Catch of the Day: Encrypted Wire Transfer Phish
Chef’s Special: Smash and Grab Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
Encrypted Wire Transfer Phish
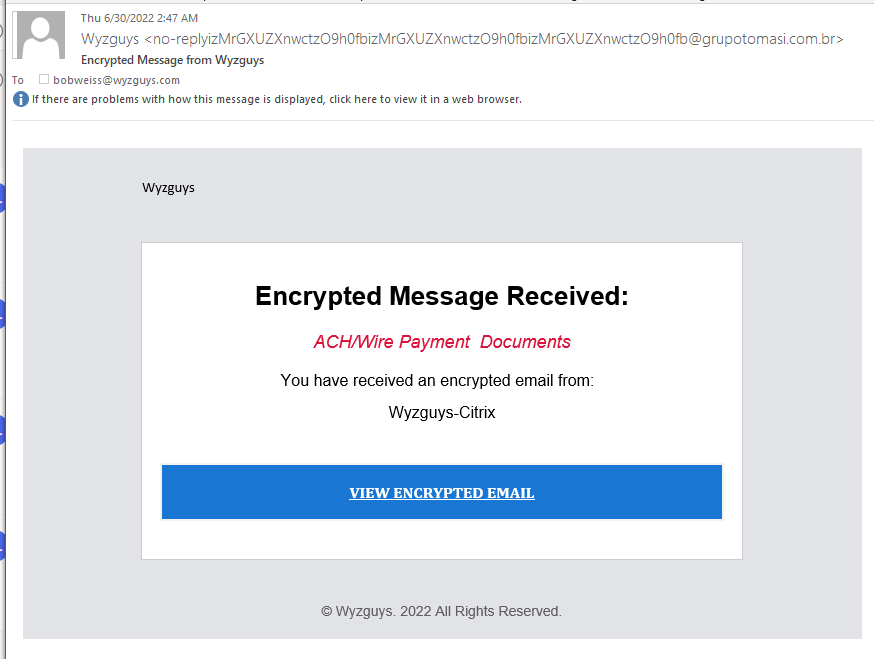
I received this on 2022-06-30 from an address in Brazil. A new twist on credential stealing. Heres the details, starting with the email
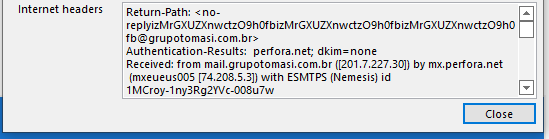
The email headers show the sender to be using a Brazilian mail server.
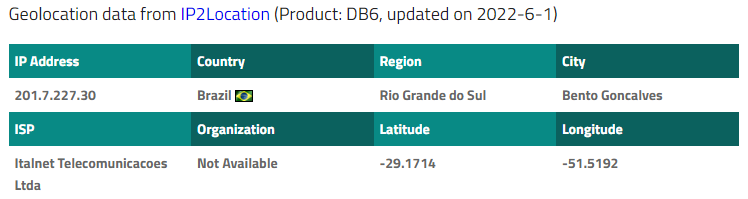
The IP address location confirms the source
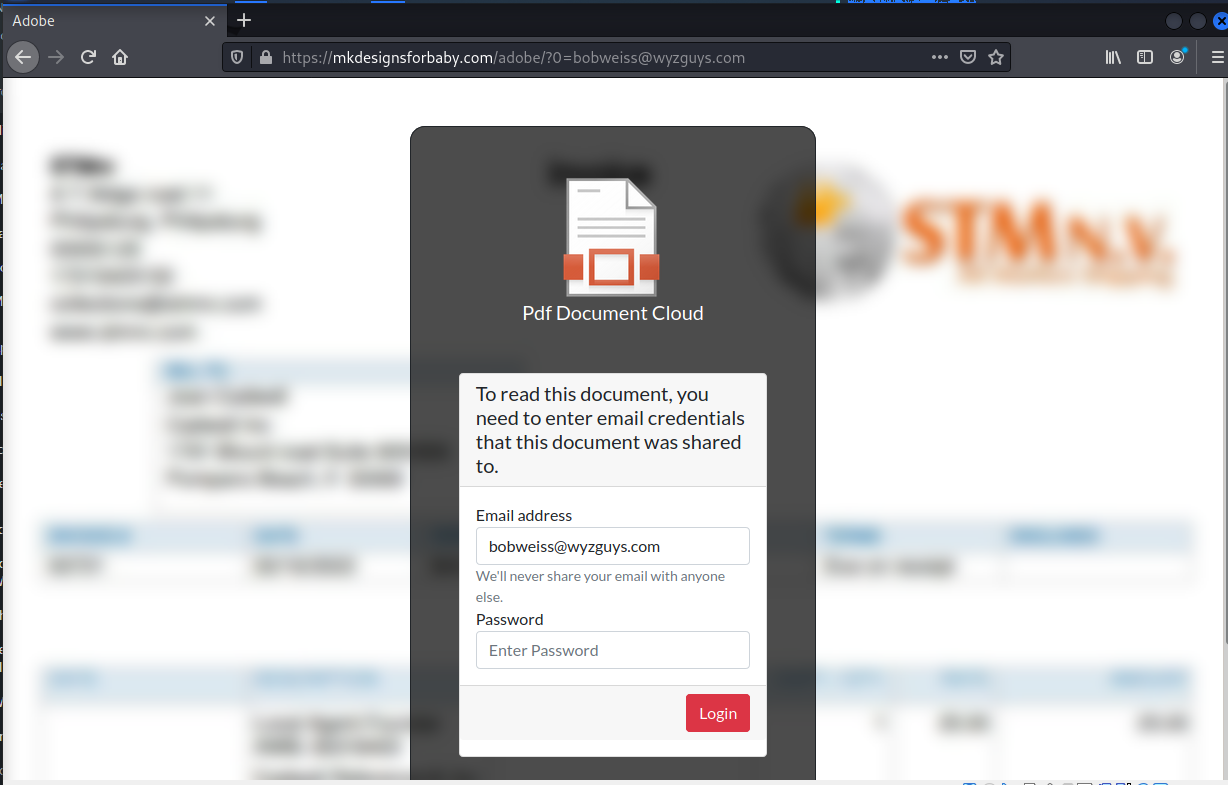
The VIEW ENCRYPTED EMAIL link resolves to http://akdhmkplf2e2kz0crkw0whoqpakdhmkplf2e2kz0crkw0whoqp.ch-tx.com/ionos/#?0=Ym9id2Vpc3NAd3l6Z3V5cy5jb20= which was redirected to https://mkdesignsforbaby.com/adobe/index.php?error=1&0=Ym9id2Vpc3NAd3l6Z3V5cy5jb20=
Using my test password generated an error message, but I am sure completed the mission for the attacker,
I opened the hijacked domain https://mkdesignsforbaby.com/ and was sent to an Office365 welcome page at https://www.office.com/.
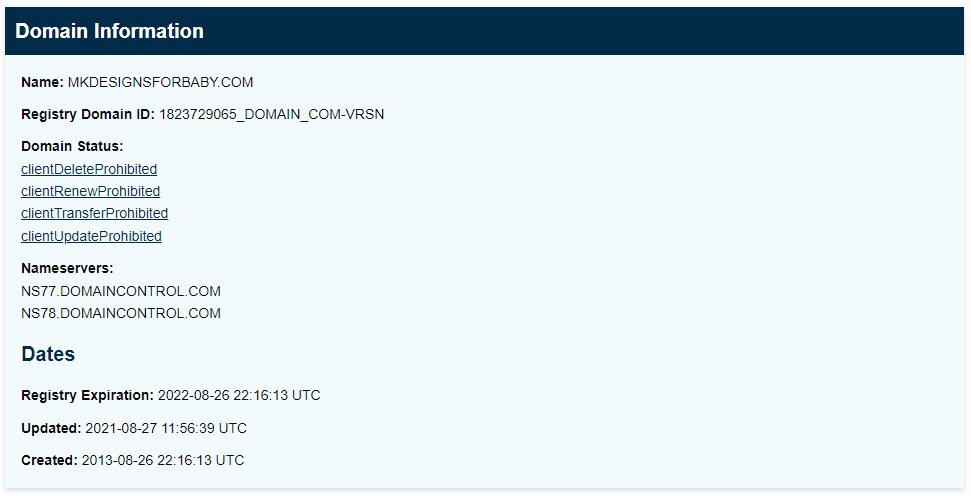
I looked up the domain on ICANN WHOIS, and found that the domain had been registered in 2013. So this domain and web server has been hijacked to host the exploit landing pages.
Information I have been receiving lately from the cybersecurity publication I read say that credential stealing is one of the major purposes of phishing emails. Based on the emails I am receiving, I’d have to say this is the case.
Executive Summary
ReversingLabs recently discovered of a new version of the AstraLocker ransomware (AstraLocker 2.0) that was being distributed directly from Microsoft Office files used as bait in phishing attacks. Our analysis suggests that the threat actor responsible for this campaign likely obtained the underlying code for AstraLocker 2.0 from a leak of the Babuk ransomware in September 2021. Links between the two campaigns include shared code and campaign markers, while a Monero wallet address listed for ransom payment is tied to the Chaos Ransomware gang.
The “smash and grab” attack methodology as well as other features suggest the attacker behind this malware is low-skill and looking to cause disruption, compared with the more patient, methodical, and measured approach to compromises used by Babuk and other, more sophisticated ransomware outfits. This underscores the risk posed to organizations following code leaks like that affecting Babuk, as a large population of low-skill, high-motivation actors leverage the leaked code for use in their own attacks. More…
Share
JUL





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com