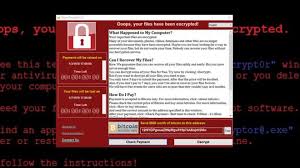
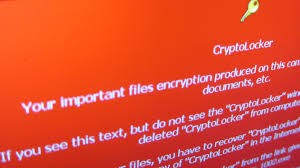
 According to a recent article on Naked Security, not at all hard. While at Black Hat in Las Vegas, researchers from Sophos gave a presentation that dissected the “Philadelphia” ransom software as a service (SaaS) model.
According to a recent article on Naked Security, not at all hard. While at Black Hat in Las Vegas, researchers from Sophos gave a presentation that dissected the “Philadelphia” ransom software as a service (SaaS) model.
Anyone can buy the Philadelphia ransomware kit on the Dark Web for $400. And for this nominal investment, the would-be attacker gets a simple executable file that sets up the whole system automatically. ...
Continue Reading →AUG