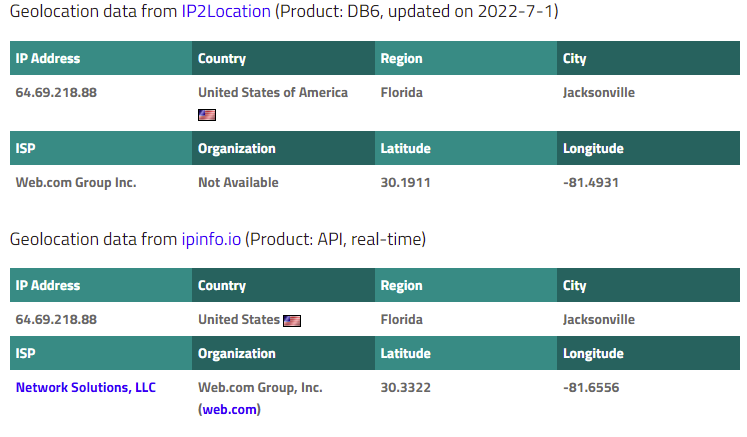
Using the IP address for geolocation shows this email originated from Jacksonville, Florida.
This is an example of a pretty convincing exploit, very good quality trade dress on both the email and the landing page. Be on your guard with these sorts of email. And check out the article below: Have you ever found phishing emails confusing? You aren’t alone
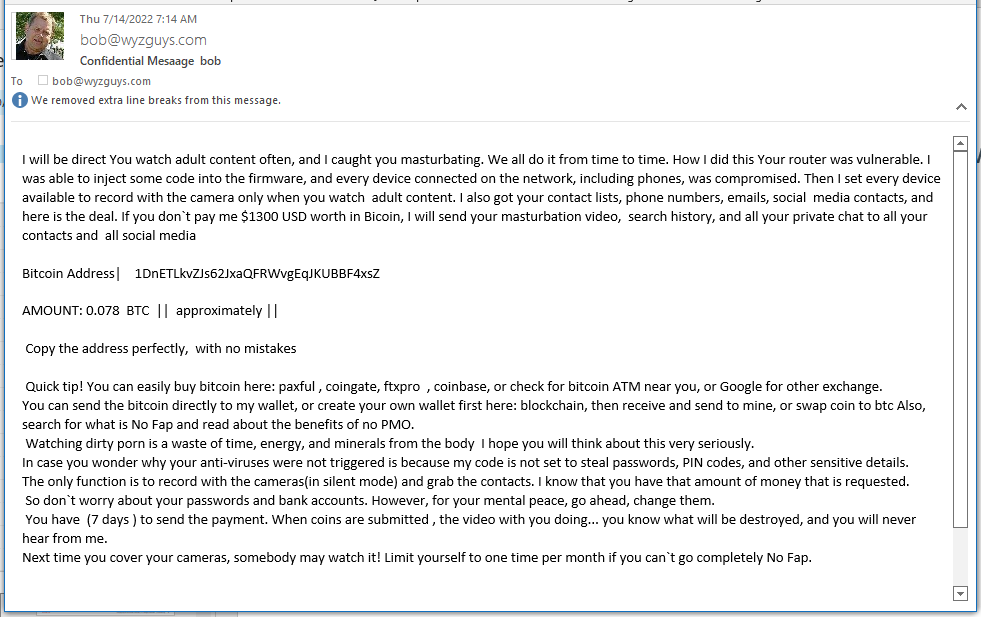
Sextortion Phish
Everybody gets on of these once or twice. This may be my third. This is just a simple shakedown. There is no incriminating video. And cover that camera anyway!! The extortion amount is $1579.00, the value of .078 Bitcoin. I am not paying it, and wouldn’t even if it was real.
Have you ever found phishing emails confusing? You aren’t alone
According to Kaspersky, 16% to 18% of employees will click an email template sent by an adversary that appears on the surface to be delivery issues or tech related errors. This is when a cybercriminal is able to take advantage of a user’s lack of awareness around the subject to gain access to their sensitive information. Per the cybersecurity company, the five most clicked on emails per the phishing simulator were:
- Subject: Failed delivery attempt (18.5%)
- Subject: Emails not delivered due to overloaded mail servers (18%)
- Subject: Online employee survey (18%)
- Subject: Reminder: New company-wide dress code (17.5%)
- Subject: Attention all employees: new building evacuation plan (16%)
In most of these cases, the employees skimmed these subjects on a surface level, as they appeared to be coming from reliable sources such as the company’s HR department or Google, but these were carefully crafted email templates attempting to pass off as legitimate.
North Korean State-Sponsored Cyber Actors Use Maui Ransomware to Target the Healthcare and Public Health Sector
Original release date: July 6, 2022
CISA, the Federal Bureau of Investigation (FBI), and the Department of the Treasury (Treasury) have released a joint Cybersecurity Advisory (CSA), North Korean State-Sponsored Cyber Actors Use Maui Ransomware to Target the Healthcare and Public Health Sector, to provide information on Maui ransomware, which has been used by North Korean state-sponsored cyber actors since at least May 2021 to target Healthcare and Public Health (HPH) Sector organizations.
CISA, FBI and Treasury urge network defenders to examine their current cybersecurity posture and apply the recommended mitigations in this joint CSA, which include:
- Train users to recognize and report phishing attempts.
- Enable and enforce multifactor authentication.
- Install and regularly update antivirus and antimalware software on all hosts.
See North Korean State-Sponsored Cyber Actors Use Maui Ransomware to Target the Healthcare and Public Health Sector for Maui ransomware tactics, techniques, and procedures, indicators of compromise, and recommended mitigations. Additionally, review StopRansomware.gov for more guidance on ransomware protection, detection, and response.
For more information on state-sponsored North Korean malicious cyber activity, see CISA’s North Korea Cyber Threat Overview and Advisories webpage.
Ransomware Gang Creates “User-Friendly” Stolen Data Search Site for Employee Victims
In an interesting extortion twist to get ransomware victims to pay up, one gang has created a search site to allow employees to see if their own private information has been made public.
Traditionally, ransomware gangs have used stolen data to extort their victim into paying the ransom. Because the data taken is in the tens of hundreds of gigabytes, the historically normal practice has been to slowly leak out the data, making it accessible to whoever decides to visit the ransomware gang’s data publication site.
But, like any business model that’s not working, sometimes it takes a bit of innovation and evolution of the execution to secure the desired outcome. As is the case with the newest – and, reportedly, the most sophisticated – ransomware “kid” on the block, AlphV/BlackCat ransomware.
According to BleepingComputer, this gang has shied away from the traditional extortion techniques and instead built out a relatively user-friendly website that allows employees of the victim organization to search through the stolen data to see if their personal data is included.
This technique feels like it would add some pressure onto the organization to pay to have this site taken down (in addition to the leaking of all the data, etc.).
This kind of evolution in innovative ransomware techniques (and more like it) should be expected, as ransomware isn’t going anywhere anytime soon. This means your organization needs to put the necessary effort into keeping ransomware from making its’ way onto your network.
This effort should include the organization’s user base who, with the right security awareness training, can help augment your security stance and lower the likelihood that ransomware will successfully strike.
Blog post with links and screenshots:
https://blog.knowbe4.com/ransomware-gang-creates-user-friendly-stolen-data-search-site-for-employee-victims
Share
JUL






About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com