Phishing Email Alerts
Catch of the Day: Password Protection Phish
Chef’s Special: Last Warning Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
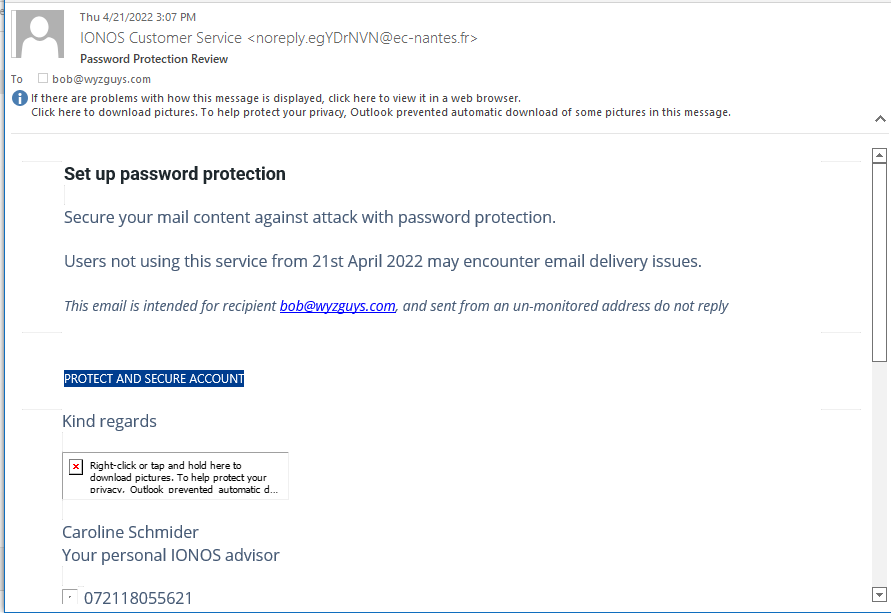
Password Protection Phish
I receive this last Friday, and it appears to be from my web and email hosting company. But the sender address originated in France.
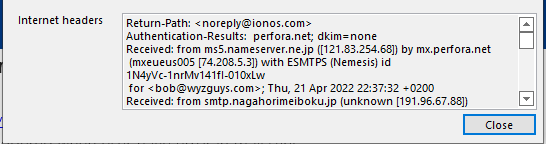
Here is a look at the email headers shows that this email originated in Paris France, and the domain is from Nantes University
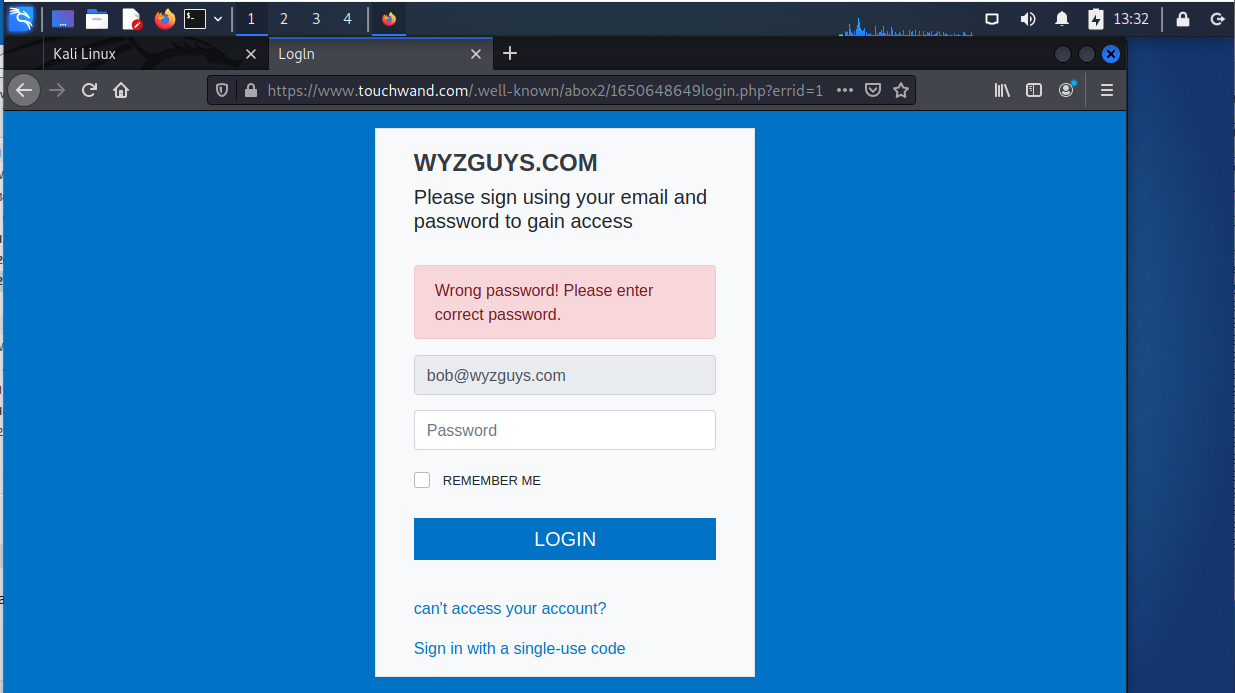
The Protect and Secure Account button resolves to https://www.touchwand.com/.well-known/abox2/?r=bob@wyzguys.com. We see a pretty straightforward email credential capture form,
My attempt to authenticate using bullshit as my password failed, but of course the information was instantly relayed to the attacker.
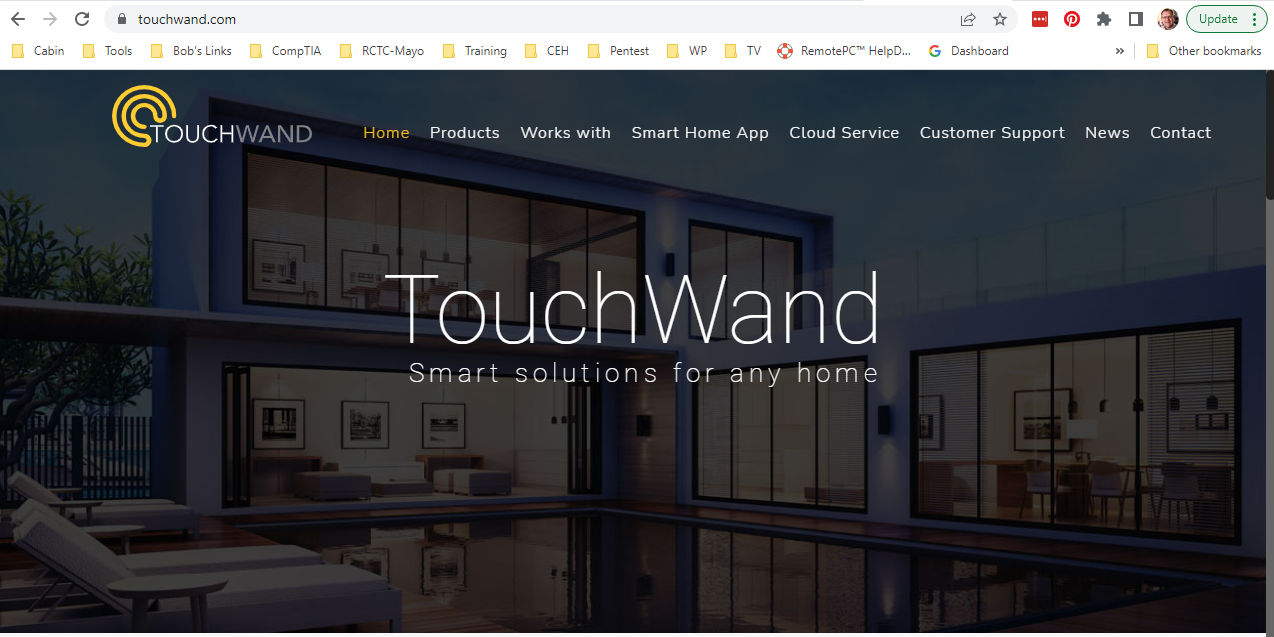
The touchwand.com domain resolved to the home page of an Israeli IoT home automation company, with offices in France. There are a lot of connections to French organizations in this exploit. The email is coming from a host in Paris, but everything else seems to be in Nantes. It would appear that someone was able to hijack both the email and web server used in this exploit. My guess is that a student at Nantes University who may also work at TouchWand is behind this particular exploit. Some kids get student loans, and some go into cybercrime to fund their education.
Last Warning Phish
This one also arrived last Friday, and also appeared to be from my email host. The from line was spoofed.
The Internet headers showed this was sent from Osaka, Japan.
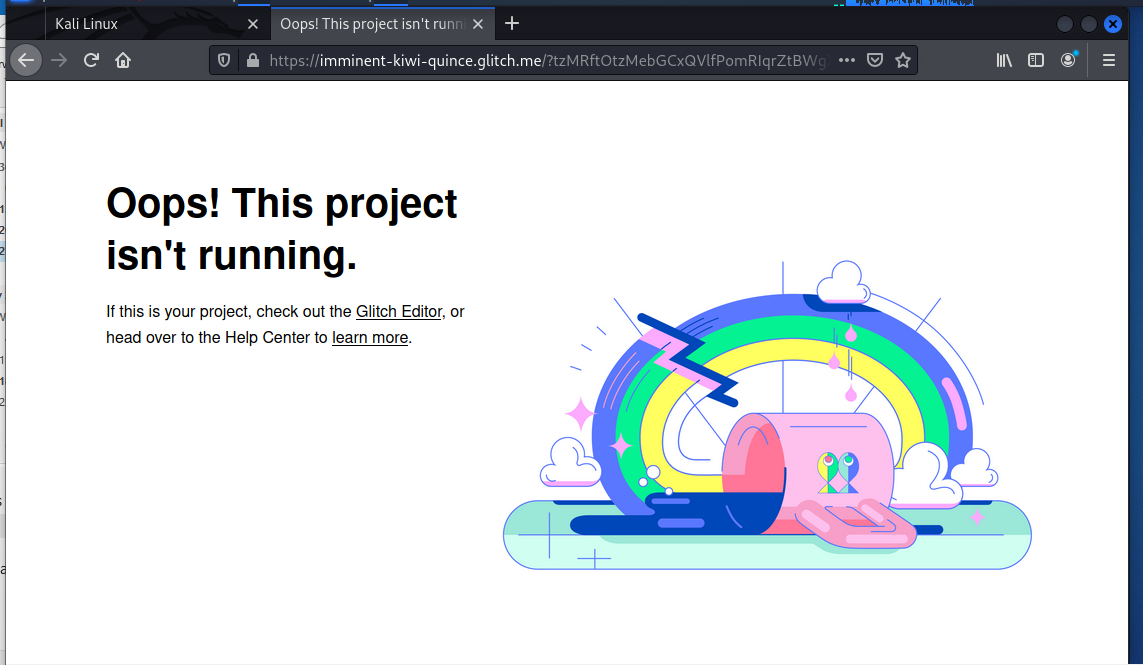
The View Message button resolved to https://imminent-kiwi-quince.glitch.me/?tzMRftOtzMebGCxQVlfPomRIqrZtBWgXGEZadYPCHEAQtsdtus&email=#WW05aVFIZDVlbWQxZVhNdVkyOXQ= Glitch.me has shown up as a resource in several recent phishing exploits. They appear to be a legitimate site for application developers and coders to use to write applications. Looking at the error page, it would appear that this exploit was taken down before I could get to it, so we really don’t know what the objective of the attacker was. At least Glitch appears to be doing a reasonable job taking down these sorts of exploits.
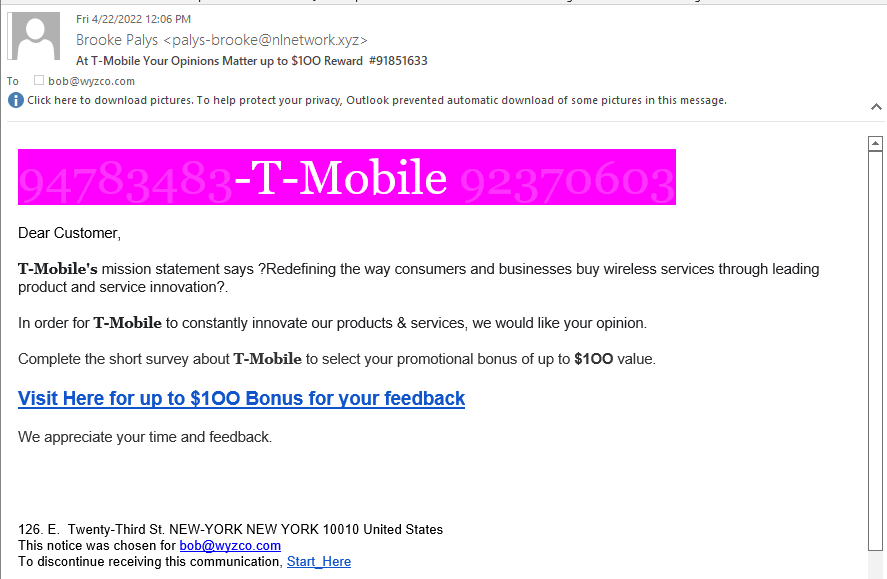
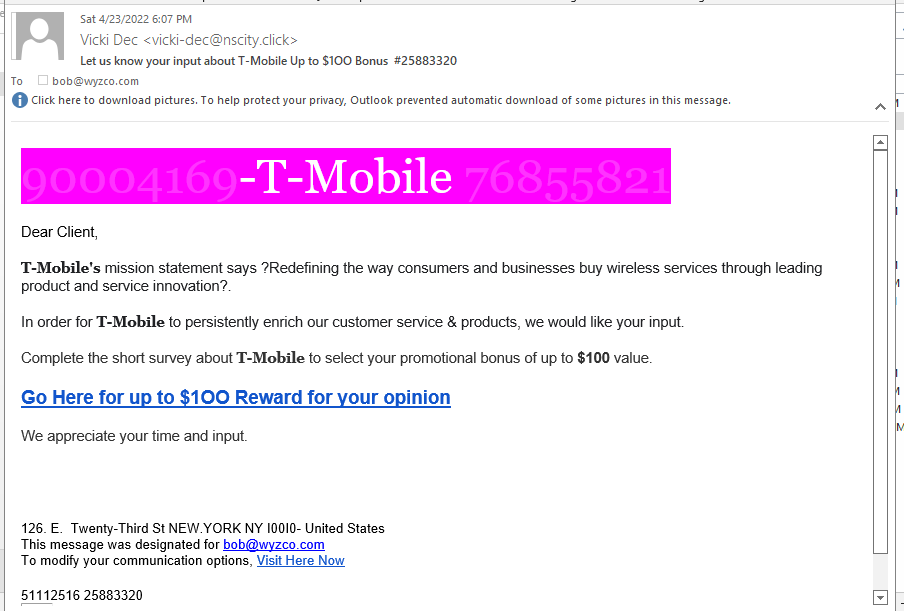
T-Mobile Survey Phish
I seen these before, too. The email seems to be from T-Mobile but the email address palys-brooke@nlnetworks.xyz seems wrong or at least suspicious.
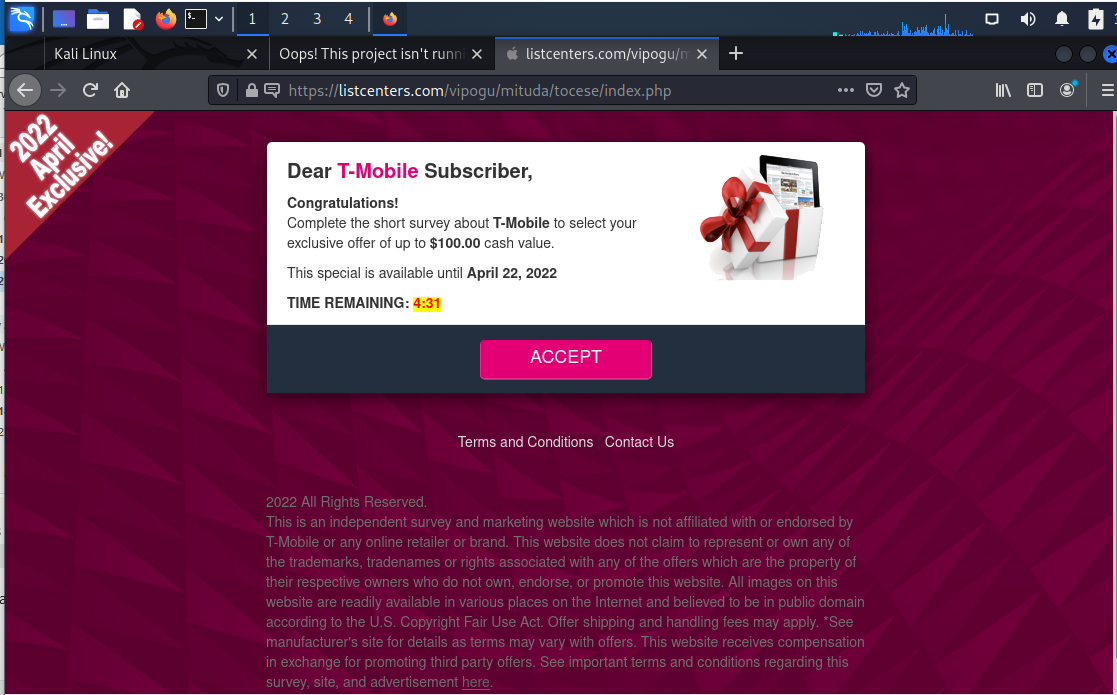
The link resolved to http://www.nlnetwork.xyz/perceptively-assaulted/cf66ll2V395op86N10Fgc9cS2a3r14LFsFf68.GsEGsi6fdFSKQ7Exxy1v06XNAjwD and was redirected to https://listcenters.com/vipogu/mituda/tocese/index.php Clicking on the link brought me to a “survey” page that asked me 5 pretty worthless questions, from a marketing perspective. The spooky part of this URL is the phrase perceptively-assaulted. Think about it.
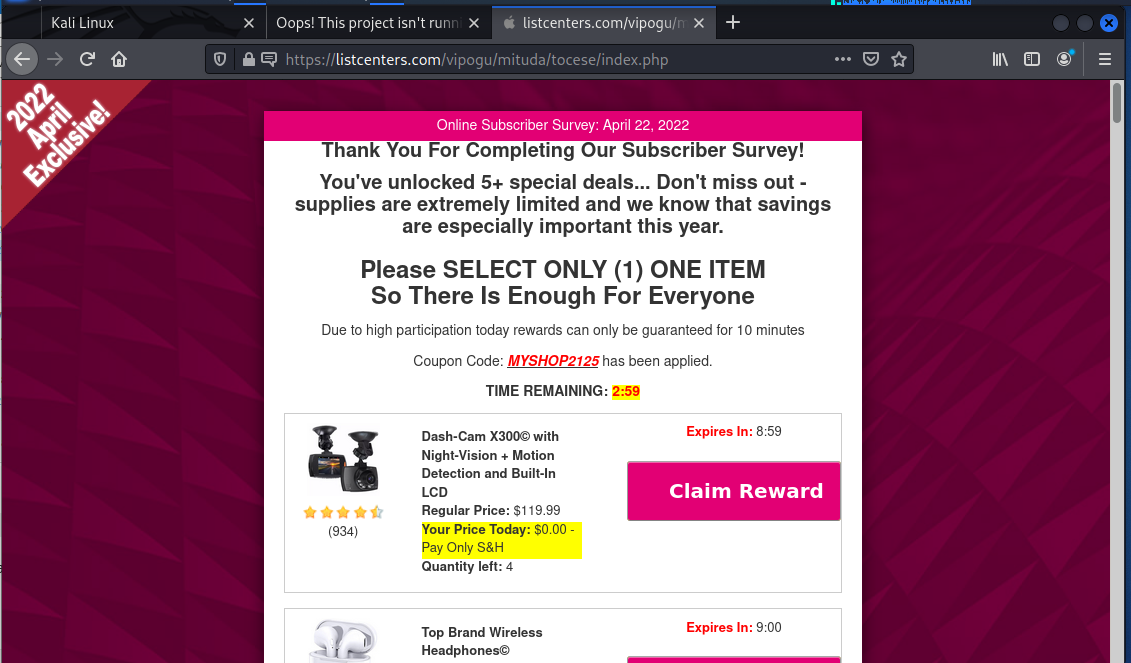
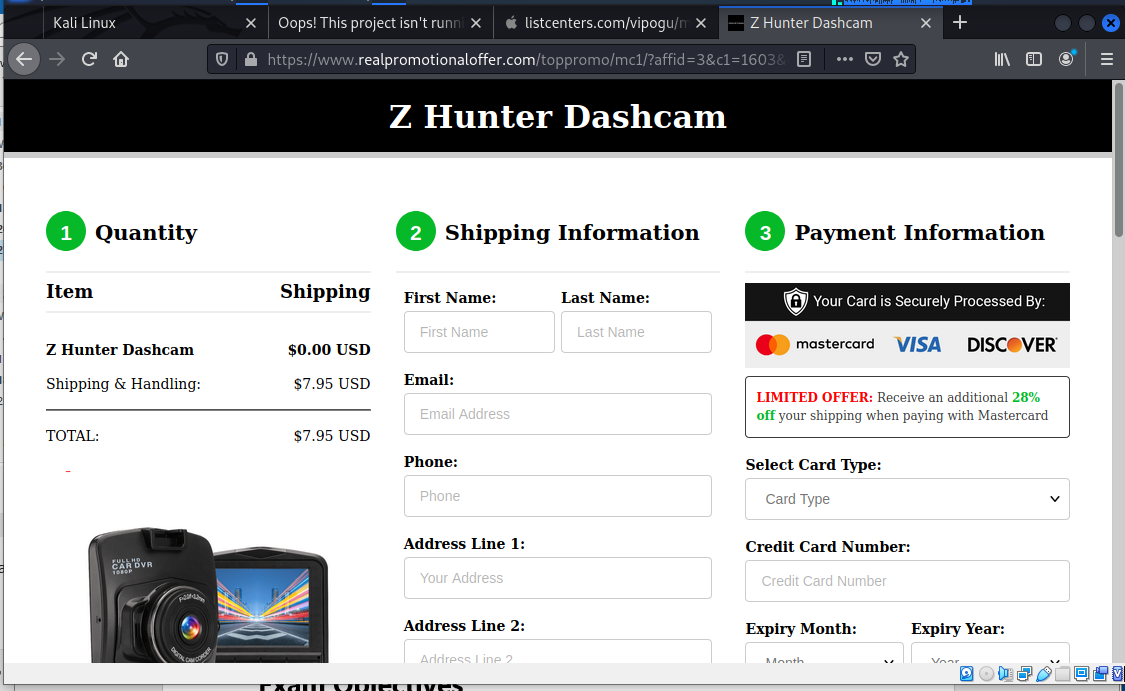
When I finished the survey, I was offered the choice of several high-end toys. So I picked the dash cam. I only have to pay shipping and handling!
The next page is collecting a lot of personal information (PII) and credit card information (PCI).
Had I followed through, I am certain that the first in several spurious charges would be for the dash cam. These items typically never arrive, but you will need to cancel and replace your credit card. The other personal information will have flown, where it will be sold over and over again to other scammers like this one.
T-Mobile Redux Phish
And here is a slightly different twist, The link resolved to http://www.nscity.click/31d5F2D395v8U6k12ocdZP9ZY2b2_14eFsFf68.GsEGsi6Qd.enm5Kq10F5zywUD/skirted-plied and then redirected to https://registermix.ru/yucema/ho/belu/index.php, which is a Russian we site,
Phishing goes KISS: Don’t let plain and simple messages catch you out!
Sometimes we receive phishing tricks that we grudgingly have to admit are better than average, just because they’re uncomplicated. More…
Share
APR








About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com