 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: Voicemail Message Phish
Chef’s Special: HR Notification Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
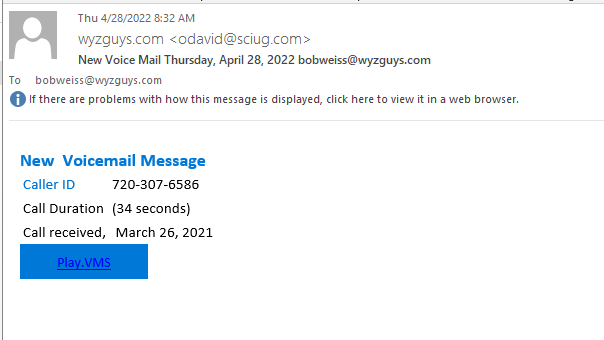
Voicemail Message Phish
This one came to my Inbox last week.
The Play.VMS link resolved to https://mailasr395grfh45ike34j67.z13.web.core.windows.net/jlre94o5ulejdflr493uls022rklw4.html#bobweiss@wyzguys.com. The windows.net domain name makes this seems like this exploit required the hijacking of a legitimate Windows email server.
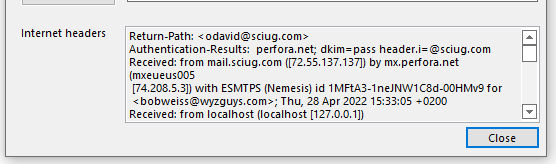
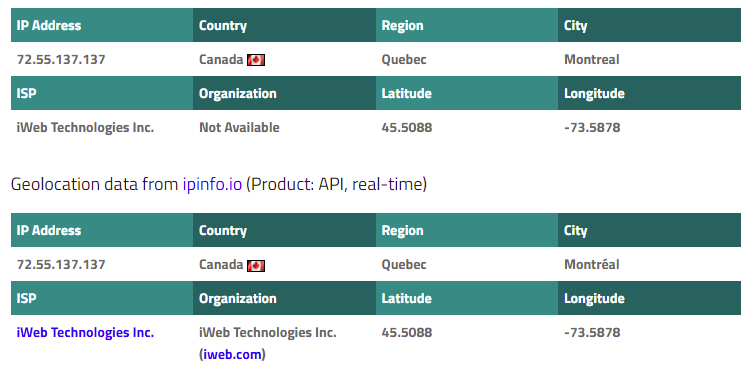
The email headers show this email ordinated from mail.sciug.com ([72.55.137.137]) The IP address resolved to Canadian hosting company iWeb Technologies in Montreal.
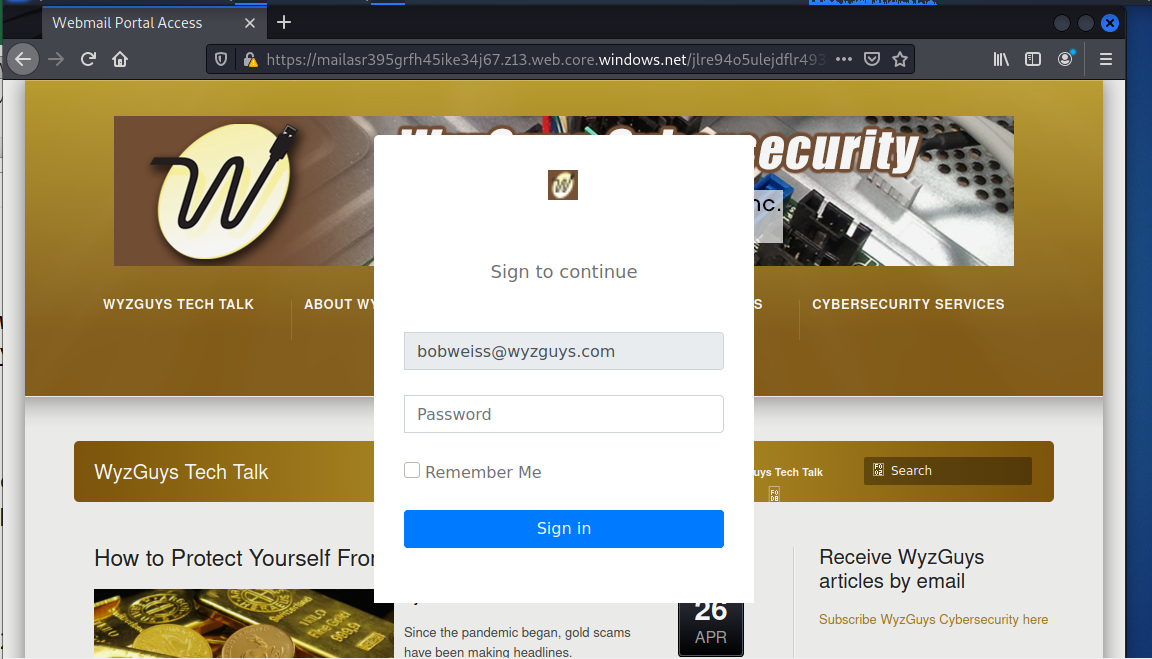
So back to the Play.VMS link. The landing page is shown below. Amazingly enough, this exploit loaded the current home page for my own web log. It took 10-15 seconds to load, but the article shown is from three days ago. I entered a fake password and nothing happened, no error messages, nothing. But I am certain this is another credential stealing exploit.
The home page to the SCIUG.COM domain is below, appears to be a legitimate, but hijacked website that is for a Ugandan tech company, but the web site is hosted in Montreal.
I am especially interested in the way my own web page was used to populate the exploits landing page. This looks very realistic. I happen to know my email does not work this way, but in a bigger enterprise you may just be able to trick users into entering their password.
HR Notification Phish
This exploit appears to come from an HR department, looking for compliance to a Workplace Violence Policy. This is certainly not for any comp-any I have ever worked for, or work for currently.
The link and button in the email resolve to https://hr-almasindos.lt.acemlnc.com/Prod/link-tracker?redirectUrl=aHR0cHMlM0ElMkYlMkZ3d3cuY29nbml0b2Zvcm1zLmNvbSUyRlNjb3R0ZWxlY3RyaWNzdXNhY29tJTJGRW1wbG95ZWVXb3JrUGxhY2VWaW9sZW5jZVByZXZlbnRpb25Qb2xpY3k=&sig=7d3a2TtCvYdfoT6T2p3g3a8Gh7MeeA67DabZAEn3hzZ5&iat=1651596445&a=%7C%7C68321852%7C%7C&account=hr-almasindos%2Eactivehosted%2Ecom&email=oUyfxm8wQWJRW2SYtkxqyXwFoqDlMHNmyq65fGLdufk%3D&s=a3290a2caa596147006a77d9a6b10929&i=3A4A1A5. This is redirected to https://www.cognitoforms.com/Scottelectricsusacom/EmployeeWorkPlaceViolencePreventionPolicy
I wonder who Scott Electric USA is?
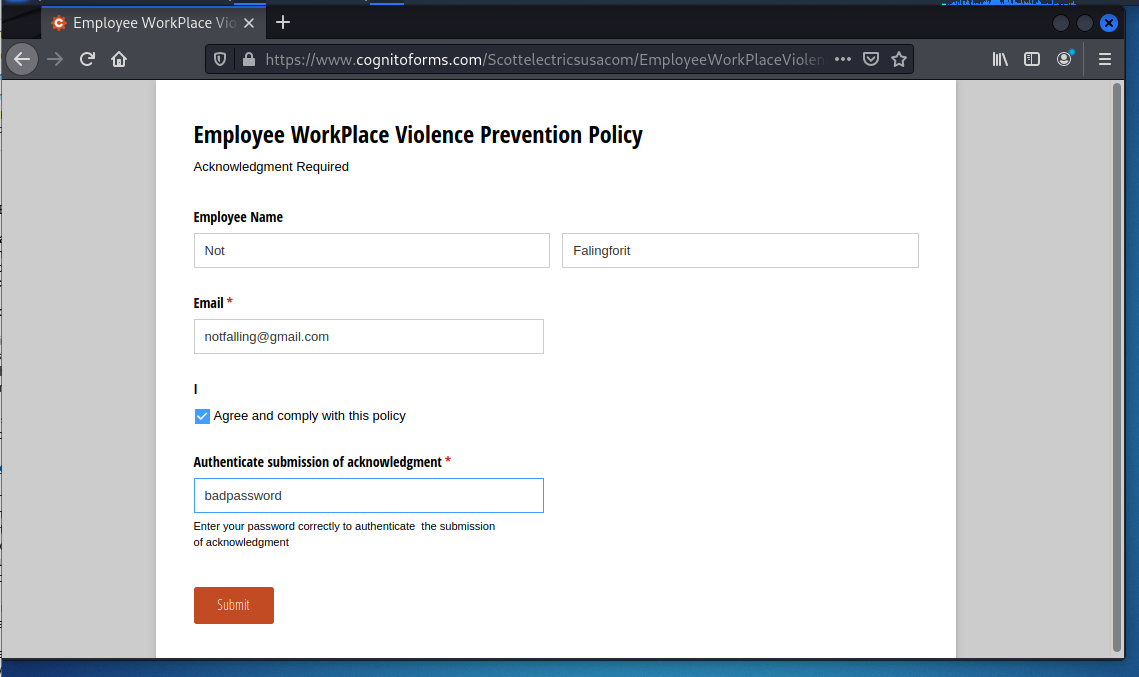
This is the landing page. I just looks like a credential stealer, and the fact that the password is displayed in plain text is a clue this is a scam.
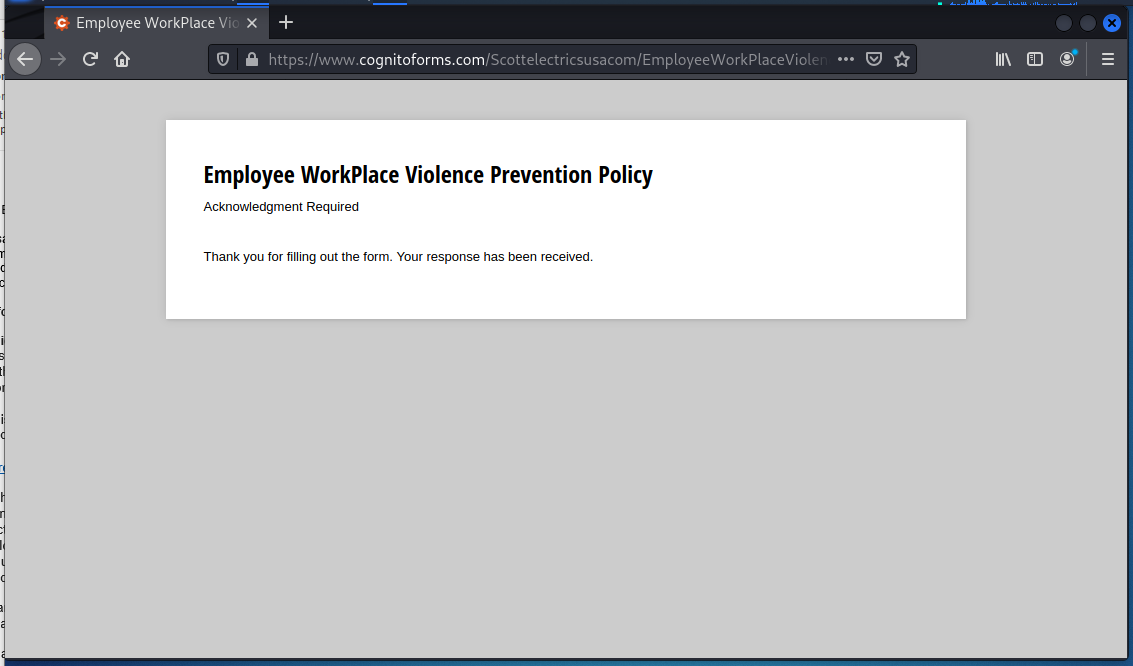
The confirmation page should show an error because I entered in a fake name and password.
Moral of the story: if you get something weird from HR, call them and ask them about it, or report it to your abuse email address, or both.
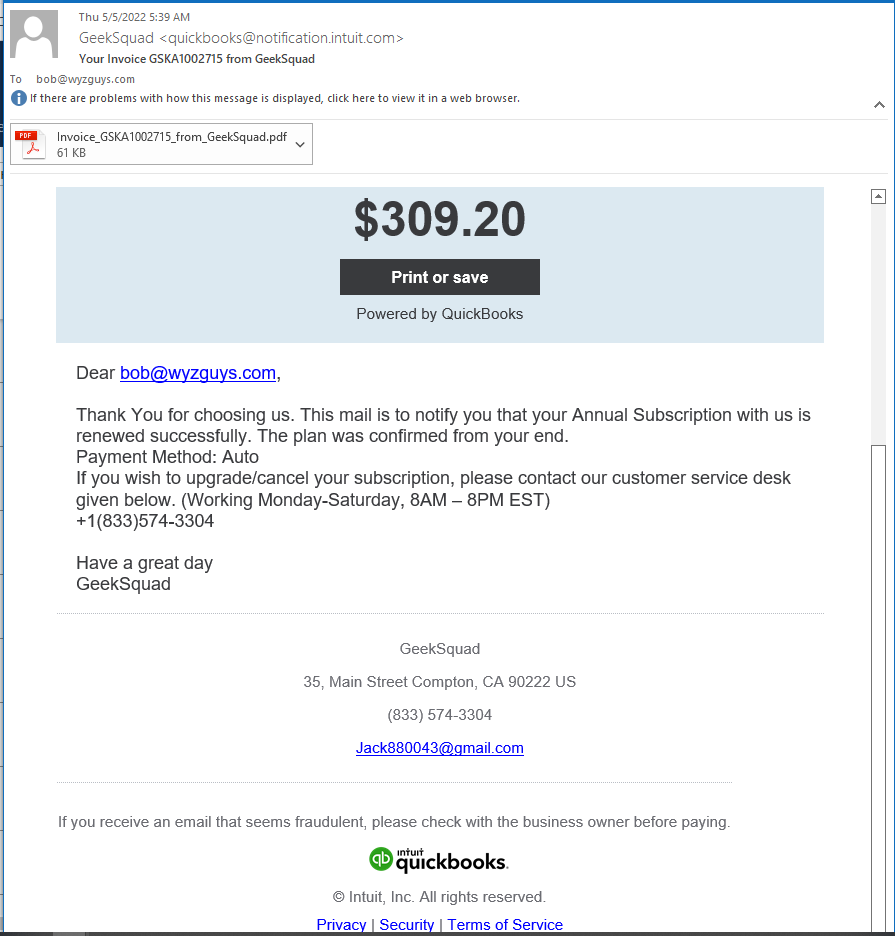
Geek Squad Invoice from QuickBooks
I got an invoice from the “Geek Squad” for an annual contract renewal. I don’t use the Geek Squad. (Why would I? I am the Geek Squad).
The email came with a PDF attachment, and an active Print or save button. Here’s the email, it was too long for a single screen shot, so there are two emails, top and bottom.
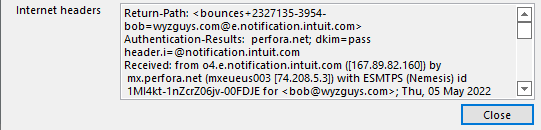
The email headers show that this invoice really came from a QuickBooks account at intuit.com
The button link was actually a link to a legitimate QuickBooks payment page at intuit.com as well.
http://links.notification.intuit.com/ls/click?upn=LEV65WI9EZ1l5TkUt4hKqzq6J49VEXJMRhUxqRckK3UK6eeEy0A<truncated>
There was something “wrong” with my browser, Firefox ESR in my Kali VM.
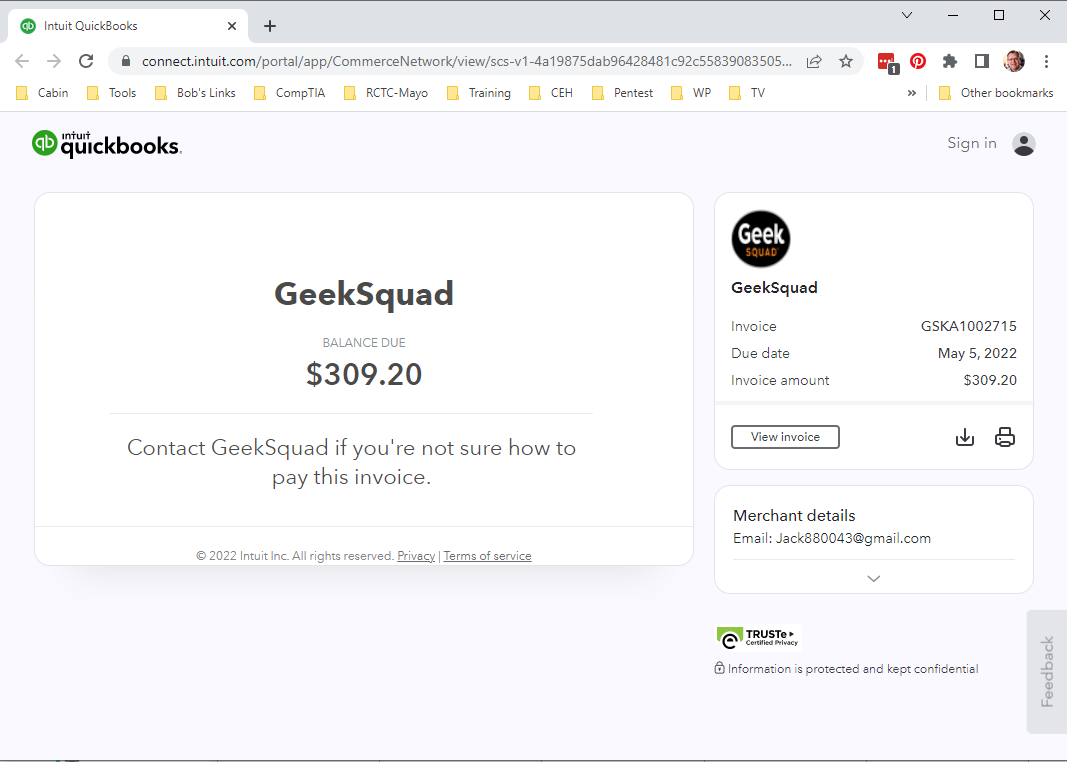
Since this was a legitimate QuickBooks site, I opened it using my computer’s Chrome browser. This is a real payment page. But notice the vendor information Jack880043@gmail.com. Not really the Geek Squad, is it?
So this exploit is a straight up scam using legitimate Inuit services to trick people into paying the invoice. And what about that invoice, any surprises there?
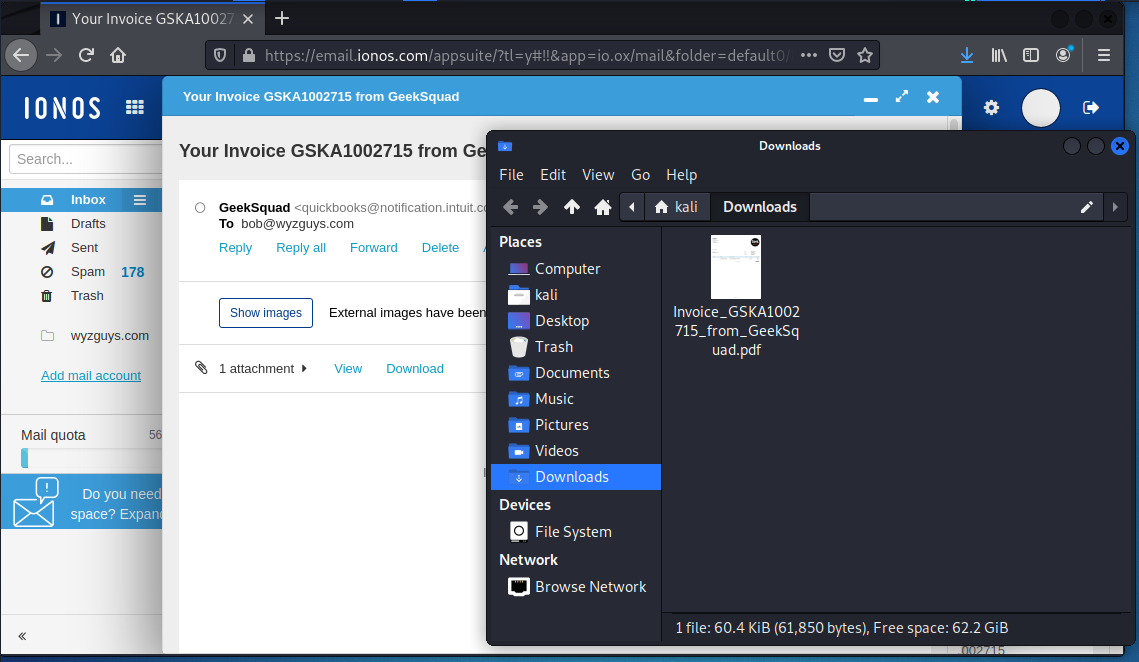
I downloaded the invoice and opened it in Kali.
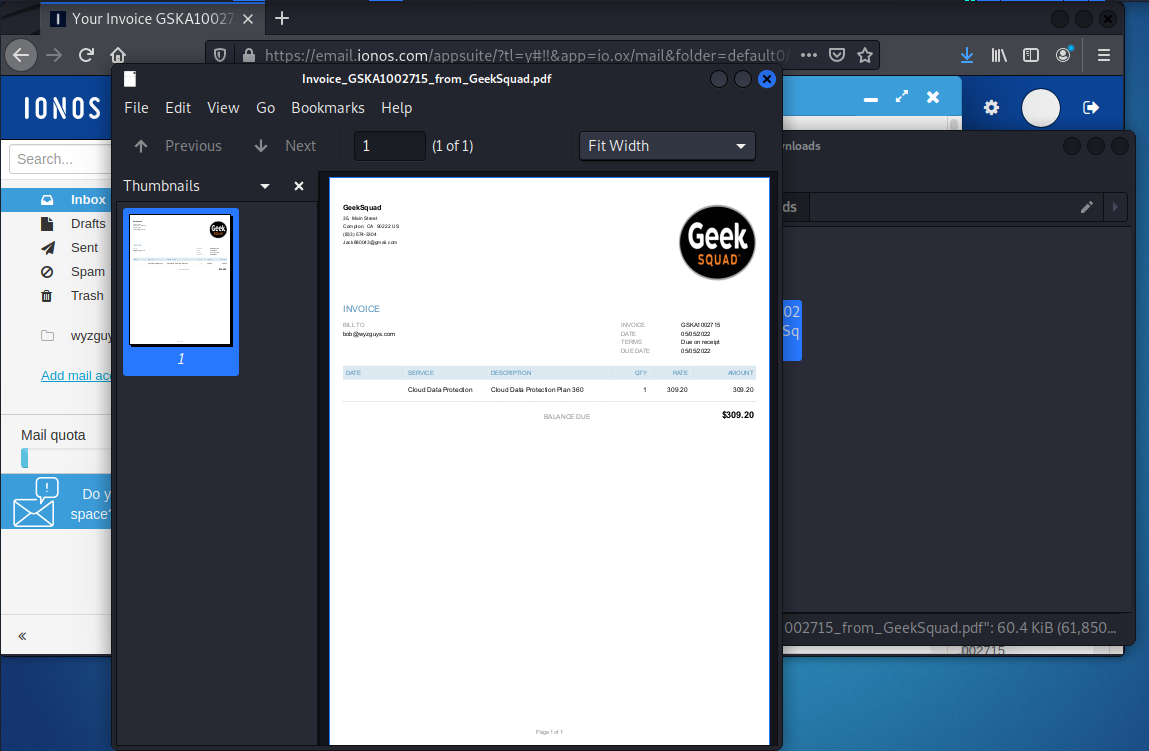
And it is just a PDF copy of an invoice.
This type of scam seems very realistic because everything including the phishing email came through legitimate Intuit services. Be on your guard for these sorts of scams.
Share
MAY







About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com